by Pandora FMS team | Last updated Aug 14, 2023 | Cloud & Virtualization, Community, Features
Computer monitoring, inventory and remote control; a natural relationship
What do computer monitoring tools, inventory tools and remote control tools have to do with computer systems?
This is a question that human beings have been asking themselves since the beginnings of time….
Well, that might not be true actually because at the dawn of time none of these tools existed, but it is still an interesting question. Depending on what you do, you may not find a connection. But, if you work with this kind of tools in your professional life, you will understand that these are closely linked.
The relationship between computing monitoring, inventory and remote access is a natural one. If you work in the Information Technology sector and one of your duties is to monitor computer systems, you will know the advantages of having an inventory or a remote management system.
In this article we are not going to see each of them in detail. We will not go into what a computer monitoring system is, what an inventory is or what a remote control system is. In order to learn more about what they are and how they work, you have many articles on this blog that will reveal many of their secrets, especially in terms of monitoring.
But we are going to look at some of the relationships that exist between these three types of tools, through the possibilities offered by Pandora FMS and another tool that you may not know yet, called eHorus. Let’s do this!
Pandora FMS: monitoring and inventory
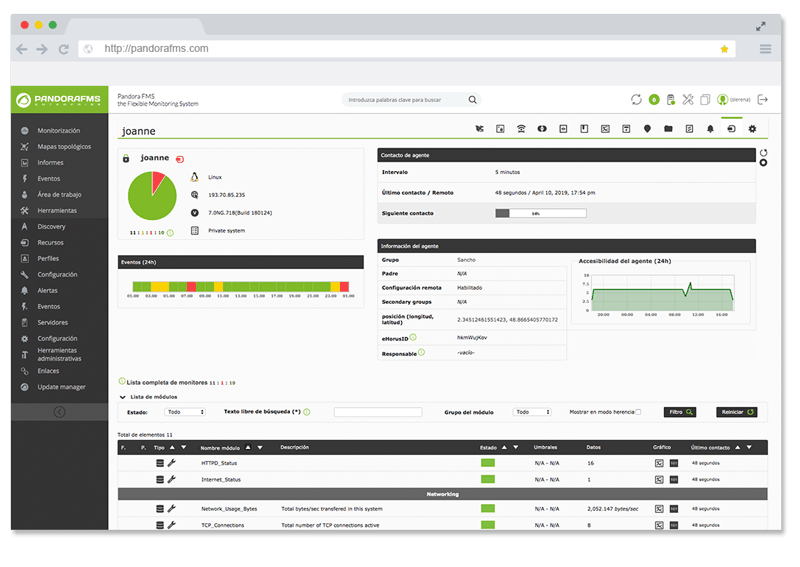
Do you know Pandora FMS? If you don’t, what are you waiting for? It is one of the most flexible monitoring tools on the market.
If you are a regular reader of this blog, you probably already know Pandora FMS pretty well. But one of the things you might not know (although you might guess it) is that, besides its multiple features, you can also use Pandora FMS to create an inventory of your computer resources.
It makes perfect sense, doesn’t it? Since you are monitoring a number of different activities, for example a company’s servers, you can create an inventory with the information that the monitoring system provides. Through its monitoring, the Pandora FMS inventory allows you to obtain very useful data about your systems, like the version and firmware, the installed hardware, the operating system version, etc.
In addition to this, monitoring offers periodically updated information, so that you can learn about any changes that may occur in the inventory.
Pandora FMS collects the necessary data to form the inventory both remotely and locally, through agents. Do you want to know more details, or see how the inventory data is displayed? Check out the Pandora FMS Documentation.
Or you can also get more information at the following address:
https://pandorafms.com/monitoring-solutions/inventory/
Pandora FMS and eHorus: computing monitoring and remote access
If you are into system monitoring you will understand this. You often need access to the computers that are being monitored, and this can mean spending a lot of time traveling if they are in different locations.
Think about the following scenario: Pandora FMS detects that one of the devices that are being monitored is having some problem, so it generates an alert. The problem is that this device is not in the city where you work, it’ s quite a few kilometres away. And the situation is critical, so you need to take immediate action. How do you plan to do that? You don’t currently have the ability for teleportation. You don’t even have a tiny helicopter….
However, luckily, for this type of situation we have remote access systems. And one of them, developed by Ártica Soluciones Tecnológicas (the creator of Pandora FMS), is eHorus.
Ehorus can be used together with Pandora FMS to have access to Windows, Linux or Mac computers on demand.
Ehorus has many advantages. It can be used from a tablet, mobile phone or any available computer. All you need is an Internet connection.
Ehorus is a very useful solution when used together with Pandora FMS, don’t you think?
But this is not the only thing eHorus can do. Do you want to learn a little bit more about it? You can find more information here: https://pandorafms.com/remote-control-software/
These are just some very basic examples. If you are an IT professional, you can certainly imagine many situations in which these tools will relate to each other. The relationship between computing monitoring, inventory and remote access is very meaningful and occurs naturally in the daily work of an IT professional. And if you have this kind of tools and you can use them together, like Pandora FMS, its inventory and eHorus, then these will make your work a lot easier.
And now, we would like to tell you very briefly some things about Pandora FMS. Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Pandora FMS already has many clients around the world; some of them are top level companies and organizations. Do you want to know some of them and some of our success stories? Take a look, here: https://pandorafms.com/customers/
Or maybe you want to learn more about what Pandora FMS has to offer. Then enter here: https://pandorafms.com
Or maybe you want to get in touch directly with the Pandora FMS team to make a specific question. You can send any query that you may have about Pandora FMS in a very simple way, using the contact form that can be found at the following address: https://pandorafms.com/company/contact/
There is a great team behind Pandora FMS that will be happy to help you!
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
If you have more than 100 devices to monitor, you can contact us through the following form: https://pandorafms.com/en/contact/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!

by Pandora FMS team | Last updated Aug 27, 2021 | Community, Geek culture, Tech
I have no mouth and I must scream. Are we afraid of AI?
We crave it and we are afraid of it in equal parts. Artificial Intelligence is on our horizon. A closer and nearer horizon. We can almost touch it with our fingers….
Will it solve mankind’s greatest problems or will it end the history of our species? It is not easy to give an answer to this question. In general, and perhaps because the apocalyptic scenarios are much more playful than the utopian ones, science fiction has almost always chosen to portray the relationship between humans and artificial intelligences in a very gloomy way…
The examples in film and literature are countless. From timeless classics like Blade Runner to modern myths like Matrix. And of course, without ignoring an icon in the field, such as the Terminator. Have you ever seen any of the films in the saga? If this is the case, then you will probably know the name of the great enemy of Humanity in this group of films: Skynet.
You probably do not know what its most immediate precedent is, which is found in a story from the distant year 1967, called “I have no mouth and I must scream“.
I have no mouth and I must scream.
This unforgettable title is the name of one of the most terrifying stories of the great Harlan Ellison, one of the most important science fiction writers of the 20th century.
It tells the terrible story of a group of five people, four men and one woman, who happen to be the last survivors of a nuclear holocaust and are under the rule of an all-powerful entity called AM.
AM is an evil being with unlimited power. It hates the human species beyond belief, and has fun torturing its “guests”, and it artificially extends their lives for decades just to get the pleasure of continuing to torment them.
As if that were not enough, the options available for the desperate humans to get rid of AM are non-existent. His actions are so terrible that, at a certain point in the story, one of the characters begs for help from Jesus Christ and then later realises that it makes no sense to ask God for help, since if there were something with a power similar to God’s, it would undoubtedly be AM.
But where did this horrible and mind-blowing entity come from? If I tell you that AM is an Artificial Intelligence, and it was originally a military system, then you will connect the dots, and if I tell you that, at a certain point, it becomes aware of itself and decides to exterminate the human species, you will surely think that you have already heard this story…
Indeed, the similarities between AM and Skynet are obvious. It is so obvious that, according to Wikipedia, Ellison himself has repeatedly stated that Skynet would be based on AM and the Terminator saga itself would have taken ideas from two episodes of the series “Beyond the Limit”, scripted by Ellison.
In fact, and after some controversy, the beginning of the credits for the Terminator films included an express recognition of Harlan Ellison’s work. The connections seem to be clear.
Should we be afraid of Artificial Intelligence?
Entities like AM and Skynet bring fear into our bodies, but that does not mean that we should abandon the development of Artificial Intelligence, but it is a path of such importance that we must walk with all possible precautions.
Over the past few years, multiple voices have warned us of this. From Elon Musk to Bill Gates, from the Swedish philosopher Nick Bostrom to the recently deceased Stephen Hawking, many people from the world of Science, Technology and Philosophy have expressed opinions that vary from one extreme to the other; from those who believe that AI will be the end of Humanity to those who think that it will be the greatest achievement ever achieved and that it will raise the standards of quality of life above anything ever imagined.
Who is right and who is wrong?
It is too early to give an answer to this question. It seems certain that, above all other considerations, nothing will stop human curiosity and the desire to improve, so sooner or later, technology will move forward to give us an answer… or a conclusion.
In any case, we must bear in mind that Artificial General Intelligence is self-conscious and capable of handling any kind of situation that the real world might present, and that it is a Weak Artificial Intelligence, like some of the ones that we already have today and that can be very helpful for very specialized tasks.
In fact, many experts believe that we will never be able to develop self-aware Artificial General Intelligence, or that it will take hundreds of years to do so, since we are not yet able to understand how the human brain works. But there are also those who think that the creation of it is a time thing and we will see it between us much sooner than most people would expect (around 2030, more specifically).
Could Pandora FMS stop Skynet or AM?
Hopefully, we’ll never have to answer a question like this again! The truth is that Pandora FMS is a powerful and flexible monitoring tool, but we have not yet thought about how it could stop a self-conscious and all-powerful Artificial Intelligence. It will be a matter of thinking about it….
Pandora FMS can monitor devices, infrastructures, applications, services or business processes. And it does it so well that many large companies around the world already have it.
And, have you ever watched “I have no mouth and I must scream”? What are your thoughts regarding this film “I have no mouth and I must scream”? Let us know down below in the comment section.
Do you want to know more about Pandora FMS? Click here: https://pandorafms.com
Or maybe you want to send us a query about Pandora FMS. You can easily do this by using the contact form at the following address: https://pandorafms.com/company/contact/
The Pandora FMS team will be happy to help you!

by Pandora FMS team | Last updated Sep 26, 2023 | Customer support, Help Desk
Everyone talks about social networks. Everyone uses social networks. Everyone’s on social networks. Not your company?
Okay, being on social networks is not mandatory, and in fact it has both advantages and disadvantages, but if you have chosen to have a company profile on sites like Facebook or Twitter, you should know that it is likely that some customers use this way to send you all kinds of queries, suggestions or incidents. And now ask yourself, is your company ready to manage this information traffic?
By now you will know that managing customer service on social networks is a very sensitive issue, because the answers you give will be exposed to the eyes of thousands of people. In this post we are going to look at some ideas so that customer service in social networks does not become a nightmare from which you’ll have a hard time waking up.
1. Dedicate an exclusive mean to customer service
Does your company receive a large number of inquiries or complaints from customers? Perhaps it’s time to separate customer service from your main profiles. You can create dedicated customer service sites on every social network. Thus, incidents and queries will not be mixed with other issues that are not so closely related to customer service -such as the presentation of products or promotions- and it will be easier to manage them.
2. Create attractive and informative profiles
Social network profiles are also part of the company’s image. If they are too overloaded or seem abandoned, the image you transmit will not be positive. If, on the contrary, you take care of the aesthetics and information found in them, your users will appreciate it and their customer experience will improve.
One idea, for example, is to create a Frequently Asked Questions (FAQ) section. They are usually one of the most visited sections of any profile or web page, and will avoid that you have to solve individualized some simple doubts that the user could solve by himself (this will save you a lot of work).
3. Work with professionals
Remember that when it comes to customer service on social networks, everything can be seen by anyone who wants to watch. In social networks everything is intensified, so you have to be especially careful. Do you really think your friend nicknamed “Dogfight” is the right person to take care of your business’ online reputation? You can hire a community manager or leave it in the hands of other people within your company who are better able to carry out the task.
4. Be very careful with your answers
It has a lot to do with the professionalism of the people who take care of your profiles. It is better not to give names, but the cases of companies that have suffered serious reputational problems because of an out of place tweet are well known. You really want to get yourself into that mess? Education, moderation and caution must be essential elements in any message you post on social networks. And of course, remember that getting into thorny matters like politics or religion is like juggling fire on a tightrope.
5. Do a continuous follow-up and be quick to respond
Be on your guard! While some social networks allow for comment moderation, in others users will say what they want and when they want, so be on the lookout for disaster control when you least expect it. Your users will also appreciate a quick response, just as they would if they used any other means of contact. Can’t you provide 24×7 service? Specify it in your profile; include your customer service schedule and, if you can meet it, the estimated waiting time to receive a response.
6. Be diligent and respond to everyone
In this sense, nothing changes if you are using a social network with respect to customer service by other means. To respond to your users, you must use the same professionalism and diligence as if you were using the phone, email or any other way. Remember that your job is to solve the problems that arise. Do not leave questions unanswered; the image you give will not be any good. And, of course, make politeness and goodwill your flag when dealing with your users.
7. Personalize your answers
The fact that you don’t have more direct contact (e. g. telephone) or that the answers on social networks reach many people doesn’t mean that you should be impersonal in your answers. Quite the opposite. If you are close in your answers, everyone will see that there is a real person behind them, which will generate more sympathy in your users and make your profiles more human.
8. Use their questions to improve
If you are a regular reader of this blog (which is highly recommended), you will know that complaints or queries from your customers are unique opportunities to improve your business. Your users’ requests can show you bugs you didn’t know about or reasons to implement changes that will make things work better. Don’t waste them. Also, if you offer valuable information, a good response can even end up generating a sale.
9. Strengthen your internal communication
To give an effective response to the incidents raised by your customers, you must have excellent internal communication in your company. Do you have any software to help you? What do you mean? That your software is called “Mildred the one that notes complaints in a post-it“? Seriously, there are better ways to do it.
Take a look at Pandora ITSM. Pandora ITSM is a software that, in addition to other functionalities, has a ticket-based incident management tool, fast and easy to use.
Want to see what Pandora ITSM can offer you? Click here: https://pandorafms.com/en/itsm/help-desk-software/
Or ask us a question on the form you can find here: https://pandorafms.com/en/contact/
We will be happy to answer any questions you may have. Thank you!

by Pandora FMS team | Last updated Mar 6, 2024 | Community, Geek culture, Tech
Mohammed Ibn Musa-al-Khwarizmi is a mathematician and creator of the term: “algorithm”, this term has become a buzzword, thanks to the rise of artificial intelligence.
Algorithms to suggest a possible match, algorithms to invest in stock exchanges, algorithms to predict crime, algorithms to organize our searches on the Internet… Algorithms are everywhere, even if they are unnoticed. These guide our economy, our purchases, and even our way of thinking.
But what is an algorithm?
An easy description and some famous examples
If you’re reading this article and have a technical background, you may know what an algorithm is, and you may even write algorithms frequently.
But there are millions of people who are unsure of what that term means and how it affects our lives. In fact, “what is an algorithm?” is a frequent search on major search engines.
Regardless of your background, stay with us! In this article we are going to answer this question: what is an algorithm? and we will discover some of today’s most influential algorithms.
What is an algorithm?
If we refer to mathematics, which is the field in which the term originates, we can say that algorithm is an ordered and finite set of operations that must be followed in order to solve a problem.
And what exactly does this mean? Let’s break it down into two parts.
- It is an orderly set of operations, which means that it is a chain of precise instructions that must be followed in an orderly manner.
A good way to figure it out is through a cooking recipe, which is still a simple algorithm. In any of them, a specific and orderly procedure is described (“First you heat half a pot of water. Then add a pinch of salt. Then cut the pepper into pieces, removing the seeds and the nerves…“), therefore each of these operations is what makes up the algorithm.
Thus, the algorithm will take the form of a flowchart.
- Its purpose is to solve a problem, which means that it has a defined objective.
This is the part which makes things a little more complicated. When we write an algorithm, we do it to produce a result. It’s not just a matter of writing a nice set of commands that lead nowhere, it’s done rationally and with a specific object.
What happens is that reality always makes things complicated. If, for example, we create an algorithm designed to work in real life, the orders in the algorithm must include instructions that consider the different situations we may face.
Thus, the shape of the flowchart that forms the algorithm will become an enormous “tree” of instructions that, depending on its complexity, may even give us surprising results.
If you want to control what happens on your computers, on your network, without needing to know much about algorithms…
Then we will tell you how you can do it completely free with this software:
What are algorithms used for?
Once you have established the limits of what an algorithm is, you will wonder how it is used in our daily lives.
Since this is a technological blog and deeply related to information technology, we are going to focus on this field which is also making algorithms trendy.
When a developer creates a program, he is essentially creating a set of algorithms. A computer program is a set of commands given to the machine, written in a specific language, to perform a series of specific operations in order to obtain a result.
As you can imagine, a raw computer does not understand human language. That’s why, to communicate with your computer, the programmer uses the programming languages.
The programming language is therefore the tool that serves as a bridge between the human language and the language that the machine can understand. Therefore, the programmer can develop the algorithms and create a series of instructions that the computer can “understand” thanks to the programming language (since computers do not have their own will, they have no other choice but to do so).
Learn about some algorithms that are more famous (and influential) than a rock star
While all this may sound formal, and even boring, programmers around the world have made some algorithms as famous as movie stars and more influential than any politician. Let’s meet some of them.
1. PageRank, by Google.
It is one of the most widely used in the world. This is the set of algorithms that Google uses to determine the importance of documents indexed by its search engine.
In other words, when you do a Google search, this is one of the elements to decide the order in which the results will be displayed.
2. The Facebook Timeline algorithm.
This is another algorithm that influences our life much more than we might think.
The set of algorithms that feed the Facebook Timeline determines the contents that will be displayed in the most visited space of the social network. Thus, based on a series of parameters (personal tastes, response to previous content, etc.), the algorithms decide which content the social network will show us and in which order it will do so.
3. High Frequency Trading Algorithms.
They circulate billions of dollars in the markets every day. These are algorithms used by many of the most important financial institutions in the world, which launch orders on the market based on the profit they expect to obtain, according to the market conditions at any given time.
To such an extent they are relevant that such algorithms are now considered to be dominant in markets and much more influential than human operators.
4. Algorithm of Round Robin.
Okay, this algorithm is probably much less well known than the previous ones, but it is widely used in the computer field. Have you ever wondered how a computer determines its priorities when it has to perform several tasks at once? Imagine, for example, that you have a word processor, a spreadsheet and a web browser open at the same time. In general, it can be said that this algorithm determines the amount of time that the CPU of a computer will spend on each of the processes in progress.
What is the future of algorithms?
Rather than thinking about the future of algorithms, some people would claim that the future belongs to them.
The algorithm is, in fact, at the heart of such potentially powerful technologies as artificial intelligence. Algorithms are already the basis of automatic learning technologies, or “machine learning”, thus surprising us every day with new features. If you are particularly interested in the subject of artificial intelligence, you can consult other previous articles on this subject in our blog.
Today, algorithms are behind technologies such as virtual assistants or autonomous vehicles. But what about tomorrow…?
And what do you think? Will algorithms ever take over the Earth? You can take part in this post by leaving your opinion in the comment section at the end of this article.
And may the altgorithms be good to us…
Are algorithms used in monitoring?
Of course.
Any monitoring software is full of algorithms inside.
The thing is, you don’t need to know them to get the most out of them.
Do you want to get the most out of a free monitoring algorithm?
by Pandora FMS team | Last updated Aug 27, 2021 | Community, Geek culture, Integrations, Tech
Interoperability in IoT; a key factor for its development
The transformative potential of the Internet of Things is obvious, and many companies are aware of this.
With the development of the new 5G networks, the Internet of Things will grow along the way, perhaps to the point of reaching figures as relevant as the $11 billion a year that McKinsey Consulting expects for this market in 2025.
But it won’t be easy. The Internet of Things is able to develop in so many areas and it has so many uses that its own diversity can be the main obstacle to its growth.
In an environment where countless devices of different types and technical profiles will operate (from household appliances to wearables, from autonomous vehicles to drones, among many others), manufactured by thousands of different brands (each with their own standards), developing the ability for them to communicate with each other will not only be a technical challenge, but also a matter of mutual consensus.
This is why the interoperability in IoT emerges as a major need for the development of the Internet of things.
In order to understand its relevance, let’s dig a little deeper into the concept. Interoperability is basically the ability for systems or components of systems to communicate with each other, regardless of their manufacturer or technical specifications.
For example, imagine that two IoT devices need to send each other any kind of information but are unable to do so because they “speak a different language”.
Imagine that the system that regulates the air conditioning of your home “speaks” in a language provided by its manufacturer and the one that controls the system for opening and closing the windows of your home only “understands” its own language because it has been created by a different company. They would be unable to communicate with each other and they would be unable to take action in a coordinated manner.
Or even more serious. Imagine that you are travelling in an autonomous vehicle and you need to communicate with other vehicles on the road to coordinate your movements and to be able to drive safely. What if they could not do so because of the incompatibility of brands which would make the exchange of information impossible? In this type of situation, even people’s lives could be put at risk.
This is the reason why interoperability is essential for the correct development of IoT. This is a problem that compromises the future of this technology and must be solved to allow its expansion.
And since this is a key aspect in evaluating the growth possibilities of the Internet of Things, we can ask ourselves: What is the current state of things when we talk about the interoperability in IoT?
The current state of interoperability in IoT and some attempts to improve the situation
If we look at the current state of things, we can say that the issue of interoperability can clearly be improved. The market is very fragmented, especially due to incompatibilities between brands, and a common effort is needed to reach common standards for communication.
The IoT philosophy is not exactly to create local, closed and limited environments. Exactly the opposite. The philosophy of IoT is to create a world in which millions of devices are able to communicate with each other in the best and widest possible way, without technical or commercial limitations, in order to make our lives a little better.
However, this is not an impossible task. It is by no means the first time that the leading technology developers and manufacturers have agreed to set generally accepted standards. Let’s think, for example, about the Internet, and how the homogenization of communication protocols has led to the growth of the network.
There are some initiatives to support interoperability in IoT.
One of them is, for example, IEEE P2413 – Standard for an Architectural Infrastructure for the Internet of Things, a standardisation project aimed at identifying similarities in IoT environments as diverse as intelligent buildings, intelligent transport systems or healthcare.
The other one is an EU project, called Iot-A, created to develop architectures that can be applied in different domains.
We also have the open source initiative called IoTivity, with over 300 members, including leading companies in the sector, which is aimed at guiding and promoting cooperation between companies and developers.
Or the so-called Industrial Internet Reference Architecture (IIRA), created in 2014 by some of the main operators in the market and focused on industrial IoT applications.
However, these are not the only initiatives. In such a diverse and insistent area, we believe that there have been multiple attempts at unification, but it is not yet possible to determine which standardization criteria will finally be chosen.
Final conclusions and a little IoT monitoring
The future development of IoT will depend to a large extent on improved interoperability, as we have already mentioned. And in order to achieve this, values such as cooperation and flexibility will be essential.
Likewise, when monitoring IoT devices, the flexibility of the monitoring systems will be something to be considered.
That’s why it is necessary to get to know Pandora FMS. Pandora is flexible monitoring software, which is capable of monitoring devices, infrastructures, applications, services and business processes. And it can also carry out IoT monitoring.
Do you want to know what Pandora FMS can do when it comes to monitoring IoT? Well, it’s easy for you. Just send us a message with all your questions. You can easily do this using the contact form at the following address: https://pandorafms.com/company/contact/
But before you do this and if you want to know more about Pandora FMS IoT monitoring, you can check out this link: https://pandorafms.com/monitoring-solutions/monitoring-iot/
What do you think about interoperability in IoT? Let us know down below by leaving a comment in the comment section. We will read all your comments and we are sure they will be helpful. Remember to share this article on your social networks like Facebook or Twitter. Thank you very much!
Do not hesitate to contact the Pandora FMS team. They’ll be happy to help you!

