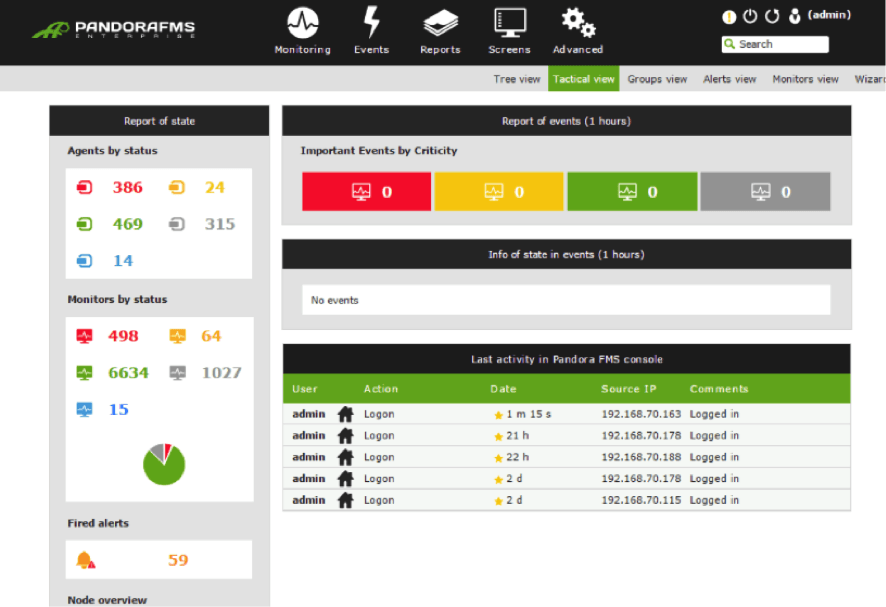
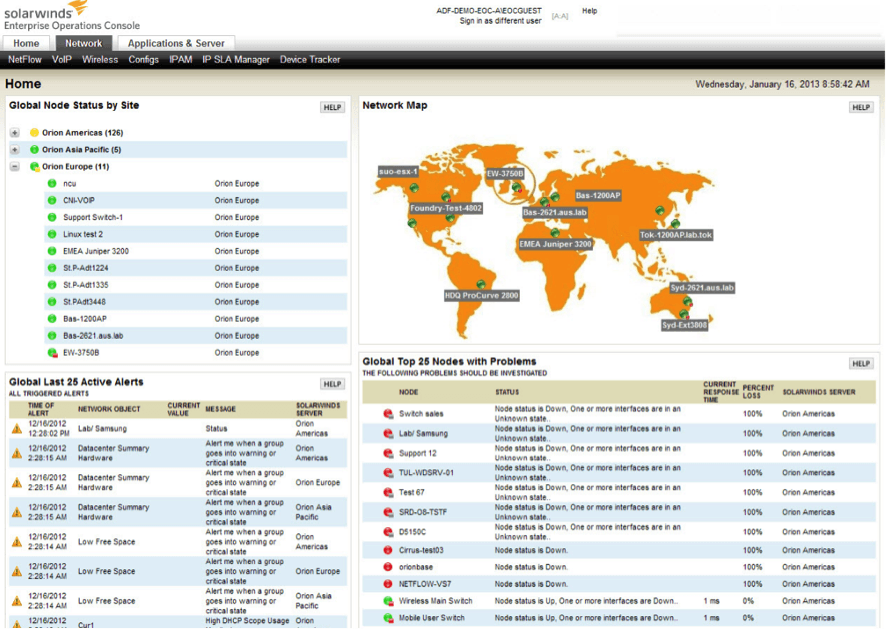
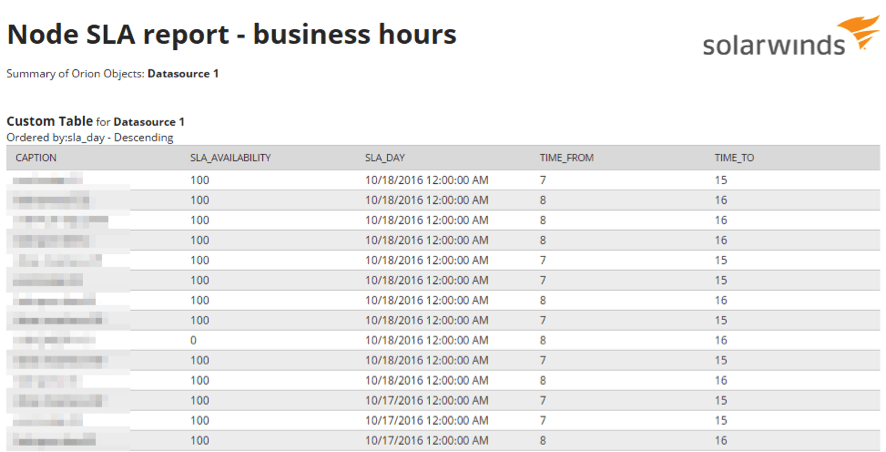
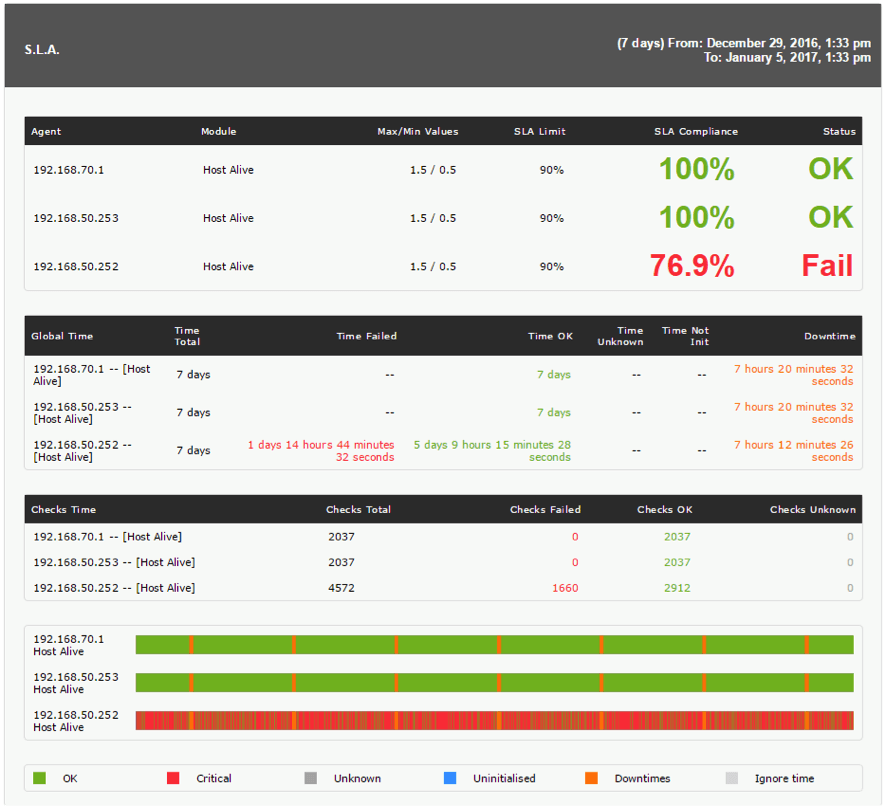
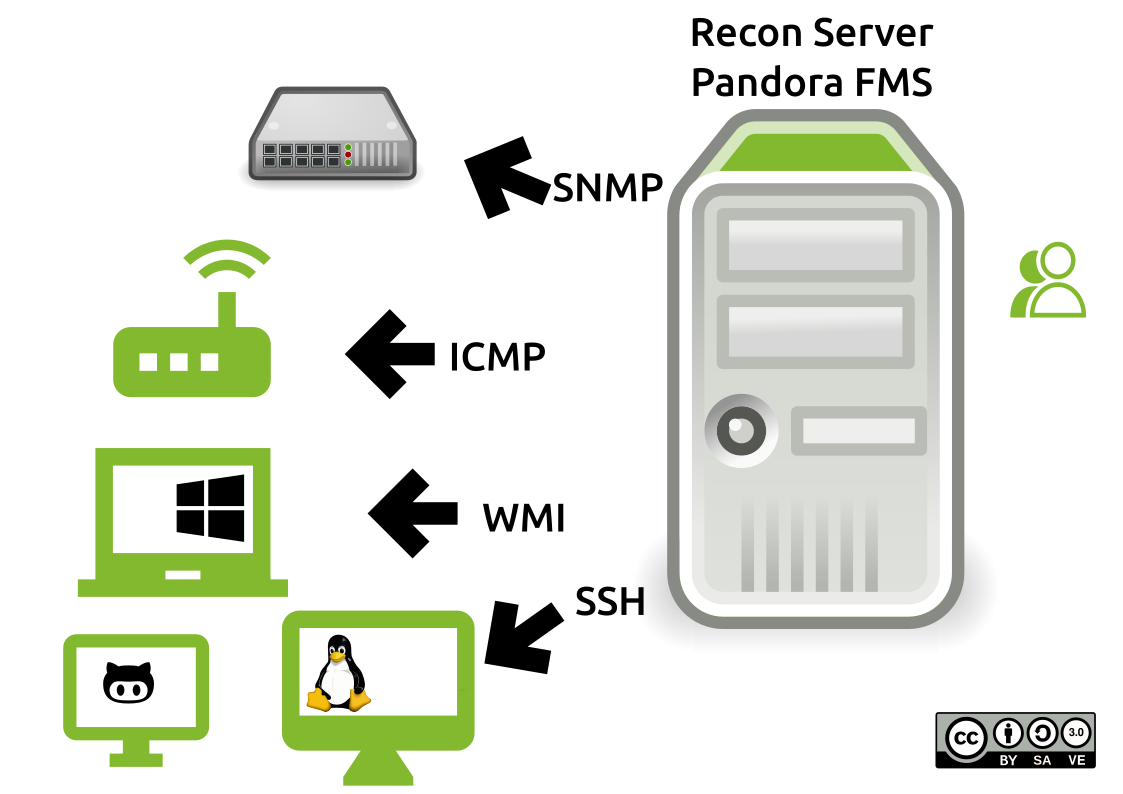
by Pandora FMS team | Last updated Aug 10, 2023 | Enterprises, Network, Tech
How to Select the Best Network Monitoring Tool
When it comes to protecting your company’s important data and network, it doesn’t matter what size your firm is, keeping things safe and running smoothly should be a top priority. For this reason, many invest in network monitoring tools like Pandora FMS. This is because we offer a software solution to make sure your network is always safe and secure around the clock.
Let’s learn a bit more about the process of network monitoring and why it’s so important here!
What Exactly is Network Monitoring?
Unless you’re a DIY computer whiz, you might not be too familiar with how network monitoring works. Basically, network monitoring tools analyze and monitor your network in real-time, flagging any issues ASAP so they can be addressed, whether it be a data breach, user issue, or server malfunction. This in turn drastically cuts down help desk requests and helps your business run more efficiently.
There are different types of network monitoring tools that focus on different sized businesses. For example, traditional network monitoring tools will work well for both small to mid-sized networks both wired and wireless. However, more expansive tools may be needed for distributed network environments and enterprise networks that require monitoring services and visibility into a range of things, such as software-defined networks, cloud-based networks, WAN links, and mobile device network monitoring capabilities.
Network Monitoring Tool Features
Network monitoring tools will offer a wide number of features specifically designed to suit your network’s needs. The most common general network monitoring tool features include:
When it comes to keeping track of your system, syslog messages can certainly come in handy. They’re messages generated between communication hardware that are then saved on a central server. Once on the server, syslog messages can be monitored and analyzed, as well as equipped with alerts to help alert you of any issues. For example, you can set an alert for failed login attempts that will notify you after a certain number, alerting you to a possible security breach or another issue.
- Bandwidth Measuring Tools
Another important component of network monitoring is bandwidth measuring. This enables you to correctly measure the flow of information through your network and determine how busy it is. It’s an extremely important component of any network monitoring software because once you’ve reached 90% of your network bandwidth, it will start affecting the systems in your network and causing issues.
The network monitoring solutions from Pandora FMS come equipped with two tools designed to inform you of your bandwidth, in addition to setting alerts and recording and measuring network activity.