by Pandora FMS team | Last updated Jul 6, 2023 | Customer support
Providing good customer service is one of the main objectives of any company that wants to survive today. The user is a part of the digital transformation and has very powerful tools such as social networks and opinion websites. All this, along with a highly competitive environment, has made all kinds of companies and organizations work harder to build effective customer service departments that can solve problems and make users feel at home.
However, it is not easy to achieve this. A customer service department has a complex dynamic that includes many aspects, such as organization, direct contact with the user, stress management, etc.
Customer Service; Discover these 6 key concepts for improvement
Do you want to understand it better? Let’s simplify it! In this article we are going to summarize the keys of customer service in a small list of basic concepts in order to make it easier for you. Let’s do this!
Listen
Do you have elephant ears? They’ll do you good! When it comes to customer service, listening is an essential part of it. However, not only is it a matter of lifting your ears like a gazelle, but it also involves carrying out the necessary activities to help solve a problem.
That’s why the concept of active listening is so important. Active listening means staying focused on what the customer wants to tell us, being empathetic with them, showing them that we pay attention to their problem, and processing the message effectively, so that their query is clear to us in order to provide an effective solution.
Communicate
And how do you handle yourself with words? If listening is fundamental in the relationship with the client, communication with the client is equally so. When contacting a customer service department, the customer not only wants to tell a passive organization about the problem, but also expects a dialogue. A good communication with the user fulfills several objectives; on the one hand, it allows them to know that their problem matters to us and we are going to get down to work to solve it; on the other hand, it generates closeness and empathy; on the other hand, it allows them to clarify possible dark areas of the problem that could lead us to confusion. That’s why we talked about the importance of the active aspect of listening. It is not only a matter of hearing, but also of listening and communicating, in order to solve it (” which leads us to the next concept”)
Solve
That is the whole point. With a few exceptions, customers who contact a customer service department do so in order to solve a problem, rather than to tell someone about their life.
And problem solving involves several factors. It is already clear to us that we must listen and communicate to understand what we need. Once this is achieved, we will need good organisation to manage incidents properly.
Achieving good organization in customer service is not easy (especially when dealing with a large volume of contacts), but it can be achieved. A good structure, a very professional team and the use of technological tools will bring you closer to this goal. Keep reading and we’ll tell you more at the end of the article. We promise!
You must be very nice
It’s the other side of customer service, along with problem solving. Customer service is not just about cold, mechanical interaction with the user, but also about an emotional component that we must take care of.
Clients are people, they have a little heart, and they want you to treat them kindly. In order to please them, factors such as the politeness, kindness and professionalism of the members of your team will be crucial. Do you want to go a little deeper into the subject? In this blog we have already published some articles dealing with issues related to this topic, such as this one where we talked about emotional marketing or this one aimed at making customers feel better about us. Take a look at them and you’ll see…
Loyalty
Finally, we have the concept that summarizes one of the key objectives of customer service.
It’s nice to be loyal, don’t you think? Customer service is an obligation for companies (you can’t leave the customer unattended), but it can also play a positive role, such as ensuring that your users want to continue to count on you for many years.
Are you able to solve problems effectively, creating a good feeling and leaving them with a nice memory that makes them happier with your business? If so, you’ve achieved your goal: you’ve provided great customer service, improved customer loyalty and they may even have found a good reason to talk about your business to friends and family. What else could you ask for?
And this is it, we’ ve come to this point, with these 5 key concepts for customer service. But we had promised you something else, hadn’t we? You thought we’d forgotten? With these 5 concepts, we can find another one that is also fundamental: to organize.
As we mentioned before, organising customer service well is no easy task. Luckily, we live in the 21st century, which means that we have the Internet, mobile phones, sticks for selfies, and even some technological tools that can help you with the delicate task of customer service. One of them is Pandora ITSM.
Pandora ITSM is software that has, among other features, an issue management system (help desk software) based on tickets (ticketing), which is capable of assisting in customer service for companies and organizations.
Do you want to know what the Pandora ITSM helpdesk tool can do for you? Take a look right here: https://pandorafms.com/en/itsm/help-desk-software/
Or you can also send us any queries you may have about Pandora ITSM. You can easily do this using the contact form, which is found at the following address: https://pandorafms.com/en/contact/
The team at Pandora ITSM will be happy to help you!

by Rodrigo Giraldo Valencia | Last updated Aug 14, 2023 | Community, Howto, Servers, Tech
Monitoring Zimbra: with this tutorial you’ll find it quite easy to do
1. Context
1.1. What is Zimbra?
Loyal to our style, let’s get started by having a look at what Zimbra is. Zimbra is a product from Synacor, which offer us a fairly complete collaborative platform, which includes email, file exchange, calendar, chat and video chat, as well as empowering around 500 million email inboxes. Additionally, it’s worth mentioning that Zimbra Collaboration was built on an easy to implement platform with a great messaging and collaboration system.
Zimbra is likely to be implemented within the installations, in the cloud or, if you prefer, as a hybrid solution and even as a hosted service throughout any of the commercial solutions of Zimbra or services offered by Synacor. Zimbra’s solutions provide to their users the control of the physical locations in which their own collab’s information is allocated.
Apropos this last aspect, we could blame it on the growing interest in the location of the data by governmental authorities (or state authorities to be more all-inclusive) and also by the industries who are being meticulously regulated, as it is the case of medical organizations or financial companies.
A ‘file manager case’ it’s included in Zimbra Collaboration Server, which allows the user to:
- Save attached files
- Sharing files with other users
- Load documents
1.2. Other important features of Zimbra Collaboration:
Zimbra Collaboration Server includes Zimbra Mobile which offers to their clients Microsoft Exchange and ActiveSync. The information is always available, without the need of installing any clients, neither middleware applications. To make it clear: it consists of a complete communication solution which allows the clients to send (and receive) emails, to add and to edit contacts in Zimbra Mobile’s address book, using a global list of addresses or ‘GAL’, or create dates and meetings, as well as managing the tasks list.
Another relevant feature from Zimbra is that Zimlets and API give the clients the possibility to download and integrate new functionalities with the aim to customize Zimbra’s experience and, therefore, widen its performance. Zimlets, in particular, include integration with Salesforce.com and Webex.

Let’s have a look at another important characteristic: Zimbra Collaboration offers Zimbra Talk, which provides the users with collab text, voice, and video capabilities, integrated with the user’s interface of Zimbra. Regarding all this, we could say that all Zimbra’s functionality (except Zimbra Suite Plus and Zimbra Talk) are included in the principal product. Thanks to this, the clients don’t have the need to constantly buy additional products.
2. How to monitor Zimbra Collaboration Server?
To understand how to monitor this well-stocked and practical server, we have to consider the following:
2.1. Statistics and server’s status
To capture and show the statistics of the server, we count on Zimbra Logger package, which is useful for:
- Keeping control of the mailbox capacity.
- Tracking messages and creating night reports.
- Log files.
- Overseeing the MTA mail queue.
- Supervise, through an SNMP tool, the error selected messages with SNMP snapshots.
It’s worth mentioning, continuing with Zimbra Logger, that in the “Module Library” of Pandora FMS, we can find valuable information about Zimbra Collaboration, concerning specifically Zimbra Mail. Zimbra Logger has a useful and much needed set of tools aimed at the creation of reports and message tracking.
Despite the package Logger installation being optional, we recommend doing it. Otherwise, the status information of the server and its statistics won’t be able to be captured, as well as the message tracking won’t be available for us.
2.1.1. Environments with more than one server.
Logger is just enabled for one mailbox. Therefore, the host for the tool to monitor Zimbra is the one responsible for checking the status of each and every one of servers using Zimbra. Also, it’s in charge of displaying the information within the administration console of Zimbra. The information is updated every 10 minutes.
However, in an installation of several servers, we have to set the configuration files of syslog, in each server, so we can allow the logger to show us the statistics from the server in its respective console. In addition, it’s needed to enable the logger of the host. So, in case of not having this configuration set when Zimbra Collaboration Server was installed, we recommend doing it as soon as possible.
2.1.2.The statistics of the server
We must keep in mind that, to enable the statistics, we have to write in each server (in its root directory) the following: /opt/zimbra/bin/zmsyslogsetup , which will give us the possibility for the server to show us the statistics. What’s more, to log the remote computers’ statistics in the host’s Logger display, we have to enable syslog.
To achieve this, we can edit the log file /etc/sysconfig/syslog, adding -r to the configuration of SYSLOGD_OPTIONS, like this: SYSLOGD_options = “-r -m 0” . Then, we have to disable the syslog daemon and write the following: /etc/init.d/syslogd stop . Next, we will get the syslog daemon started again by writing: /etc/init.d/syslogd start . It’s important to mention that all these steps are not necessary for the installation of just one node.
2.1.3. Server’s status check-up
The section called “Server Status” lists all the services and servers, along with its status and, really importantly, when was the last time the status was checked for the last time. To better understand this concept, we’ll say that the servers include the LDAP, the MTA, and the mailbox.
In addition, the services include LDAP, MTA, SNMP, inbox, anti-virus, anti-spam, logger, and orthography corrector. Now, when it comes to starting a server (in case that it’s not already running), we can use the following command: zmcontrol CLI. As well, we could initiate and stop services through the administration console of Zimbra, inside Servers and, more specifically, in the tab called “Services”.

2.1.4.The server’s performance statistics
Something really important to bear in mind when it comes to monitoring Zimbra is the fact that the section “Server Statistics” show us several bar graphs, in which we can see the volume of the messages, the count of them, the activity of the anti-virus and information related with the spam. This graphical information can be seen within the last 48 hours and in periods of 30, 60 and 365 days. To be more clear about this, here’s a more in detail explanation:
- The count of messages shows us the amount of these, both the received and the sent ones, every hour, every day.
- The volume of messages gives us the information about the size, in bytes, of both types of messages, in the same way, every hour, each day.
- The anti-virus and the anti-spam activity show the number of messages which were checked by Zimbra, in both the search of the anti-virus and the anti-spam, as well as the number of messages which were discarded as “spam” and the ones which were considered a threat.
- The drive shows us the use of our storage and, also, the available space for individual servers. We can sort this information by the last hour, day, month and year.
Important: the anti-virus and anti-spam activity graphs, in addition to the count of messages, they do different recounts for several reasons. One of these reasons is because the sent messages can’t go through the filter Amavisd as it quite is the case that the architecture of the system doesn’t require for them to be verified. Another reason is that the messages are sent and checked by Amavisd in search for viruses and spam before being delivered to all the recipients.
We have considered important to give a brief explanation of what Amavisd is. This open source tool consists of a filter of content for email, which also implements the email messaging transference to decode them, as well as interacting with the external content filters to give us protection against viruses, malware, and spam. We’ll also mention that it could be considered as an interface between an email software, as MTA, and one or more filters of content.
Remember when we said before that Zimbra also has services which include LDAP, MTA, SNMP, inbox, anti-virus,etc.? Right, we can use Amavisd additionally to detect banned content or to capture syntax errors within the email messages. You can also quarantine and then release or store messages in mailboxes or in a SQL database. The last version of Amavisd is 2.11.0, which was launched in April 2016.
2.1.5. Message tracking
It’s possible to track a message which has been received or sent during the last 30 days. Each email has a heading which shows us the route it has had, from its own origin up to its destination. This information is used to trace the route of the email when there’s an issue with it. In this case, Zimbra’s utility, zmmsgtrace , can be executed to look for emails, filling the following attributes:
- Message ID:
-i [msd_id]
- Address of the sender (“From”):
-s [sender_addr]
- Address of the recipient (“To”):
-r [rcpt_addr]
- IP address from which was sent:
-f [ip_address]
- Date and time:
-t aaaammdd (hhmmsss)
To finish with this subsection, we can sum this up by saying that the heading of the email in Zimbra we can see it through the display offered by the web client of Zimbra Collaboration, in which case we can right-click on a certain message to select “Show original”. In case the messages are being displayed through the “Conversation view”, first we’ll have to open the conversation to see the messages, and then we’ll select the message we want to read.
2.1.6.Creating daily mail reports
When we installed the package Logger, it’s set automatically, in crontab, a daily mail report which contains the following information:
- The total number of messages which were handled by Zimbra MTA.
- The errors from the logs of Zimbra MTA Postfix.
- The delay (in seconds) for the delivery of messages.
- Information regarding the size of the message, in total and average of bytes for each message.
- The amount of returned deliveries.
- The majority of the active recipients’ accounts and the number of sent messages.
- The majority of the active senders’ accounts and the number of messages.
PS: The report contains all the data which we’ve just listed is called every morning, at the same time it’s sent to the email of the administrator.
2.2. Monitoring mail queues
To monitor Zimbra when it comes to the supervision of mailbox queues we know that if we have any issues with the deliveries of the mails, we can check the queues of sent emails within the administration console. For this purpose, we have to access the section “Mail queues monitoring”, to analyze if we can solve those issues, keeping in mind that when we open the queues, the content shown belongs to the delayed, active, received, corrupt and “waiting” queues. Also, we can see the number of messages, their origin, and destination. Additionally, if you want to read a description of the types of queues, we suggest you check Zimbra’s site on monitoring mail queues.
2.3. Monitoring mail storage
We can access the information about the mail storage, for all the accounts, through the administration console and, more specifically, in Supervision > Server Statistics > Mail Storage. Inside this last tab we’ll see the following information for each account:
- Assigned mail storage.
- Used storage.
- Percentage of the assigned storage used.
Be careful: when the assigned storage is completely used, all the messages will be rejected. Therefore, the users will need to free some space (by deleting emails) in order to receive those emails. Another option is to increase the assigned storage for emails.
2.4.Log files
The processes related to Zimbra create files for the majority of the activities of Zimbra Collaboration Suite. It’s not needed to check most of the log files as the most relevant logs appear, as well, in many main log files, being the case, for example, of Zimbra’s syslog (which specifies the activities of Zimbra Collaboration Suite MTA), Logger, Authentication, and Directory.
3.Concluding
Monitoring Zimbra is a relatively easy task, as long as we follow the steps closely to the recommendations we have shown you in this clear and simple tutorial. For those in search to complete this information, we propose you to check Pandora FMS to find additional solutions.
by Pandora FMS team | Last updated Mar 8, 2024 | Remote Control
Do the computers in your office roar like lions and burn like embers in the underworld?
Have your computers taken over the kitchen? Have your computers spent the morning drinking coffee and playing darts? What did you expect? Just like any other electronic device (from a car to a dishwasher), in order to function properly, computers need maintenance.
In fact, due to its importance and complexity, computer equipment maintenance requires special attention.
When approaching the different types of IT maintenance, two aspects must be considered:
- The maintenance includes both hardware and software of the computer. Both are very important and will decisively influence the operation of the system.
- The various types of maintenance can work simultaneously. In the case of corrective maintenance, it will act if the predictive maintenance or preventive maintenance are not able to anticipate the problem.
In this article we will discover the main types of it maintenance, and all about each one of them, and finally we will learn all about a tool that can be very useful in some of the tasks of IT maintenance. And be careful with those wild computers, please!
Predictive Maintenance
It is a type of maintenance that is carried out using diagnostic tools, in order to anticipate possible failures and to try to avoid them before they occur.
One of the most important ways in which this type of maintenance is carried out is through the monitoring of computer systems. This way, one or several operators control the proper functioning of equipment and systems, using tools such as monitoring software, to control all different types of variables, such as temperature of the CPU, battery levels or many others.
Preventive Maintenance
This is a very frequent type of maintenance, which is carried out in order to prevent possible failures and improve the functioning of a system, but also to lengthen the useful life of the different components of the system.
Preventive maintenance is useful in many aspects. For example, it decreases the number of system downtimes or it can reduce the number of repairs, and it can also detect weak points in the system that might affect its operation.
When we talk about preventive maintenance of software, we include operations such as the creation of backup copies, the freeing-up of hard disk space, the freeing-up of RAM memory or the scanning and cleaning of computers through antivirus.
When we talk about preventive hardware maintenance, we usually talk about two different types, which are tasks such as periodic cleaning of equipment and its components, or “active preventive maintenance”, which aims to ensure its durability by protecting the systems from possible environmental aggressions, for example, by separating the computers from areas with a direct impact of sunlight, this is known as “passive preventive maintenance”.
Corrective maintenance
This is the solution that must be applied when the predictive and preventive maintenance have not worked properly or when these have not been able to avoid the failure.
There are times when a computer or system fails (for example due to a hardware failure) but we want it to be operational again and in optimal conditions. Then this will include repairing or replacement operations, depending on the needs of each case.
One of the considerations to be made regarding this type of maintenance is that not only will it be important to solve the failure, but we must also determine what was the cause of it, in order to find the possible repercussions that might have affected other parts of the system and to prevent it from happening again in the future.
Evolutionary maintenance
This type of maintenance is not meant to correct or prevent possible failures, but to develop the computing resources that are available.
As you might already know, dear reader, technology is always evolving, and that means that the tools available and the needs of users also change constantly. With evolutionary maintenance, we want to ensure that computer systems do not become obsolete, but remain updated in order to offer the users the best technology options, depending on the possibilities of each company and organization.
This type of maintenance will include everything from software update tasks to the complete replacement of equipment or systems, depending on the needs.
Summary
And so far, we have looked at the main types of IT maintenance out there. As you can imagine, due to the complexity of this type of operations, this work is usually in the hands of professionals, such as system administrators or specialized companies, who offer maintenance services to companies, professionals or individuals.
Is this for you? Do you work in IT maintenance or systems administration? Then you should take a look at Pandora RC! Is your work related to these areas? Then, you might be interested in it, because it has different uses. And don’t forget that Pandora RC is looking forward to meeting you!
Pandora RC is a remote management system for computers (remote desktop software), which can be helpful in some of the tasks of IT maintenance, but also with many others.
Do you want to discover what Pandora RC can do for you? Great then! Take a look here: https://pandorafms.com/en/remote-control/
Or you can send us any question you might have about Pandora RC. You can do that, it’s quite easy, you just have to send us a message through the contact form that can be found at the following address: https://pandorafms.com/en/contact/
And don’t forget to leave a comment in the comment section down below, we want to hear your thoughts, what do you think about it maintenance? Do you work in it maintenance? If you don’t, then you might have learnt something new with this article! Want to find out more about it maintenance? Don’t forget to check our other articles about it maintenance! We have published many of them on this blog!
So don’t forget to check them all out! Leave your opinion down below, we look forward to hearing from you!
And don’t forget that…
The Pandora RC team will be happy to help you!

by Pandora FMS team | Last updated Mar 10, 2025 | Customer support
Are you a customer service professional? Do you work in this area in your company? Do you have a small or large business? Do you usually deal with customers?
When it comes to your business, at some point in your life you will have to deal with clients. And it is also very likely that you will have your own way of dealing with them, based on your personality or your experience. We know that you might already know this, but you can always learn new things. You should know that, there are some customer service techniques that can improve your ways of dealing with them. In this post we will talk about some interesting customer service techniques for you.
Feel, Felt, Found Technique (FFF)
This is a method, which is aimed especially at generating empathy between the agent and the client. There are three steps:
- Feel refers to the emotional connection that must be established with the client’s problem. You have to achieve this and let him/her know that you understand his/her situation.
- Felt is about letting the client know that you know how he/she feels, because you have also felt in a similar way in the past.
- Found is about letting the client know how you’ve faced this type of problem in the past and then you found a successful solution.
ELI5 technique
This stands for “Explain it like I’m five years old”. It consists of explaining a very structured message and using a very simple language with the client, in order to make it easier for him/her to understand the message.
This is a technique, which is widely used in the area of technical support, especially when it comes to assistance that involves asking the client to execute a series of specific steps. Due to the technical knowledge of the person who offers support in this customer service, it will be very useful to use clear and simple steps and to use non-technical words with the clients.
But you need to keep in mind that this simplicity must be limited when explaining specific technical instructions. The technique is not about treating the client as if he really were 5 years old…
Active listening technique
This one is about letting the client know that we are paying attention to the problem. This type of actions will have a double effect: on the one hand they will allow us to summarize the problem and clarify the main points, and on the other hand they will help us improve the client’s mood, since they will notice that their problem is important to us.
These types of techniques include all kinds of small practices in order to let the client know that we will take care of their problems.
One of them, perhaps the most basic one, is to agree repeatedly while the client talks about his/her problem, which will let him/her know that we are listening to them (this is a particularly important practice when it comes to telephone customer service).
Another one is to repeat the phrases of the client. This will be very useful when it comes to emphasizing some interesting aspects, and it will also show that we are paying attention.
Another great one is to make a brief summary of the situation. With this practice we will not only show that we have paid attention to the whole message, but we will confirm with the client that we have correctly understood that, and it will help us clarify any misunderstanding.
By the way, if you are interested in learning more about active listening when it comes to customer service, we already published a post about this. You can find it here.
Counselling techniques through questions
When a client gets in touch with you, the client might have a hard time explaining the problem or query.
You need to be quite specific about the kind of questions that should be asked, this will be a very effective way to achieve small victories, such as clarifying the situation, streamlining the workflow, and even creating a better feeling for the client.
For example, if the client cannot explain his/her problem, it can be very useful to guide him/her through questions aimed at explaining essential points, such as “when has the product stopped working?” Or “When do you usually hear those weird noises in your product “?
But, you need to know that due to our experience, from the very start of the conversation with the client we can already predict the cause of the problem. Thus, asking questions in order to know more about the problem can be quite effective in order to solve the problem faster. If, for example, we think that the product does not have any problem, but the user does not know how to use it, we can ask them questions about how they have used the product in order to find out if they have missed an essential step, which might be the origin of the problem.
These are some customer service techniques, but I’m sure that you, dear reader, know some more customer service techniques. Do you want to share them with the readers of this blog? You can do that by leaving a message in the comment section, which is placed at the end of this article. But you need to bear in mind that, before writing, you can spend a few minutes in order to learn more about a technological tool that can help you improve the customer service of your company or organization. We are talking about Pandora ITSM.
Pandora ITSM is a program that has, among other features, an incident management system (help desk software) based on tickets (ticketing), which is capable of helping you with customer service.
Do you want to know what Pandora ITSM can do for you? You can find out all about it by clicking here.
Or you can send us any question you might have about Pandora ITSM. You can easily do that by using the contact form.
The Pandora ITSM team will be happy to help you!
by Pandora FMS team | Last updated Jun 10, 2021 | Community, Geek culture, Network, Tech
What is Internet of things? Discover how it’ll change our world
Hey! Do you know what is Internet of Things? The Internet of Things, or IoT (which stands for Internet of Things) is the network of physical devices, vehicles, home appliances and other items embedded with electronics, software, sensors, actuators, and connectivity which enables these objects to connect and exchange data.
The Internet of Things is a buzzword when it comes to IT and new technologies, we all know that. We are pretty sure that you’ve heard about it. This term is everywhere. But what is Internet of things? Let’s answer that question now.
The Internet of Things will be a massive part of our lives and we won’t even notice it.
But what is Internet of things? Well, the concept of Internet of Things first appeared in 1999, in the vicinity of the Auto-ID Centre at MIT, and it was developed by one of its cofounders, Kevin Ashton, who subsequently expanded and supplemented the Internet of things during the following years.
But what is the Internet of things? Do you actually know? In order to better understand all about the Internet of Things and its scope we will go to Wikipedia. According to this,
The Internet of things would encode 50 to 100 trillion objects, and be able to follow the movement of those objects. Human beings in surveyed urban environments are each surrounded by 1000 to 5000 trackable objects.
In 2015 there were already 83 million smart devices in people`s homes. This number is about to grow up to 193 million devices in 2020 and will for sure go on growing in the near future.
In order to understand what this would mean, we will make the following observation: throughout history, most of the generated information has been in the hands of human beings. During the last few years, an important fraction of that information generated has fallen into the hands of computers. The expansion of the Internet of Things would cause a huge increase in both the volume of information generated and the amount of information shared, at levels never before seen in history.
How can we see the real consequences of all this? Let’s have a look at some examples:
- The domestic use and especially in the field of home automation, this is one of the first uses that comes to mind when we talk about IoT. Some IoT applications are already quite popular, while many others are still in development. Now you can, for example, turn on the heating through a mobile phone before you get home. But not only that, the IoT will allow the automation of new tasks. For example, your fridge will be able to discover your needs according to your tastes and order online so that you receive what you need as soon as it detects that your stocks are about to run out.
- Public services will reach an incredible dimension thanks to the IoT. The immense amount of data that is generated (coming, for example, from sensors distributed by the city) will improve the safety, transport or even health of citizens. For example, these will be used to measure the level of environmental pollution in a given area, or to detect accidents caused by a flood.
- At a personal level, and through the use of wearables, the devices that we will wear will acquire all kinds of functions. For example, the smart watch that you will carry on your wrist will be able to guide you inside a department store and lead you directly to the product you are looking for.
- At a business level, the IoT will be quite useful. From the field of marketing to industrial production, the number of IoT uses for the company will be endless, and this is something that we are currently witnessing.
And these are just a few examples. As the Internet of Things develops, new applications will be created, based on the idea behind the IoT: the exchange of information without human intervention (or with minimal intervention). In addition to this, technological improvements such as 5G and the next generation of phones will allow the operation of the IoT to be faster and more effective over time.
But, as you can imagine, an infrastructure that involves billions of devices running simultaneously will always be exposed to failures. And this is when good monitoring is needed. With good IoT monitoring it will be possible to control specific aspects, such as the status of the devices, their firmware version or their battery levels. In addition to this, one of the key factors when monitoring IoT will be flexibility, considering the diversity of devices and environments in which the Internet of Things will be developed.
And now, do you know what Pandora FMS is? Pandora FMS is a flexible monitoring software, which is capable of monitoring devices, infrastructures, applications, services and business processes. And, it is also capable of monitoring IoT devices.
The best way to learn all about the IoT monitoring of Pandora FMS is to ask our team who created it, don’t you think? For example, do you want to know what Pandora FMS can monitor? You can do that using the contact form that can be found at the following address: https://pandorafms.com/company/contact/
Our Pandora FMS team will be happy to help you!
So then, what is Internet of things? We hope we have answered question with this article. Do you want to find out more? Then check any of our other articles about monitoring, these are all published in our blog, and don’t forget to leave a comment in the comment section, what are your thoughts on the Internet of things? Do you think this will be useful? Do you think it will be worth it? And if you have read any of our other articles, which one was your favourite? We want to know!
Let us know by leaving a comment in the comment section down below, we look forward to hearing from you! Thank you very much.

by Pandora FMS team | Last updated Jul 7, 2023 | Customer support
As Bob Dylan, a man who sings, knows a lot and has a Nobel Prize, once said: “Times are changing”. But also, the way in which companies and customers are connected.
Although there are still “lifelong” customers, we now find a new category of customers who have a relationship with certain brands – which we might call “fans” – similar to the relationship established with football teams or bands.
Although these extremes are rarely reached, some customers have a real appreciation for certain brands and consider themselves “fans” of them. They defend them in opinion forums or promote them among their friends, and are even able to queue for hours to purchase their new products on the first day of their launch.
Turn customers into fans; 6 ideas to make them love your brand
Naturally, for any brand, this type of follower is a blessing. They are not only loyal users, but they promote it better than anyone else.
The problem is that getting users to feel this appreciation for a brand is not easy; it takes a lot of effort and work. Are you willing to do that? Do you want to see some ideas on how to turn customers into fans of your brand? Have a look….
You must offer the best product on the market (in order to turn customers into fans)
It’s obvious, but it’s also a good starting point.
Sooner or later, quality is valued. In addition to this, offering the best products not only reflects the value of the product itself; but for some people, it is an issue that affects their self-image and confidence. Many customers take particular pride in getting the best products they can find, and will often display them publicly.
And even if they don’t, even if your customers don’t link their personal image to the products they buy, offering quality will always be valuable. Provide a good product and your fan base will grow on its own.
Be different from the others
In order to be different from the rest of the brands, offering maximum quality will be one of the main ways to reach the heart of many users.
Some companies, the so-called “lovemarks”, have succeeded in doing this and have been able to make the public identify their brand with certain values or lifestyles.
Becoming a “beloved brand” is not easy; it requires a clear vision, great marketing, and years of good work. That being said, why shouldn’t yours be the next lovemark to hit the market?
Create loyalty programs
“Loyalty” is a nice word, but do you do anything to put it into practice? Loyalty programs can be very effective in linking customers to a brand.
Many companies have been using them for decades with good results. There are many ways to do this: point cards, membership discounts, etc. Think about the type of products you offer and who your regular users are; it will help you design a great loyalty program.
Think of the details
Do you offer free parking to your customers? Is your sales team nice and helpful? Do you give away gifts to your customers? Is your establishment always clean, bright, and sunny?
Details can mean the difference. These are ways to please the user, to bring small benefits or to make their customer experience more enjoyable. Don’t forget that and always pay the greatest attention. Any small detail can affect the love they feel for your company.
Use social networks
It is one of the best ways not only to establish bonds, but to maintain them over time.
Social networks are a direct contact between companies and users and, if you manage them with professionalism and dedication, they offer multiple benefits. For example, they create a habit in the relationship between the brand and its customers. And they also offer companies something as valuable as getting direct feedback from their users.
In addition to this, they allow the user to have many valuable actions. Both explanations about the use of products and articles of interest, including customer service. A good profile on a social network can make many users feel more attached to your brand.
Offer great customer service
In many cases this may be the key. The customer service involves people, so it has an undeniable emotional component.
Have friendly and diligent professionals, structure your service in an intelligent way, and provide your team with the necessary tools to do the job well. If you achieve all this you will be much closer to assisting your customers effectively and not only will you solve their problems, but you will leave them with a great feeling, which will deepen their attachment to your company.
Here are some ideas in order to turn customers into fans of a brand, but I’m sure you have some very creative ideas. Do you want to share them with the readers of this blog? That’s great! Just leave a message in the comment section at the end of this article.
But wait! How about taking a few minutes to get to know Pandora ITSM?
Pandora ITSM is a program that has, among other features, an issue management system (help desk software) based on tickets (ticketing) that can help you with customer service in your company.
In addition, it also has other very interesting features, including an inventory or a project management system.
Do you want to know what the Pandora ITSM helpdesk tool can do for you? Click here: https://pandorafms.com/en/itsm/help-desk-software/
Or you can also ask us any question you may have about Pandora ITSM. You can easily do this by using the contact form at the following address:
https://pandorafms.com/en/contact/
And don’t forget to leave a comment in the comment section down below on how to turn customers into fans.
The Pandora ITSM team will be happy to help you!

by Pandora FMS team | Last updated Jul 13, 2023 | Customer support
Digital transformation and customer service are concepts that are closely related. This is due to the fact that the customer is the focal point of the digital transformation.
Although the customer has always been important (and this has led to classic statements such as” the customer comes first” or” the customer is always right”), new technologies have provided the customers with tools that make them more powerful than ever.
For example, think of the opinion websites. Multiple studies show that a large part of customers are informed on these types of websites before making their purchases. And we must take into consideration that buyers’ feedback is what feeds these types of websites.
We can also take a look at social networks, where any comment -positive or negative- about a company or product- can become viral and end up reaching hundreds of thousands of people. A reaction can have a significant effect on a company’s digital sales or reputation.
With such powerful tools in their hands, the client is no longer just an important figure, but is also a key figure in the strategies of companies that are aware of the new era in which we live. Therefore, the power of technologies for the user must be taken into account in any approach to digital transformation.
Digital transformation and customer service: the two of them are bound to get along
At this point, it is inevitable to think that one of the services that will be most affected by the digital transformation in any business will be customer service.
If there is a key moment when it comes to determining the opinion a client about a company, it is the customer’s contact with the service. Keep in mind that when someone gets in touch with customer service, multiple emotional factors are involved.
First of all, we will find a different mood in the clients than their usual one. When a person contacts customer service it is usually because they have a problem with a product or service and problems generate stress, nerves and bad mood, especially when they pay for a product for which they have a series of expectations that are not being met.
Second, the interaction with the service itself has an emotional component, as the face-to-face treatment usually causes feelings that range from enjoyment to anger, depending on the level of satisfaction provided by the experience.
And this satisfaction will greatly depend on the loyalty or loss of the customer, as well as the potential publicity, both positive and negative, that can be passed on when the customer talks about our company with his or her family or acquaintances. Don’t you think that’s a good enough reason to take all this into consideration?
The digital transformation itself also affects customer service
But it’s not just the importance of customer service that makes this service a key issue when it comes to digital transformation. Similarly, the resulting changes also change the way customer service is performed. Let’s look at some examples:
Multi-channel
The time it takes to answer a customer’s complaints or needs by answering only behind a counter or over the phone is outdated. Today, users expect to have various means of dealing with companies, which results in multi-channel (or even omnicanality) when it comes to interacting.
Telephone and face-to-face contact, but also through e-mail, apps, social networks, chats, web forms and anything else that technology can offer. The options for customer contact are multiple and this increases but also makes customer service more complex, so it will be necessary to invest on more resources and better organization.
Customization
And the multiplication of contact methods is accompanied by an enrichment in the relationships between companies and customers, the possibility of getting to know them and of giving them a more personalized treatment. Because it’ s by no means the same thing to send a product to a physical store and then forget about the client than to sell through a website and see how he or she interacts with our company’s social networking profiles, leaves comments on our blog, fills out satisfaction surveys on our website, etc.
These are all means that technology offers to get to know our customers better and that, as a consequence, force us to give them a more personalised service so that we do not lag behind our competitors.
Technology
It is part of the concept of digital transformation. And when it comes to customer service, it is not just about the new technological possibilities available to the user in order to contact the company, but also about the technologies that the company can use to manage customer service.
Thus, there are currently many technological tools that can help improve the management of such a complex activity. Do you want to meet ours? It is about Pandora ITSM.
Pandora ITSM is software that has, among other features, an issue management tool (help desk software) based on tickets (ticketing), which can be very useful to help customer service in a digital transformation environment.
You probably already know how help desk tools work, but you might not know Pandora ITSM yet.
Pandora ITSM is software created by Artica Soluciones Tecnológicas, a young and dynamic Spanish company that has developed tools as powerful as Pandora FMS monitoring software. Don’t forget to leave a comment in the comment section down below! We will read all of them, and these will be quite helpful! Do you have any bad experience with customer service? Let us know right at the end of this article!
Today, some of the leading companies already have Pandora ITSM. Here you can find some of them: https://pandorafms.com/en/itsm/customers/
And here you can learn more about what the Pandora ITSM helpdesk tool can do for you: https://pandorafms.com/en/itsm/help-desk-software/
In addition to this, you can also contact the Pandora ITSM team and send us any questions you may have about the product.
You can easily do this using the contact form at the following address:
https://pandorafms.com/en/contact/
The Pandora ITSM team will be happy to help you!

by Rodrigo Giraldo Valencia | Last updated Aug 10, 2023 | Community, Features, Howto, Tech
Oracle GoldenGate Monitoring: Learn how to monitor this
What is Oracle GoldenGate?
Oracle GoldenGate allows the exchange and manipulation of data in a company, allowing decisions to be made in real time. It works with multiple platforms, while moving transactions that are committed to the integrity of the transaction, allowing a minimum overload in its infrastructure. It has a modular architecture, providing flexibility, while being able to extract and replicate selected data records, changes to DDL which stands for “Data Definition Language” and transactional changes.
Regarding DDL support, we know that certain capture or delivery configurations and topologies vary according to the type of database. From Pandora FMS, we recommend our readers to consult the documentation related to the installation and configuration of Oracle GoldenGate, for their respective databases, in order to obtain detailed information regarding the supported configurations and, also, about those features. It is important to know all this, before analysing all about GoldenGate monitoring.
GoldenGate supports several requirements, such as:
- Initial load and database migration
- High availability and business continuity
- Data storage and decision support
- Data integration
For those who want to obtain complete information about the processing methodology, feature, configuration requirements and compatible topologies, they should also check the Oracle GoldenGate documentation for their respective databases.
Along with this architecture and before getting into Golden Gate monitoring, let’s say that it can be configured for several purposes:
○ For extraction and replication of transactional operations of DML which stands for data manipulation language and changes in the data definition language or DDL (for compatible databases), in order to maintain an adequate data coherence of origin and destination.
- For a static extraction of data records from a database and the loading of those records into a different database.
- For the extraction of a database and the replication to a file outside of that database.
Oracle GoldenGate components
The components of GoldenGate are the following ones: Data pump, Extract, Control points, Extract files or Trails, Replicat, Collector and Manager.
The extraction process stands out due to the Oracle GoldenGate capture mechanism. In addition to this, the extract is executed in a source system or in a descending database or, if preferred, in both of them.
We can configure “Extract” in different ways:
- By changing the synchronization: It turns out that Extract captures the DML and DDL operations , once the initial synchronization has been carried out.
- With initial checks: for initial data loads, Extract captures a current and static set of data, straight from its source objects.
Method 1.
-
To extract captures from a data source, we can make Source Tables (when the execution is an initial load) and from the recovery records of the database or the transaction records (just like with the records of “Redo” of Oracle Data Base or, also of the audit records of SQL / MX). However, the actual method of capturing the records varies according to the type of database concerned in each case.
-
For example, Oracle GoldenGate for Oracle offers an integrated capture mode, in which Extract enters to interact, directly, with a database base registration server that, in turn, proceeds to extract the flow of Oracle transactions. From Pandora FMS, we recommend readers who wish to obtain more detailed information about the integrated capture, to click
here
Method 2. Another method is found in a third-party capture module, which provides us with a communication layer that passes data and metadata from an external API to the Extraction API. It turns out that the provider of the database, provides us with the components that, in turn, extract the data operations and proceeds to pass them to “Extract”.

Data Pumps
What is a Data Pump? It is an extraction group that is within the Oracle GoldenGate source configuration. When a Data Pump is not used, Extract should proceed to send the data operations that have been captured to a remote path in the target. However, in a typical configuration of a Data Pump, the so-called Primary Extraction Group proceeds to write in a record located in the source system. The Data Pump proceeds to read this path and sends data operations, via the network to a remote path on the target, while the Pump adds storage flexibility and of course, it also serves to isolate the (primary) extraction process from the TCP / IP activity.
In general terms, a Data Pump is capable of carrying out data filtering, conversion and mapping, but it can also be configured in “step mode”, this way the data is transferred without any manipulation. This way of passing, also known as “Pass-through mode” increases the performance of the Pump, since that entire feature that looks for object definitions is omitted.
For those readers who want to expand the information we have provided about Oracle GoldenGate, from Pandora FMS we recommend clicking on this link .
But how do we carry out Oracle GoldenGate Monitoring?
By using the information commands in GGSCI:
To see and analyse the processing information, use GGSCI. The following are the commands to see the process information:
- The command
INFO {EXTRACT│REPLICAT} group [DETAIL] shows us: execute status, control points, approximate delay and environmental information.
INFO MANAGER shows us: execute status and port numberINFO AL shows us INFO output for all Oracle GoldenGate processes in the systemSTATS {EXTRACT │ REPLICAT} group shows us the statistics on the processing volume and the number of operations carried outSTATUS {EXTRACT │ REPLICAT} group shows us the execution status, which is, start, execution, stop and abendedSTATUS MANAGER shows us Execute statusLAG {EXTRACT │ REPLICAT} group shows us the latency between the last record processed and the time stamp in the data sourceINFO {EXTTRAIL │ RMTTRAIL} trail shows us the name of the associated process, the position of the last processed data and the maximum file size
Important note: there are many other commands for Oracle GoldenGate monitoring. We recommend readers to check this link.
Oracle GoldenGate monitoring through the analysis of an extract recovery:
Limited Recovery is exclusive for Oracle. If Extract closes in an unusual way, when a long-term transaction is open, it may seem like it takes a long time to recover, when starting again.
To recover its processing status, Extract must perform a search through the online (and archived) logs, in order to find the first log for that long-running transaction. The further back in time for the start of the TRANSACTIONS, the more recovery time will be needed, and Extract may seem frozen. To avoid this and confirm that Extract is being recovered properly, we must use the SEND EXTRACT command with the STATUS option.
Thus, one of the following status annotations will appear, while we will be able to continue with the process as Extract changes its log reading position, during the recovery itself:
In recovery [1] : it indicates that the extract is being retrieved at its checkpoint, in the transaction log.In recovery [1] : it indicates that the extract is recovering from its control point, until the end of the road.Recovery complete : it means that the recovery has finished, while normal processing will be resumed.

Monitoring:
The statistics of Lag show us the Oracle GoldenGate processes, follow the rhythms of the amount of data generated by commercial applications. Through this information, we can diagnose suspicious inconveniences and adjust the performance of those processes. In order to minimize the latency between the source and destination databases.
Regarding Lag for Extract, the delay is the difference (in seconds) between the time at which a log was processed by Extract (according to the system clock) and the time stamp of that log in the data source . For Replicat, the delay is the difference (also in seconds) between the time when Replicat processed the last log (according to the system clock) and the time stamp of the log on the way. Now, to observe the delay statistics, we must use the LAG or SEND command in GGSCI.
It is very important to keep in mind that the INFO command returns delay statistics. However, in this case, the statistics are taken from the last log that was controlled and not from the current log, which we are processing. Also, this command is less accurate than LAG and INFO.
For Oracle GoldenGate monitoring, you need to control how Lag is being reported:
In order to specify the interval in which the Administrator is verifying the delay of Extract and Replicat, we must use the parameter LAGREPORTMINUTES or LAGREPORTHOURS. On the other hand, in order to establish a critical lag threshold and to force a warning message in the error log, when the threshold is reached, we must use the parameter LAGCRITICALSECONDS; LAGCRITICALMINUTES or, if preferred, LAGCRITICALHOURS . Let’s clarify, that these parameters affect the Extract and Replicat processes.
Now, to determine a threshold of delay, We must use the parameters LAGINFOSECONDS , LAFINFOMINUTES or, , LAGINFOHPURS . But, in case the delay exceeds the value that we have specified, Oracle GoldenGate reports the delay information in the error log. In case the delay exceeds the value specified with the parameter LAGCRITICAL, the Administrator will inform us that the delay is critical. If the delay is not critical, we are informed by a message. A value of zero (0) causes a message to be forced to the specified frequency, with the parameters LAGREPORTMINUTES or LAGREPORTHOURS .
We have talked about the most important tools for Golden Gate monitoring, but if you want to check some other methods such as Volume Supervision Processing, the use of the Error Registry, the use of the Process Report, the use of the File Disposal, Maintenance of Discard Files, Use of System logs, Reconciliation of Time Differences, then click here to go to the Official Oracle page . In addition to this, in Pandora FMS you will be able to find valuable information on server monitoring.
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
Or if you have to monitor more than 100 devices you can also enjoy a 30 days FREE DEMO of Pandora FMS Enterprise. Get it here.
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!

by Pandora FMS team | Last updated Aug 21, 2023 | Remote Control
In the antediluvian period, the Internet did not exist. We know right, can you imagine a world without Internet?
Imagine a world without social networks or email. Imagine that you have a problem on your computer but you’re not able to solve it on time because you lack remote computer support.
Maybe you don’t know the size of this problem. This brief example might help you.
Noah is a kind old man who has a long white beard who loves Nature so he lives there with his family. He has spent some time building an ark and now he organises in his Excel a list of animals and he needs to finish that as soon as possible. However, when he turned on his computer this morning, he received an error message on his desktop.
Noah is quite stressed and desperate due to the bad organisation with his animals.
These problems are quite annoying! Methuselah, the most experienced and closest computer scientist, is 3 days away from Noah’s ark, and Noah cannot wait that long. The sky is overcast and he needs to finish his Excel before it starts to rain!
Noah has a real problem, which could easily be solved with an Internet connection and remote computer support.
What is remote computer support?
Okay, you might have heard this term before, or perhaps you have never heard these words, but you can guess what these words mean. It’s about fixing problems (or providing a service) remotely. Here’s the proper definition:
Remote computer support is a service provided by computer professionals, in order to establish a remote connection between the technician and the client’s computer, which is affected by problems, these problems will be solved with Internet and with the help of remote access software.
Remote computer support allows you to solve multiple incidents in a computer, when it comes to software problems; remote computer support plays a lead role and it’s used by the professionals of the sector.
When it comes to the type of remote computer support, it can include services such as the resolution of incidents with the operating system, help with the installation of programs or the resolution of incidents that may arise with its use, and the resolution of problems generated by malware or assistance in the installation of peripherals. Thus, we can say that within its technical conditions, remote computer support can be quite wide and diverse.
What are the advantages of remote computer support?
The benefits offered by remote computer support for an individual or company are endless and this has a lot to do with offering a great service without travelling.
1. It’s faster
It is one of the biggest advantages. Remote computer support helps the professionals in charge and gives them the possibility of offering their clients fast assistance, since the travelling time is removed and the availability of the technicians usually is much greater. In the example we mentioned earlier, if Noah and Methuselah had had an Internet connection and good remote desktop software, Methuselah would have been able to connect to Noah’s computer and he would have solved his incidents in just a few minutes.
2. It’s cheaper
Since the travelling cost (in terms of time spent, fuel, vehicle wear, etc.) disappears, the professionals who are responsible for offering remote IT assistance tend to adjust their rates more than those face-to-face services. In our example, with a face-to-face service Methuselah would have charged Noah 3 bags of barley, but he could have reduced his rate to only one bag of barley if he had worked remotely.
3. It’s more flexible
Remote computer support offers more adaptability than face-to-face services. For example, many companies that offer this have a subscription per hour, which can be consumed depending on the needs that arise. So, if Noah had had this type of subscription, for example 10 hours, he could have contacted Methuselah again in order to help him with future problems with his computer.
How is the remote computer support provided?
When it comes to individuals, they usually hire one-off assistance with professionals or companies for this. On the other hand, if a company needs remote computer assistance services, they either do this with an external but trustworthy technical assistance service, or, if the company is big and they need continuous IT maintenance, they need to have a professional (this could be a systems administrator) or a service of their own that is part of the company and is responsible for solving all problems that may arise when it comes to computers.
Anyway, there are very useful tools that will provide a remote computer support service, yes; we are talking about remote desktop software.
By remote desktop software, we mean those programs that provide a connection between the affected computer and the one, which will solve the problem, and these must have an Internet connection. Pandora RC is one of these. Let us show you what why mean by Pandora RC
Pandora RC is a remote management system for computers (remote desktop software), which helps both companies and IT professionals.
Do you want to know what Pandora RC can do for you? Well, you should know that, in addition to remote computer support, you could also use Pandora RC to help you with other tasks, such as teleworking. Find out more about Pandora RC here: https://pandorafms.com/en/remote-control/
Or you can ask us any question you might have about Pandora RC. You can do that, using the contact form that can be found at the following address:
https://pandorafms.com/en/contact/
Don’t forget to leave a comment in the comment section down below, how would you use remote desktop software in your everyday life? Let us know! Did you enjoy this article? If you did, then don’t forget all the other articles we have already posted about this subject!
Oh, if you have already read these, then which one was your favourite? Do let us know! We are looking forward to hearing from you!
Thank you very much! And… Don’t forget to send us your questions!
The Pandora RC team will be happy to help you!
by Jimmy Olano | Last updated Jul 27, 2023 | Community, Geek culture, Integrations, Tech
This article was first published in 2018, some technical aspects may be outdated.
Continuous Integration Software: Learn all about Jenkins
In a previous post we explained all about Continuous Release of Software and today we will see the previous step: the Continuous Integration of software but from the point of view of automated tools . We chose Jenkins for didactic purposes since it is written as a free software license and it is very flexible, just like Pandora FMS.
First of all, we will talk about some practical tips to contrast it with Jenkins, which will also work for any other similar software such as Buildbot or GitLab CI or even more advanced tools such as Concourse or Drone(in fact, there is a Jenkins plug-in for Drone) thus combining Continuous Integration and Continuous Release of software.
Continuous Integration (Change is the only constant)
Continuous Integration is hard to implement but once it is ready, programmers always wonder: how did we manage to live without this in the past? In order to explain its operation, we must briefly look at what a software repository and a version control system are.
How does a software repository work?
A software repository gathers all the necessary files so that a program or system can be compiled or installed on a computer. If a version control software is responsible for its administration, then we will have the perfect combination for a new programmer to start working on the code development (this is known as process chain).
Nowadays, the most widespread version control system written in free software is Git, which allows us to have a distributed copy of all the code used in an application or project. So a new employee can obtain a copy of the whole project, make the modifications in that copy, and once completed, the employee is able to perform compilation tests (convert high-level language with low level language or machine language) and the employee is also able to test databases or data processing.
Once you know that everything is fine, we will have to check if the project has been modified, in this case it will download (automatically) modified files and a summary will be submitted if these updates affect the work that you have just made. In this case, it will correct, assimilate and combine the new code (this usually happens when two programmers work simultaneously in one code)
After all this, it will compile and it will try again and finally it will “upload” its contribution to the repertory, but wait, there’s more: and now let’s say hi to Jenkins, this is the software that will be responsible for carrying out the tests automatically and once approved, its work will be finished (and then the cycle will be repeated).
Tips for the Continuous Integration
We have collected the best tips in order to obtain the best results in the Continuous Integration of software; don’t forget to leave a comment in the comment section if you think there’s something missing.
- Place everything in the main repository: Excepting credentials, passwords and private codes. Everything else must be in the repository, the source code and the test scripts, property files, database structures, installation scripts and third – party libraries. Programmers should be warned that temporary files or collections made by programming environments (which are easily recognizable by their file extensions) are not “uploaded” to the main repository.
- A main trunk with very few branches: Going back to the example of the new employee as a programmer, it is good to create a development branch to assign a job, perhaps, in order to correct a bug. This branch must have short duration and then it must be added to the main trunk, and it will even be tested twice with Jenkins.
- Discipline: The work of programmers must be carried out accurately and it must contribute to the repository as often as possible.
- The Golden rule: The longer the time spent without compiling, the harder it will be to find the bugs , and in the worst possible scenario these could overlap with each other, thus making it difficult to detect them.
- The compilation tests must be quick: Around 10 to 20 minutes after uploading the contribution of the programmer, an approval or rejection must be issued, graphically on a web page or by email. In order to achieve this, we must look at special considerations as soon as we look into Jenkins.
Automating processes with Jenkins
Our Continuous Integration of Software, when applied to our chain of processes, must set us free from the work of pre-compilation, compilation and even installation (creation of databases, configuration of predetermined values, etc.). For this, Jenkins, which is software whose logo shows an English butler who is ready to help us in our daily lives, is written in free software under the permissive MIT license and it runs on GNU / Linux.

It was formerly known as the Hudson project and it was made with the Java language, it was created by the company Sun Microsystems in 2005 and eventually it became the property of the Oracle company. With the privatization of the company, Jenkins was born in 2011.
It’s quite easy to install: you need to add the public key from your website, and then add it to the list of repositories and then install it from the command line. Jenkins offers a web interface, therefore we need to install Apache or Ngix as a web server as well as an email engine for notifications, and once enabled it will let us install the main plugins in order to work.

For Jenkins, most things are plugins, including the chain of processes. Due to the amount of plugins that are available, it is difficult to replicate Jenkins environments on other computers. We can confirm our Continuous Integration through the Apache Groovy language, which is derived and simplified from Java or you can create those you need through the web interface.