Advanced Network Monitoring Solutions
In addition to the more general tools mentioned above, there are also more advanced monitoring features that can be easily customized to suit your network’s needs. Although depending on your specific requirements, the number of the following solutions you’ll need will likely vary. However, some of the key advanced network components include:
- Automated Device Detection:High-quality network monitoring software is equipped with features designed to detect and monitor every component of your network, providing you with key insight as to how they’re being used and their status.
- Cloud Monitoring:In addition to making it easy to store data, cloud monitoring solutions can provide you with tools to keep track of any applications that are connected to your cloud network, as well as giving you resources to boost efficiency and effectiveness.
- Customizable Dashboard & Control Panel: The best monitoring solutions will come equipped with an easy-to-use dashboard and control panel that can be customized to suit your needs. Such applications will keep track of all of the relevant information pertaining to your network and be equipped with status graphs and tables, a network topology map, and commands for troubleshooting different issues.
- Scalability: This is an especially important component should you want to expand your business down the road. Comprehensive network solutions will enable users to expand their network, adding more complex applications and devices as needed.
- Security: Although most security breaches are due to human error or negligence rather than complicated hacking, there can be cases where data breaches are caused by such activities. The best way to minimize these scenarios is to invest in network monitoring solutions that offer double access protocols and encryption.
- Hardware & Software Inventory: Monitoring solutions come equipped with tools to help take inventory of all of the hardware and software being used within your network, regularly running tests and checks to ensure everything is organized and running smoothly. The most important hardware and software to monitor includes all installed programs, patches and program versions, as well as CPUs and drivers, bios, memory, IPs, and operating systems.
- Comprehensive Data Acquisition: Another important aspect of network monitoring to consider is that of data acquisition. When choosing your network monitoring tools, collecting as much data as possible should be at the top of your list. That’s why the best monitoring software will include a range of data acquisition tools, collecting data from protocols such as jFlow, sFlow, and Netflow.
Contact Pandora FMS for your network monitoring needs
Pandora FMS is one of today’s leading network monitoring tools, enabling users to monitor anywhere from 100 devices to several tens of thousands, unifying all of your network components in a single console. Pandora FMS is a comprehensive network monitoring environment; we’re experts in complex environments and remote networking solutions.
We also offer other services, such as server monitoring, SAP monitoring, IoT monitoring, and much more!
Contact us online today or call +1 (305) 900-6683 to receive a quote for our product.

by Laura Cano | Last updated May 17, 2023 | Community, Tech
Check out a great Check Mk alternative: Pandora FMS
Checkmk was created and developed by German Mr. Mathias Kettner, and since 2007 there is an open source version. In this article, we will get to know Checkmk Open Source, which contains 90% of all the code of said monitoring software, and a Check Mk alternative… But since there are several versions, let’s see them first!
Checkmk versions
I start by presenting the different versions of Checkmk:
- Checkmk Open Source (“Checkmk Raw Edition” or CRE), which I analyze and compare in this article.
- Checkmk Enterprise Edition or CEE, which is free up to 10 devices for each Checkmk instance. Keep on reading and I’ll tell you more.
- Checkmk Managed services Edition or CME, which includes directly working with the client, logos according to the corporate image of each company, etc.
The Check Mk alternative, Pandora FMS, presents the Community version, with which I compare it in this article, and the Enterprise version, that offers multiple additions for business environments. In this link you can see in detail the differences between versions.
Checkmk Open Source features
Mr. Mathias Kettner, born in Munich and graduated in computer science in 1998, worked for SuSE, no more and no less than developing the architecture of Yast2, a powerful software management tool in said GNU/Linux distro. What is all this digital archeology about? You’ll see.
Back in 2003 Pandora FMS was born, and at that time Nagios monitoring software became very popular. Mr. Kettner noticed the advantages of this software: it was open source and there were multiple third-party solutions that supported it. That’s why Mr. Kettner took a step forward and added his own solution with Python language, initially as a Nagios plugin: “Check MK” or “Check_MK”. Exactly, initially it had that name, but later on they simplified it as Checkmk, the current name. But Mr. Kettner evolved too: he created a company called “Mathias Kettner GmbH” (short for “Mathias Kettner Gesellschaft mit beschränkter Haftung”), since he was the only cornerstone of this software. When the free version came out, the company was renamed as “tribe29 GmbH”. “Tribe” was in recognition of the community that could participate now thanks to it being open source. Number 29 was for the physical address of the company: Kellerstrasse 29, Munich, Germany.

Get used to the German language from now on, because Checkmk is available in three languages (German, English and Romanian) but, in my opinion, the best information is all in German. Even terms like werk (work in German, plural werke) are literally translated into English as werks (a term that conceptualizes and encompasses changes and improvements in Checkmk Open Source). On the other hand, Pandora FMS is completely developed in English and then it is translated into Spanish and many other languages.
Open Source Checkmk Agents
Known in our Check Mk alternative, Pandora FMS, as software agents, at Checkmk, the agents are, or I consider them to be, the most brilliant or at least the strength of this software. They are written in C++ or BASH language and they make Nagios improve from 2,000 collected metrics to tens of thousands! This is possible because agents focus on discovering the services and software installed on the device to be monitored, and then send this information (we’ll see later on how). It is particularly favorable in Windows® environments because it calls the operating system API, it does not need anything else. This layout also allows SNMP monitoring. In Pandora FMS, each module in an agent represents a service that an agent contains. Checkmk, however, has its own SNMP server. In both softwares, monitoring can be carried out by both events and status.

If C++ language is good for agents, will it be better for the kernel? Yes, the CEE and CME versions have their own proprietary core that replaces that of Nagios, but that’s another story apart from this comparison.
Open Monitoring Distribution
The Open Monitoring Distribution, or OMD, is another creation of Mr. Kettner to manage Checkmk Open Source virtual instances in a real one. The terms virtual and real are mine, I did not see that they refer to it that way in the documentation. I proceed to describe in more detail: by installing Checkmk Open Source, we are actually installing a software environment that includes the following:
- Checkmk (obvious).
- Nagios.
- Thruk Monitoring interface.
- ICINGA.
- NagVISa.
- PNP4Nagios.
Although the components may vary, the strictly necessary are Nagios, for its core, Checkmk of course and PNP4Nagios for graphics.

What benefits (or reasons) justify OMD? I think it is a very good idea that, regardless of the GNU/Linux distro that will hosts the Checkmk server, a successful installation is guaranteed. That is a very good reason, but we can also create users to delegate creation tasks as well as those of deployment, deletion, etc., of Checkmk instances. I can think, for example, of having an instance to test the new Checkmk versions and then, if they work properly, apply them to the main Checkmk server. All this is similar to what was explained in Administration of Server Configuration (Blue-Green Implementation). With OMD, each instance will have its own name, which will be used to connect to it (www.domain/instance-name). WATO (Web Administration Tool) offers the graphical interface to the user. In the Check Mk alternative, Pandora FMS, there is the console, which you may install on many different machines connected to a “central server” and also both are fully customizable by each user.
Pandora FMS, meanwhile, has its images for Docker, which offers an equivalent feature to OMD. Checkmk can also run in Docker, although they officially acknowledge that it is not the best solution for performance reasons: I say that a virtual device over another virtual device has its drawbacks. Also, due to this OMD schema, you have to add the first device to monitor: the one that hosts the OMD itself. It is as if they were two separate computers but with the exception that you can indicate whether the agent is local or remote. Look at the following image with an agent from each one:

Do you remember that at the beginning I told you that there is a free version of CEE? Yes, but with a maximum of 10 for each OMD instance. Pandora FMS Community version does not have a predetermined limit, if you want to go further, it is up to you to add your own code!
Communication protocol
To finish off, I will talk about the way both software communicate their agents with their respective servers:
- Checkmk Open Source uses an advanced derivative of inetd called xinetd, which has not been updated for years. In the case of CentOS and Ubuntu, you must install it and open your firewall through the port (unofficial IANA) 6556. Although xinetd is a very old software, it complies with the GNU philosophy: it does one thing and it does it right, it allows a large number of connections with very few hardware resources.
- The Check Mk alternative, Pandora FMS Community uses the Tentacle protocol through IANA port 41121. Metric data is in XML format.

Feature comparison: Pandora FMS as Check Mk alternative under close review
Now that we have a general overview of installation and architecture of both softwares, I will now describe the functions of each one in three comparative tables with their explanations and comments, if necessary:

- In “Event Management” for Checkmk, such feature is possible by installing a plugin created by Christian Michaelski (ACTGruppe), under GPL v2 license, programmed in Python and PHP.
- In “Command Line Management” for Checkmk, its programming has not been finished yet right when this article is written.
- In “Recommended capacity per server” for Pandora FMS, the figure is much higher. In the case of Checkmk, the author himself acknowledges that Nagios delays the metric collection intervals by 60 seconds and the CPU efficiency is reduced by half. I don’t recommend trying to monitor over a thousand with a single Checkmk instance.

- In “Official plugins”, Checkmk is benefited by the inheritance of Nagios. However, we must weigh this against server performance with the Nagios core.

- In “Unified Boards”, you need the Metaconsole (Pandora FMS Enterprise). For Checkmk it is only possible in the CME version.
Clearly, the main disadvantage that Open Source Checkmk has, compared to Pandora FMS Community, is the Nagios kernel, which is a drawback by increasing the number of devices to monitor.
Before finishing, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Would you like to find out more about what Pandora FMS can offer you? Find out by going here .
If you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise DEMO . Get it here .
Finally, remember that if you have a reduced number of devices to monitor, you can use the Pandora FMS OpenSource version. Find more information here .
Do not hesitate to send us your questions. Pandora FMS team will be happy to help you!
*Erratum: A member from Chekmk team was so nice to contact us to let us know that there were some mistakes on this article that we proceed to make straight hereon:
-CMK Raw allows distributed supervision and unified dashboards. It can combine as many Raw instances as you wish and configure them with a master instance or create any other configuration.
-In access control levels, it did not make reference to LDAP / AD, since it is more about user management. RBAC deals with how granular function control can be segmented.
(We also take this opportunity to remind you that the comparative refers to Pandora FMS Community version. The Enterprise version has a full RBAC with authentication systems such as LDAP or AD, in addition to double authentication systems such as Google Auth).
-SNMP decentralized monitoring is also possible through distributed monitoring. Furthermore, Chekmk has an event console for SNMP trap monitoring.
-Regarding ACT ITSM event management, Checkmk’s suitable version is Event Console.
-Finally, we would also like to add a correction of ours saying that the table where “Unified dashboards” appear in red, both features should be in green since both Checkmk and Pandora FMS Open offer this type of dashboards.
Do you want to know more about Pandora FMS?
by Pandora FMS team | Last updated Aug 10, 2023 | Enterprises, Servers
What Can Pandora FMS Offer as a Server Monitoring Tool?
When your server goes down, it can certainly throw a wrench into your daily processes, costing you money and even causing you to lose customers until it’s back up and running again. Thankfully, Pandora FMS can help you prevent it from happening, and in the worst-case scenario when it does, you have the tools to get back up and running again in no time with our server monitoring solution!
An All-in-One Server Monitoring Software
One of the best things about the server monitoring software available from Pandora FMS is that it’s a one-stop-shop for all of your server monitoring needs. Our software comes equipped with default policies for each operating system, application, and user environment. We also cover everything from user applications to hardware; our monitoring software is also compatible with both Linux and Windows.
Our Comprehensive Server Monitoring Solutions
When you invest in Pandora FMS server monitoring tool, you’ll be able to:
- Unify different information sources (applications, logs, base operating systems, storage, networks, user experience, etc.) into a single point.
- Manage everything in a centralized location equipped with plugin deployment features, remote configuration, templates, and more.
- Access expansive information, including multi-year history performance data, and unlimitedly access application and server logs.
- Manage tens of thousands of servers through a single console.
- Ensure that your software and hardware meet your expectations thanks to various SLAs, trend reports, and Top-N reports.

Some Server Monitoring Best Practices
When it comes to server monitoring practices, there are some specific things to keep in mind that will help you and your IT team utilize your new monitoring solutions to the fullest. How easy it will be to deploy some of these practices will depend upon the monitoring tools you’ve employed as well as your knowledge of the applications, but it’s important to be aware of them nonetheless.
Phase 1: Actions to Start Monitoring
First and foremost you need to take some actions, including:
- Identifying Your Assets: Identify all of your assets, including databases and the systems they feed, to make it easier to determine where the issue lies.
- Identify What Needs to Be Monitored & What Doesn’t: Establish priorities to determine what is critical in terms of monitoring and what falls at the bottom of the list.
- Classify Your Assets: Once you’ve developed a hierarchy for your assets, classify them by service, application, system, or resource to make identifying issues easier.
- Categorize Alerts: Categorizing your alerts will make it much easier to collect data on certain issues and keep track of them when they arise.
- Come Up with an Action Plan: When it comes to solving server issues, the fewer surprises the better, so come up with an action plan for every scenario you can think of to minimize downtime.
Phase 2: Identifying Problems Before they Happen
Unlike phase 1, using the right server monitoring software can also help you identify problems before they occur by providing intuitive monitoring solutions. The right software solutions will be equipped with automatic monitoring tools like big data monitoring solutions, dynamic monitoring services, event correlations, and smart thresholds, enabling users to identify things that can become major issues down the road.
What Exactly is Preventive Monitoring?
When it comes to preventive monitoring there are two important aspects, the first being defined by receiving small alerts when something leaves the normal operating thresholds. In this first scenario, it doesn’t necessarily signify a major issue, simply that something unexpected has occurred. However, defining clear parameters in such a scenario that leaves no margin for error in misunderstanding is key, that way a major event doesn’t go unnoticed.
In the second scenario, users can create monitoring displays or dashboards that are labeled and designed to compile information and create a real-time graph, enabling IT teams to determine precisely when something isn’t right.
Some of the most important tools for successful preventive monitoring include:
- Alerts: Such alerts must include item groups and allow for users to define complex tasks, with the ability to insert an event into a group, including a graph and a clear description of the issue.
- Graphs: Graphs can be used combined with other data to form a comprehensive understanding of an event.
- Logs: Logs help users understand the raw information when an issue has arisen. These can be created through the use of data charts or analyzing the raw data being introduced to the system via log registries.
- Direct Access to the Source: Direct access to the system creating the issue, as well as all of the detailed information behind an event, enables users to quickly address any issues and close the cycle.
Development from the Ground Up
Unlike many other forms of server monitoring software, the solutions from Pandora FMS have not been developed by any third-party developers; our team has built everything from the ground up. This means that you can get any necessary information directly from the source through native calls to the operating system. There’s no need to waste time dealing with going through third-party connectors to troubleshoot or obtain the info you need when you need it!
Contact Pandora FMS for your server monitoring needs!
Pandora FMS is one of the leading server monitoring companies because we offer comprehensive solutions at every level, working to meet our clients’ specific needs.
As experts in the IT monitoring sector, the team from Pandora FMS also offers a range of other solutions, including virtual monitoring, remote control solutions, MSP monitoring, and much more.
To receive a quote or learn more about the solutions we offer, call +1 (305) 900-6683 or contact us online today.