Here, we get to see the versatility of Jenkins: we simply create, using a Plugin, a folder or directory called Pandora FMS to store there the customized files related to the Continuous Integration process, but not the source code itself. Then we must make a practical use of it: if we have our hosted project on GitHub, by using a plugin, we can specifically tell our user ID (and password if the code is private) and in one or two hours Jenkins will take care of analysing our repositories through the API of GitHub (in fact this API limits the use by time, that is why Jenkins takes so long when it comes to downloading, respecting the “rules of etiquette” when it comes to the use of resources).
Declaring our identifiers in our source code
Once Jenkins is connected to our repository and the analysis is done, we will see the following :

For example, if we use Python language we must include the following file with the extension “.jenkins”:
/* Requires the Docker Pipeline plugin */
node('docker') {
checkout scm stage('Build') {
docker.image('python:3.5.1').inside {
sh 'python --version' }
}
}
Jenkins needs this in order to create an environment contained in Docker , a software that consumes fewer resources than a virtual machine and offers the same advantages, thus Jenkins can create a test scenario for the specified language and it can run python–version .
Specifying our tests for continuous integration
Now we will add our scripts and although it will take a while to create them, this way we will save a lot of time since it automates the tasks of compilation and testing. Here we have an example on how to instruct Jenkins in GNU / Linux with sh :
pipeline {
agent any stages {
stage('Build') {
steps {
sh 'echo "Hola Mundo"'
sh ''' echo "Múltiples líneas permiten escalonar el trabajo"
ls –lah
'''
}
}
}
}

Private environments also have support, for Microsoft Windows we will use the bat process:
pipeline {
agent any
stages {
stage('Build') {
steps {
bat 'set'
}
}
}
}
Likewise we will make the respective scripts thus allowing each programming language to execute the respective compilers, just to name a few (free and privative):
Hardware for our battery of tests
Today hardware has lagged behind compared to virtual machines; we can run several of them with only one computer. Jenkins needs an infrastructure in order to do its work in a few minutes and now we want to recommend the following:
- A local area network: which must be well managed and planned (automated) with PHIpam .
- A repository of Operating Systems (OS): with ISO images of the OS needed, as well as a repository and/or proxy server with updates for them.
- We must have a manual integration machine: a human being must corroborate Jenkins‘ daily work.
- We must have one or several machines with accumulated compilations: especially if our project works on several platforms or operating systems, we will then make the necessary scripts to partially compile the integrated differences throughout the day, at a first level, this guarantees us fast approvals of Jenkins.
- Several machines for nocturnal executions: on “clean” and also “updated” OS but these must not have received our project (we will make scripts for these cases too) obtaining approvals at a second level.
- Machines with heavy software, which is already installed, and stable: such as database, a Java environment or even web servers, in order to be used by the rest of the computers that carry out tests.
- Model integration machines: which are configured with the minimum, recommended and maximum hardware that we officially recommend for our project.
- Identical machines (as much as possible) to the servers in production: same amount of RAM, cores, video memory, IP address, etc.
In all these scenarios, we can draw on virtual computers, in order to test in real machines through the Continuous Implementation of software.
At this point we recommend Pandora FMS on the issue of monitoring the continuous integration of software as a way to measure the stress on the systems with our new project that is installed. The fact that this is correctly compiled and installed it does not mean that it is doing what it should be doing; in fact in Pandora FMS we offer the Pandora Web Robot (PWR) for web applications and Pandora Desktop Robot (PDR) for desktop applications and in order to test those scenarios with detailed and accurate reports.
Conclusion
As you know, software development in the 21st century is in the pre-stage of software creating software, but that already enters the field of artificial intelligence.
Meanwhile, nowadays, in Pandora FMS from version 7.0 (Next Generation) we use rolling release and we adapt to new technologies thanks to our flexibility, do you want to find out more? Click on this link: https://pandorafms.com
Do you have any questions or comments about Pandora FMS?
Get in touch with us for more information: https://pandorafms.com/company/contact/

by Pandora FMS team | Last updated Aug 22, 2023 | Geek culture, Remote Control
Have you seen the horrible look of the desktop of your computer?
The shortcut icons to the work software are mixed with the photos of your last holiday in Ibiza and videos of funny cats. And then you find yourself complaining about those files that you cannot find and then you spend all day wasting your time with the search engine of your operating system. Now, you know why this happens.
Why is it important to have an organized computer desktop?
Having a messy computer desktop is quite similar to having a messy physical desk, and it is quite annoying. We know that at first this might not seem like a big problem (and indeed, there are bigger ones), but it can cause you more inconveniences than you might think. Do you want to find out some of them?
- If your computer screen is full of desktop icons, it will take more time for your computer to start.
- It will take you more time to execute some of your tasks, while you look for the files on your desktop or in the depths of your computer and some of them might not even be there anymore.
- That feeling of disorder will increase your stress.
- If you have to use your computer in front of a client, perhaps to carry out a demo, you will give a negative impression.
These are some great reasons for you to spend a few minutes to organize your desk better, don’t you think? In this article we will see some ideas to achieve that. Let’s find out some more ideas!
1. Be careful with the wallpaper and get ready to organize desktop
Yes, we already know that you love these multi-coloured rotating mandalas, but perhaps this amalgam of shapes and colours might not be the best option for your wallpaper.
The best wallpapers are the simplest. Not only will these facilitate finding your files, but also you will be much more relaxed when working. Bear this in mind… it’s quite important
2. Reduce the amount of desktop icons
Yep, it is not necessary to have a direct access to ALL the programs that you have on your computer. The usual thing is that in your everyday life you will only use a part of the software that you have, so choose the icons that give access to the programs that you will use and eliminate the others. Remember that to access the software that you’ve installed, there’s also a start menu, so you don’t need to have everything at the same time on your desktop.
What can you actually have in your desk? Well, those files that you will defnitely use at the moment. But of course, remember to store these if you are not going to use them immediately.
3. Identify the files properly
If you name your files with the default name established by the software (for example “My document 1”, “My document 2” or “Invoice 5873”, “Invoice 5123”) you will have a hard time identifying these and finding them when you need them. You need to get used to putting a representative name every time you save them for the first time. You will see how your life improves and that rage that you get every time you look for a file, will be gone.
4. Create folders to sort your files
It is another way to keep a great amount of files close to you, but these have to be ordered properly and shouldn’t be visible on your desktop. Create folders, choose the name you want to give them and place there those files. You can create, for example, one folder for files related to your work, another one for photographs, etc. And within these you can also create subfolders, if you want to increase the order.
Another good habit that you can have is to create a folder in which to store everything you download from the Internet and without a particular folder. Configure your browser so that the content you download will be downloaded in that folder and you will see how you find everything faster and the number of icons on your desktop will be reduced reduced.
5. Use programs to manage desktop icons
Whatever the operating system, there are multiple tools created to organize desktop and the icons. From those that allow you to return the icons easily to their original position, to those that appear or disappear from the desktop with a simple “click”, and also those that create floating windows. Investigate on Internet, there are great options out there
6. Create more than one desk in order to organize desktop
There are programs that allow you to manage desktop icons; and there are programs that can generate several different desktops on your computer. You can create for example one for work and another one for leisure, and choose between these depending on the needs of each moment. Remember that your clients don’t need to see those funny videos…
So far, these are 6 ideas to organize desktop in your computer so that it doesn’t look like a battlefield, but I’m sure you know some more. Do you want to share them with our blog readers? That would be great! You can do that by using the comment section that you can find at the end of this article.
And don’t forget to leave a comment in the comment section down below; we are looking forward to hearing from you! We want to hear your thoughts!
Thank you very much!
But before that, take a few minutes to find out all about our nice and useful tool called Pandora RC. Have you ever heard of it?
Pandora RC is an amazing program for remote management for computers (remote desktop software), which can be used for tasks such as remote computer assistance, remote customer service or teleworking, among others.
Do you want to find out what Pandora RC can do for you? Click here: https://pandorafms.com/en/remote-control/
Or you can also ask us any question you might have about Pandora RC. You can use the contact form that can be found at the following address:
https://pandorafms.com/en/contact/
The Pandora RC team will be happy to help you.

by Pandora FMS team | Last updated Aug 27, 2021 | Community, Geek culture, Network, Tech
5G. What is it? When will it arrive and why do we need this now?
The term 5G stands for “Fifth Generation“. As you may guess by the number 5, there have been previous generations, we find ourselves surrounded by the 4th generation at this very moment, but things are about to change.
Okay, we are pretty sure that you have realised that in the phone world things have changed quite a lot over the past 10-15 years. Not long ago, mobile phones were slow and heavy and did not have Internet access. If we look back in time, we, as humans, used to use horse-drawn carriage and we used to wear clothes that were not very good-looking but quite useful and practical, like robes. If we keep going back in time, we will find that time when we used to paint with charcoal in caverns and that roasted mammoth used to be a delight for the most refined palates. Oh wait; let’s get back to mobile phones.
In times of 1G (first generation), back in the 80s, the technology was mainly analogue and there was no international standard, but it depended on each country.
The first standardization that reached more than one country – called GSM – emerged in the European environment in the 90s, and it gave rise to the Second Generation (2G). A few years later, it was clearly insufficient due to its slowness – it was only intended for the use of voice and SMS – and it was followed by the Third Generation (3G), also called UMTS, at the end of the 20th century, which introduced the use of the internet on mobile devices (at low speed, of course).
About ten years later, around 2009, a new evolutionary leap took place in response to the demands of consumers; therefore the Fourth Generation (4G) was created, also called LTE. This is, the one we use today, which represents a substantial improvement in the speed of data transmission.
And now, you might be wondering, why do I want a higher transmission speed if I am already able to watch videos of dancing dogs on YouTube? And more important, when will 5G be around us?
Why do we actually need 5G?
Although the current technology already allows us to watch videos of dancing dogs at a great speed, the technologies that we will see in the upcoming years, will demand a new standard that will turn into a significant increase in the speed of data transmission, in the amplification of frequency bands and in the reduction of latency. What does this mean?
Bandwidth amplification is very important in relation to the reduction of interference. In the upcoming years, thanks to the Internet of Things, the number of devices connected to the network is expected to be multiplied by more than 10 (Huawei, the brand, estimates that around 100,000 million devices will be connected to the Internet Network caused by the IoT by 2025). 5G will operate in a bandwidth wider than 4G, which will enable a greater number of connections without interference, and will make it possible for cars, appliances or wearables to be connected to the network without interruptions.
Equally important or maybe more is the matter of decreasing latency. When we talk about latency we refer, roughly, to the time that a device takes to request information and receive it. Probably, this is not that important if we talk about watching videos online, but for some technologies such as autonomous vehicles, the response time will be vital. Regarding to this, 5G is expected to reduce the current latency time by approximately 10 to 50 times (up until about a millisecond), which can be the point of difference between life and death when talking about a vehicle that moves at a speed of 100 km/h.
For some people, 5G will be the basis on which the long-awaited Fourth Industrial Revolution will be based, which will transform the life of human beings in a way as never seen before.
The importance dimension of 5G can only be seen today. We can already imagine what will happen when telephones, computers, wearables, vehicles, appliances, buildings and millions of sensors of all kinds connect with each other to share information, but, until then, we will not be able to know the change that this will imply in our lives.
When will 5G arrive?
In order to answer this question, we need to bear in mind that nowadays there is still no 5G standard, so an exact date cannot be established. However, the deployment is expected to begin around 2020, which will probably coincide with the celebration of some sporting events, such as the Olympic Games that will be held in that year in the Japanese city of Tokyo.
However, the development of the 5G standard faces many difficulties. For example, it is necessary for all countries to agree on the bandwidth that will be used.
In addition to this, just like it happened when establishing previous generations of mobile telephony, the deployment of 5G technology is expected to be uneven between countries, it will probably start in the most developed countries of Asia and the United States, and then it will move to Europe and then it will be in other countries of the world.
Conclusion
We can say that even though previous generations of mobile technology were aimed at people, 5G will mainly be used by machines. Millions of devices will connect with each other to receive all kinds of information which will make our lives easier. By the way, someone will need to have control for all those devices to work properly, don’t you think?
While we await the arrival of 5G, we have to remind you that monitoring is already very useful today in order to control the proper functioning of devices and infrastructures, applications, services or business processes.
Do you know Pandora FMS? It is a flexible monitoring software that will adapt to your needs.
Learn more about Pandora FMS by clicking here: https://pandorafms.com
Or perhaps you want to find out what exactly Pandora FMS can monitor. In order to find out all about it you can ask our Pandora FMS team. How can you do that? Well that’s quite easy, you can do that by using the contact form that can be found at the following address:
https://pandorafms.com/company/contact/

by Pandora FMS team | Last updated Aug 22, 2023 | Help Desk
They are as essential as water is for plants. As the seasoning for a dish. As the bulb for the lamp. As the night for the day.
But enough with the metaphors! If you own a business and you don’t have clients, you have it tough. That’s crystal clear, and you don’t need poetic constructions to understand it.
And even if you have your clients, many of them, nice and smiley, surely you want more, right? Although the task of earning more users for your business is not always easy, as it covers different factors to keep in mind, and because you face competitors avid to get hold of them as much as you.
Client portfolio: 5 useful ways to make it grow. Don’t miss them!
In this article, we are going to see some ideas to turn your business portfolio into an attractive and brimming one. Let’s dive in!
Offer the best products or services
I know this one seems a bit obvious, but, probably, you have stopped thinking about it, and you might have forgotten about it. When businesses reach a certain level of experience and their products have excelled and they sell well, it’s easy to get too comfortable here and fail to remind yourself that you can improve even more.
Some of us we know it well and think about this constantly. Have you heard of the Kaizen method? It’s a philosophy with an extensive record that advocates for continuous improvement. Because, even if you are good, you can always be better.
If you offer the best products and services, and you do it in a well-balanced way, you’ll receive a steady income of clients. Try it yourself and you’ll see how the effort is worth it.
Don’t forget about advertising
Just because it’s traditional or because it involves an economic investment, you should not discard it. If advertising has been in the game for decades and still is, it’s clear that it’s due to the effectiveness to reach new potential clients. While, for some business, is its main way to get them, others try to reduce their investment in advertising to the bare minimum, more often than not for economic limitations.
The amount of money placed to invest in publicity will depend on the necessities and possibilities of each company. Nonetheless, notice that nowadays, thanks greatly to the Internet, there are advertising options of all kind, which allow you to target the audience you want to reach and be more flexible with the quantities of money that you’d like to destine to promotion. Think carefully about all the available options and remember that this is an option for you to reach new clients.
Create new products or services
Is one of the ways in which you can grow your business and therefore your business portfolio (or vice-versa). New products will lure new clients who might not be interested in what you were offering in the past but would be interested in an innovative and quality new product that your company launches.
In addition, another good option could be to give a twist to your already existing products. Could you give them a new approach and modify them so they are of the taste of members of a niche market different from the one you’re currently in? Maybe you’re actually quite close to being liked by a new and numerous group of people with just a few little changes and you haven’t realized already.
Step up your digital strategy
You might have already an online presence (if you don’t have it already, you have a lot to work at) but, do you have all the presence you need?
These days, for many companies the net is a channel for new clients to arrive that can’t be overlooked. You may have your webpage by now, but you must know that there are many other ways to turn into clients the millions of people who lurk around the net. Profiles in social media, blogs, inbound marketing… There are many different media which didn’t exist a couple of years ago and, every day, new ways of getting to know new products and services appear. Don’t ignore them!
Provide an amazing customer service
Customer service does not just allow us to keep clients that we already have (which also contributes to maintaining the volume of our portfolio), but can also be one of the best ways to attract new clients.
An amazing customer service experience sets a good image of our business. It lets the users know that we are there if any problem comes their way and that we care to give them the best service possible. If we achieve this goal of providing such a great service, it’ll be much more likely for our clients to be satisfied, and something interesting about clients is that they use to have friends, acquaintances or family to whom talk about their life, which can be quite positive if they pass on the great customer service they had had without company.
Seriously, customer service is one of the best ways of indirect advertisement that a business can access. Never forget about this!
And now that we’ve seen 5 ways to increase your client portfolio, why don’t you spend some time to know Pandora ITSM? It’s a great idea, doesn’t it? Maybe not, but that’s because you still don’t know what it is…
Pandora ITSM is a software which provides, among other features, an issue management helpdesk based on ticketing which can help you to improve the customer service of your business.
Why not have a look and get to know the helpdesk tool that Pandora ITSM offers? It’ll just take you a couple of minutes. You can do it on here: https://pandorafms.com/en/itsm/help-desk-software/
In addition, Pandora ITSM provides you with other tools that you may find interesting, as an inventory, a project management system and a vacation manager, among many others.
Would you like to ask us anything about Pandora ITSM? You can easily do it by using the contact form that you’ll find at the following address: https://pandorafms.com/en/contact/
Pandora ITSM’ team will be pleased to answer you!

by Pandora FMS team | Last updated Apr 1, 2024 | Community, Servers, Tech
Dynamic thresholds: some characteristics of dynamic monitoring
A threshold is a value used to change from one state to another in a check and dynamic monitoring is used to automatically adjust the thresholds of module states in an intelligent and predictive way. When the thresholds are defined by dynamic monitoring then we are talking about dynamic thresholds.
Depending on the threshold, a different state is defined; this way we will be able to find out the state of our check. Therefore, the state of the different checks will depend on these thresholds and from this information, we will be able to find out if the server, process, application or network element are working properly and we will also be able to find out if there is any anomaly or incidence so that we can launch the corresponding alerts in order to solve it.
Internally, at a low level, the operation of dynamic thresholds results in a collection of the values of a given period and a calculation of a mean and a standard deviation. It is necessary to establish a period so that the monitoring system can learn from the data collected, and also should be able to analyse which values are below or above the average and thus it will help us assess whether there are possible incidents in our IT infrastructure. If we give it a low learning time, such as five or ten minutes, the system will only have recent data so it is advisable to set a period of time of days or weeks so that more values are considered when performing these calculations to obtain the dynamic thresholds in a more solid way, through a greater number of values. Once the calculations have been carried out with the obtained data in order to obtain both the mean and the standard deviation, these are used to establish the corresponding dynamic thresholds in the modules automatically. These thresholds change, depending on the data that has been collected, the recalculation is performed, therefore, thresholds vary and adapt themselves to the new reality by applying the intelligence mentioned above about the data.
Under these premises, we obtain the following advantages in our monitoring tool when applying dynamic monitoring:
- It applies the thresholds automatically. The main feature is that once it has learned from the data collected in the defined time, thresholds are automatically applied in those modules we want, it is not necessary to define the thresholds manually. This task is automated and it is also customized according to the values of each module, which leads us to think about intelligent monitoring.
- It recalculates the thresholds. The system recalculates thresholds from time to time based on the information obtained, therefore these are updated with the values received.
- It provides flexibility when defining thresholds. Although dynamic monitoring is focused on automation, it is also possible to manually adjust a dynamic range in order to give greater flexibility to those automatically generated thresholds.
Once we have seen its operation and the advantages of monitoring our infrastructure using dynamic thresholds, we will put it into practice by looking at some examples.
Monitoring the web latency
We define a learning time of 7 days (a week) in the module:

Once the indicated configuration has been applied, the following thresholds have been defined:

This module will change its status to warning as soon as the latency is higher than 0.33 seconds and to critical state as soon as it is higher than 0.37 seconds. We represent these changes on the graph in order to see the action that will be carried out:

We can refine this more, since the threshold has been set high due to the peaks included in the monitoring. It is possible to reduce it by 20% so that alerts are triggered with a lower threshold. We will modify the values of the Dynamic Threshold Min. Field using a negative value so that the minimum thresholds fall. As there is no maximum value, since it will be considered critical from a certain time on, we do not have to modify the Dynamic Threshold Max:

After applying the changes, the thresholds have been recalculated, in this state:

Now, the graph looks something like this:

By applying the dynamic thresholds we have managed to define the thresholds, in addition to that, we have verified that apart from the calculation that is made to obtain the thresholds depending on the time, we can dig deeper and manage to adjust the changes of state even more according to our monitoring needs.
Monitoring the temperature in a CPD
The temperature in the CPD must be controlled and stable, so if you consult the monitoring graph, you will see the following information:

As you can see in the image, it is a linear graph that is always placed between the same values, it shouldn’t have sudden changes, which means that it shouldn’t rise or fall too much.
In this case we wanted to adjust the thresholds as much as possible, so we have manually defined a dynamic range with the following information:

We have enabled the “Dynamic Threshold Two Tailed” parameter to define thresholds both above and below. These are the dynamic thresholds generated:

These are shown in the graph:

This way, we are adjusting as much as possible to the temperature desired for the CPD, between 23 and 26 degrees. By looking at the graph, we can analyse that everything that is in the range between 23’10 and 26 is considered normal. Everything that goes beyond these thresholds will trigger the alerts.
The Pandora FMS monitoring software has dynamic monitoring
It establishes dynamic thresholds in the modules so it is not necessary to be aware of the definition of the thresholds for alerts and events. Let Pandora FMS do it for you.
You can find out more information about dynamic monitoring in Pandora FMS in the following link.
Our Pandora FMS team will be happy to answer your questions.
If you were interested in this article, you can also read: What is alert fatigue and its effect on IT monitoring?

by Rodrigo Giraldo Valencia | Last updated Aug 21, 2023 | Servers, Tech
Do you already know the best antivirus software for Windows 10 in 2018?
From Pandora FMS we don’t recommend our readers to download the most popular antivirus on the Internet, because its popularity or good reputation might not translate into effectiveness. Malware, spyware and adware are becoming increasingly sophisticated and many of those antivirus that you see online, might not protect your computer as they should. Just like biological viruses, computer viruses can mutate and might become resistant and powerful. Therefore, we will look at the best antivirus for Windows 10 in 2018.
When it comes to antivirus, the best thing to do is to check with independent antivirus laboratories, such as the German AV-Test Institute. This one is known for working 24 hours a day and hunting more than 6,000 million viruses. Other independent laboratories, whose opinions have been considered, are the MRG-Effitas and the Simon Edwards Labs (which is the successor of Dennis Technology Labs), in addition to the West Coast and the ICSA Labs.
It is important to know that when it comes to virus and antivirus, the great reality is that malware is more dangerous and might become devastating. But the truth is that there is no “anti-malware” but antivirus, which is used to fight malware, Trojans, adware, spyware, and the evil Ransomware among many others.
It is very important to know that Windows Defender, the antivirus by default of Windows 10, has not shown the best results according to the investigations carried out by the most important independent laboratories, although it has been improved in recent months.
On the other hand, many of the aforementioned laboratories use around 100 hosting URLs with malware to test each product, this way locating the most recent URLs specifically by the MRG-Effitas laboratory. This one and some of the aforementioned laboratories test the products, and by detecting which of those antivirus software, they manage to avoid access to malicious ULRs and , they are also able to remove malware during download.
We must keep in mind that spam filtering and firewalls, which are not common features in Antivirus, may be present in some of the products that we will mention later on. There are other additional features, such as secure browsers for financial transactions, the removal of traces left by your computer and mobile devices, the removal of browsing history, the safe removal of confidential files and the virtual keyboard to counteract the so-called “keyloggers“, in addition to the multiplatform protection.
The vulnerability analysis offered by antivirus programs are able, in most cases, to verify that all the necessary patches are present and can even apply missing patches. But malicious spyware (which is hidden) can record every move you make with your keyboard. But wait! There’s more…there are Trojans that have the incredible ability to pass themselves off as valid programs, while stealing all your personal data.
Other features that are necessary for a product (antivirus) to be described as “good” or “very good” by the aforementioned laboratories are: these must know how to handle spyware, given the extremely harmful features of this ” bug”. Many of these antivirus programs might have dodgy behaviours, but some are legit. Are these able to avoid “false positives”? This is another factor that must be considered by laboratories in order to assess antivirus software.

Okay, so let’s make a list of the best antivirus for Windows 10 in 2018, we will begin with the most qualified ones, by the laboratories that we have already mentioned and others that we have discovered along the way:
- Sophos Home Premium, which is quite good to fight malware, and it’s also suitable for Windows 8.x and Windows 10.
- Kaspersky Anti-Virus
- Bitdefender Anti-Virus Plus
- Norton Anti-Virus Basic
- McAfee Antivirus Plus, which allows you to install protection on all your Windows, Android, Mac OS and iOS devices, with a single subscription.
- Webroot SecureAnywhere Anti-Virus, which is an antivirus program that has a technology based on unusual behaviour.
Let’s analyse separately the best programs in order to protect Windows 10, according to the criterion of independent laboratories, bear in mind that we will not consider their hype or their popularity on the Internet.
1. Bitdefender Antivirus Plus:
The laboratories give this antivirus program the best reviews. In addition to this, Bitdefender’s Internet Security 2018 is like the big brother and, the strongest in the Bitdefender’s Antivirus Plus package, by the way. It provides security against intimidating viruses. On the other hand you can get a bi-directional firewall that prevents those annoying viruses that are already installed on your computer, from getting in touch with the Internet.
In addition to this, it offers an Internet browser that is independent and is designed, especially for your banking security. In addition to this, it has a real “crusher” that removes all traces of your PC, while also protecting your webcam, so that you cannot be spied on.
It has an anti-spam tool, file encryption, a parental adviser, it has anti-ransomware and anti-phishing features, and a rescue mode that will ensure that your computer boots safely, from rootkits.It’s algorithms measure the data to discover unknown threats and also to discover the new threats that might have appeared on the internet.
2. Kaspersky Total Security Antivirus:
The different laboratories place Kaspersky at the top of the list, and they clarify that Kaspersky has other versions, but the best one is Total Security. It includes safe mode for children, while also protecting them from inappropriate content and messages. It also has a built-in password manager so you can track the ever-growing list of them. It also has an online backup so you can keep your files safe.
It has traditional viral scans and backup software, and you will also have a firewall to protect you from unknown connections, as well as a very advanced anti-malware security to detect “bugs” before they infect your computer. It gives you anti-phishing protection so that your personal information is secure. It is a great antivirus for Windows 10.