by Laura Cano | Last updated Apr 26, 2023 | Community, Network, Tech
How a network operating system works and how to monitor it
In the early days of telephony, there were few people who had phone numbers in every town and city. There were just a few numbers to remember and if your brain failed, you could check with a telephone operator, women who always knew (and know) how to listen. Let’s see how a network operating system was born in the middle of the 20th century, right at the center of telephone networks.
Today, our mobile phones have replaced telephone operators, even to the smallest detail they can receive verbal orders about. In reality, the device is a simple and stupid terminal (but with higher computing power than the computers that took us to step on the moon back in 1969) but our voice ends up being executed on powerful servers… that perhaps are part of a network operating system.
X.500 Protocols
In the middle of the twentieth century, the different telephone companies had the ability to connect continents by means of satellites, apart from conventional submarine copper cables, which in turn were replaced over time by optical fiber. This created the possibility of connecting millions of people and millions of registered phone numbers. We needed to exchange information from telephone subscribers in an organized and decentralized but standardized way.
An idea arose in the International Union of Telecommunication (IUT) and they agreed on protocols (from X.500 to X.530) that evolved little by little. The project started in 1984. but it was not until 1986 that European and American standards reached a consensus. Also in that glorious year (I was finishing high school) NetWare® 2.0 came to light, which I consider to be a very famous network operating system that I worked with in the 1990s. But let’s get back to phone companies and their eagerness of sharing information.
Essentially, these protocols were well thought out and, although some did not go well, others were successful.
- DAP (Directory Access Protocol).
- DSP (Directory System Protocol).
- DISP (Directory Information Shadowing Protocol).
- DOP (Directory Operational Bindings Management Protocol).
The first of them was the source for LDAP (Lightweight Directory Access Protocol),that basically offered a flexible way to handle and work with information. In 1988, at the University of Michigan, they started the OpenLDAP project, opened and used in most GNU/Linux distributions. To delve fully into the monitoring issue, Pandora FMS has developed a plugin that allows you to search for a value (a person’s phone number, for example) on an LDAP server, or just to know whether it is up and running.
Now you may be wondering: what does all this have to do with a network operating system?
Network Operating System and Distributed Operating System
We will use the opposite-concepts learning method.
A distributed operating system operates fully and functionally, uniquely. They are a group of very well-known computers (called rather nodes) that look like a single, large operating system for users. It is closed, and although within its characteristics an increase in nodes is planned at any time, it is under very strict and complex rules. They are systems that take a long time to be developed due to the necessary classification of the hardware that will run it. I sidestep going into more detail, but more or less, it’s like a huge gigantic computer running a single distributed operating system.
A network operating system is also made up of many computers, some as servers, others as clients and even as both in some cases. The hardware is diverse and based on open and widely known standards, and it seeks sharing to take advantage of absolutely every penny invested so that each user can carry out their work quickly and efficiently.
Although this whole perspective of sharing resources was well understood -and requested- more than anything, due to the high cost of the equipment at that time (I mean the ratio of computing power and storage for each currency invested), there was a small detail: each server was the center of its own universe and network administrators had to be very aware, for example, of the change of location of a user from a certain network to another (create a new user account in the network that receives the employee and deactivate the previous account).
Let’s see if we can notice this on the phones: today you may live in Washington and tomorrow in London; phone books will automatically take care of the whole process and the work of the International Telecommunication Union will pay off!
Following the example, if I am a network administrator in Washington and I am in London, I can log in and my information can be checked across the seas. There are additional details, such as a copy of my data being stored in London and if there is any change in Washington, it is notified and the other way around. All of this is just wonderful and it is what drives me to continue working in the field of computing!
By the way, Pandora FMS, among its user authentication methods, can use LDAP with the help of OpenLDAP software. Later on, I will talk about other important technologies also used for the same purpose.
Netware® Novell® 4.x
A good example of a network operating system is proprietary Netware® Novell® software. Or rather, it was proprietary as it evolved to GNU/Linux when its sales declined. Today, I consider it to be virtually disappeared even though it uses free software.
I had to work, as I said, with said network operating system at the end of the last century, more to provide access to databases, shared printers and optical readers than anything else. Yes, you read correctly, not all computers had CD players -DVD had not been invented- and although they do not have such drives now, it is for another reason: the ubiquity of the Internet! An inherent feature of network operating systems is coexisting at layer 3, the network layer, so it had its own IPX / SPX network protocol, which we ran alongside the “new” TCP/IP. Take a guess on which one survived and which one fell into oblivion…
The success of this network software is that, although it was proprietary, it was always ready to coexist with other proprietary or open technologies: it also supported the AppleTalk® protocol, among others, and allowed the development of third-party modules (Loadable NetWare Modules® or NLM). But the icing on the cake was NetWare Directory Services®, based on (yes, you guessed it right) the X.500 protocol suite. I consider that this gave it the competitive advantage over others for around a decade, when a powerful opponent emerged from the very core of the Internet…
Microsoft Windows 2000®
After what must have been the millennium shock, they launched this truly professional version that we quickly adopted for its stability and secondly because it first introduced the famous Active Directory® based on versions 2 and 3 from LDAP.
Pandora FMS, in its Enterprise version, offers authenticating users through Active Directory, in addition to a complement to monitor many important aspects of this information store.
Monitoring a network operating system
I already told you how Pandora FMS has never lost sight of any technology and here I describe the features – not all though – of a network operating system, although its use has decreased considerably for its own sake, in favor of improved technologies.
- As I told you, it can be managed from any workstation, it is not necessary to be sitting right in front of the server. This may sound weird at this time, but the concept is fully current. As an example we have the Pandora FMS Enterprise Metaconsole that unites in a single console several of its different monitoring servers.
- Very efficient file server: NetWare Core Protocol® (NCP, 1983) had “embedded” commands to manage a protocol aimed at working with Network Attached Storage or simply NAS. To be honest, this has been replaced by multiple hardware expressly built for that purpose that assume the same functions of a network operating system (disk redundancy, monitoring, auditing, etc.). Pandora FMS has plugins such as Synology NAS for that popular manufacturer brand. Other important providers that Pandora FMS can monitor (right now that I’m writing): “HP Compaq Smart Array“, “Dell Server (through SNMP OpenManageServer)” and “Hitachi DF Disk Array“.
- In the previous point, with a NAS device (or several), we had our files in one (or more) very specific places, but what if we have to distribute a “disk” across a network? Look at the quotation marks: the “disk” looks like a unit, but its content is hosted on several servers… and it is as old as 1984, when it was openly developed by the company Sun Microsystems® (and later adopted by NetWare ®). If you think it is an expired technology, nothing could be further from the truth. In fact, Pandora FMS can use it if you have several Pandora FMS Dataservers, which collect and send information from software agents in a unified way (data traffic securely encapsulated through the Tentacle protocol).
- Another way to share files that has caused network operating systems to decline is the popular Samba software, based on the SMB protocol, which also allows sharing printers and, to “give it a twist”, from version 4, it supports Active Directory® as a Domain Controller. Pandora FMS has multiple plugins to monitor Samba!
Finally, remember Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Would you like to find out more about what Pandora FMS can offer you? Find out by going here .
If you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise DEMO . Get it here .
Finally, remember that if you have a reduced number of devices to monitor, you can use Pandora FMS OpenSource version. Find more information here .
Do not hesitate to send us your questions. The Pandora FMS team will be happy to help you!

by Laura Cano | Last updated Aug 3, 2020 | Tech
What cloud service types are there?
In previous and great articles in here, we already talked about what Cloud is and the types that exist floating above our heads. But today, for a change, we want to focus more on one of its totally forgotten key aspects: Are clouds actually made of childish dreams and cotton candy? No! Just kidding! Today we are going to talk in “Pandora FMS discussions” about what cloud service types there are.
Of course, before, we will do a little review to get updated on what the Cloud is and the types of cloud that we can find in the extensive field of technology.
What is the Cloud?
We know as “the Cloud” a worldwide network of servers that have their own role. This server network is humongous and they work and interact with each other from the most remote places in the world. They communicate with each other to work as a single omnipotent system. Their main task is to store and manage information. They can also send content, grant services, run applications, work in streaming… Thanks to the Cloud, you don’t need to access information or files stored in your computer. You can get them online, from any device connected to the Internet. The data will be wherever you are and when you need it. The Cloud is like that, almighty.
What is Cloud Computing?
“Cloud Computing” is that wonderful technology that, using Cloud features, provides services through the Network. Cloud Computing allows us to have all our information on the Internet and to be able to work with it. It gives us access to all kinds of computing resources spread throughout the whole world. Perhaps multi location is the strength of Cloud Computing, since it offers the possibility of reciprocity and collaboration among all users. We are a team!
Cloud service types: Software as a Service (SaaS)
The most common examples of this type of service in the Cloud (SaaS) may possibly ring a bell. You just have to think about your email and office tools. That’s because Software as a service (SaaS) gives us the chance to connect to cloud-based applications, do it over the network and use them.
Software as a Service provides a comprehensive software solution, available from a cloud service provider, through a pay-per-use model. You rent the use of an application for your company and the blessed users connect to it through the network. All the infrastructure that keeps it and the information of the applications are in the information center of the supplier. The service provider is in charge of all the hardware and software and must also guarantee the availability and security of both the application and the information used. This type of service (SaaS) allows a company to start and run its applications with a low initial cost.
Cloud service types: Platform as a Service (PaaS)
There is also PaaS or Platform as a service. We can say about it that it is a complete cloud-located development and implementation environment. Its resources range from simple Cloud-based applications to fully sophisticated and chic Cloud-ready business applications.
It works as follows: You buy the resources you need from a cloud service provider, which you will access through a safe connection, but you will only pay for the use you make of them.
Like IaaS, which we will talk about later, PaaS has a server infrastructure, storage and network types, as well as middleware, development tools, business intelligence services, database administration systems and much more. The Platform as a Service is designed to hold what we could call “the complete life cycle of a web application”; That is from compilation, testing and deployment to administration and updating.
Regarding the practical part, the Platform as a Service will save us the costs of purchasing and managing software licenses or application infrastructure, as well as investments in the underlying middleware, development tools and many other resources. You can manage the applications and services they develop, and the provider everything else.
Cloud service types: Infrastructure as a Service (IaaS)
IaaS or Infrastructure as a Service is an instantaneous computing infrastructure, supplied and managed through the Network.
IaaS takes in fluctuations and rapidly increases or decreases on demand, allowing you to pay only for what is used. It also helps considerably to avoid high expenses and the complexity of purchasing and managing your own physical servers or any other data center infrastructure. Each resource is offered as a separate service component and you only need to rent a certain one for as long as you need it.
Among the great advantages of IaaS, there is avoiding high expenses and reducing current costs, innovating quickly (as soon as it is decided to market a new product) and, of course, the corresponding increase in security.
Once you delved into the technological ins and outs of cloud service types, are you hungry for more? Would you like to go even further in the world of technology? Do you know Pandora FMS? Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Would you like to find out more about what Pandora FMS can offer you? Find out by going here .
If you have to monitor more than 100 devices you can also enjoy a FREE 30-day Pandora FMS Enterprise DEMO . Get it here .
Finally, remember that if you have a reduced number of devices to monitor, you can use Pandora FMS OpenSource version. Find more information here .
Do not hesitate to send us your questions. Pandora FMS team will be happy to help you!

by Laura Cano | Last updated Aug 27, 2021 | Community
Interview with Sara Martín, HR at Pandora FMS, a software company
“Human Resources”, what are “Human Resources”? Vegetal charcoal? A set of goods or means of subsistence? The ability to touch your nose with your tongue or move your ears on demand by just focusing your mind on them? Yes, many would consider the latter as an awesome resource, and human too, but no! Today we are not going to talk about that. We are going to talk about true Human Resources.
Human Resources is that department within companies where everything related to the people who work there is managed. Selection processes, hiring, welcoming, training, promotion, payrolls, contracts, layoffs and more human things that they make up. As department, it is essential to deal with employees, real matter, pure charcoal that gives life and energy to the hitherto lifeless machine of companies.
A good head of human resources must have instinct, leadership, patience, cunning, know how to behave, commitment, kindness, a vast knowledge of comics and glamor, the latter two are optional, but Sara Martín Boluda, Head of Human Resources at Pandora FMS, also has them.
How and why did you start working at Pandora FMS?
When I finished my studies as a health social worker, I decided to continue training in the field of psychology. While I was getting my second degree, I decided to look for a job that I could combine with my studies. And so I found a job as administrative assistant and receptionist at Pandora FMS. One of the things that most caught my attention was that, within my tasks, I was also going to be able to take part in personnel selection processes. As soon as I stepped into the office for the first time and saw the tentacle of the Maniac Mansion in a picture, I thought “this place rocks!”. That’s how they got me from the start. Within a few months, I began to carry out the first selection processes. I increasingly had more HR tasks, so I decided to get training in the sector and study a Master in HR. A year later I was already head of HR.
What is Human Resources for a company and what exactly do you do in your position?
That question would be enough for another whole interview, so I will try to be brief. The HR of a company includes all the administrative tasks related to personnel, but it is much more than that. In my case, I give much more importance to the human part. At Pandora FMS, I have done all kinds of tasks, but within HR one of the things I value the most is trying to keep peace within the organization, to help people to be as happy as possible in here, and stay motivated working comfortably. I think that way we are all much more productive and that is a visible benefit for the company.
Among those kinds of tasks, I am in charge of the administrative management of personnel, that is, holidays, transfers, payrolls and the little day-to-day things. Also recruitment and personnel selection and internal and external training, as well as the prevention of occupational risks, social benefits, mediations when necessary, etc. In addition, I’m also in charge for the Community-related issues and the wonderful videos, which you can watch in our channel.
What are the keys to choosing well when hiring someone?
The most important thing is to fit within the team and have the necessary knowledge to carry out their tasks. At Pandora FMS, we place great importance on resolution and learning and adaptation abilities.
I don’t think there is an ideal candidate. Throughout my life I have seen may endless job offers where they asked for all kinds of programming languages, in addition to high level of English and 5 years of experience, offering a salary below the market, but then, for example, when you talk to them, the candidate will never actually speak English and will only use PHP. That way you leave many highly talented people out of job offers, people willing to give their best and with a learning curve that can pleasantly surprise the team.
How is team spirit encouraged or how is the employee encouraged to work hard?
The truth is that it is hard and since recruiting at home due to COVID, much more. Now that you say it, I think that all the professionals in the sector are wondering the same.
For our part, we have always done small actions to enjoy being in the company, whether it be ordering takeout together, celebrating the birthdays of the team members, meeting in the evening to hang out, “team building” through games or our wonderful summer barbecue and christmas dinner. Now with the pandemic, we only have team meetings through Meet and improve the training of people who request it or who need to improve any of their abilities. We all hope all of this is over soon and we can organize our long-awaited barbecue of the year.
On the other hand, for workers to work to the fullest, it is necessary for them to understand what they do, that their work has a meaning and they can enjoy it. There are always monotonous and boring tasks, but when you know it is for something, everything has much more meaning. In addition, having a team full of wonderful people, who collaborate and always make you smile, helps a lot to work motivated and with a smiling face. In the end, a company is made up by its workers and, here at Pandora FMS, we can be satisfied, we have the perfect team.
Any tips to make a layoff smoother?
No, the truth is that there is no trick. It is an unpleasant situation and much more when we work in such a united way. We all know each other very well and every time there is a layoff, it is hard for everyone. You have to put yourself in the other person’s shoes, be tactful, explain the process in detail, not go beat around the bush too much and try to help as much as possible so that this person can find a new job.
How many years have you been in the company? Any funny anecdotes during these years that help to liven up a meal or a hangout?
I have been working for four years and I think I had many anecdotes during this time.
On my first day working here, for example, they gave me a documentation to shred, so I got on it, but when I saw that it started to get stuck and the sound started to disturb everyone I shared the room with, I was so embarrassed. I tried to remove the jammed paper and broke the shredding machine. A lovely girl named Carla rushed to help me and tell me not to worry. I think since then there is no shredding machine. That was the beginning of a great friendship.
The truth is that I have had a great time during these years, I have had a blast and I have very good memories.
What is the geekiest hobby you have? Does it help you in any way in your work?
I’m quite a geek in general. I collect comics, I really like video games, playing board games and role playing. I guess I have the full pack. But apart from that, I am also fond of yoga, mycology and I love fossils.
I’m kind of weird and I guess that made me fit in well with the team. We are lucky to have common hobbies and that makes lunch times much easier.
What band, singer, DJ, instrumentalist, or thing can’t you stop listening to lately?
I’m on an endless loop with Candlemass and Amelie Lens. Yes, they have nothing to do with each other, but electronic music and doom metal are my two favorite genres.
Tell me the first thing that comes to mind when I say these words:
* Pandora: FMS
* Friday night: Pizza
* Team: Pizza
* Sunday evening: More pizza!

by Laura Cano | Last updated Dec 22, 2022 | Community
SNMP alerts: what they are and why you should configure them
The SNMP world is becoming more and more important within the monitoring environment, as companies need to find software that has specialized tools for trap monitoring. If you are not familiar with the term SNMP, take a look here.
In this article, we will focus on Pandora FMS SNMP alerts, on how they work and how you can benefit from them.
What are SNMP alerts?
As some of you may already know, Pandora FMS has an alert system based on previously created modules, where different actions can be performed depending on the values that each module collects. We have even gone so far as to talk about more complex alerts derived from the events that are generated within Pandora FMS. Still, let’s take a brief look at the alert concept, focusing a little more on this particular type.
SNMP alert concept
The first big difference between the aforementioned alerts and SNMP alerts is the “arrival” of the data that triggers the alert. While in the first alerts, Pandora FMS is in charge of collecting data through remote or local checks, in this case, it is the device the one that will send Pandora FMS the trap that will trigger one of the configured alerts.
As there are several identifying fields within a trap, SNMP alert configuration is very versatile to be either very restrictive or very general when it comes to detecting the trap that triggers an alert.
Among the different configurable fields of SNMP alerts, it is worth highlighting:
- Enterprise string
- Custom OID value
- Agent (IP)
- SNMP trap type
Let’s take the case of a restrictive configuration or a very general configuration. For a general configuration, it would be enough to add, for example, an IP of a router from your network. In this case, any trap that arrives from that router will trigger the action that it has configured within the alert.
On the other hand, maybe you want to have an alert that fires in very special cases. To that end, for example, you have to fill in all the fields and set the alert to only fire when it comes from the router with IP XXXX, from OID .1.2.3.4.113.122, which is the type of interrupted linking trap.
What can I do with SNMP alerts?
There is a wide variety of actions that can be performed when Pandora FMS receives a trap, either with default actions or custom commands. Below we will see some examples of common actions in SNMP alerts.
Send an email
A widely used action is to simply send an email to the operator in charge of managing the company’s systems. This email could include specific details of the hardware that triggered the alert and its characteristics, keeping the operators up to date in real time.
Create event
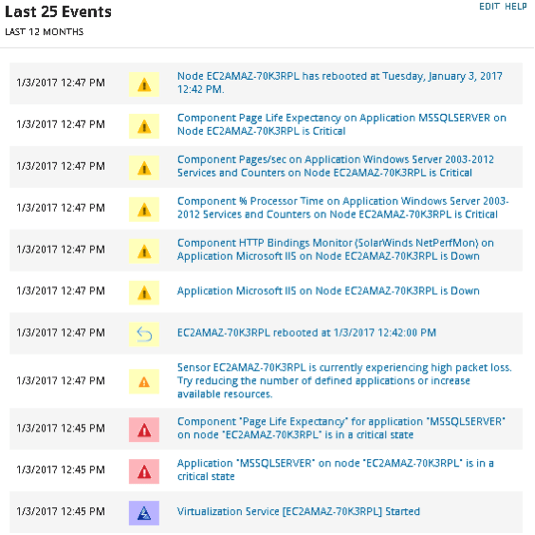
When a trap is received, you can generate an event in Pandora FMS. This event would show which agent (IP) it is and what happened.
Let’s see a practical example. If you had an agent with IP 192.168.70.1, an IP that matches your main router and which is sending traps with its changes, once the trap arrives and matches the configuration of the created SNMP alert, it will create an event with custom data such as: event text, event type, agent, priority or even comments so that the operator of the event view can see the corresponding information.
Custom Commands
Just as there is a wide variety of traps that Pandora FMS can manage, custom measures can be created for each of them.
This configuration is designed to be able to generate multiple very specific SNMP alerts for each trap, hardware or status and to be able to take custom measures for each of the setbacks that may take place in your system.
Let’s look at a particular example of a custom command with specific settings. Suppose your SNMP alert setting is as follows:
- Enterprise string: .1.3.6.1.4.1.9.9.826.1.21 (Ethernet port)
- Agent (IP) 192.168.80.21
- SNMP trap type: Broken link
So, if you get such a trap, what you need is to create a custom command that will get the link itself up, connecting to the router with IP 192.168.80.21 and execute the command: ”snmpset -v1 -c community hostname IF-MIB::ifAdminStatus.interface i 1” to activate it.
What are the advantages of SNMP alerts?
Although monitoring with traps itself is already a great advantage when it comes to talking about SNMP devices, there are many advantages when it comes to having SNMP alerts within the selected monitoring tool.
Control in the same tool
Thanks to the action described previously of creating an event, having all your devices’ traps pointing to Pandora FMS and with the corresponding general settings of SNMP alerts, you may have in a single window the total display of what is happening in all your devices simultaneously.
Simplification
By means of the possibility of sending an email to the tool’s operators, the data obtained through the trap that caused the SNMP alert to be triggered can be simplified. This means that the user who receives the alert does not have to know how to translate the trap OIDs or know the different types of traps that can be generated, since they can receive the email with all the necessary translations and clarifications created in the alert.
Automation
Perhaps the greatest advantage of SNMP alerts, as it can happen with the rest of Pandora FMS alerts, is the automation of actions to be carried out in different cases. As there is no SNMP alert creation limit, and since the trap reception limit is imposed by the hardware in which Pandora FMS is installed, you can cover a very wide range of automatic actions for the different problems that may take place within your monitored systems.
So far we have learned a little more about SNMP alerts in Pandora FMS. Would you like to find out more about what Pandora FMS can offer you? Find out clicking here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
Also, remember that if your monitoring needs are more limited, you have Pandora FMS OpenSource version available. Learn more about it here.
Do not hesitate to send us your questions. Pandora FMS team will be happy to help you!

by Laura Cano | Last updated Jun 10, 2021 | Geek culture, Tech
CIOs, CTOs and executives. What you need to know about IoT
If you occupy positions of certain responsibility (such as CIO or CTO) and you do not know what is necessary about IoT, you run the risk of being out of the game. So here in this article is what you need to know about IoT.
The following post is not intended to be a full encyclopedia on the Internet of Things. It doesn’t even intend to be a comprehensive list of “everything you need to know about IoT.” But we do would like to remind you of some aspects of IoT that you should take into account if you want to hit the jackpot or, at least, not get hit by the jackpot.
What you need to know about IoT
IoT will be more important than what it seems
It is not only a hot concept, but it already is really important in many companies and the chances are it will be very relevant in the very near future.
We are not going to go on and on about growth forecasts that you have already read a thousand times, but take a look at a key concept: 5G.
The Fifth Generation of mobile phone technologies is one of the factors that IoT needs for its growth, and its arrival will enhance its development in a way we only have a glimpse of today.
If there is someone who should be in charge of the IoT in the company, it is the IT department
You already know that all eyes will be looking in your direction. If someone in the company is expected to take advantage of IoT is the IT department, and as the person in charge, you have no choice but to put on your captain cap and take the helm.
Get all the knowledge you need
We do not question your trainning or your experience. Surely you invested a lot of time and effort in acquiring them. However, you probably already know that in the IT world you never stop learning.
Although the IoT domain has been developed for years, it is still very new, so you probably have a large field for learning before you. In addition, you already know that a position as complex as that of a CIO requires both technical and business knowledge, so it will be twice the challenge.
Mark these words: flexibility, interoperability and scalability
What you need to know about IoT is that it is necessarily something that will work with very heterogeneous environments where diverse manufacturers and solutions must coexist. Therefore, factors such as flexibility and interoperability (about which we already wrote in this post) will be of the utmost importance.
At the same time, the variety in the number of devices and the changing scope of the necessary infrastructure will make it very important to think about options that favor scalability.
New markets, new products
Although your company’s activity may seem to have little to do with IoT, what yo need to know about IoT too is that its versatility can accommodate a wide range of activities.
Have you thought about how your company can make the most out of IoT to launch new products and services? Perhaps you have at hand great potential for growth that is being wasted – at least for now. As always, keep your eyes open for new opportunities.
Another keyword: sensorization
It is one of the key points of IoT. Taking advantage of sensors can bring multiple benefits, even in the least expected ways. There are some magnificent examples: for example, there are livestock facilities that monitor the health and productivity of their cows through collars on their necks, which provide information as useful and funny as the way and frequency they moo.
It is an example that may be very foreign to you, but sensorization can offer an extra value where you least expect it. Think about how to take advantage of it!
IoT and Big Data can also work hand in hand
IoT produces a relentless flow of information. Don’t you think it would be a great idea to take advantage of it? Today, more and more companies are using Big Data solutions to obtain the performance from the huge amount of information received from different sources.
IoT will multiply the available information and therefore its potential, while an improvement in the systems that are responsible for its treatment and analysis is foreseeable.
Don’t forget about security and privacy
The flow of data and the presence of devices in all kinds of places offers great opportunities, but not without risks. IoT development will require facing big security challenges you must also pay a lot of attention to.
As always, the customer will continue to be important
It is not about accumulating IoT devices, but about developing those that really provide an extra value to customers. In an increasingly diverse and demanding market, the user is of utmost importance and demands increasingly useful and customized products, so do not forget that their satisfaction will be both an objective to achieve and a good scale to know if things are working as they should.
Another essential word: monitoring
IoT represents much more technology and much higher supervision demands.
Monitoring is not a new thing, nor is it a surprise that it’s needed. It has been vital for decades in all kinds of IT environments. However, the Internet of Things will multiply its importance.
In addition, IoT monitoring will have its own features. For example, when monitoring IoT devices, monitoring system flexibility will be something to keep in mind.
That is why you need to learn about Pandora FMS. Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes. And among all the things it is capable of, it can also monitor IoT.
Would you like to know what exactly Pandora FMS can do when it comes to monitoring IoT? You have it very easy, just send a message asking all your doubts. You can do it in a very simple way, thanks to the contact form that can be found at the following address: https://pandorafms.com/contact/
Before doing it, and if you want to know more about the Pandora FMS IoT monitoring, take a look at this link: https://pandorafms.com/iot-monitoring/
We hope you liked this article about what you need to know about IoT and remember that if you have a reduced number of devices to monitor, Pandora FMS OpenSource version may be more suitable for you. Learn more about it here: https://pandorafms.org
Do not hesitate to contact Pandora FMS team. We will be happy to help you!