3. McAfee Antivirus Plus:
This is quite important: with a single one-year subscription, all your devices will be protected, regardless of the different operating systems such as Windows, Android, iOS or MacOS, as long as they are all located in the same place. Just like Norton, it has been around for a while.
You should know, that not all these features are available for all devices. But, what kind of security do you want to have for your PC? A great protection against malware, a great technical support, a firewall and a user interface, this should be simple. In addition to this, it has protection against commercial viruses. We know that Bitdefender and Kaspersky have a better performance for protection; McAfee is the best for people who have a large number of devices in one place.
4. Webroot SecureAnywhere Antivirus:
It is a small but very fast program, since it barely uses the resources of your system. It can delay the harmful activity of Ransomware. It comes with a package of services, which is quite interesting. The signature database is stored in the cloud, so it only occupies about 4 MB of RAM, when the system is inactive. In addition to this, it does not require permanent updates (which are annoying for many users); therefore, this is one of the best and most comfortable antivirus for Windows 10.
Now, for those computer professionals and webmasters of websites or blogs, who might be interested in antivirus programs, but also in monitoring software, we recommend Pandora FMS. In addition to having extensive information on viruses and antivirus, Pandora FMS is flexible and capable of monitoring devices, infrastructures, applications, business processes and much more. If you still don’t know about us, you can ask us any question you might have in this contact form.

by Pandora FMS team | Last updated Sep 26, 2023 | Customer support
In times of digital transformation, the client is the centre of the Universe. Clients have a very wide range of products and brands and they change quite easily from one product to another, and with a very powerful tool such as the Internet, with those opinion pages and social networks, which might turn each customer experience into a potential viral thing.
Therefore, customer service has always been very important, but now it has become a key issue. Good customer service will turn into a loyal client who might recommend your company through multiple communication channels. However, bad customer service will mean the loss of valuable clients, and also the loss of potential clients due to negative publicity. Do you really want this to happen?
In this article we are going to see some mistakes that companies make when it comes to customer service. Try to avoid them!
1. Remember that the service is quite important
In some companies, people think that the relationship with the customer ends once the sale is closed. This is a huge mistake. Bad customer service begins as soon as you forget that customer service is the most important thing. Many studies claim that getting a new client is between 5 and 10 times more difficult than keeping a client. Don’t you think this is a good reason to try to preserve the ones you already have?
In addition to this, customer service has an essential role, which is related to the image of the company. Customer service is the most important thing for clients as soon as they have a problem.
Nowadays anyone can have a blog or a profile on social networks and reach thousands of people, don’t you think they should be positive when it comes to your company?
2. You shouldn’t be unapproachable
What are you, an ostrich? Do you think problems will disappear if you hide your head under the ground? If you don’t give customer service then that already means bad customer service!
Although some companies are used to this philosophy, which includes practices such as hiding all means of contact or waiting for a long time on the phone, it is not a good idea. Whether due to unwillingness, or any other reason, hiding from clients or putting obstacles in the way usually leads to trouble.
But, making it easier for your clients, usually leads to better results. Have you ever heard about the multi-channel approach? It consists of providing the customer with several contact channels, such as email, social media, etc. More companies do this now.
3. Your service should be in the hands of professionals
Are you planning to leave your customer service in the hands of your cousin Paco, who spends his mornings on the sofa watching TV? Providing good customer service is not easy. It requires personal values, such as empathy or patience, and good training, both to serve the client, to know the business, and to know how to use the tools in order to carry out the job. As in any other department of the company, customer service will require trained professionals who must know the importance of their work and act accordingly.
4. Listen to your clients
Whether due to lack of consideration, or due to stress and lack of time, some businesses don’t help the client, but they dispose of them.
This is not a good solution. First, listening with interest to the client is the first step to take in order to solve their problems, and second each contact with the client is an opportunity to learn. Indeed, every business is susceptible to improvement, and the best information always comes from the customer. Listen to their needs and problems. This will make it easier for you to help them and your business will grow.
5. Be organised
Evaluate the usual procedure when a client contacts your company. Again, have you hired your cousin Paco who picks up your calls and then hangs up straight away because he wants to go for a coffee?
Having just one person for customer service is not enough. The service must have good organization, which includes a proper provision of resources, a definition of service policies and a structure in order to solve queries in a comfortable, fast, and efficient way.
6. Your team shouldn’t have old-fashioned tools
Are the contracts in your company too old-fashioned? No? So why do you force your customer service team to work with notebooks or a simple Excel? We know that you are fine with these tools, but there are other modern ones, which may help you.
Why don’t you take a look at Pandora ITSM? Pandora ITSM is software that has, among other features, an incident management system (software help desk) based on tickets (ticketing) that can help you give a better customer service for your clients.
Do you want to know what the Pandora ITSM help desk software can do for you? All right then! Take a look here: https://pandorafms.com/en/itsm/help-desk-software/
In addition to this, Pandora ITSM has other very interesting features, such as an inventory, a project management system or a vacation manager. Do you want to find out more? Click here: https://pandorafms.com/en/itsm/
And don’t forget to leave a comment in the comment section, have you ever experienced bad customer service? What was your experience? Can you tell us a little bit? Do let us know! We look forward to hearing from you. Have you ever read any of our other articles of this blog? If you have, then which one was your favourite one? We usually talk about many different subjects in our blog. Let us know by leaving a comment in the comment section down below! Thank you very much for your comments and don’t forget to…
Send us any question you might have about Pandora ITSM. This is quite easy, you just need to use the contact form that can be found at the following address: https://pandorafms.com/en/contact/
The Pandora ITSM team will be happy to help you!
Have a great day!
by Pandora FMS team | Last updated Sep 24, 2024 | Remote Control
Do you own a company or do you work in one? Have your computers started doing weird things? Have they lined up and begun to dance the conga? If this is what you are witnessing, then you might be suffering from hallucinations, so you should visit a doctor straight away.
Even if you do not have strange visions, if you work with computers in your company, it is quite common for a technical problem to appear from time to time.
Computer problems are usually quite annoying, because these are created in tools that we use to develop our work and this way these problems prevent us from doing it, and this can end up generating a lot of frustration. In fact for some people this can generate what is known as “computer stress”.
In this article we will discover in a very summarized way, what a computer technical support for companies is and how it works (external or internal). We will also show you all about Pandora RC, a tool that will help you solve computer issues on your computers.
What is computer technical support?
Computer technical support is a type of assistance that is given to computer users, as a result of needs or problems that may arise with the software and with the hardware of their computers, networks, etc.
As you can imagine, this is a service that is usually provided by people with extensive knowledge in computer science (nope , we are not talking about the 3-hour WordPress training course that your uncle Ramiro did once). Usually, and depending on the size of the business and its needs, companies will have either their own technical service –which is usually carried out by the people in charge of computer maintenance of the company, such as system administrators-, or a technical service with third parties external to the company, both occasionally and on a regular basis.
What do we mean by computer technical support?
The number of tasks that can be carried out by a computer technical support service is so extensive that we would need several articles just to list each one of them. But we are not going to list all of them as this would be very boring), instead we’re just going to name some of the most basic ones.
The simplest way to describe the multiple tasks covered by IT technical support is distinguishing between tasks related to hardware and those that are related to software.
Hardware
This group includes activities such as the repairing of components of damaged computers, the internal cleaning of computers, the testing of motherboards, the configuration of Bios, the assembly of customized computers, the updating of components, the repair of power supplies, the solution of overheating problems, the installation of peripherals or the installation of networks, among many others.
Software
Here we would find tasks such as installing all types of software, installing or updating operating systems, recovering lost data and creating backup copies, freeing up hard disk space, solving malware problems (viruses, Trojans, spyware, etc.) or the uninstallation of unnecessary programs, among many others.
How does a computer technical support work?
A computer technical support service will work in one way or another depending on the problem you need to deal with. Have you dropped a glass of Galician soup on the laptop and now it doesn’t turn on? Did you get a virus on your computer while you watched videos of the puppies? Did you drop the screen of your computer to the ground and it turns out that now it is broken? The origins of the problems can be different, and the solutions will also be diverse.
We usually talk about levels or types of computer technical support:
- By phone or chat: it is usually used to deal with software problems that are ewasy to solve, or in which the user is a person with enough knowledge to solve these with the indications that will be given by phone.
- Through remote assistance: in this type of support, which is also usually used to solve problems with the software, the technician accesses the user’s computer remotely and “takes control” of it. In order to provide this type of assistance, computer technical services usually have remote desktop programs.
- Face-to-face: it is mainly used to deal with hardware problems. This way, the technician moves to the place where the computer equipment is located, in order to solve the problems “personally”. When carrying a physical displacement, it is usually a more expensive service.
Our great tool
Now that we have seen in a very summarized way what is computer technical support , we would appreciate it if you could spend a few minutes to discover a tool that can be very useful for some computer technical support tasks.
We are talking about Pandora RC, a remote management system for computers e (remote desktop software), which will be helpful when solving some of the problems that can affect a computer.
Do you work in computer technical support? Do you want to find out what Pandora RC is? It could help you when working remotely.
Do you own a company and a team that works with this type of work? Pandora RC can also help you!
In addition to this, Pandora RC can also help you with other interesting parts of your company. For example, it can make teleworking easier.
Pandora RC is available at a very affordable price, and you have several options to choose from according to your needs. And you can try it for free! Take a look, here.
Do you want to find out what Pandora RC can do for you? Click here.
Or you can also send us any question you might have about Pandora RC. You can do that in a very simple way, thanks to the contact form.
And don’t forget to leave a comment in the comment section and let us know what you think about the computer technical support. Thank you very much!
The Pandora RC team will be happy to help you!
by Jimmy Olano | Last updated Nov 23, 2022 | Community, Features, Tech
PostgreSQL10 logical replication. Find out all about it here
Some time ago, we published a study on PostgreSQL monitoring in a very detailed way. A few days ago, a specialized magazine announced the good news about the launch of a plugin to monitor PostgreSQL10 with Pandora FMS, our monitoring tool. Today we will enrich our knowledge with the new version of PostgreSQL: version 10, let’s go!
Introduction to PostgreSQL10
PostgreSQL is a powerful database which has been mentioned in our other articles as one of the best relational free distribution databases and nowadays this is still true. There, you will find a summary of the articles which have been published in this blog or in the Pandora FMS forum, this way you will be able to broaden your information about PostgreSQL 10 but also about its previous versions. We need to mention that these articles are still fully valid, since the new versions always include a compatibility, thus the software that uses PostgreSQL can be updated to version 10. PostgreSQL is completely written in open source with a license which is similar to BSD and MIT. Essentially the license indicates that we can do anything we want with the source code as long as we don’t have any liability for its use to the University of California.
With this article, we want to continue the other article that we mentioned eariler, where we explained the query of the locks in PostgreSQL with the pg_locks parameter:
SELECT COUNT(*) FROM pg_locks;
When several users accessed the same registry (or several ones) a lock was produced to avoid collisions of versions in the data, which is an important parameter to monitor. In a different study we did on another popular database, we introduced and briefly explained what the ACID is, (Atomicity, Consistency, Isolation and Durability), this way, from the registration of new data and transactions together create locks in a relational database: and yes, this also happens in other storage engines, hence the importance of the new feature of PostgreSQL10!
Locks, locks, locks: the nightmare of programmers
We need to explain why locks get in the way with our tasks of Database Monitoring. This happens because of the backup monitoring, their correct execution, storage in a safe place, and databases are not exempted from these locks. In addition to this, we must follow the basic advice in order to optimize the performance of them, this way everything is harmonized with a monitoring system.
This can be carried out with specialized care (for the “Enterprise” version of Pandora FMS, and there are user training plans), in addition to this, the network administrators keep replicas of the databases on other servers in different physical locations.
These replicas represent several advantages:
- These may be physically located outside the company or in their branches, as well as always considering the encrypted communications in order to pass data from one side to another.
- Conceptually it can be considered as “backup copies” which are updated essentially in real time.
- We will be able to perform audit tasks and statistics on the replicas without affecting the performance of the main database.
What is a database replica in PostgreSQL10?
A database replica replicates the data in a very simple way: it copies the files of the master database, bit by bit, byte by byte. PostgreSQL10 saves in the specific files each element of a database and in order to do that it takes a binary record, a kind of log that summarizes the change made in those files when records are added or modified. This way of replicating is also used by other database engines since it is a well-known scheme.
A collateral effect of database replicas is that the slave will not be available while the replicated information is being written. This is not something to be worried about, the most important things is what happens in the master database when there is a lock of records or, even worse, a set of records that belong to a transaction that must be reversed. These should not be copied in the replica, because it is an information that will not be permanently registered and will be deleted (only a summary of the information will be saved).
Let’s look at these previous things with a simple example: two clients of a bank keep accounts and client A wants to transfer money to a client B (in real life this is much more complex, this is only a simplified example). At least two writings must be made in the database: one debiting the amount to customer A and another one crediting the amount to customer B: when both events have been verified the transaction can be completed and the changes become permanent.
What would happen if, client A made this transfer of money to customer B, and then the automatic payment of his credit card were deducted, ending up with no balance for the transfer? Well, the accreditation that would have been made to customer B and the debit made to customer A would not be permanently registered and would be discarded: this is how ACID works, guaranteeing the integrity of the data and thus complicating the replication of the information.
The replication process does not know anything about registers or users that want to record or modify data, the replication process only knows that the files must be the same in both machines and if the origin writes data in any of those files, then it must wait until it finishes so that the file is then available to be read and copied.
What is a logical replication of a database in PostgreSQL10?
The approach is different in PostgreSQL10 and consists of the following: it does not matter the way in which the normal replica makes the process of consulting the binary record, which keeps track of the files that have been modified since the last successful replication. This is what’s new, it translates these changes into information about the records that are already permanently recorded in the database, these records are then read and added in the replica. This way, blocks are ignored because we don’t know how these will end up (either permanent or discarded), which is a very practical and ingenious solution and also gives us additional benefits.
How are logical replications possible in PostgreSQL10?
Thanks to this new version 10 we can install a PostgreSQL extension called pglogical from the software house 2ndQuadrant and they have added logical features to PostgreSQL since version 9.4.
pglogical is available as free software under the same licensing conditions of PostgreSQL10 and in order to install it we must follow the following steps that we will explain in a practical way when using GNU/Linux Debian and its derivatives:
-
- First we must add the repository in our computer from the PostgreSQL website, in the case of Ubuntu we have version 9.5 and we need version 10.
- We must insert the key of the repository which will guarantee us that whatever we download , will be legit according to what is published in the PostgreSQL page (all the details in this link).
- We will do the same process with pglogical, we will add the repository from the 2ndQuadrant website in order to get the latest version available.
- We must also add the respective key of the 2ndQuadrant repository (all the details in this link).
- Once we have configured the repositories, we command apt-get update and then apt-upgrade.
- Finally, we need to install PostgreSQL10 with apt-get install postgresql-10 pgadmin3 and pslogical with apt-get install postgresql-10-pglogical.
- We tested these processes on a 64-bit Ubuntu 16.04 machine (in fact the database offered during the installation of Ubuntu Server is indeed PostgreSQL) and the only problem we had, was with the Russian-language dictionary regarding the Hunspell spell checker.

If we want to experience the latest development version of pglogical we can bring the source code straight from its repository on GitHub. In the website of 2ndQuadrant , they inform that the version of pglogical must always match the version of PostgreSQL installed and different machines can work with different versions (and replicate between them) as long as the above is respected, so depending the database administrator, this is how it should be done.
Extending the utility of logical replication in PostgreSQL10
The logical replication overcomes certain technical limitations of normal replication thus fulfilling our goal of data backup but we can go further: we already know that the logical replication is NOT a true and faithful copy, byte by byte, of the master database. Therefore the information that we are copying from the master database arrives at the replica as if it were an “independent” database and will write in its own files, depending on the type of hardware and the operating system installed etc…
A register X is copied in the replica and is identical byte to byte to its original, but the way in which this is written on the hard disk will be different in both machines. In order to finish this we must point out that with a logical copy we can extract statistical or audit information from it without having to wait for the replication to be written (for example, every five minutes or a gigabyte, whichever comes first).
The fact of extracting statistical or audit information from a replica database implies that we must write the queries (or even modify indexes) which, of course, do not exist in the master database, but we need to give back the information: when writing these queries (even if they are temporary) the database is no longer a faithful and exact copy of the master database, which causes problems when replicating files one by one.
With the logical replication we will not have that problem since it is guaranteed that all the original records are copied in the replica, which guarantees (because it is a machine for replicating) that these cannot be modified or deleted but they can be read and consulted.
Extending the utility of logical replication leads us to practical examples, for example, the Credit Card Department of a bank must keep record of clients in real time without impacting the main database with their work: we will be able to install a logical replication server that will only copy the data of the clients who have credit cards. These data could be personal data, bank accounts and of course data of credit cards. It is not necessary to replicate all the customers of the bank, only a part of them; Likewise, the Credit Card Department can even create additional tables to analyze bank movements thus being able to approve an increase in the customer credit limit and thus other things which mean income of money for the company.
Configuring PostgreSQL10 for logical replications
When installing PostgreSQL10, this defaults in the WAL configuration by default. This configuration allows recovering from unexpected shutdowns or failures that have prevented the data from being recorded on the hard disk.
In the case of replications, logical replication is a new feature that many people do not yet because it is disabled by default. First, we need to have exclusive access to the database (we will be connected with the proper credentials) and second we need to change the value of the wal_level parameter to ‘logical‘. In order to know the location of the postgresql.conf file, we just need to execute in a psql console the command: show config_file and edit the file thus modifying: set wal_level = logical and save the file. Then we will need to restart the service, which is not a problem since we are the only ones who are connected.
This change will tell PostgreSQL10 that it will have to add the corresponding registers in order to translate the binary catalogs into record catalogs, hence the need to momentarily stop the database and restart it. PostgreSQL10 has the ability to host scripts in the Python language, so what we describe will depend on each database administrator this way working together with the network administrator(s) in order to take advantage of night time or early morning to do the work without impacting the normal daily work of the company.
Creating publications in the master database
PostgreSQL10 is configured to work with publications that we must define in the master database. If we are connected with the appropriate credentials by a terminal window , we will create a publication for our example of the Credit Card Department of our imaginary bank , it will be something like this:
CREATE PUBLICATION dpto_tc FOR TABLE clients, bank_accounts, credit_card;
This will create a publication called dpto_tc for the tables called clients, bank_accounts, credit_card for the logical replication
If we need to add all the tables to a single publication, we should write the following:
CREATE PUBLICATION all_the_tables FOR ALL TABLES;
We must emphasize that by default for the publications that we add, the data of those tables will be copied to the logical replication in its entirety, however there is the option to copy only the data that have been added after the creation of the publication.
Preparing the logical replication
Once we have defined the publications, we will proceed to carry out the work that may involve greater thought and decision from us: we will have to create the data structure of each and every one of the tables that each publications and if we use the order ” FOR ALL TABLES “in at least one of the publications, we will have to make an identical copy of the entire structure of the database.
That is why we recommend to advance work and always create a complete copy of the entire structure of the database since pglogical will never do this work for us and when replicating, it will only return a ‘table not found’ error (which will lead us to the monitoring of the work of logical replication, so Pandora FMS, get ready to monitor!).
Creating subscriptions
Once the data structure is ready to receive the logical replica, we must create a subscription using the same names of the publications created. Once we are properly connected to the machine that will contain the logical replica, the syntax will be the following (we will use the same bank example):
CREATE SUBSCRIPTION dpto_tc CONNECTION 'host=bd_maestra dbname=mi_credenciales ...' PUBLICATION dpto_tc;
To make it easier, the subscription will have the same name as the publication and regarding the connection data we must include the values according to our network structure and configuration: waiting and expiration time of the connection attempt, the port, etc… everything according to the RFC3986 standard.
Modifying the publications
With the ALTER PUBLICATION command in the master database we can add new tables, delete, change users or even rename the publication, among other options.
Keeping subscriptions up to date
We can automate the maintenance of subscriptions in the slave database with the following order:
ALTER SUBSCRIPTION dpto_tc REFRESH PUBLICATION;
This will update the tables that we have added, so that’s why talked about copying the complete structure of all the tables in the database but we need to dwell on this: if we create a new table in the origin and add it to the publication, we must also create this structure of table in the destination and then update the subscription.
Monitoring logical replication in PostgreSQL10
Just like normal replication, which we can extract its state with pg_stat_replication in the logical replicas we will use pg_stat_subscription as follows:
SELECT * FROM pg_stat_subscription;
We can also select specific fields of subscriptions:
- application_name: the name of the subscription
- backend_start: specific date and time of the start of logical replication.
- state: if it is working we will see “streaming” or transmitting.
- sent_location: hexadecimal value for binary audit purposes.
- write_location: previous idem.
- flush_location: previous idem.
- sync_state : it returns asynchronous value, which is executed independently or in the background.
To finish this article, now programmers will need to create a script to connects both databases in read only mode and compare record by record to see if the information matches in both origin and destination. This process, could be carried out at dawn or on weekends and the results should be stored in a third database or in log files, in order to be monitored with Pandora FMS so that we configure the respective alerts in an appropriate way.
Conclusion
We have hardly gone through the logical replication since there are still many other features such as:
- Row-level filtering (registration): just like the CHECK command, we can only replicate those that meet a certain rule.
- Column-level Filtering (field): if a table contains many fields that are not relevant for the credit card department (as in our practical example), we will only replicate the ones that we want.
- pglogical has a parameter that is unique to this add-on and that consists in delaying replications according to the period of time we need: we might need replication to start at night when the employees are gone. This feature is not “embedded” in PostgreSQL10.
We think that these concepts will become quite common in the future in other data management environments, if you have any question or comment, don’t forget to write it down here! Thank you !
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
If you have more than 100 devices to monitor, you can contact us through the following form: https://pandorafms.com/en/contact/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!

by Pandora FMS team | Last updated Aug 27, 2021 | Community, Network, Tech
Social media monitoring. Find out 8 tools for great monitoring
From your cousin Paco to your grandmother Maria. From the Pharmacist around the corner to the President of your country. Some studies claim that about 3,000 million people around the world already use social networks. Don’t you think that’s a lot of people?
Since its emergence 10 years ago, social networks have quickly become one of the great things about the Internet. The success of social networks has led millions of people to spend hours and hours each day immersed in endless content and for many of these people this is why they use the network. Given that the number of Internet users is estimated at around 4,000 million users, it could be said that about 75% of people who use the Internet use it for social networks.
Nowadays, companies know how important social networks are. Today, most businesses have profiles on social networks. On the other hand, thousands of professionals also have used these to make themselves popular or to share ideas and experiences.
But the direct presence is not the only concern for brands when it comes to social networks. Users perform all kinds of comments about companies, brands or products in their own profiles. Thus, there are basics concepts for survival online such as digital reputation, which is in the hands of users through these networks like Twitter, Facebook, etc.
In addition to this, it is not just a matter of digital reputation for companies on social networks. The good thing about social networks is that these can be used to advertise the products of a company or these can also be used to generate some buzz about a product.
However, it’s quite difficult to control the volume of content that is generated there. All this volume and complexity, combined with the interest of professionals and companies, has generated all kinds of emerging applications for social media monitoring. Both those ones which specialize in specific networks, and also those ones which are capable of monitoring dozens of them at once, there are many of them to suit the needs of each user.
When it comes to companies, these applications are very useful to answer a question that is quite important nowadays: What do my clients think of my brand?
In this article we will briefly discover some of the tools for social media monitoring which can be found on the Internet. Most of these have some cost-free option, but some of them also have paid versions, which provide additional features. Let’s start!
Hootsuite
This is one of the most popular monitoring tools on social networks and according to their own website, it has more than 15 million users. It’s capable of being used in a number of social networks, specially the most common ones; it is easy to use and intuitive. It allows you to monitor your brand and to monitor whatever your customers say about your brand on social networks.
Klout
It is one of the most popular tools. It is specially focused on content. It has features that suggest content that may be of interest to followers and it can monitor their reaction. His “Klout score” is quite popular, which is an index between 1 and 100, which represents the influence or ability to generate actions, in every user.
Social Mention
It is able to monitor mentions received by a brand in more than 100 social networks. It classifies its influence through 4 different categories: “reach” “Passion”, “sentiment” and “strength”
Howsociable
It’s very useful for measuring the presence of a brand on social networks. One of its distinguishing features is that it rates differently for each platform, which allows us to distinguish what platforms are performing best for our brand and which ones should improve.
Twitter Analytics
This is one of the greatest tools when it comes to monitoring Twitter. It is able to measure the interaction and improve the success of “tweets” but it also able to explore the interests, locations, and demographics followers.
Tweetdeck
Another tool which is quite relevant among those for Twitter monitoring. It has several features in relation to this social network, which makes it a very complete tool for monitoring this great social network.
Google Trends
It is one of the classic ones in this industry. It monitors the most common searches on the most used search engine in the world: Google. It also allows you to compare results, by country and to see graphically the evolution of the interest (search terms) for a brand.
Google Alerts
This is another Google service sends by email the new content that has been generated and has been found by the search engine, and that contains the search terms selected by the user. It has configuration options that allow you to select variables such as the type of alert or its frequency.
And so far we have seen some of the best known social media monitoring tools, but there are many more, according to the taste and needs of users. As in so many other fields, the offer you can find on the Internet is limitless.
And yourself, what do you think of social networks? Do you think they will continue being quite popular for the next few years or, perhaps, do you think they will be overcome by some new trend? What do you think?
We are looking forward to hearing your opinion. Let us know your opinion down below in the comment section. Have you checked any of our other articles? We have a lot of articles, which talk about many different topics.
If you have checked any of our other articles, then which one is your favourite?
We want to know!
And remember, if you have any question; don’t forget to get in touch with us! We will be quite happy to help you!
Don’t forget to check our products in our website! We have many different technological tools that might help your company. We have Pandora FMS, eHorus, and Integria IMS. Do you already use one of these? Have a look at our website to check them out! And let us know your thoughts on these social networks monitoring tools.
Thank you very much for participating! We look forward to hearing from you!
by Jimmy Olano | Last updated Nov 23, 2022 | Community, Tech
Blackbox and whitebox testing for a better monitoring
In the automated field of computing, some terms or trends are in from time to time. Today we will look at the concept of blackbox and whitebox testing, applying it to the science and art of monitoring.