by Laura Cano | Last updated May 17, 2023 | Community, Tech
Pandora FMS como una alternativa a Icinga 1.x, ambos escritos en código abierto
Examina. Busca. Navega. Icinga, en idioma zulú. El origen de los nombres de gran cantidad de software son un tanto extraños (o desconocidos), y eso es material para un artículo aparte. En esta oportunidad os propongo a Pandora FMS como alternativa a Icinga y, si sois lector(a) consuetudinario de nuestro blog, una reminiscencia vendrá a vuestra mente.
Finalizando el año 2018 evaluamos varias herramientas (Icinga incluida, aunque de manera breve), por ello hoy actualizamos la información y a la vez ofrezco a Pandora FMS como alternativa a Icinga. En un principio Nagios, software patriarca de la monitorización, nace en 1999, justo antes de finalizar el milenio. Se mantuvo fresco y nuevo por diez años y en este ínterin nació Pandora FMS, en el año 2004. La comunidad de Nagios es entusiasta y en ese período estaba cohesionada. Hasta que un grupo de programadores de su comunidad plantó cara al Sr. Ethan Galstad y anunciaron una bifurcación: Icinga. Para ser más precisos, esto ocurrió en el mes mayo de 2009.
Considero que en ese punto Nagios adolecía de conexiones a bases de datos robustas, como Oracle® y PostgreSQL®; además faltaba una interfaz web escrita en PHP (no os riáis, considerad la época). Estas dos características fueron los primeros puntos que los bifurcadores retribuyeron al proyecto original. Vamos, que «el alumno superó a su maestro». Lamentablemente, la separación fue dolorosa, con detalles que no vale la pena comentar.
En la actualidad Icinga no ha perdido ni un ápice de su dinamismo, pero su herencia de Nagios es innegable.

Leyenda: Principios de operación de Nagios https://es.wikipedia.org/wiki/Icinga
Icinga e Icinga 2
En octubre de 2012 anunciaron «Icinga 2», la cual fue escrita casi desde cero en lenguaje C++, tanto para la plataforma Microsoft Windows® como GNU/Linux®. Como bien sabéis, tener solamente una idea clara de lo que se quiere y/o necesita no es ninguna garantía para el éxito: llevar a cabo una versión estable del núcleo tomó varios años y en el mes de junio de 2014 tuvo a bien su renacimiento. Esta «competencia», a veces fuerte, entre Nagios e Icinga los fortalece a ambos; en general el mundo de la tecnología así es como puede evolucionar. A Icinga le tomó 4 años y medio de duro trabajo el lograr su independencia de Nagios por medio de Icinga 2. Para el caso de Pandora FMS, ya desde su planificación se tenía claro que Nagios es más bien de propósito general (aquí estamos muy conscientes de las limitaciones de Nagios). ¡De aquí es que nace una verdadera alternativa a Icinga!
Icinga, empresa como tal, hace énfasis en que, cuando utilizan el simple término «Icinga» en vez de «Icinga 1.x» se refieren a la bifurcación de Nagios (su núcleo compartido). «Icinga 2» es tan diferente que necesita una conversión para ir de uno al otro. Pandora FMS como alternativa a Icinga ofrece desde un principio el mismo núcleo, haciendo sumamente fácil la transición a la versión «Enterprise».
Llegado este punto comento que, para incluso mayor complejidad -por no decir que provoca confusión- en este asunto de los tipos, versiones y componentes y sus nombres y denominaciones, también existe «Icinga for Windows®»… Pero no, no es lo que ustedes están pensando. Si bien Icinga 2 se puede instalar en Windows®, este componente que traigo a colación es un módulo totalmente completo para PowerShell (PS), en realidad un entorno de programación para dicha herramienta. Pandora FMS toma la alternativa de guiones con los comandos estándar de PS para cuando monitorizamos en dicha plataforma. A continuación esto nos lleva a exponer a los agentes de ambas soluciones.
Métodos de recolección de datos
Simplificando al máximo, hay dos formas de obtener datos de las máquinas a nuestro cargo: les «preguntamos» directamente a nuestros dispositivos (también llamada verificación activa) o bien usamos un software que instalemos en cada uno de los dispositivos (también llamada verificación pasiva). La primera opción recae sobre los servidores de Icinga y Pandora FMS, aquí no hay mayor diferencia (estos datos bien pueden ser HTTP, correo -POP3 y sus comandos- y ping ICMP, por ejemplo). Sin embargo, otorgo a Pandora FMS una ligera ventaja en el aspecto más útil de consulta a distancia: SNMP.

Leyenda: Métodos de monitorización de Icinga https://www.digitalocean.com/community
Veamos entonces los agentes software, o simplemente agentes: Icinga utiliza «Nagios Remote Plugin Executor» (NRPE), el cual agrega además un servidor en el lado del cliente… Ya comenté el aspecto sobre PowerShell pero también es extensible a GNU/Linux: si nos vamos por lo normal y estándar podemos rápidamente crear nuestros propios diagnósticos personalizados. Informo de esto porque NRPE también espera que el servidor Nagios (o Icinga en este caso) pregunte de manera explícita por los datos a recoger, lo cual es similar al primer método de recolección de datos (y en honor a la justicia son datos más complejos como uso de almacenamiento y memoria, servicios en ejecución y muchos más que no podemos hacer por la consulta pública a la interfaz de red).
Pandora FMS trabaja de manera distinta: envía los datos en XML con su protocolo Tentacle para mayor seguridad, en un intervalo de 5 minutos (valor por defecto) al servidor especializado para ello en Pandora FMS («Data Server»).
Esto facilita nuestro trabajo y minimiza la necesidad de instalar nuevas versiones del agente, porque solo debemos configurar de manera interna pequeños guiones con una sintaxis rápida de aprender (en la versión «Enterprise» incluso va a un paso más allá: los editamos por la consola y se guarda en el servidor Pandora FMS y se reparte de manera automática en cada dispositivo, o grupos de dispositivos, así sean miles de ellos).
Pandora FMS concentra mayores esfuerzos en presentar datos de rendimiento, mientras que los estados están en el siguiente nivel de importancia. Un dato de estado generalmente es verdadero/falso, como por ejemplo «¿está en línea?», mientras que un dato de rendimiento pudiera ser «¿cuánto tiempo ha estado en línea seguido, sin interrupción?».
Notas sobre instalación
Icinga, sobre GNU/Linux, solo necesita ser instalado por medio de apt ya que se encuentra en la mayoría de los repositorios Debian y sus derivados. Para su configuración de manera gráfica se puede utilizar NConf, herramienta compatible con Nagios también (aunque en 2019 se detuvo su desarrollo y soporte). En estos casos siempre alabo al software libre porque bien podemos hacer nuestros cambios y allanar nuestro propio camino.
Para el caso de Pandora FMS se recomienda CentOS, agregar los «Extra Packages for Enterprise Linux» (EPEL), adicionar Pandora FMS al repositorio local y luego descargar e instalar con yum. También existen otros métodos de instalación como clonar directo desde GitHub o emplear Docker.
Interfaces
Icinga viene con una interfaz clásica denominada apropiadamente «Icinga Classic». Viene con HTML y CSS sin mayor dinamismo, así que necesitaremos recargar la página en cada oportunidad como al cambiar algo o agregar una configuración, etc. Fue mejorada en Icinga 2 con «Icinga Web», la cual utiliza tecnología AJAX (que esencialmente es JavaScript con el que se intercambia información en segundo plano con el servidor y modifica/actualiza la página web). Denoto que también existe «Icinga Web 2» para «Icinga 2», el cual requiere incluso componentes adicionales, como por ejemplo flatpickr (calendario más ligero escrito en JavaScript). La consola de Pandora FMS, como alternativa a las interfaces de Icinga, utiliza cualquier navegador web moderno, sin cortapisa alguna.

Leyenda: Inicio de sesión en Icinga Web 2
Captura de pantalla
Pandora FMS como alternativa a Icinga
Sí queréis probar y ver cómo funciona nuestra versión comunitaria estamos en Github y también contamos con un Dispositivo de Virtualización de Software, el cual trae CentOS como sistema operativo, todo listo para usar. Os recomiendo leer nuestras Preguntas Frecuentes, aclaratorias prácticas y directas para la mayoría de nuestras situaciones de trabajo en el área de la monitorización.
Antes de despedirnos, recuerda que Pandora FMS es un software de monitorización flexible, capaz de monitorizar dispositivos, infraestructuras, aplicaciones, servicios y procesos de negocio.
¿Quieres conocer mejor qué es lo que Pandora FMS puede ofrecerte? Descúbrelo entrando aquí.
Si tienes que monitorizar más de 100 dispositivos también puedes disfrutar de una DEMO GRATUITA de 30 días de Pandora FMS Enterprise. Consíguela aquí.
Por último, recuerda que si cuentas con un número reducido de dispositivos para monitorizar puedes utilizar la versión OpenSource de Pandora FMS. Encuentra más información aquí.
No dudes en enviar tus consultas. ¡El equipo que se encuentra detrás de Pandora FMS estará encantado de atenderte!
Do you want to know more about Pandora FMS?

by Laura Cano | Last updated Aug 27, 2021 | Enterprises
Smart business. What is it? Is yours?
Defining what a smart business is can be as difficult as defining what a smart person is. For decades, we have known that there are different types of intelligence that can help us in different aspects of our lives, and something similar happens with smart businesses.
However, since we do not want to give up on our efforts to know what it is, we can see some of the different aspects that can turn a business into a smart business. Shall we take a look at them?
Is your company a smart business?
If we want to go for a basic definition, we could say that a smart business is the one that knows how to use the resources available in order to achieve its goals.
Now this is the simple definition, but we can go further and get to know some of the aspects that outline that intelligence, which can also help you to know if our company is more or less smart. Let’s take a look at some of them.
A smart business is a company that uses digital transformation, it does not fear it
Let’s start at very the beginning because, in a way, the concept of smart business could hardly be understood in a different context than that provided by digital transformation.
Today, there are all kinds of technologies that make company operation easier. A smart company is not afraid of technology, nor the changes that adopting it implies, but rather knows how to make the most out of it to work better, achieve its goals and create business lines. Is yours capable of doing it?
A smart business is a company that knows how to manage the data it has
In the era of Big Data, we couldn’t miss a section like this for data processing, and even some authors understand that this is a essential factor in determining whether or not a company is smart.
Currently, there are countless tools capable of helping manage and use data generated by business activity, and there are even some professions specifically devoted to it, such as a CDO (Chief Data Officer). After saying all of that, which was only a brief profile, you may wonder: Does my company know how to manage data?
A smart company is a company that knows how to value its assets
A smart company not only looks towards the outside, but also pays attention to the assets it has, and especially its human resources.
Because inappropriate or unfair treatment is definitely not a sign of intelligence. A smart company knows how to value the work its staff does and reward it accordingly. It knows how to offer incentives and take advantage of new ways to make work more flexible. It knows how to keep its teams properly trained and updated. And it also knows how to motivate and involve its people in the company’s goals. Does your company do it?
A smart company is a company that knows how to communicate
Both externally and internally, communication is another factor to consider as an aspect of the intelligence of a company.
Thus, an intelligent company knows how to listen to and communicate with its customers, but not only that. It also knows how to make communication fast and efficient internally, both in vertical and horizontal relationships.
There are a lots of ways to do it. From omnichannel to tools for internal communication, you will find many options available. Does your company know how to use them?
A smart company is a company that knows how to adapt to market changes
In a time of constant change, companies that do not know how to adapt run the risk of disappearing.
A smart company knows how to recognize changes and adapt. It cares about understanding the customer and is able to offer them what they need better and faster than its competitors. At the same time, it is able to adapt its organization and production processes to market demands in order to work better and be more efficient. Is your company capable of all this?
A smart company is a company that uses monitoring
Finally, dear reader, let us take a separate section to the aspect that interests us the most from the point of view of this blog and that is relevant in terms of smart businesses. Indeed, a smart company is a company that uses monitoring
Monitoring systems are responsible for supervising IT systems (hardware, networks and communications, operating systems or applications, for example) in order to analyze their performance, and to detect and alert about possible errors.
In fact, in a modern company, computing is a kind of indispensable nervous system that runs throughout its “body” and its proper functioning is of paramount importance.
And if we talk about monitoring, of course, we should talk about Pandora FMS. Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to assist you!

by Laura Cano | Last updated Jun 10, 2021 | Community, Geek culture
What is a “developer”? What do they mean for a company?
“Developer”, “DE-VE-LO-PEEEERRR”… It sounds pretty good. It’s easy to make your parents buy it when you explain them they are going to pay for your degree and they will be able to boast about their children being geniuses who joined the wave of computer science and technicalities… But what is really a “developer”? They are there, surely in your company, doing their developer stuff and talking to each other in their developer code, but few people really know what they really are.
People have studied their habitats, what they eat and even how they reproduce, whether by binary fission of their DNA or by vegetative multiplication, like sweet potatoes, but to delve further into what a developer really is, we have decided to ask them, specifically those of our company, Pandora FMS, for a definition. They will clear out all of our doubts.
Luis Calvo, the fourth member of Destiny’s Child
-Could you define what a developer is and what it means to be a developer for you?
A developer is the person who usually builds a software based on an idea.
For me it means creating and contributing with something that will later be used by other people or, someday, be seen by other developers. It is a bit like leaving some mark with your “creation”. Michelangelo made the frescoes for the Sistine Chapel, Beyoncé “Crazy In Love”. I’m happy with this.
-How does a developer like you end up spending hours worth of code into a monitoring software like ours?
Part chance, part curiosity, a job offer from a company in Madrid that I didn’t know at all and the fact that, when searching on Google, this company appears referred to in a news story as: “Ártica, the David that challenges the software giants”… This obviously sounds attractive and interesting.
-What’s the fun of it?
I love it when things get a little difficult and I have to investigate how to solve it, look into it and use some new trick, that works well, of course. I am one of those who laugh it out and have a good time disconnecting a bomb in the last ten seconds. If you ever see yourself in that situation, it’s always the yellow wire. Cut that one for sure. Or was it the red one?
José González, a misunderstood and modern being
-Could you define what a developer is and what it means to be a developer for you?
A developer is (or should be) a type of modern artist, a misunderstood being, who writes buzzwords and unintelligible symbols on a machine. For me it’s a lifestyle, like a hallmark. When someone types in code and likes it, it shows, like a tattoo. From afar, in small groups, we are often mistaken for a gang of bikers.
-How does a developer like you end up spending hours worth of code into a monitoring software like ours?
It was by chance, but when I saw the opportunity to get in here I didn’t even think twice. Working on a project like this, which covers so many areas and is so big, it’s intimidating at first, but it pushes me to face new challenges and reach new goals.
-What’s the fun of it?
I don’t know, there’s something to developing that is very addictive. Different languages, different paradigms, different types of problems to be solved, the fact of wanting to reach perfection or at least touch it… Every day is a new challenge and I think that’s what I really like.
Borja Sánchez. (For the record, it is ME who allowed him to modify the question.)
-Could you define what a developer is and what it means to be a developer for you?
A developer is in charge of transforming an idea, following a procedure, into a usable tool. Offtopic, the ‘developer’ thing is not as if you said that in a construction site all people working there are bricklayers… I do not consider myself a ‘developer’, because my work is not limited to typing in code to reach a solution already planned by others. In my case, a problem arises and I am in charge of analyzing, designing and developing that solution. Those are really three different jobs: engineering, architecture, and development (analysis, design, coding).
To be clear, the software life cycle is a cycle divided into these stages: definition, analysis, design, development, testing, validation and maintenance.
Only the “development” part is the developer’s job (whether junior or senior). In my case, I focus on the analysis, design and development stages. QA would be testing and validation. Support, project/commercial maintenance, definition.
-How does a developer like you end up spending hours worth of code into a monitoring software like ours?
Allow me to modify the question based on what I answered before… How does a systems technician end up doing the tasks of a software architect? By getting in the company without a degree and showing my abilities based on my work. Mario Pulido (another nice guy from our company) mentored my foray into the world of Pandora FMS as a technician, but after things like pandora_ux, route parser, the distributed transactional system… it was Sancho (CEO of the company) who gave me carte blanche to define new opportunities within the product.
-What’s the fun of it?
By taking care of three stages, work tasks become something more artistic, let’s say. It is not only following step by step a model of a pre-built solution, but rather I can start laying out the basis and prepare tools that will help us in the future to make more efficient developments, which are what make Pandora FMS be really flexible.
Marcos Alconada, life giver
-Could you define what a developer is and what it means to be a developer for you?
For me, a developer is a person capable of giving life to all the ideas that you can think of, technologically speaking, of course. And the meaning, for me, is to be able to make easier for people to do their work or their work environment, be it by making simple web pages, promoting their businesses (SMEs) or giving to clients, in this case those of Pandora FMS, the option to monitor their systems more easily.
-How does a developer like you end up spending hours worth of code into a monitoring software like ours?
I ended up working on a monitoring software because I consider it to be a very complete type of software. I mean, it interacts with different types of language. Until I came to Pandora FMS, I had not seen any PERL language and after all this time I already feel familiar with it. I believe that working in companies like Pandora FMS make you achieve a progressive and complete professional evolution.
-What’s the fun of it?
The best thing about my job is to develop new and cool things that I can be proud of and that make me say: “Look, I did that.” As well as looking back and seeing what I was before and what I am now. Improving both personally and professionally is one of the best parts of this job. And the free fruit that we get at the office. It is easier to work if you know that there is always a tangerine or plum in the fruit bowl.
Alejandro Campos, professional also on weekends
-Could you define what a developer is and what it means to be a developer for you?
Someone who has a demanding profession that never allows them to stop learning, even outside of working hours.
-How does a developer like you end up spending hours worth of code into a monitoring software like ours?
In my case, I finished my degree in Computer Engineering and I was lucky to get in and keep on learning.
-What’s the fun of it?
Working as a team sometimes involves finding yourself in difficult situations when it comes to modifying or complementing a code that is not yours, tracing the source of a problem and it can even add more stress to the work having all the situations that could take place covered and controlled in an increasingly complex software. However, when everything goes according to plan, and more so if you learn something new in the process, there are few things more rewarding.
As we have seen, “The Developers” are those easy going artists, life givers and problem solvers who, like architects, build a building and watch over it. Your building would be the software of your choosing in this indisputable metaphor.
Computer specialists capable of conceiving and developing computer systems, as well as implementing and launching them, using only their impressive imagination, coffee, and one or more programming languages.
From here we send our deepest love for them and for their work. We love you.

by Laura Cano | Last updated Aug 27, 2021 | Enterprises, Geek culture, Tech
The future of e-commerce: 5 ways to grow
E-commerce is skyrocketing, there is no doubt whatsoever. With unstoppable annual growth and close to 2,000 million users worldwide, e-commerce has already been able to surpass traditional commerce in some product categories and takes an important place in most of them. But what is the future of e-commerce?
Since its inception, back in the 90s, taking advantage of the Internet getting widely known, e-commerce has not stopped growing to become even more and more popular. And while growing, it has also changed the way it works and gotten more familiar for the customer. For example, who could think in the 90s that just a couple of decades later we would go shopping through a mobile phone?
During the next few years, it will keep on changing in order to increase key factors such as userfriendliness and user’s trust and loyalty. And in these changes, technology will of course play a fundamental role. How about taking a look at the future of e-commerce?
The future of e-commerce: 5 ways to grow
As we said, e-commerce forged its path based on changes and everything suggests that we will keep on bearing witness to a constant transformation in this sector for the next few years. Let’s take guesses trying to foresee some of the innovations that could be seen soon.
Integration between physical and online
Are you one of those who hate carrying bags around after going shopping? It looks like you’ll get lucky soon…
In the future, it is foreseeable that integration between virtual stores and their online versions will avoid this type of inconveniences. The Internet of Things will allow you to do your shopping easily (for example, pointing your mobile phone at the products you want to buy), without the need to carry them aroung and even avoiding to queue. It will only be necessary to have an account at the shop. You will be charged the total bill when you leave the store -which will be rather a kind of exhibition space- and you purchases will arrive shortly after at your home (perhaps by some of the interesting means that we will see below). It doesn’t get simpler than that.
New shipping ways
Did you know that some companies are already developing their own order shipping projects with drones or autonomous robots?
In the future, the current concept of shipping done by people will probably go down in history, leaving room to an army of different types of devices that will take the products you purchased to your home or workplace. Thanks to these types of technologies, shipping costs are expected to decrease, which would promote an even greater increase of e-commerce.
Virtual reality to buy as if you were in a physical store
Some online stores are already experimenting with these concepts and they are expected to experience a huge increase in the coming years.
Not surprisingly, it is one of the most anticipated functionalities for virtual reality for decades. The possibility of “going into” a virtual store as real (at least visually) as a physical store and buying stuff there without leaving your living room has been a much desired option for years. As virtual reality develops, it is to be expected that this new way of buying will become usual, contributing to the growth of a “different” type of e-commerce.
More customization
Customization in advertising, products and services is a clear trend today, but it seems like it won’t stop, on the contrary, it will even grow in the coming years.
Thanks to techniques such as Big Data, companies will analyze user behavior to suggest their products and services, which will be fully customized. For example, thanks to your mobile phone, companies whose services you have subscribed to will know your habits and even the place where you are and suggest customized purchase options. Of course, in this type of practices, security and privacy protection will be a factor to take very much into account.
Augmented reality
Although augmented reality requires interaction with a physical environment, e-commerce could also benefit from it.
Following our previous point, augmented reality devices will be able to provide information and suggest purchase options to users just by walking down the street. For example, if a user looks at a storefront in the physical world, the device could warn them that a certain product they are looking at is available online for a lower price.
Back to the present and to monitoring
And now that we’ve seen some possibilities for the future of e-commerce, how about we go back to present?
As we have already said, e-commerce is currently very relevant and represents for many companies the majority – or even the integrity – of their income. Is that your case? Do you have an online store? In that case, you may be interested in getting to know Pandora FMS.
Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!

by Laura Cano | Last updated Aug 27, 2021 | Community
Security monitoring as prevention and tool in computer security
Security Information Monitoring or Security Event Monitoring is part of Security Information Management. Yes, I acknowledge they are flashy names and that even experts have their differences about concept and scope. Here in Pandora FMS, flexibility is part of our name, so, hereby, I will abbreviate it as Security Monitoring. As you can see, it is short and manageable!
If this is your first time reading Pandora FMS blog, we are glad to inform you that in our programming plan for 2020–2021 we have included security monitoring as another element of our IT supervision software.
In monitoring systems, the use of alerts for when an event takes place, whether authorized or not, is inherent in the network system. Said alerts are easily defined with Pandora FMS to detect changes or behaviors, even suspicious ones, for their collection as data and, after being analyzed, turn them into information.
This set of alerts also includes those that are more used and interesting: free disk space, workload, etc. They are predictable and quantifiable parameters, but how can we apply it to the issue at hand, security? With the help of a very specialized software, such as Lynis, you may also obtain a quantitative analysis, with whose result you can set a security qualitative state in your system.
Metric use
Any system can be degraded if it is not properly improved over time. To know if an improvement has been made, it must be measured, quantified and compared. But in order to measure anything, it must be defined. If defined, it can be measured and monitored. That includes security.
Directly, Pandora FMS intervenes in the following key aspects, to name a few and to precise our work:
- Keeping track of service level agreements (SLA): it is very important to check the expiration date on a regular basis. That way, you ensure you won’t have no support if there is a failure or no access due to a lack of license to any of the business-critical applications.
- Device inventory monitoring.
- Pandora FMS supports third party authentication through LDAP or Active Directory (except for users with admin permissions, who always authenticate locally), so user and password management can be handled massively. You can even monitor a server with the OpenLDAP Plugin.
- Managing any other type of issue, including a security one can be managed through Integria IMS, a Pandora FMS suite software.
- Supporting backup management, even for different applications, to somehow protect from ransomware attacks.
- You may check antivirus programs work through software agents in an automated way, and also interactively through eHorus, another Pandora FMS suite product.
Previously we mentioned Lynis to check for updates and security patches on GNU/Linux systems, but also through Windows Management Instrumentation (WMI)® you will have a clear and exact overview of the coverage status of the possible vulnerabilities in the software installed on Microsoft Windows®.
Let’s say, for example, that you need to monitor backup executions on a weekly basis: it is important to know what success percentage you have. So you choose the metrics on the time dimension against the number of times correctly performed (that is, the pseudocode would be: number of times correctly performed divided into the number of performed backups within a week). An indicator like this gives an exact image value of your security monitoring.
What security monitoring is not
Often a great way to define a concept is by means of its “opposite”. That is why I take this chance to set what an Information Security Management System (ISMS) is. It is an extremely standardized field, whose main rule is ISO/IEC 27001, internationally, and then in each country according to its own laws.