Introduction
Today we will show a new approach to the matter of monitoring, from installing Pandora FMS (or any other software that we have selected, since we will talk for the most part about concepts) to then introduce the ideas of blackbox and whitebox testing. We will be brief in our explanation; however, we will include links so that whoever wants to delve into every aspect, is able to do so.
Collecting metrics
Every administrator of a local area network must be aware that monitoring is unavoidable and that with Pandora FMS the task becomes much easier. For this, Pandora FMS takes into account the most important metrics, but since as -for now- Pandora FMS can’t do magic, it uses dynamic monitoring: a feature that has been present since the release of our version 7.0 NG to make the installation easier.
The metrics we can collect are grouped into four categories:
All these metrics are collected in very different ways and forms, depending on the network topology, which leads us to distributed monitoring, where we explain thoroughly the flexibility that characterizes Pandora FMS.
Alert management
After a certain amount of time (let’s say a week) collecting data, our lives will be filled with alerts (either by email or by messaging services such as Telegram or Twitter), which is completely normal and is not to be frightened or pushed back:
- If it is something really important, we will proceed to correct it and leave the alert as it is, starting to harvest the fruit of our work with Pandora FMS.
- If it doesn’t deserve more attention we can modify the alert (yes, we know that the dynamic monitoring of Pandora FMS was the one who included it, but in the end we are the ones who decide) adjusting the values to avoid excessive repetition. Each alert in Pandora FMS has a comment tab where we can justify and/or explain the reason why we modify the alert values. This way we can go on vacation and our substitutes will have a human guide present to advise them.
- It is necessary to know that an alert can be suspended so that it is not shown in the Pandora FMS desktop, either because we are going to do something punctual and urgent or we can even program it in certain schedules (for example, when it comes to backup database server data, logically the network will be congested and trigger an alert, since Pandora FMS is not aware of how our policy or way to backup data are).
- The next step would be to deactivate a certain alert, which is the most advisable thing to do instead of eliminating it, because in the monitoring field, today we have an environment and tomorrow we don’t know what will happen, so we could need it again and we’ll spare ourselves the work of creating it again. This also explains why monitoring tasks cannot be fully automated.
- When we modify an alert, one of the values that we can set is the maximum number of repetitions that Pandora FMS will notify us (this is like when our skin feels the first raindrops of rain, after a certain time, and being already wet, it stops informing us about it). However, there are other events that take place in cascade and trigger a large amount of mass alerts: if the modem with which they access the Internet in a certain branch office is, for example, damaged or not connected, all devices in that local area network will trigger the alarms (assuming that we do not have a satellite server). To do this, Pandora FMS has a Cascade Protection under a “parent-child” entity model: we activate the corresponding checkbox and then we go on to associate it with the parent agent. In the event that the parent officer has any critical status alerts, the child agents will not trigger their alarms.

- We cannot end this section without commenting that once all these alerts have been fine-tuned, we will be able to evolve and create generic alerts by groups of agents (in order to reuse them in new devices that we add to our networks) and even create alerts by correlation of events to identify and act in cases where no classic alert is triggered. Imagine that we have several web servers with balanced load and we have them configured to alert if any one exceeds 90% of CPU usage but it happens that each and every one of them reach 60% and up to 70% of their capacity: this is a good time to alert us to make the decision to first review what is causing the overload and if it is necessary to add more servers, if the case were the natural growth of the company and its web clients. In addition, it is even useful for detecting hardware and/or software modifications that lead to investigating and/or adding more monitoring agents (or at least their modification).
Whitebox
We can then define the whitebox model: we know our system, how it works, what the processes are, and with the help of Pandora FMS we can place agents (and even satellites) to collect the data. We are in the whitebox category because we have the complete map, we know in detail every process and the complete mechanism, there is nothing hidden or closed for us. Obviously, the collection of metrics under the whitebox scheme allows us to save time and effort, since we know in advance where and how key points work and we can monitor vertically. However, it may happen that some unknown or unexpected aspect, under certain conditions, escapes from our grip, so the whitebox test arises.
Whitebox testing
Whitebox testing is also known as a transparent box (among other names) and is actually out of our reach as it belongs to the development team and operations team (which we are attached to as a monitoring team) and takes advantage of our knowledge of the software and system to make it part of a test process. It happens that, under certain circumstances that we have detected by our alerts, based on metrics well collected by the whitebox model, we can indicate the exact conditions to reproduce a certain exception. The advantages are clear:
- We obtain a better overview of the situation.
- Helps optimizing the code.
- Introspection of programmers, awareness of their actions.
- Allows finding hidden errors.
- All this leads to efficiency in finding errors and problems.
Disadvantages of whitebox testing:
- We need to know the source code of the involved software(s).
- Requires a high level of understanding and experience of the affected program.
Monitoring software using the whitebox model
Apart from Pandora FMS itself, there are many other softwares that use this model, some time ago, we published an article about Zabbix (where we will be able to see its operation in detail even though it is a comparison); we also have PRTG Network Monitor (which we evaluated and is of the same weight and size as Pandora FMS but with proprietary software).
When users report that “the system is going slow,”
Although we already have our Swiss pocket knife (Pandora FMS) and we are more ready than a child explorer, at some point the dreaded qualitative report of one or more end users will arrive:”the system is slow“.
With reports, our patient must be that of a saint: from our users, whether it’s employees or clients (the latter will have no shame in complaining, with or without a reason), here is where we must sharpen our wit. For the users who are employed by us, we should indicate the most appropriate method to report any problems.

In the case of the company’s customers, we must rely on the customer service department. This doesn’t mean that the battle is lost, but that it’s time to use the artillery we have in Pandora FMS.
Applications that interact with users
Today, our world of information is divided into two types of applications: on one hand, the usual one, which is installed in an operating system through a suitable process and properly configured for that particular environment, which we have always known as vulgar desktop applications (compiled especially for a particular environment).
On the other hand, there is, ironically, also a desktop application but which during the last ten years has gained a tremendous prominence thanks to the add-ons developed for it: our web browsers. A web browser programmed with free software such as Mozilla Firefox offers developers the typical HTML (CSS included) and JavaScript languages, giving us a well known and secure environment, regardless of the operating system installed or hardware used. But even more, it allows us to incorporate plug-ins for a wide variety of tasks, from games to emulating operating systems or simply running virtual terminals. Programming is progressing more and more towards this sector, given the obvious advantages.
Monitoring desktop applications
Pandora FMS has for the Windows operating system the Pandora Desktop Robot (PDR) which will allow us to record actions on any installed software and obtain its results (right execution or not, processing time) that later can be sent to our monitoring server to evaluate the data.
It is recommended to install the PDR and the probe in virtual machines with auto-start and user auto-registration in order to record the actions, save them and we’re ready to go. We can have these virtual machines running continuously to run periodic tests or launch them when a user reports a problem to us. To do this, we will reproduce the situation once only because we will save it and program it to run autonomously many times, then analyze the results and confirm either the error or the error in the report.
A more daring option is to install it through Active Directory on the end users’ machines and from there, from the real environment, run our tests. This option must be carried out very tactfully, even on specific users who repeat the same report over and over again.
Monitoring web applications
There are two components that we can monitor: on the server side and on the client side. On the server side we will make use of the whitebox model because we know how it works, to which database it connects, the languages used, etc. But on the client’s side we will make use of the Pandora Web Robot (PWR) that allows the navigation through web sites simulating user actions and collecting the results as if it was just normal monitoring. You can watch this explanatory video on Youtube.
Among the possibilities of this monitoring, it’s included the ability to install virtual or real machines in different geographical situations, let’s take the case of different cities and even continents pointing to the same web server, this will give us a real panorama and most importantly, a quantitative report that can be confronted with what is reported by users (corrective mode) or by tasks programmed by ourselves (preventive mode).
Blackbox
The last thing we’ll see is the blackbox model because we can apply it even if we don’t have the data of a whitebox model at hand (in fact, it’s an independent model). The blackbox model can be used in any desktop application or web application and start collecting data for a while as if it were normal metrics and averaging values (again, let’s take a week per subject) to generate alerts from there.
It’s called blackbox model because we don’t know how applications work, where they go and where they come from, what we know is what the end user sees, who will tell us which processes are critical and that we will analyze and monitor in search of deterioration (or perhaps improvement) in software performance. We are at the final end, where we only know the result and have no idea what causes it.
We can see this blackbox model as an audit process: a company hires us to review its software in different environments but does not provide us with the source code or allow us to access their servers, only their API or WEB services as the case may be. Its operation is hidden but we can quietly send our reports quantitatively where the values are extended/exceeded or when they have changed significantly (a value of 10% is always a good variation reference, for better or for worse) and in different conditions (time, geographical location, connection method, different computers and/or operating systems, etc.).
In the development of proprietary software blackbox model is very handy: Pandora FMS is the tool to test and / or take to the extreme future applications that will reach users without compromising the source code or touching the servers or infrastructure. In other words, we monitor even before the production stage begins, like a kind of beta user but with very specialized tools.
Following the last example, our client may be interested in finding out where it happens or what causes the problem, but we will not be able to give that answer since we were hired to work under the blackbox model and said model only evaluates results, not the causes, unless we have Pandora FMS in our arsenal.
Blackbox testing
Blackbox testing (also known as functional testing) treats the software under test as a whole without knowing its internal components. The tests use software interfaces and try to ensure that they work as expected. As long as the functionality of the interfaces remains unchanged, testing should be successful even if internal functions are changed. The blackbox test is “conscious” of what the program should do, but has no knowledge of how it does it. Blackbox testing is the most commonly used type of testing in traditional organizations that have beta users as a separate department, especially when they are not coding experts and have difficulty understanding the code. Provides an external perspective, such as an audit, of the software under test.
Software that uses blackbox model
Nagios (although its agents are a bit cumbersome to set up) is a software in the end, itt actually gets its metrics this way.
Monitoring: whitebox and blackbox
Pandora FMS is designed to adapt to many of the challenges that arise, each company has its particularities but it does not mean that we are not prepared at all. The monitoring of services is something very different from the usual thing: the services will be that series of functions that we offer to our clients or collaborators. These services, in short, will be low level (whitebox model) or high level (blackbox model) so it is a mixed working model and we even dare to say that it is the most appropriate but also the one that involves more work because both results must be combined and delivered to the development and operations teams in order to find the solution to the errors or find possible performance improvement.
Conclusions
We have covered at least 80% of the monitoring material, in the most enjoyable way possible. If you wish, you can add our article to your favorite websites so that you can read -and discover- in several days the reason why we are so passionate about our work: it includes programming, network administration and assistance to end-users, users programmers and even robots – what a titanic task!
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
If you have more than 100 devices to monitor, you can contact us through the following form: https://pandorafms.com/en/contact/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!

by Rodrigo Giraldo Valencia | Last updated Aug 27, 2021 | Community, Geek culture, Tech

Gpay, what is it? Quick, easy and safe online payments
On January 8, Pali Bhat, Google’s vice-chairman in management of payment products, announced that from that date on, “Everything would be brought together in Google Pay.” Bhat was the promoter of this great idea, which is meant to make our lives easier. Let’s have a quick look at it.
For those people who have used Android Pay to pay for food and have used Chrome for their payment information or have purchased apps on Google Play, it’s clear that they were able to experience how Google helped them pay. While these processes were being developed, Google worked hard in order to make these experiences easier and shorter in time. In addition to this, they also worked hard to make these processes safer and more consistent.
This way, Google Pay was invented. Here, all forms of payment are brought together, including Android Pay and Google Wallet. It is now possible to search it in Google applications, either online or in stores, and is available in different applications and websites for different types of customers.

When it comes to developers, we can say that they will be able to visit the website “Payment Solutions”, to explore how they can implement Google Pay, although in this tutorial we will give you the important information so that you don’t waste time. The developers will also be able to work with one of the partners of the processor of this new Google application, in order to carry out an even simpler integration. Then, you will be able to discover how to achieve this in this post.
Let’s have a look at some of the most outstanding features of this Google innovation:
- The entire payment process will be easier and faster.
- Customer experience will be improved.
- It will reach billions of Google users, all over the world.
- It is implemented only once and can be used everywhere.
- It is a very simple process for the suppliers of goods and services and for their clients.
- Conversions are improved, with simple payments, on time.
- Customers will be able to pay very fast, this way, it will be easier to purchase in the app and also in Chrome with just a phone.
- Global reach of customers in Google Scale.
Why has the shopping experience significantly improved?
Since the payment process is very simple, fast and agile, the shopping basket abandonment is considerably reduced, while customer satisfaction is increased. In addition to this, there are no additional fees, since Google does not charge sellers or buyers. Additionally, customers/buyers can access any of their credit or debit cards that are stored, so that they can have control and pay as they wish.
Regarding the security factor, we need to point out that additional security is provided, while Google stores the payment information of customers/buyers, in the safest way, and only shares what is required for each transaction. Let’s have a look at one of the interesting factors from Pandora FMS: the implementation of this new Google application.
How is Google Pay implemented and operated?
Well, it works with several payment processors:
Ayden
It turns out that hundreds of millions of people, around the world, add payment cards to their respective Google accounts which, in other words, can be used to withdraw from any Google product, so that there’s no need to enter your payment details every single time. With this new Google payment API, we can enable the same payment experience, for our own products and/or services without effort. Customers, in turn, can pay with any credit or debit card stored in their Google accounts. So sellers and service providers can allow payment online, without any interruptions in Android applications or, in Chrome with a mobile phone.
Google Pay is a unique solution that accepts payments from anywhere and from any device, this is due to:
- Complete functionality for mobile phones.
- Global reach, with a single solution.
- A Targeted risk management.
- Greater authorisation for subscriptions.
- Flexible and easy integrations.
As we mentioned earlier, Ayden (one of the several payment processors of this Google API), is an excellent solution to accept payments anywhere and from any device. In addition to this, Ayden reviews payment flows without friction, plus it has Ayden MarketPay which is a payment solution for marketplaces, with different payment methods, and has “Revenue/Accelerate” that allows the optimization of authorization, and it also allows payments in the store.
Additionally, Ayden has RevenueProtect (integrated risk management), a global reach with a local focus, a unified report of crossed channels, and an entire associated ecosystem that offers the option of connecting existing platforms.
Braintree
Currently, Google Pay is available in the beta version, with the latest Android SDK and Java Script. In addition to this, it offers a mobile shopping experience, both in the application itself and in the mobile web for customers with compatible Android devices. On the other hand, it allows customers to pay with cards stored in their Google accounts, in addition to those stored in Android Pay. In other words, we can say that this new Google API extends the existing feature of Google’s Android Pay, to include access to the safe of the Google card. This allows customers to make purchases quickly and, also, safely on their Android mobile devices.
Then, when selecting this new Google API in the Android application or, in the mobile web, customers can pay using the cards associated with their respective Google accounts. Now, regarding compatibility, we can say that the place where the business of a seller of products or services is domiciled determines the ability to either accept Google Pay or not. Then, most of the merchants that are located in the regions that we will mention later on, and depending on their processing configuration, will be able to accept “G-Pay” transactions from eligible customers, with these types of cards:
- United States: MasterCard, Visa, American Express and Discover.
- Europe: MasterCard, Visa and American Express.
- Australia: MasterCard, Visa and American Express.
- APAC (Asia-Pacific): MasterCard, Visa and American Express.
When it comes to Europe, APAC and Australia, it is necessary to bear in mind that, in order to be eligible to accept the new Google API, with American Express, you must proceed with the Amex accounts. For those who are not sure of the configuration they need, we recommend you visit this page of Baintgree to contact them and solve the problem.
Entrepreneurs and merchants domiciled in the United States and integrated with Google Pay, will be able to accept Discover cards from their respective customers, without having to carry out any additional integration work. But, if you use split shipments or recurring billing in this new Google API, you should contact Discover, to set up the necessary permits, in order to avoid annoying rejections.
Regarding the compatibility with the customer, let’s say that right now, businessmen and merchants can accept “G-Pay” from customers with Android devices, in the countries that we have mentioned:
- Australia
- Belgium
- Spain
- United States
- Hong Kong
- Ireland
- Poland
- United Kingdom
- Singapore
- Ukraine
When it comes to Ukraine, we must clarify that customers in this country can make purchases through this new Google API. However, merchants domiciled in this Eastern European country are not eligible to work through Braintree.
Now the transactions of “G-Pay” process and resolve, just like credit card transactions but it is possible to identify them in the Control Panel, by its logo-symbol of single payment. When it comes to the registration, we need to point out that there are no standardized (or additional) rates to process “G-Pay” transactions, given that the price of this Google API is the same as the other transactions with credit cards.

EBANX
Through this processor, business owners / merchants let their customers pay with local cards stored in their respective Google accounts. It is a good payment experience without interruptions, and with a few clicks, customers who have stored credit card data in their accounts of Gmail, Android Pay, Google Play or YouTube, can safely pay for their purchases.
When it comes to Latin America, businessmen already have the possibility of offering their local payment options to their customers by integrating EBANX with Google Pay. In general terms, the integration is easy and fast between “G-Pay”, and the application or mobile website, with EBANX. And when it comes to the operation, let’s say that it is enough for the client to click on the button called “Buy with Google Pay” during the payment itself, then choose between using a payment method already stored or add a new one to your Google account. Then, the client must grant the respective permission to the merchant / businessman to access “G-Pay” and, click on “Send order” this way, finishing the transaction.
Paysafe
Through this processor, it is possible to simplify the payment process for customers, by offering “G-Pay” on the mobile web and, also, in the Android application. This one provides improved security and also, reduced PCI responsibility for greater peace of mind. The integration is simple and unique, through the Paysafe SDK, while providing the full capabilities of Google Pay.
With this processor, cards from several Google accounts of users are accepted. Additionally, the entrepreneur can offer an uninterrupted payment experience, within the mobile application and, also, in the mobile web. Entrepreneurs can also offer secure transactions, using, “tokenization” and fingerprint authentication, if available.
With Paysafe, customer data is protected, given that card data are not stored on the devices, while information is encrypted by Google and is only available to its payment providers, who are certified. For this new and better experience, “G-Pay” unlocks a global audience of hundreds of millions of new customers.
And how can we configure Google Pay?
Using Java Script v3 SDK
The new Google API is available in the beta version, with the latest version of JavaScript v3 SDK and Android v2 SDK. But bear in mind that JavaScript requires an Android device with Chrome v61 or higher. On the preparation, let’s say that, in order to accept payments through “G-Pay”, in SandBox or in Production, it will be necessary to enable it in the Control Panel. To do so, it is necessary to log in previously, in the SandBox Control Panel or in the Production Control Panel, so you need to log in previously. Then, we should go to Settings> Processing> Google Pay.
If “G-Pay” is not yet enabled, you must click on the respective button. If this new Google API is already enabled in our Control Panel, but we need to enable this payment method, we will need to get in touch with the support team.
Through Android 2V SDK
Android SDK requires Google Play Services Wallet 11.4.0 or later. When it comes to its configuration, in order to be able to accept payments through “G-Pay” in SandBox or in Production, it is necessary to enable it in the Control Panel and to do this; we must login in the SandBox Control Panel or, in its Production Control Panel.
Then, we have to go to Settings> Processing> Google Pay, but if “G-Pay” is not yet enabled, we must click on the respective button. If we already have “G-Pay” enabled in our Control Panel, but we need to enable this payment method for a commercial account, it will be necessary to contact the support team. Anyway, in Pandora FMS, we will find valuable additional information for entrepreneurs.

by Pandora FMS team | Last updated Jul 13, 2023 | Help Desk
If you own a company, you might want to make the world a little better. But you probably want to earn money too. And one of the key things to make money in a company is to establish your income model.
When it comes to considering how you want your business to generate income, there are things that you need to consider, such as the target audience. We cannot compare a large engineering works company with a multinational that sells helmets for puppies. Therefore, you need to ask yourself who your clients are or how your clients access your products and services.
Income model for companies; 5 classic and modern ways for this
Lucky for you, technology has changed and now there are more different options and more types of payment, which facilitates the arrival of new income models that make more flexible the question of how to generate money for a company.
In this article, we will look at some of the most common income models for today’s businesses. Let’s go!
Single payment. (A quite common income model)
It is the classic one. When you go to a bakery, you pay for your loaf of bread and then you leave. When you go to a supermarket, you pay for your grapefruit-flavoured isotonic drink, and then you also leave.
What happens is that, in times of digital transformation, things get complicated. For example, if you have an online store, you should be very good at making your payment process simple and effective, don’t let your sales go by doing dodgy things. In fact, some studies claim that almost 70% of ecommerce sales are aborted during the payment process. Beware of this, this is actually quite important
Payment by subscription. (Another popular income model)
It is another popular one. From the electricity bill to the subscription to television channels, thousands of companies use the subscription payment model, used by millions of users every month.
This income model has many benefits, such as customer loyalty and a constant flow of income, but also requires companies to perform a magnificent job in order for the users to keep the subscription active, and the effort to have an excellent customer service that ensures that the company takes care of the clients as soon as a problem arise.
Advertising
It is a way of indirect income, which works mostly in media. The company (a television channel, a radio station, a newspaper, etc.) offers its product free of charge to thousands of people, and obtains income through the businesses that are advertised.
Although this income model has always been linked to popular media, nowadays , you can do that from home and with talent and hard work, this is the power of internet, anyone can turn their website, YouTube channel or Instagram profile into the mass media. Yes, we do know this is not easy, but it’s not impossible.
Commission. ( a different income model that is quite interesting)
It’s about selling products that are not yours, but from third parties, but these report a profit for each sale (which will be paid by the “owner” of the product).
Although it is another classic income model, again the Internet has transformed and expanded the concept. From “dropshipping” to the affiliate programs, new ways to obtain commissions have proliferated, turning the commission model into a very flexible concept, which has been adopted by thousands of companies and individuals.
Freemium. (this income model is quite trendy at the moment)
As we mentioned, this one is quite trendy, and it has found the right place in things such as mobile apps.
As we already mentioned, technology has facilitated the adoption of income models that could hardly be established in other contexts. Businesses such as the online sale of software, both for the consumption of individuals and for companies, have fostered this model in which most of the product (either software for companies, an app, or a videogame) is offered free of charge and the user, if he wishes, pays for supplements or improvements.
This is a fantastic way to publicize the product and reach a large number of people who might not want a single payment purchase or a subscription, but then they become clients as soon as the products become free. Keep in mind that, only a small part of the clients will pay for the improvements that are offered, but that can also mean significant income if the product reaches thousands or even millions of people…
These are 5 of the most common income models, but there are others, and technology will continue to facilitate new ways to earn money.
And another thing that technology can also achieve is to help improve customer service. Do you want to know a great way to achieve this? Take a look at Pandora ITSM.
Pandora ITSM is software that has, among other features, an incident management system (help desk software) that will help provide good customer services for companies.
In addition to this, Pandora ITSM has other features that can also be very interesting for a company, such as an inventory, a project management system or a vacation manager, among others.
Do you want to know what Pandora ITSM can do for you? Click here: https://pandorafms.com/en/itsm/
Or you can also ask us any question you might have about Pandora ITSM. You can do that, thanks to the contact form that you will find at the following address: https://pandorafms.com/en/contact/
And don’t forget to leave a comment in the comment section, we want to hear your opinion! Do you know another income model? Have you ever seen a new interesting income model? Do let us know by writing in the comment section down below! Your comments might help different readers. And also have you checked our other articles? We have already talked about customer service on them! Take a quick look at them!
Thank you very much and don’t forget to…
Send us your questions! We will be glad to answer them!
The Pandora ITSM team will be happy to help you.

by Pandora FMS team | Last updated Jun 10, 2021 | Community, Geek culture, Tech
Webcam cover; discover some reasons why you need to protect your PC
Perhaps you like to use your computer in summer, you know that special season when you run around your house in your underwear and you think that nobody can see you. Or perhaps all members of your family show up out the blue in the screen of your phone. Or maybe someone can detect whether you are at home, at work, or traveling. Or they might be able to spy you and find out what you do when you work with your computer. This is not a joke, if you have a webcam, you are in danger and everyone should respect your privacy.
The truth is that there are many good reasons why you shouldn’t allow anyone to access the webcam of your laptop or smartphone.
The problem is that there are evil people out there who actually think this way and they are able to attack our privacy. From “voyeurs” to people who are interested in accessing details of our private lives or other important top secret data, such as passwords. What can we do if we come across someone like that?
Some people are already aware of the problem and take steps in order to protect themselves. We are pretty sure that you’ve seen at some point people who use laptops on the street or in coffee shops; and these people protect their webcam of their laptops with stickers, or a small plastic thingy, or even a post-it note. There are many different ways to have a webcam cover. In fact, some companies have realized that this is quite essential and have launched all kinds of small items (nicely designed) in order to have a webcam cover in a more elegant way. Anyway, what’s important is to choose a safe thing in order to cover your webcam so that nobody can see what you do.
When it comes to mobile phones, here we are talking about a really dangerous issue. To be honest, we take smartphones with us everywhere, and these are part of important moments in our lives and most of them have cameras that can send any image, so these cameras should also be protected. However, in this case, not many people actually do this.
Whether on a laptop, whether on a smartphone, whether on a tablet, or in any camera from a device which can be accessed via the Internet, the truth is that you should use a tool for webcam cover so that nobody can access it and spy you.
Yes, despite all the potential risks, there will always be people who consider all these things a bit “too much”. Maybe you’re one of them. Why do you think so? Let’s have a look at some additional factors so that you take into account this type of protection:
- It’s quite easy to access the webcam of your computer. “Malware Infection” of your device can happen through different ways, such as when downloading software, or when you enter a website or when you download something that was attached in an email, among other things. In addition to this, some apps, which are available for free download, these might access our webcam, and sometimes we authorize that without even realising it…
- This type of malicious software is more popular than you might think. It is known, as “creepware” and it’s quite popular. In fact, there are communities of webcams spies that are called “voyeurs”, and ill-intentioned people, who exchange pictures, videos and malicious programs. Although it is impossible to know an exact figure, it is estimated that there are thousands of “infected” devices around the world. Be careful, yours might be one of these.
- You might think that the LED from your camera will warn you if your camera is on, but sometimes it won’t work like that. In fact, this is not a safe method to know if the camera is being used or not. They may be unauthorized access to the camera without the use of the LED lights, so some people might sneak around and spy you and you won’t even notice.
- This type of “malware” (malicious software) is quite easy to avoid and protect. Unlike other types of infection, when you might actually need the intervention of computer professionals, when it comes to spyware the best effective remedy is usually to install a physical tool that blocks the camera to avoid spying in order to gain more security and to be able to use the camera when you need it.
As you can see, these are some good reasons for webcam cover that we can find in your electronic devices. Yes, if at some point you want to use one of your cameras remember that you might be vulnerable to potential spies …
So this is it, we have seen some reasons why you need to be very careful with the cameras of our devices. Do you want to find out more?
It would be great if you could take a few minutes to discover Pandora FMS. Pandora FMS is highly flexible monitoring software that suits the needs of your business or organization. Pandora FMS is able to monitor devices, infrastructure, applications, services and business processes.
You already know that monitoring can be very important for a company. Do you want to know what a good monitoring software can do for you? Click here to learn more about Pandora FMS : https://pandorafms.com
Many businesses and organizations around the world, and universities, corporations, insurance companies, hospitals, transport companies or public entities already use Pandora FMS. Do you want to discover some of our clients? Click here : https://pandorafms.com/customers/
Or you can ask us any question you might have about Pandora FMS. You can do that using the contact form, which is found at the following address:
https://pandorafms.com/company/contact/
And don’t forget to leave a comment in the comment section down below, let us know if you have found a different webcam cover, we look forward to hearing from you!
And remember that…
Our Pandora FMS team is a great team and they will be happy to help you!

by Pandora FMS team | Last updated Aug 21, 2023 | Remote Control
Do you have a remote management system? Remote management software, also known as remote desktop software, these are programs that will allow you to access the contents between different computers. The only requirement is that these computers must be turned on and need an Internet connection, but it does not matter if they are miles away!
Many people have never used this. These are widely used programs in some areas, for example in computer technical assistance.
If you have had a computer problem, for example at work, you will surely remember a situation like this. After calling the technical assistance service and after installing a small program, suddenly your computer goes crazy and you realise something’s up.
After this paranormal phenomenon, you will find a remote support technician, who will take care of solving that problem with your computer. Currently, remote management systems are quite helpful for people who work in computer support or maintenance, because these allow them to save a lot of time and money on travels, this way they are able to solve many problems and carry out different tasks from a distance.
In this article we will see some examples of daily situations with clients, and how a remote management system will help you and will make your life a little easier.
EXAMPLE 1
Your grandfather has bought himself a computer! After fighting with technology throughout his life, your grandfather Paquito has changed his mind and has bought himself a 2,000 € laptop, and now he calls you all the time because in his screen there are all kinds of weird messages (updates, etc) and he doesn’t understand why and he also wants to get back to playing his online games on his computer.
The problem is that your grandfather lives 180 km away, and it’s just too expensive to go to Seville to find out what happens every time he has a problem. And he also keeps having more and more problems over time.
With a remote management system this would be easier for you. You just have to ask your grandfather to install an agent on his computer (this is quite easy) or you can install it yourself in his computer, and every time you need to help solve a computer problem you could access his desktop remotely. This way, your grandfather could play those online games he loves, without interruptions and you could live more calmly. Easy-peasy, right?
EXAMPLE 2
Teleworking has entered your life! Your dream has finally come true. Your boss has offered you to work from home twice a week, and the first thing you did , it was to buy a lot of cosy pyjamas to enjoy those moments of glory that you will have by working from home, with a coffee and toast in your hand.
But, suddenly, a chill has run down your spine. What happens if every time I work from home I forget to copy in the USB important material that I need (such as files) and then I can’t work from home? The experience could be a disaster as you could lose your teleworking option! And if you cannot telecommute, what will you do with those pyjamas?
Don’t you worry dear reader. With a remote management system you can access the desktop of the computer that you use in your work. You only have to leave the agent installed on the computer you want to access and ask one of your colleagues to turn it on when you need it. So enjoy your pyjamas!
EXAMPLE 3
You love to travel you cannot help it. But you do not like to carry the computer you use to work on your trips (you could lose it and it contains many files that which means most of your hard work), and yet you have to access its content from time to time.
How will you do it? Do not worry, it’s easier than it seems. You just have to install an agent on your home computer and ask someone (your sister Florinda who shares a flat with you) to turn it on with the router when you need to access it. Thus, you will not run the risk of losing the computer on which you keep most of your work and you will be able to access your desk comfortably when you need it. So now, don’t you think the Fontana di Trevi now looks a little bit more beautiful? Enjoy it!
EXAMPLE 4
You love nature! For you there is nothing better than a walk in the countryside. You love birds, trees, and even dung beetles. Even a walk around the park in front of your house seems like a little wonder! You love that freedom when working by the shade of a tree while breathing fresh air.
However, the computer in which you work and in which you have your entire files safe is placed in your home and you cannot take it out of the house, as it’s too big. How are you going to solve this problem?
It’s very simple, again a remote management system can help you. You just have to install the agent and leave the computer and Internet connection on, and you can access your main computer from the laptop that you take on your trips. This way you can mix your passion for nature with your work.
What do you think now? These are just some fake examples of situations in which a remote management system could make your life easier, but I’m sure you can think of many more. Do you want to share them with our blog readers? You can do so by leaving a message in the comment section that is located at the end of this article.
Oh, and do not forget that Pandora RC is a great remote management system.
Do you want to know what Pandora RC can do for you? Click here: https://pandorafms.com/en/remote-control/
Or you can ask us any question you might have about Pandora RC in the contact form that can be found at the following link: https://pandorafms.com/en/contact/
The Pandora RC team will be happy to help you!
by Pandora FMS team | Last updated Sep 26, 2023 | Customer support, Tips
Are you a call center manager? Or do you work in a call center? Do you like this type of job? Do you have customer service experience? Are you willing to take this path?
A call center manager is a difficult job, which requires a great skill in order to manage teams under pressure. Apart from the usual leadership skills that you must have in order to manage teams, for this type of job, you must also have specific qualities.
In this article we will look at some skills that a call center manager must have in order to carry out his job properly. Shall we start?
1. Leadership
If you are a manager, you must have the qualities to be a good leader. But when it comes to supervising a contact center that leadership is even more important. With a job in customer service, stress and fatigue will be quite common. Therefore, a good call center manager should be an energetic person, someone who is capable of remaining calm.
2. Self-control is quite important
This is one of the qualities of a great leader. In certain call centers, which receive hundreds of calls every day and demand a quick solution to their problems, stress can easily appear. Therefore, the call center manager must be able to control himself, both towards his clients and his team. The call center manager is the captain who runs the ship, and a captain shouldn’t get nervous.
3. Empathy and communication skills
These are personal and professional qualities that a good manager must have. As the leader of a group, your ability to communicate the needs of the service and to put yourself in someone’s shoes will be a very useful tool for the work to go forward effectively and in a pleasant environment. As head of service, and when facing clients, these are very useful skills to be able to communicate with users properly and to be able to understand their needs, and this will be the first step to be able to solve these effectively.
4. Don’t forget to motivate them
A call center manager should know how to use his energy; this means that he should know how to use his energy in order to carry out his job effectively. And also one of the most important things about a great leader is that he/she should know how to motivate his/her team.
Yes, we know that customer service is not easy. Therefore, a good supervisor should know how to motivate his/her team, so this person should also take into account that each person is different. Therefore, the manager must have the necessary sensitivity to treat each of the members of his/her team as they deserve.
5. Experience and knowledge
We already know that being a call center manager is not an easy task. A good manager is that someone with experience in the industry, and might have previously occupied this position before. In addition to this, you must have a broad knowledge of the company and the needs of the service, and should have a continuous contact with all the departments of the company, which will be quite helpful.
6. Versatility
A good call center manager does not sit on a throne. Instead, he/she is an accessible and dynamic person who does whatever necessary in order for the service to work. If you must directly deal with a client, then do it. If you have to perform management tasks, then you execute them. If you have to talk to a member of your team who is going through a bad time, sit down with him, and talk to him. Your versatility is a value which will be very appreciated by the members of your group.
7. Diligence and responsibility
In a call center, the pace can be frenetic; you probably know this if you work in that industry. You must deal with clients quickly and efficiently. Clients not only want their demands to be solved, but they want their problems to be solved as soon as possible. So the call center manager must have the diligence and responsibility that is needed in order to carry out the work effectively and without wasting a lot of time.
8. Management skills
In addition to all the personal qualities that you must have in your everyday life, do not forget that a call center manager is exactly A manager. A good supervisor is aware of the importance of customer service for the company and always looks for ways to improve the service. In order to achieve this, this person uses the methodologies in order to suit the needs of the work and ensures that his/her team can work with the proper tools, and must have extensive knowledge about the technological options available in the market.
And so far we have gone through some of the qualities that will help a call center manager in order to carry out his/her work properly. Do you want to see something else?
At this point, we would like to introduce you Pandora ITSM, our help desk software that will help you.
Pandora ITSM is a tool that includes, among other features, an incident management system based on tickets, which will help you in the operation of a call center
Do you want to find out more about the Pandora ITSM help desk tool? Click here: https://pandorafms.com/en/itsm/help-desk-software/
Or you can also ask us any question you might have about Pandora ITSM. You can do that with the contact form that you will find at the following address:
https://pandorafms.com/en/contact/
And don’t forget to leave a comment in the comment section down below, we want to hear your thoughts. What do you know about these qualities of a great call center manager? Do you know some more qualities for a great call center manager? Do let us know!
You can also ask us your questions by leaving a comment in the comment section.
We will be quite happy to answer your questions!
And the Pandora ITSM team will be happy to help you!

by Rodrigo Giraldo Valencia | Last updated Apr 26, 2023 | Community, Integrations
Data Guard monitoring: find out all about it in order to monitor it
What is Oracle Data Guard?
Before getting started with the tutorial for Data Guard Monitoring from Pandora FMS, first, we need to understand what Oracle Data Guard is. In order to understand this, we need to know what the protection modes of Oracle Data Guard are and how these are configured. It’s fair to say that your configuration always runs in one of these three data protection modes: Maximum protection, Maximum performance (default operation mode) and Maximum availability.
- a) Maximum protection
This protection mode guarantees that no data will be lost if the main database fails. In order to provide this level of protection, the “redo” data which is necessary to retrieve each transaction, must be written both in the “redo” log on the local line, and in a “redo” record on standby and at least , a database on standby before the transaction is carried out. To ensure that no data loss is generated, the primary database will be closed in case a failure prevents it from writing its “redo” sequence in a synchronized database on standby.
In this data protection mode, we prioritize the protection of data over the primary database. In this context, Oracle itself recommends administrators to use at least two standby databases in order to protect a primary database, which runs in a maximum protection mode.
- b) Maximum performance
This protection mode provides the highest level of data protection without affecting the performance of the primary database. This is achieved by allowing a transaction to be confirmed as soon as the “redo” data necessary to recover that transaction is written in the local “redo” record. Then, the “redo” data sequence of the primary database will also be written in at least one waiting database. But, that “redo” sequence will be written asynchronously, regarding the transactions that create the “redo” data.
When using network links, with enough bandwidth and latency, this mode of protection provides a level of data protection that is quite similar to the maximum availability mode and, with a minimum impact on the performance of the primary database.
- c) Maximum availability
This protection mode, in turn, provides the highest level of data protection, without affecting the availability of the primary database. It’s exactly what happens with the maximum protection mode, in this case the transactions are not compromised, until all the “redo” data which is necessary to recover those specific transactions, have been written in the “redo” online record and at least, in a synchronized database. We must also say that, unlike the maximum protection mode, if an error prevents you from writing your “redo” sequence in a standby database which is synchronized, then the primary database will not shut down.
On the other hand, the primary database will operate in re-synchronization mode, until the fault is corrected and also until all the registration spaces have been resolved. When these spaces have been resolved (all of them), then the primary database will automatically resume its operation in maximum availability mode. This mode guarantees that if the main database fails, no data will be lost. However, we must bear in mind that this will happen only if a second eventual error does not prevent a complete set of “redo” data from being sent from the primary database to at least one standby database.

What are the prerequisites for these three protection modes?
Before getting into the different ways of Data Guard Monitoring, we need to analyse these requirements. So let’s have a look at this:
For maximum protection, we have to:
-
- Redo the file process: LGWR.
- Network transmission mode: SYNC.
- ‘‘write to disk’’ option: AFFIRM.
- Redo standby records: YES.
- 1.1.2 For maximum availability, we have to:
- Redo the file process: LGWR.
- Data transmission mode: SYNC.
- ‘’Write to disk’’ option: AFFIRM
- Redo standby records: YES.
- 1.1.3 For maximum performance, we have to:
- Redo the file process: LGWR or ARCH.
- Network transmission mode: ASYNC, only when LGWR is used.
- ‘’Write to disk’’ option: NOAFFIRM.
- Redo standby records: No, but it is recommended and necessary for real time.
2. So how do we carry out Data Guard Monitoring?
First, you must configure a standby instance for monitoring. In order to be more clear about this, we have to say that a back-up instance in the data protection feature of Oracle, guarantees high data protection, high availability and a very good chance of recovery, after disasters in business data. Let’s see, then, what we should do before Data Guard monitoring. For this purpose, we must configure an Oracle instance. Then, after installing BMC PATROL for Oracle, we must load the Knowledge Module (KM) in BMC PATROL Console, and then configure the product, this way, we can obtain parameter data from BMC PATROL for Oracle.
We recommend readers to visit this link, where they can analyse each task related to the configuration of a standby instance for Data Guard Monitoring. On the other hand, you must have SYSDBA privileges in the database, in addition to the respective access permissions, which are needed. And also, the correct user credentials in order to configure a standby instance.
We must bear in mind that the PATROL account must have read access to the tnsnames.ora file. Then, we must confirm that ORACLE DATAGUATD.kml is loaded in our system. In order to load a knowledge module, we must do this from the PATROL console:
In the tab called “Common Tasks”, located in the Task Panel of the Central Operator, we must click on the icon “Load Knowledge Modules”. Then, in order to start the wizard, we click on “Next”. Then, we select the check boxes for the managed systems, where we want to load knowledge modules. Then, we click on “Next”. Afterwards, we select the check box for each Knowledge Module or KML that we want to load. We click on “Next”.
Next, we must look for the Individual Knowledge Modules. KML, in turn, can be found in the tab “Lists of Knowledge Modules”. Finally, we click on “Finish”.

2.1. A standby instance for Data Guard Monitoring in the Central PATROL console
In this case, the standby instance type is the logical or physical standby mode. Then, in order to configure the standby instance, we must click on this video to learn how to configure an Oracle Data Guard instance, to monitor a PATROL environment. Let’s say that it is necessary to verify that the user of the PATROL console has the privilege of executing SQL*Plus commands. From the ORACLE_DATAGUARD application, we must click with the right button to select: Knowledge module commands> install DataGuard instance.
Then, we select the main instance of the “Configure DataGuard Instance” dialog box, and then click on “Apply” and “Exit”, in order to close this dialog box. In the “DataGuard Instance Configuration” dialog, we must enter the data that we will show down below (details of standby instance) and then click on “Apply”.
When it comes to the field “TNS entry waiting”, we must use the name of the TNS service entry, which we will use to connect to the standby instance. And in the “Username and Password”, we must write, the username and password that we will use to connect to the standby instance. We need to keep in mind that we should not write “as sysdba” in the password.
2.2 The display of the ORACLE_DATAGUARD instance, in the PATROL Central interface
After configuring the standby instance, the hierarchy of the data implementation in the PATROL Central interface goes like this:
- The ORACLE_DATAGUARD application represents the data protection instance monitoring (Data Guard monitoring) feature.
- Primary instance database name.
- DGCollectors application with parameters that collect the data for the standby instance, CollDataGuardia and CollTimeDataGuard.
- DGPARAMS application, with data delay parameters and with time for each standby instance (configured). Such as: ApplyLag, LogTranferGap, LogApplyGap and TransportLag.
- DGConfigurationStatus: it shows us the configuration status of DATAGUARD.
- StandbyStatus parameter: this one checks the configured standby database, and runs in a data protection environment.
2.3 A standby instance for monitoring in the TrueSight console
The user has the chance to configure a standby instance, for Data Guard monitoring, in the TrueSight console to apply the instance in a PATROL agent. But, before configuring a standby instance, the user must have a configured instance of ORACLE DATABASE.
In order to carry out the configuration of the standby instance, we must:
- Determine a monitoring policy (monitoring) in TrueSightConsole to select the parameters: We must click on “Add”, then select “Monitoring Solution”, and establish the Oracle database. Regarding the “Version”, we must choose 9.7.10. Then, regarding the “Monitor Profile”, we need to establish OracleStandby DataGuard. On the “Monitor Type”, we have to choose OracleStandby DataGuard.
- We must enter the name of the main instance and then click on “Add” in order to enter the details of the standby instance.
- Then we enter the Standby instance information and click “OK”. With this, we must clarify that, in the field “TNS standby entry “, we must write the name of the TNS service entry, which we will use to connect to the standby instance. Then, we must write the username and password, we have to keep in mind that we should not add “as sysdba” in the password.
- We must click on “Accept”, in order to save this monitoring configuration of the standby instance. Let’s clarify that after creating this standby instance, the implementation hierarchy for the application has an important similarity to the PATROL Central view.
2.4 Preparation of standby instances, for monitoring with batch configuration
From Pandora FMS, we recommend readers to resort to these instructions, so we prefer to talk about the manual configuration of a file, in batches, for the standby instance. So, to configure a batch configuration file, we can use the DG_batch_conf_sample.wri file as a template. Then, from a command prompt, we do the following:
We open the file DG_batch_config_sample.wri in the following location, depending on the operating system of each user:
- For Data Guard Monitoring, from Pandora FMS we recommend readers that have UNIX operating systems, to locate the file in
$ PATROL_HOME /.../ Oracle / conf .
- Windows users can find the file in
% PATROL_HOME% / Oracle / conf .
Once the file is found, it is necessary to edit the Oracle System ID (SID) and edit the values of keywords, in order to reflect the instances that you wish to continue. Then, it is necessary to save the file as DG_batch_conf .txt , in a text-only format.
As soon as we find this file, we must begin to process the file itself, in order to configure the instances in this PATROL agent point. So, when the discovery completes the processing of this file, the name of the file itself will change to DG_batch_conf .done .
In order to successfully complete the batch configuration or to correct any eventual errors, we can verify the following files (which are saved in the same directory location as the file, in DG_batch_conf_sample.wri): DGBatchConfig .log . and, DataGuardConfig .log .
Now, for webmasters and for IT professionals, we recommend Pandora FMS, which is the most flexible monitoring software on the market, this one is able to monitor infrastructures, devices, business processes, applications and services of all kinds. Pandora suits the needs of your business. If you don’t know us, you can get in touch with us in this contact form.
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
Or if you have to monitor more than 100 devices you can also enjoy a 30 days FREE DEMO of Pandora FMS Enterprise. Get it here.
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!

by Pandora FMS team | Last updated Apr 23, 2024 | Community, Geek culture, Tech
What is smart retail? How will this change the future of retail?
Some people think that stores will disappear over time. We will buy everything online, and if we want to “take a look” at the products that we want to buy, we will do that while sitting on the couch at home, via virtual reality.
However, it’s quite difficult to imagine that the common habit of shopping will disappear. A lot of people enjoy going to a physical store and they also enjoy searching for the product, it’s an undeniable pleasure for them, even when they can easily buy anything from their computer.
However, the stores of the future will change, nowadays some of them have already changed for the better.
When we talk about “smart retail”, we are talking about the use of techniques and technologies used to make the customer experience more satisfying and more personalized.
The idea of smart retail is to close a sale, but also the idea is to get the customer to experience a customized experience so that the customer wants to return to the establishment in the future. In order to achieve this, concepts such as “customer journey” in the store, are quite relevant.
If we have a deep look into it, the customer journey is the route that the client takes which goes from observing the showcase of the store until the client leaves after purchasing a product.
What is that route? What are the specific moments that are part of it and create the customer experience? How can we improve each one of those moments and unite them in order to create a complete and personalized shopping experience, which will satisfy the client in order for the client to come back to the store? This is the kind of questions that are answered with smart retail.
But, how will the customer experience change in the future? Okay let’s say that…
The interaction with the customer will start a few meters away from the establishment. Given the proximity of the client, personalized messages will be sent to the customer’s phones and these will let them know about their product and the price or discounts.
Once the customer is in front of the store, the client will be quite impressed with the store window. Different screens and three-dimensional effects, designed to attract the attention of the clients, will appear before their eyes, this will prompt them to enter the establishment and this way they will start their own journey. In addition to this, these stores will be able to detect the gender or age of the passer-by, this way the stores will offer personalized advertising.
Once inside, we will see different things from what we find in a store nowadays. These will have become “exhibition halls” (like “museums”) in a way that the products will be there for us to observe, touch or test.
But wait, there’s more: the products on display will be part of an environment and a story, in which smells and sounds will be integrated with the customers in order for the clients to be part of it, by touching their emotions.
And what will we do if we actually want something? It will be as easy as ordering the purchase through our phones or screens which will be enabled for that purpose, and our products will then be sent automatically to our house.
But bear in mind that some products will also be available to us immediately if we wish, but it won’t be that common.
The customer service will also be quite different. Although some establishments will keep human employees, in others, they will be replaced by robots and screens equipped with artificial intelligence. Probably, this will also determine the opening hours and days, which in many cases will be extended, and it will reach 24 hours and 365 days a year.
The fitting rooms will also be very different. These will also be equipped with artificial intelligence, and these will know your tastes and your measurements, and will be able to advise you and recommend products that might be interesting for you.
Finally, the payment method will also be very different. The cashiers and the queues will disappear for good. The customers will pay for their purchases through their phones. In some cases, this will be done automatically, so that when the customers leave the establishment, they will get charged straight away.
But, in addition to more “standard” stores, other highly specialized establishments will offer personalised experiences for customers who are keen to live unique moments. Do you want to buy Star Wars products? How about doing that inside the Death Star while a big space battle is held outside? Do you want to buy products for diving? What if you could do that in the environment of an impressive seabed? The possibilities will be endless…
Now that you know what smart retail is and the changes that we will see in the stores of the future, you need to know that technology will be essential when developing these. And by technology, we mean monitoring. And when it comes to monitoring, the best thing is Pandora FMS.
Wait; don’t you know what Pandora FMS is?
Pandora is a very flexible monitoring software, which is capable of monitoring devices, infrastructures, applications, services and business processes.
Discover what Pandora FMS can do for you.
Companies and organizations all over the world already use Pandora FMS. Do you want to discover some of our clients? Click here.
Or you can also send us any question you might have about Pandora FMS. You can do that through the contact form that can be found at the following address.