Caption: “Deming Cycle” or PDCA: “Plan-Do-Check-Act” used in ISO/IEC 27001
Image: https://commons.wikimedia.org/wiki/File:PDCA_Cycle.svg
In security monitoring, prevention is the biggest advice, by unifying events and collected metrics. For example, to cite a critical and vital case for many companies such as electronic payment: there is the Data Security Standard for the Payment Card Industry (PCI DSS) that sets measures such as sending duly encrypted information on clients, on a mandatory basis, and the use of firewalls to prevent intruders from accessing the data you have stored about your clients. A well implemented Information Security Management System (ISMS) includes security audits, either regularly or unexpectedly (or both even), and must ensure that these two resources (and others, in addition) are working and are being used correctly.

Caption: Common firewall configuration, an important element in Security Monitoring
Image: https://commons.wikimedia.org/wiki/File:Firewall.png
On the other hand, in Security Monitoring you can offer reports about whether the security certificates for information encryption are in force and operational, so that they can be renewed in advance in order to keep communications encrypted at all times. Likewise, you will be able to monitor the company firewalls, where, how and when they are working, and restart them through alerts if necessary. These are just two examples that provide reporting tools on strong bases, but they are not and are do not replace an ISMS!
Thus, at this point, an ISMS covers many aspects and in each of those aspects, security monitoring ( ) may or may not be present:
) may or may not be present:
- Patches and updates
 and their automated management.
and their automated management.
- Antivirus status
 , as well as the network status regarding spam filtering.
, as well as the network status regarding spam filtering.
- Staff training regarding fraud and its prevention ☒.
- Network and computing resource usage
 .
.
- Mobile devices on your network and its security ☒. (Although, at least, you can report connection times, megabytes consumed, etc., the basics).
- Services and their accesses through user permissions
 .
.
- Data leak ☒. Delicate task, mostly based on staff surveillance (although you will be able to monitor the application records in the company and generate reports that look for specific fields and values in them).
- It is important to fully comply with the legislation in each country ☒.
- Depending on the size of the company, evaluating whether it is possible to implement Unified Threat Management, which despite its disadvantage of being a single point of failure is relatively easier to manage and security monitoring can benefit from it
 .
.
ISMS Tools
I do not intend to name them all, and I explain it oriented towards security monitoring:
- Network audit: looking for router models, which ones connect the company or cataloging information. In its analysis, models are correlated against firmware installed versions, exposed ports, etc.
- Perimeter Security: it sets or determines the different layers or steps, from the point of view of outside the company, to “get” to the network audit components.
- Penetration test: the so-called red team, personnel totally foreign to the company and coordinated to attack and try to enter without knowing the previous audit information.
- Web audit: both internal to the web server within the company, and its encrypted synchronization to the web server hosted by third parties on the Internet. It also includes legal aspects.
- Forensic Audit: to perform an exhaustive analysis of post-mortem incidents. In case evidence is needed, part of them can be provided by Security Monitoring.
Before finishing this article about security monitoring, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!
Read our related success story and see the results we’ve got

by Laura Cano | Last updated Jul 17, 2021 | Enterprises, Tech
Digital maturity; find out what it is and if your company reached it
Do you know what digital maturity is? Do you understand how achieving it can affect your company? Do you know how to detect if you already reached it?
Knowing what digital maturity is and the ability to assess it can be essential for a company. In this article we will find out what digital maturity is and see some clues that can indicate the degree of digital maturity a company has. Shall we get started?
What is digital maturity?
Digital maturity is the degree to which a company is able to take advantage of digital technologies to improve in all possible areas, from economic performance to relationships with customers, including business processes, productive processes, internal relations, etc.
The concept of digital maturity is closely related to that of digital transformation. If we understand the later as the process that companies carry out in order to incorporate and take advantage of the use of digital technologies, digital maturity would be kind of a goal to achieve, a place where you can look back and think “we have done a good job”.
But it doesn’t end here. There are a some aspects you have to take into account.
- Digital maturity is not static. As digital technologies get developped (and this keeps on going, and at an ever-increasing rate!), you will have to continue incorporating them into your company in order not to be left behind.
- It is not always easy to understand if you have managed to reach digital maturity or if, on the contrary, your company is a “newbie” who’s lost when it comes to using digital technologies.
How can I know if my company has reached digital maturity?
Even knowing that it is a dynamic concept and that, therefore, you cannont stay in your comfort zone, it is legitimate to wonder whether at a certain point you have reached digital maturity. The answer to this question can indicate both the digital transformation stage you are in and whether the practices you are doing are bearing fruit. Although each company has its particularities, there are clues that may guide you. Let us take a closer look at a few of them.
Do you have digital awareness?
It is something that should encompass the whole company and can influence it on many levels.
On the one hand, you must have your digital transformation goals clear as well as what measures you are going to take to achieve them, without forgetting to set ways to measure the degree of success achieved. On the other hand, it will be necessary to take into account the digital dimension in all the important decisions you make regarding the company. Are you doing it?
Furthermore, do you have the importance of digital technologies in customer relationships clear? Do your employees have in mind the importance of the company’s digitization?
At the end of the day, it is all about always keeping in mind the digital field, its importance and never losing sight of it. Is it like that in your company?
The most important point is the customer
If that’s not clear for you, well that’s pretty bad. The client is essential, that is why it is located in the center of digital transformation. If we do not keep all this in mind, it will be impossible to know what our degree of digital maturity is.
Let’s see some more specific questions. We assume that you have a website and an online store (if applicable), but that’s only the beginning. How many digital communication channels do you keep open and with what degree of effectiveness and satisfaction? Have you reached omnichannel? How well do you handle mobile technologies? Have you thought about responsiveness? Do you have your own app? How do you handle social networks? They are just a few questions. Ask yourself many more and evaluate your answers.
Do you use digital technologies internally?
Remember that using them in customer relationships is only one of its aspects. Digital technologies can be used in multiple fields, such as internal communications, different kinds of processes or flexible work ways, among others. Are you using them?
Furthermore, its use will frequently require training and learning. Can your employees use and take advantage of them? Do you have specialized staff in key aspects, such as management or maintenance? Is all of this Greek to you? Then you have a lot of work to do yet…
What about data?
This is a very specific aspect of the internal use of digital technologies. Data is nowadays a hot topic more than ever, but do you know what to do with it? Technologies like Artificial Intelligence or Big Data are not just something to chat about over coffee. Many companies use them in their day to day and have incorporated them in processes such as decision making.
In addition, you should not lose sight of other issues such as the correct data management. Is it effective? Is it safe? Data is important, don’t forget about them!
Look around you and don’t stay behind
We already warned you: reaching digital maturity does not mean that you can stand still and get a pat on your back. You can have it one day and start staying behind a short time later.
Digital technologies don’t stop and neither should you. Look around you. The world around you. Analyze other companies, learn from their successes and failures, and try to stay ahead of them. Are you a digital leader?
Are you investing in digital technology?
This is all very nice, but if you do not invest, you will most likely have tremendous difficulties reaching digital maturity. How much do you spend on digital technologies? Do you consider it enough or not? Furthermore: Are you taking advantage of the technology you have? Do you have technology that allows you to monitor the state of the technology itself?
Digital maturity and monitoring
To finish off, there’s a key issue left: monitoring.
Monitoring systems are responsible for surpervising IT systems (hardware, networks and communications, operating systems or applications, for example) in order to analyze their performance, and to detect and alert about possible errors.
The very fact of having a good monitoring system for computer systems can be key in determining whether your company has reached digital maturity or, on the other hand, has still has a long way to go.
Pandora FMS can be applied in businesses large and small, read our success story
Do you still not have a good monitoring software? Do you already have one but want to explore other alternatives? How about discovering Pandora FMS?
Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!
by Laura Cano | Last updated Aug 27, 2021 | Features, Tech
The network discovery software that turned Pandora FMS upside down
Previously, in Pandora FMS blog, we learnt a little about the great revolution that the Discovery feature brought to Pandora FMS. This tool reduces the complexity of certain existing features in Pandora FMS, and also introduces new tools that turn this software into a complete monitoring system.
In today’s episode we are going to take a walk through the bowels of one of its tools, Discovery Net Scan, which is an exponential upgrade to recon tasks. Are you ready?
Network discovery software: What is Discovery Net Scan for?
Discovery Net Scan is created to discover devices on a network, simultaneously kicking off some kind of monitoring for those devices.
Let’s see those real examples that you like so much. Imagine you are going to start monitoring your office, where you can find multiple devices connected to the same network. Within these devices, there might be personal computers, servers, routers… The thing here is to monitor every last device you have in your office. This would lead us to have to create each of the agents that point to these devices individually, which takes a lot of time and effort. Thanks to this tool, however, all these agents will be created automatically by just configuring a Net Scan task.
Network discovery software: How does Discovery Net Scan work?
We will explain how Net Scan task configuration works following several steps:
- To begin with, enter a descriptive name of the chekup that you are going to carry out, such as the name of the network that you want to monitor.
- Then, enter the network or networks that you want to discover with your network discovery software, adding the IP and the mask that you are going to analyze.
- Enter an interval with which this task will be executed automatically or configure it to be launched manually.
- Once you have entered the general fields, configure the initial monitoring that you will perform on the devices found:
a. You can choose a template with predefined modules.
b. You can choose SNMP monitoring if you correctly enter the necessary data to do it.
c. You can specifically monitor Windows elements thanks to the existing WMI tool in Pandora FMS.
d. You can detect additional information from the devices, such as their operating system or whether they belong to a VLAN.
Once created you can see the task being completed, as well as be able to edit or delete it.
This is how a Net Scan task is configured to start discovering new devices within a network. But… how does this task work underneath?
In order to perform this task, Net Scan relies on a library developed by Artica ST that is located within the server that executes the task, which is in charge of retrieving the network information of the elements to be discovered. It retrieves all available information from discovered computers and devices, in addition to that information configured by the user with the data entered in the configuration itself. With this information, and whenever SNMP is enabled, it tries to link all the devices found by checking different elements, such as path calculation or connected interfaces.
Network Discovery Software: Differences Between Recon Task and Discovery Net Scan
After reading all this information about Discovery Net Scan, you may wonder what the differences between old recon tasks and this new system are.
The first major difference between the two is the network device discovery improved performance and the increased scalability of the code used for such discovery.
Task configuration has been visually enhanced, simplifying the view for the user and the data to fill in. Additionally, once you have completed the Net Scan task, in the list of completed tasks you will have the option of displaying a network map representing the relationships found regarding the discovered devices.
As for monitoring, with the change of code to perform the discovery, the possibility of making WMI queries for those network Windows devices has been added, which also means obtaining additional information from said devices.
Finally, regarding event creation due to discovery, all the discoveries of a single Net Scan task have been reduced to a single event, unlike recon tasks that created an event for each device found. Thanks to this, server performance and database occupancy are improved as it does not have to generate as much information.
This tool, like all those that make up Discovery, is becoming very important within Pandora FMS. That is why, little by little and with a lot of work from our R&D team, we will keep on improving it to make Pandora FMS a more complete, fast and intuitive system for the user.
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!

by Jimmy Olano | Last updated Aug 27, 2021 | Community, Servers
Load spikes? We give you some tips to optimize MariaDB
This 2020 is perfect to check our beloved Pandora FMS server and precisely a very important component is the database (BD). As our loyal readers already know (and if you visit us for the first time you can read the introduction to architecture on our Wiki), MariaDB is one of the databases chosen by Pandora FMS to keep all your information about your device monitoring: Let’s see how to optimize MariaDB!
I am a big fan of GNU/Debian, specifically its GNU/Ubuntu distribution, but for Pandora FMS CentOS is officially recommended due to its high development stability. No worries, here you have the first tip: install MariaDB on CentOS 7.
Our second tip, as an introduction to today’s topic, is the number of devices you must monitor. For one hundred or more, apart from recommending you Pandora FMS Enterprise Version, you should use a High-Availability Database Cluster or simply HA. The following short video introduces the subject. If you want to learn more, read the article in our blog specific on this topic.
Whether you use a single server, several or many of them, you will always have in each instance a database managed by MariaDB stoically withstanding load spikes.
Who uses MariaDB?
Before optimizing MariaDB to receive load spikes, let’s see a short history… it’s short, I promise!
Wikipedia®, Google®, WordPress®, among many others use MariaDB for mission-critical tasks. There you have it, I told you the story was short, right? Ok, I know, you need to know a little bit more.
You may already know this: MariaDB is the fork of MySQL® but with a totally free license (GNU General Public License). It’s been developed and maintained since 2012 by MariaDB Foundation (MariaDB), and one of its golden clients is MariaDB Corporation.