by Sancho Lerena | Last updated Apr 26, 2023 | Community, Geek culture, Tech
Programming skills: 10 useful skills to improve your ability.
Are you a programmer or are you thinking about learning how to code? You might already know that is not an easy task. Can anyone be a programmer? We could say that, with enough effort, yes. But knowing how to code and to be a great programmer are two different things.
Many studies estimate that the number of professional developers in the world lies between 16 to 18 million. Do you think this is a great figure? It’s quite likely that this number continues to increase in the following years. Although surely you don’t want to be just one more, you want to be one of the best.
To stand out at any job is not an easy business. It demands effort and certain abilities that not everybody has (at least at the beginning). Do you want to know how to be a great programmer? In this article, we’re going to look at some of the traits that programmers themselves consider to be fundamental to excel at their job. Let’s get started!
Be eager to learn
IT is a science which is constantly evolving. New programming languages, new versions of already existing ones, new knowledge to acquire… As a job, it is very difficult to reach the top if you’re not constantly updating yourself. And to be updated, the interest for learning new things is a must. If you like and enjoy learning, you’ve chosen the right job. Your curiosity will be your best attribute. If you never stop reading and digging knowledge, you’ll be better at your job and you’ll enjoy it more doing it.
Develop a competent analytic capability
If you are a professional programmer you already know about this one. To a great extent, programming is to know how to fix problems. Because of it, being able to understand the problems and divide them into smaller problems easier to handle is quite useful in this profession. Moreover, if you have skills to think in a logic manner, you’ll be a step ahead and your work will be better.
Be creative
In addition to being analytical, to develop and to be able to solve problems, you’ll find quite handy to have a creative mind. If you take programming as a monotonous task, you’ll probably struggle; you’ll find it more difficult to keep going, and overall you’ll get bored quite a lot. If you stimulate your creative side, not only your work will be better, but you’ll have fun doing it.
Be mentally strong
Is one of the main reasons why people don’t even think about programming as a career path. To be a great programmer you’ll need a significant amount of mental strength. You’ll have to gather a wide range of knowledge and, not only that but also you’ll require enough dexterity to manage them wisely. Also, you’ll need to be able to manage stress efficiently. Nobody said it was going to be easy!
Be patient
Programming is the kind of job in which results aren’t expected in a short-term, but it’s rather more about mid to long-term achievements. Because of this, you’ll frequently need strong doses of patience. Usually, you’ll find yourself facing problems difficult to solve which will test your poise once and again. If you’re capable to handle these situations with a stiff upper lip, it’ll be more likely to succeed at your job.
Grow a detail-oriented mindset
As it is said: ‘the devil is in the detail’. To be a great programmer, you’ll need to be meticulous in your job. Your code will be of a better quality and you’ll avoid problems and save a lot of time by not having to look for the reason why something is not working.
Know how to communicate and work with others.
The image of someone who works all day locked in the garage with a computer doesn’t resemble the truth of how great programmers look like. It is common for programmers to work with other people, being other developers or another kind of professionals, as executives or clients. This is why the ability to communicate and work effectively with others will be a key factor in your work.
Likewise, keep in mind that unless you work only for other programmers, you’ll find quite handy to have some good notions of other fields of knowledge, like economics or the ins and outs of a business, among many others.
Awareness of your own limitations
You know what they say: don’t spread yourself too thin. To succeed as a programmer you need to be mindful of your know limitations. Accept that, huge quantities of work or coding for those who are not skilled enough (being the reason of this because of a lack of knowledge, experience, or any other reason) can cause serious problems. Therefore, to be aware of one’s own strengths and acting accordingly will also be something to keep in mind.
Be flexible
Besides having a positive outlook towards learning new things, you’ll need to be flexible at your job as well. In the ever-changing world we live in, a dynamic profession as programming will require of you to adapt yourself to new situations. Along with this, solving problems involve to develop an open mind and not to dwell on paths which don’t lead anywhere. And, of courses, will need the flexibility to work with others in different fields and people with no technical knowledge.
Be passionate
To finish with, here’s the most important one. We could say that to be passionate is a quality needed in any job, but to reach the top in such a demanding world as coding is, it’s a must. If you have no passion for your job, you’ll find enormously difficult to reach far. To keep the flame of passion alive, never stop learning and looking for new challenges.
These are some of the traits that developers themselves find to be essential for a programmer to have if he or she wants to be successful at his or her job. But don’t get discouraged, some of these traits can be nurtured or improved with practice, providing you have the required passion. Are you a programmer already? Surely you have found other indispensable traits. Would you like to share them with us and give us your opinion on how to be a great programmer? You can do it in the comment box down below. Thank you so much!

by Pandora FMS team | Last updated Aug 14, 2023 | Enterprises
A lot of people love writing. Some of them have managed to turn their dream into their lifestyle, and others would like to do that someday.
Although a few years ago the number of jobs for a writer was a bit more limited, with the rise of the Internet and also the rise of new media and business blogs, nowadays the possibilities are endless.
If you are a writer, one of the most common ways to carry out your job is as a “freelance”, which means independently and for several clients.
The freelance work matches perfectly the flexibility offered by the network. The freelance writer can work for clients who are located in various countries around the world without having to travel to a particular workplace. They will also enjoy their independence to organize their work and their schedules.
What happens is that as a freelance worker there are some disadvantages; the potential uncertainty when relying on clients who give you a job and an income, and also working odd days and sometimes at strange hours, miscellaneous expenses or even the famous “avoid getting sick”. These thoughts are suffered by the freelance.
Anyway, the decision is yours, and if you love writing then, be a freelance and the Internet can be quite good for this. Let’s look at some aspects about being a freelance.
What should I do in order to become a writer?
If you’ve thought about becoming a writer, you should assess, first, if your work is good. Bear in mind that someone must be willing to pay for it.
Good spelling is essential and you should have some basic knowledge of SEO, because, your articles will be published in some website.
Although there are many different styles when it comes to writing, the richness of the language will also be assessed, but also bear in mind the clarity and simplicity in the writing.
Finally, it will also be great for you to know what you write about because you’ll see if you’re able to join your writing skills and also to be an expert in some area, This way you will find better-paying jobs.
What are the steps to become an online freelance writer?
As in many other jobs, when you start a freelance writing career, a single path doesn’t exist. As you can imagine, before selling thousands of books or working for big media, the important thing is to promote your work. In order to achieve this, there are several ways.
1. Create your own website
Although it is a bit difficult, it can give very good results in the medium and long term. You own website can provide a quick look of your talent and it will give a great business look for your clients and if this is well built, it will give the sense of professionalism.
2. Get known in forums
There are some forums used by publishers and editors in order to establish collaborations, they look for people who can write in blogs. This can be a great way to find your dream job, become popular and earn some money.
3.Advertise yourself in work platforms
Nowadays there are multiple platforms used to connect freelancers with their potential clients. Often, the professional offers a particular job at a fixed price and the customer gets in touch with him/her if they wish to purchase.
How can I become a better online freelance writer?
If you’ve already been there, either because you are now popular or because you already have the experience of working professionally as a writer, for example in a newspaper- you might need to keep improving.
Here, the objective to be achieved will depend on your career aspirations and your own creativity. Here are some examples that can give you some ideas.
1. Write for businesses
Today, more and more businesses realize the importance of having Internet presence. In order to enhance this presence, some of them hire writers, as freelance, in order to create content for blogs and social networks that will reach their users and potential customers.
This way, it’s quite important that you know all about the topic that you’re going to write about and find out all about it; the higher the quality and specialization of your job, the better your chances of finding a good remuneration.
2. Write for large media
It is one of the classic dreams of an online freelance writer. The mainstream media often offers good salary and offers greater visibility, which is a good incentive for those who want to aspire to a highest career.
Working as an online freelance writer is not easy. You will need to offer great quality in your work and should have certain reputation. But it’s not impossible. A lot of people have already achieved that.
3. Sell your own books online
This is the dream of many writers, to write and sell thousands of books, offer your readers a quality work so that you can change the history of literature. This has been the dream of many people for centuries. As you can imagine, it’s not an easy task, but it is not impossible.
If you want to become a Shakespeare of our XXI Century, there are multiple ways to achieve this, from publishers to self-editting your work and then sell these on your own website or some great online store. This will not be easy , but if you have enough talent, work hard and with some luck, maybe you will achieve that.
Conclusion
And here we have looked at some ideas in order to become a freelance writer to work on Internet, but we are pretty sure that you, dear reader (and perhaps you are also a writer), you have some good ideas too. You can share your ideas, using the comments section, which is right at the end of this article.
We are really looking forward to hearing your thoughts and comments so don’t forget to leave a comment in the comment section for everyone to see.
Thank you very much for participating!

by Pandora FMS team | Last updated Jul 7, 2023 | Customer support
In the past, customer service was very different from now. Nowadays customer service is a new experience for customers. Let’s have a look at it.
Have you ever heard about customer service? We are pretty sure that you’ve bought things online at some point. Although sometimes we might feel that things don’t change and stay the same for a long time, little by little things change and we don’t even realise.
This is exactly what happened to customer service. Years ago, customer service was carried out by telephone or face-to-face and it was focused on solving the complaints or problems of the customers, in a friendly and quick way. And that’s it, nobody cared about anything else.
Now things have changed.
In a highly competitive environment, each contact with the customer is an opportunity to sell or, at least, to build loyalty. In addition to this, a greater number of communication channels (mainly Internet) have broadened customer service, and now it has been turned into something different, a wide world full of opportunities.
What is customer service 2.0?
Customer service 2.0 is a new way of placing the customers and their customer experience on top, this way the customer service is the most important value, and the use of technology and new communication channels is an essential element in order to provide the best possible service.
This concept, which is very wide, can be broken down into many aspects, which provide a different way of understanding customer service.
Getting to know all about the client
In customer service 2.0, the client is not that gentleman who is there behind the counter to bother you with his annoying problems. On the contrary, by getting to know the clients, we find out what he likes and his needs, and because he is there, it means that this is another opportunity to let him know that the company works to achieve his satisfaction. Remember: in customer service 2.0 the client is the centre of everything and every time a client gets in touch with you, it is an opportunity to build loyalty.
Personal experience
Once we know all about our client, it is time to offer a personalized experience. I cannot think of anything worse than being treated in a robotized way, as if you were just another human on this planet. With customer service 2.0 each person has to be carefully treated, the employees have to actually care about the clients and their needs and they have to make them feel different from the others. Therefore, previously non-existent concepts such as “customer experience” are now valuable.
New channels
It is one of the biggest differences from the traditional customer service. In the past, as we mentioned at the beginning of this article, there was only one counter. And, some phone rang once in a while. And that was it.
Nowadays, the customer service world extends through any kind of channel. Websites, contact forms, blogs, forums, email, social networks, chats, apps … The channels are limitless, this way companies have a closer relationship with customers.
However, it is not always easy to manage such a large number of channels. So we have to be careful, common sense and professionalism are essential when managing customer service.
It is now bidirectional
It is a logical consequence of everything we have mentioned above. The multiple communication channels and new tools that allow us to analyse the information provided by clients make communication useful in both senses. Now it is not only the companies that offer customers useful information to solve their problems, but also the companies themselves receive valuable information with the interactions in the customer service, which allows them to know relevant issues and what the customers like and their needs, and common problems and it also lets us know what measures could be taken to increase their satisfaction.
Viral things
It is the most desired and also the most feared word by marketing and customer service departments of loads of companies. The rise of social networks has ensured that any message can reach millions of people in hours. With a good image, it can generate hundreds or even thousands of new customers. If, on the contrary, the image is negative, then it can damage the digital reputation of the company.
It is one of the reasons why customer service 2.0 has become so relevant and has increased even more the importance of customer service for the future of companies. This way it provides the best possible service. Be careful with this! Watch out!
Technology
This could be for any aspect of the company, and also in customer service. In fact, it is one of the key elements to carry out our customer service duties effectively. This way with technology people won’t go crazy with their work when having loads of complaints from people
A customer service 2.0 requires technological tools, which can help provide a better service.
Do you want to find out the one that we use?
Pandora ITSM is a helpdesk software that, among other features, has an incident management system based on tickets that can help you manage the customer service of your company or organization.
In addition to this application, Pandora ITSM has other very interesting features, such as an inventory or a project manager, among others.
Don’t forget to leave some comment in the comment section down below if you’ve enjoyed this article, we are looking forward to hearing from you!
Do you know another type of customer service? What kind of customer service you provide? Do you think customer service 2.0 is a good idea? Is it making our lives a bit easier? We want to know! Let us know with your comments.
Do you want to find out what Pandora ITSM can do for you? Alright then! Click here: https://pandorafms.com/en/itsm/
Or , you can send us any question you might have about Pandora ITSM in the contact form that can be found at the following address: https://pandorafms.com/en/contact/
The Pandora ITSM team will be happy to help you!

by Jimmy Olano | Last updated May 17, 2023 | Community, Network, Servers, Tech
Graylog2 VS Pandora FMS: a detailed comparison
Brief history of syslog and Graylog2
Before introducing Graylog2, we first have to dive into what syslog is. Its history dates back to 1981 when Eric Paul Allman used to work at Berkeley University in California and developed a software which would be the predecessor of modern email services, Sendmail. Therefore, they needed an application to report them of any event from each server in which Sendmail was running.
UNIX, integrated into its own kernel, had the ability to generate its own messages, which were stored in text files inside the file system. Eric Allman developed a kind of software that runs in the background (daemon), called syslogd, which was in charge of reading the files with said stored messages, and created a syslog protocol to send them to other computers (called collector) to analyse the data. You can broaden your knowledge about this if you read the RFC 5424 norm on the layers and their working structures (note: the norm indicates that all the components of syslog can easily stay in just one computer, although, the image shows sort of two computers communicating between each other. We must not confuse syslog with syslogd).

Syslog became so popular that soon the need for the collector to deal, not just with the log from the server which was running Sendmail, but also to receive the logs from the clients who were connected to that email server, as merging both documents chronologically was of great use -and still is- to track errors within the code. This way, syslog was given an absolutely different future than the one it originally had.
Graylog2 was born thanks to Lennart Koopmann in mid-2009, when he decided to create his own software due to the high costs of the monitoring software. According to him, the offer in this sector of open source code was nonexistent, but we assure you that Pandora FMS was in its 3.0 version.
Its official website is www.graylog2.org (although the site redirects you automatically to www.graylog.org) and its Twitter account is @Graylog2. This name change happened the 16th of January of 2015 with the release of version 1.0 (beta). In this article, we’ll use preferentially its original name Graylog2. During the last two years, it has achieved an explosive increase of users and the 27th of April of 2016 they released the version 2.0, being the version 2.3.2 the current version (by 19th October 2017).
Graylog2 operation
Both proprietary software and open software are going to stay with us for a long time and that’s Graylog2’s bet. Right, let’s crack on by talking about security and performance!
syslog, syslog-ng, rsyslog, logrotate and nxlog
Despite being free software, Graylog2 is not like a ‘black box’ controlled by third-parties, we are us the ones who have control over it. Thus, the data we input to this software is our responsibility, solely ours.
Keeping this in mind, our monitoring needs are for many devices, inside our local network as well as any network, and syslog only allows to send the information by UDP packages. These packages don’t provide ‘acknowledgement of receipt’, neither ‘shake hands’, so we won’t be able to use a safe protocol of encryption to ensure that our information doesn’t end up in someone else’s hands. We may think of installing a VPN (Virtual Private Network) everywhere to send them, but even so, any device will keep sending information. If the network fails or our Graylog2 server goes off or out of order, it could be of no good for our purposes.
That is the reason why, besides syslog, other solutions which send packages via TCP -that can implement safe protocols and guarantee the delivery of each one of the sent packages- in addition to other features, for instance, delivering those packages straight into a database engine as MySQL or file preprocessing and even its saving name to store them in an organised way in many devices.
Syslog-n has an open version and an enterprise version (this last one with additional modules) and is available for Linux and even there’s a version for Windows running with Cygwin. In spite of the many other existing alternatives, we’ll focus on rsyslog which appears in 2004 by the hand of Rainer Gerhards directly competing with syslog-ng and nowadays it comes preinstalled with Debian, CentOS, Ubuntu 16, (Debian distro which comes with it as default as part of Logrotate). For practical purposes the event logs from each computer stop being important once the’ve been sent to Graylog2.
What are we trying to accomplish with this explanation and what does it have to do with Graylog2? Well, Logrotate, being a hint in its name, is in charge of rotating and compressing, and erasing them periodically. If this were to be left undone, our disk would end up full. For Windows proprietary operating system from version 2000 (and all its successors) they have their own integrated service of:
- Applications event log (for example, failures when accessing a database with MS SQL).
- Related events with the Active Directory, a kind of technology that allows managing hundreds of computers by using domains with the help of DNS. Imagine the amount of data generated by one of these servers handling a tree or a whole forest of these domains!
- Related events (in another category) with the DNS, using or not any Active Directory.
- File replication, handy distributed backups which synchronise with each other.
- Security: for the administrators. Everything related to the access to the operating system such as managing users, failed attempts when writing your password, etc.
- Last but not least: the events related with the operating system and its interaction with the hardware, such as hard drive’s S.M.A.R.T., running time, restarts and forced shutdowns, etc.
We can even save our own test events in Windows. With the required admin credentials on the command line we can practice the following:
eventcreate /s nombre_servidor /t ERROR /id 100 /l APPLICATION /d "This log is a test"
The eventcreate command will save it to send it later to our Graylog2 server. Talking again about the subject of the transmission, in Windows, we can install an open source solution for this purpose: Nxlog. This software is available for Windows, Unix, Linux, BSD and Android: for the operating system as well as the application’s event log. How to know which is which? Let’s go back to the last thing we saw about creating our own events in Windows (in other operating system happens in a similar way) with the parameters “/t” and “/l” passing the importance and the origin of the log message. Let’s see:
Parameter “/t”:
- ERROR
- WARNING
- INFORMATION
- SUCCESSAUDIT
- FAILUREAUDIT
Parameter “/l”:
Graylog2: functioning and requirements
The functioning and the installation of Graylog2 are closely related, so to simplify it we have created this diagram. (It’s not recommended for other purposes than mere tests, as in a production environment it will be impossible to use it that way).

We’ll run iit with the recommended installation requirements (functioning include), pointing out that we’ll just install it in a Linux host, as it’s not recommended doing it with Windows:
- Graylog’s built-in server is coded with Java so we’ll need at least Java SDK 8. In essence, it’s in charge of receiving the logs of other devices (without the source data it won’t exist any process).

- Elasticsearch, based on Apache Lucene, both coded completely in Java (in its version v2.X, but not for a greater version with Graylog2 v2.2). This component is in charge of doing the hard work. Elasticsearch is a program which will receive ALL the logs and will do anything required for breaking down, classify, link and store the information no matter which format they come (it handles a great variety of protocols). We emphasize that it’ll be here where the whole of our data will lay and we’ll need several devices. Being this job hard, Graylog2 deals with it by using the following working scheme: the users normally use the last 30 days of log and up to a maximum of one per year, which is what they recommend for a system so it doesn’t get overloaded while doing it.Pandora FMS, instead, keeps constantly migrating its data with a “prediction server” in a transparent way to its users: you are the one who decides when to erase the information; additionally, in the enterprise version you’ll also have the Goliat server at your disposition to move and migrate big amounts of data.Remember when we talked about logrotate? Well, for this job Graylog2 offers an enterprise version to protect the data (compression, encryption and transport through the Internet with secure protocols to protect the privacy of the clients).
- With Pandora FMS we need just one database engine (MySQL), while in Graylog2 we’ll need to instal, besides Java and Elasticsearch, the software MongoDB for everything concerning the user’s access through the web interface (HTML, CSS and JavaScript) and something of greater importance: the alert conditions we want it to expeditiously report to us; getting started with the basic monitoring tasks. Mongo DB will also allow us to store our indexing profiles for Elasticsearch. Gray log 2 will erase automatically the indexes which had finished their lifecycle, or even recreate them.
Filtering or selecting information?
At first glance, it sounds as if both terms were the same thing but, as we will see, they are not.
We consider Elasticsearch an auditing tool quite helpful with data mining.
Remember rsyslog? Inside the configuration file that we’re naming “60-graylog.conf”, we’ll add the following:
*.* @Graylog_server_ip_adress_ 2:8514;RSYSLOG_SyslogProtocol23Format
The asterisk-dot-asterisk at the beginning means send everything to Graylog2 server, generating a great amount of data traffic, despite being compressed! In contrast, Pandora FMS delegates the delivery to Console Agents (using well-known and accepted norms, which come already with the monitoring devices) and to Software Agents with a wide variety of monitoring options (computer temperature, status of a web server o database server) and this way, we select the information that really is of our interest. But with this we don’t mean that the rest of the data is not important! It’s just that there always are more urgent things than others to monitor. (Pandora FMS has fixed profiles for each type of client, standard configurations, and with the Enterprise version we can create tailored agents.
To back the previous statement, in Graylog2 from version 2.x they created a `pipeline process` in which we need to configure the following elements:
- ‘Pipelines’
- ‘Rules’
- ‘Stream connections’
- ‘Functions’
Once we had set all this information, we’ll proceed to filter the information that the server of Graylog2 receives so the server doesn’t process anything which is not matching what we specified before (and avoid it to get to Elasticsearch).
To conclude, remember that filtering implies to ‘move’ all the data so we keep what we are interested in and selecting -the approach of Pandora FMS- is to extract the information that we really want: with both methods we achieve the same result but at extremely different costs.
Extending Graylog2 capacities

If you found it difficult, we must remember that this was just a basic example. We could have even built it on a device like Azure, but the truth is that, for a production environment, we need to add more, much more to Graylog2.
- To make Graylog2 escalate, we first need to mount more clusters for the functioning of Elasticsearch and its database engine.
- For MongoDB, we’ll need to install copies to increase its reliability, although we won’t see any improvement in its performance.
- Another advantage of having Elasticsearch is to be able to use other products from the same company such as Logstash, a powerful tool to transport and filter data (in Elasticsearch format, of course). We could also use Kibana for fantastic and marvelous graphical representations… but we’ll need to get a solution for the management of users aside, something Graylog2 can actually do with the help of MongoDB (and with the enterprise version we’ll also be able to process the user’s aduit).
- If we need to monitor several local networks spread across a country o throughout the world, we’ll need to install a Graylog Server 2 to collect all the data from our network for send it through the Internet later. Do you remember the difference between filtering and selecting? It’d be now the time to apply it before sending it to a central server. Pandora FMS is capable of dealing with this matter with a light-weight satellite server which is specialised and fitted for this job. With Graylog2, on the other hand, we’ll practically need to install the whole solution again.
Other solutions we can choose related to the last point:
- Install Windows Servers 2008 or greater and install ‘Windows Event Collector Service’ to collect the data from a local network. Then, run Nxlog on them to finally set our Graylog2 server farm to centralize the operations.
- Install ‘Graylog Collector Sidecar’ and use the integrated API of Graylog2 (with Pandora FMS this won’t be needed as it has its own Software Agents).
- Graylog2 focus heavily on its own sending norm called GELF (Graylog Extended Log Format) which allows the delivery of messages of more than 1024 bytes well-structured, divisible in 128 pieces to send them compressed via UDP (of questionable security). What prevents us from sending them compressed through TCP is the restriction for null in JSON format, which has also carried problems with Logstash. So far, the solution for this is ‘Graylog TcpLogstashOutput Plugin’, a utility developed by a third-party which adds another task to our monitoring job.
- All these spread utilities have been fostered by the ‘Graylog marketplace’ where they sort them and store the links to their corresponding links for the users to integrate them to Graylog2.
- As we said before, the delivery of all the logs for its later filtering when they reach a Graylog2 server will contain a large amount of data, so it’s advised the use of a load balancing application for the server farm. This way we’ll have everything in the same place with a better functioning, and a greater tolerance to failures (on the contrary, by having a Graylog2 dedicated server for each geographic area we’ll get servers busier than other and even some of them idle). Balancing the load keeps all them always active and working for us.
- Pandora FMS as Graylog2 offer support for the authentication LDAP o Active Directory.
Conclusions
It’s clear that both Pandora FMS and Graylog2 have definitely some similarities when it comes to collecting data, although, for the data filtering and selection, their ways of working are quite different: while Graylog2 relies up to a great extent on third-party products for two database engines for two different sets of information, Pandora FMS uses only one database engine which can be easily replicated with absolutely all the information in one place and collects the data first-hand in a well-selected manner. With Pandora FMS flexibility also comes with simplicity, in contrast with the complexity of Graylog2.
If you’ve liked this article and you think we’ve missed something or we should correct any detail, don’t hesitate to comment below. We will be pleased to answer you.
Do you want to know more about Pandora FMS?