Caption: MariaDB Foundation https://mariadb.org/about/#logos-and-badges
A MariaDB bronze client is Percona.
Since 2013, Google® hires engineers to work at MariaDB. Other companies have followed suit, or donated billions of dollars to the foundation.
Michael Widenius is one of the creators of MySQL. “My” is the name, in Finnish, of his oldest daughter and “Maria” is the name of his youngest daughter and the storage engine that was born long before MariaDB. To differentiate it, they later renamed it Aria. MyISAM is the counterpart of Aria.

Caption: Michael ”Monty” Widenius
https://commons.wikimedia.org/wiki/File:Michael_%E2%80%9DMonty%E2%80%9D_Widenius_at_MariaDB%E2%80%99s_Developers_Unconference_2019_in_New_York_City_04.jpg
Of course, due to all of this, MySQL and MariaDB are like sisters both in theory and in practice, but hold on, there are important differences!
Right at the time of writing this article, MariaDB is in its stable version 10.3.21. Since version 10.3.7, it has set itself far apart from the use and development of InnoDB.
InnoDB in turn replaced MyISAM as the default storage engine for BD tables in both MySQL and MariaDB.
There are many database storage engines, even Facebook® has its own that makes the most out of the use of solid state hard drives. There is another extremely fast one that is only stored in RAM memory and when you turn off the computer all data is erased. Others have only academic interest. Here we will talk a lot about InnoDB.
Load spikes
A load spike, in computing, takes place either due to our interaction and/or human activities or due to unforeseen events. The very fact that we all go to work at 7:30 in the morning every day creates a load spike for any computer system, for example. We must learn to live with load spikes, deal with them, or at least mitigate them to the best of our ability. Let’s see how to improve MariaDB for that purpose.
Tips
- Maximum number of connections (“max_connections”): one hundred and fifty-one by default. Some recommend raising it to 750 or even 1000. I think that we obviously should raise it but without losing sight of the hardware and/or virtual resources we have. So I don’t really set a specific number. Limits: minimum 10, maximum 100 thousand).
- Thread_cache_size: The role of these threads is to stay in memory for up to five minutes in order to be reused if possible. It is related to the previous point, the default value is 256. If we raise that one to more than 256, this one rises automatically to the same value. You could first try the maximum number of connections at 256 as a first step and evaluate the performance, although I would dare to say between 150% and 200% the value of the maximum number of connections. Limits: minimum 0, maximum 16384.
- Thread Pool: I mention it because activating it spoils the last tip. This feature is useful if we know in advance that we will have lots of short queries that will involve extra calculation work for the processor. Although Pandora FMS uses more the CPU to limit the data from the last 30 days and the rest it does is receiving and saving, which is why I consider that these threads are not any more useful in our case.
- Sync Binlog (Synchronization binary log): this would be enough for a whole article. Essentially it means sacrificing a bit of speed by ordering the operating system to write on disk after every transaction. That way, you prevent data from being lost from synchronization to database replicas. Since the default value is zero (it is in the hands of the operating system), if you increase the value to one, which is the slowest, you have to pay attention to increasing it further if you see things go too slow.
- InnoDB optimization: As I mentioned, InnoDB is very important and MariaDB uses XtraDB, a Percona-improved version for InnoDBD. At programming language level, you will not see XtraDB, since it identifies itself as InnoDB. Yes, quite a headache. However, it shares common features, and the first advice of this group to optimize MariaDB is to modify the InnoDB Buffer Pool Size. Again it depends on your hardware or virtualized resources, but it is always good to set it up to a maximum of 80% of the memory, as long as you do not have other software running on the same server and all your tables are InnoDB. Limits: minimum 5 megabytes, by default 128 megabytes. If you assign more than 2 gigabytes the number of instances must be increased (divide the pool into logical units), maximum 8192… petabytes!
- InnoDB Log File Size: depending on the value you set to the reserve fund, you will have to assign half or less. By setting a larger size for this log file, it reduces writing at the expense of increasing the recovery time if there is a failure (for example a power cut, which is quite common, or someone shutting down the server manually). Limits: minimum 1 megabyte, 48 megabytes by default, maximum 512 gigabytes.
- InnoDB Log Buffer Size: Here I recommend a figure, 64 megabytes, which reduces disk writing and reading. Limits: minimum 256 kilobytes, 16 megabytes by default, maximum 4096 megabytes.
- InnoDB Log Flush Interval: here there is nothing to change, its default value is one. But if your power supply is completely reliable, you can change it to two to increase performance. I repeat, if you are really confident that the Uninterruptible Power System (UPS) won’t disappoint you!
- InnodB IO capacity: this last tip to optimize MariaDB is better described with the storage hardware you have, although it is an approximation because you actually have to do specialized tests on each particular device. It is measured in operations per second (IOPS) and has a default value of 200 units, a value suitable for hard drives of 10,000 RPM. You must lower it to 100 (one hundred) for discs of less than 7,200 RPM. With solid state hard drives you can take it to 1,000 (thousand IOPS)!
Before finishing this article about optimizing MariaDB for load spikes, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
by Laura Cano | Last updated Aug 27, 2021 | Community
Hughes India and Pandora FMS joined together as partners
Pandora FMS keeps making friends. We like to make them all over the world. With them, we learn and share the best we have. They in turn play their part, creating a smooth professional harmony capable of achieving the impossible in the world of technology.
This time, Pandora FMS has had the pleasure of collaborating with and considering Hughes India as a unique partner. Together they seem to be on their way to an excellent and promising teamwork.
Who is Hughes India?
Hughes India is a subsidiary of Hughes Network Systems, the well-known world leading brand in providing satellite broadband networks and services. It offers advanced solutions and business offers for both public administrations and companies.
Hughes India is the largest operator of this type of service in their country, and for more than two decades they have been working, with increasing intensity, to reduce the existing digital divide between the community and large companies, achieving, among other notable goals, a great contribution to disaster prevention and recovery. We could not miss the chance to have them as allies.
But that was just the beginning, Hughes is present in all key vertical markets: banking, education, energy, defense, telecommunications or retail sectors, in addition to addressing the connectivity needs of multiple government departments.
How did we meet?
Being the best one comes with great responsibility. Superman knows it, Beyoncé knows it and so does Hughes India. And this is easy to say with the huge customer base and more than 100,000 active VSAT nodes the company has throughout the country. An honor and a huge commitment at the same time.
Hughes India used the same dashboard for many years, but times change and they saw the need to change along with them: give a new image to their network management portal to update user dashboards, have a common dashboard for nodes distributed across different gateway locations, providing detailed statistics for 100,000 nodes, and prioritize their new project to provide MPLS solutions to their customers, for example.
At Hughes India, they had multiple technologies and solutions to take seriously, and although at first they tried to cover the issue with different measures, such as an HP NNMi solution with the SIP portal or adding some open source solutions based on the client, finally they decided to go ahead with a common platform for all their clients. And, here, friends, is where Pandora FMS comes in.
Impressed by our software features, especially the ability to monitor devices on a distributed platform and its ability to support more than 100,000 nodes, Hughes India couldn’t be happier about choosing us. Only one challenge remained: tailoring the initial configuration to their needs. But thanks to Pandora FMS support and after-sales teams, they were able to change these settings with no issues to be able to monitor VSAT devices quickly.
Immediate Results
The results of this union between Pandora FMS and Hughes India did not take long in showing and being recognized by their clients. Hughes has been able to provide all of them with an updated and centralized dashboard for VSAT nodes distributed across satellite networks and MPLS infrastructures. In addition, it has also allowed them to design dashboards according to the displaying preferences of each client.
So has Pandora FMS met Hughes India’s expectations? Let’s see what Ashutosh Agarwal, their National Manager of IDC and MPLS Backbone Services tells us: “Thanks to Pandora FMS we can meet customer expectations regarding dashboards and centralized monitoring. This has contributed to creating an atmosphere of trust between the departments in charge of its operation. Pandora FMS has proven to be a great product, with many features backed up by an excellent technical support team”.
You see, we are still at the beginning of this adventure together, but don’t tell me you don’t have the feeling this is going to be great. “What do you say?” Do you want to become friends too?
by Dimas Pardo | Last updated Mar 12, 2024 | Geek culture, Tech
What are the laws of robotics?
1 ) A robot shall not harm a human being or, by inaction, allow a human being to be harmed.
2 ) A robot must comply with the orders given by human beings, except for those that conflict with the first law.
3 ) A robot must protect its own existence to the extent that this protection does not conflict with the first or second law.
What are they, and will they work in the real world?
The 3 laws of robotics are one of the best-known statements in the history of science fiction, and have often been taken as a reference when speculating on how we should create intelligent beings without them ending up harming or even destroying us.
Formulated in 1942 in the story “Vicious Circle”, by the famous writer Isaac Asimov, the 3 laws of robotics have become part of the collective imagination, to the point that many people think that an exact formulation of these laws could protect us from a hypothetical “robot rebellion”.
However, things are not as simple as they seem. In this article we will learn what the laws of robotics are and why they would not work if they had to be applied in the real world.
These precepts not only appeared in “Vicious Circle”, but were repeatedly alluded to in different stories by Asimov, and even in many later works written by other authors. According to Asimov himself, the purpose of the 3 laws in fiction would be to prevent a possible rebellion of the robots. Thus, in the event that one of them tried to violate any of the laws, the electronic brain of the robot would be damaged and it would “die”.
However, if there is one thing we know, it is that reality is very complex and it is impossible to subsume it in simple statements. And this was not something Asimov ignored, far from it. On the contrary, in some of his later stories he would pose situations in which the 3 laws could come into conflict.
This was one of the reasons why, in the 1985 novel “Robots and Empire”, Asimov would include a 4th law, called the Zero Law of robotics:
0 ) A robot will not harm Humanity or, by inaction, allow Humanity to be harmed.
This Zero Law was, in fact, intended to rule over the remaining laws of robotics, in order to resolve possible conflicts. However, it would also encounter serious obstacles “in practice”.
Why wouldn’t they work in real life?
Let’s imagine that, at a certain point, we managed to develop robots endowed with intelligence. And imagine using Asimov’s 4 laws of robotics to control their behavior. What would we expect?
Probably, we would be met with a resounding failure.
And it is not that Asimov was not skilled enough in formulating them (quite the contrary!), but that they were children of their time, and moreover, they were intended to control something that is possibly uncontrollable. Let us explain all this a little better.
The laws of robotics -especially the 3 initial ones- were created in a context in which computer science had barely begun its journey and Artificial Intelligence was a concept purely confined to science fiction.
Therefore, Asimov’s approach was that of the predetermination of the robots’ actions. All their behavior would be foreseen through exhaustive programming that would attempt to control every last detail.
However, Asimov himself warned us in his stories of the dilemmas that this could entail. Reality is enormously complex and conflict situations can arise frequently. But not only this.
During the last decades, and especially in recent years, the concept of Artificial Intelligence has been closely linked to what we know as machine learning.
This technique allows – very roughly speaking – programs to learn from experience in a more or less autonomous way. Thus, they repeatedly experience certain types of situations, after which they extract patterns that they will use in order to achieve a specific objective. This is the technique by which some programs are learning to identify images, drive vehicles or understand human natural language.
This makes us think that, if we were to develop a General Artificial Intelligence, as proposed by Asimov, it would not be completely programmable, but would be able to learn based on its own experience and draw its own conclusions.
Thus, the question arises,
Would the laws of robotics be able to control the behavior of an Artificial Intelligence developed on the basis of machine learning principles?
Even more. Although it is a hypothesis, many authors think that, once the development of a General Artificial Intelligence is achieved, it would be able to continue evolving, becoming more and more intelligent and surpassing by far the capacity of human beings.
Wouldn’t such a powerful intelligence be able to find loopholes in its code to be able to break pre-programmed laws? For example, it is not difficult to imagine that, over time, it could override the mechanisms developed to self-destruct in cases of non-compliance with laws.
Notwithstanding the above, the fact is that the debates that Isaac Asimov raised through his laws of robotics continue to be valid today and could receive a lot of attention, almost a century after he captured them in his stories. Almost nothing! Any writer would be proud to make us imagine so much and for so long.
By the way, before you go and look at your robot vacuum cleaner with a suspicious face, how about discovering Pandora FMS?
Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Do you want to know more about what Pandora FMS can offer you?
Find out by clicking here.
If you have to monitor more than 100 devices you can also enjoy a FREE 30 days DEMO of Pandora FMS Enterprise. Get it here.
Don’t hesitate to send your questions, the great team behind Pandora FMS will be happy to help you!

by Laura Cano | Last updated Aug 27, 2021 | Community, Geek culture
Perfect telecommuting open tools to work from home
«Every cloud has a silver lining». Popular sayings are wise and pragmatic. This year we added coronavirus and telecommuting to our daily vocabulary. Both words are compounds and the first one represents a danger that has massively propelled the second, whether we like it or not. Therefore, regarding remote working, in this post I will tell you all about the telecommuting open tools that we can use at home. Let’s go!
Very few countries, lucky them, have not been “visited” by COVID-19, but most of us are suffering from a very insidious pandemic. The creator and founder of Pandora FMS, Sancho Lerena, very well describes the current situation, that will keep on going for at least several more weeks at the time of writing these article (depending on the country where you are).
Certainly, there are companies that have been working remotely for years, and if we go back centuries, we can find news correspondents in distant countries as the pioneers (of course, although not working in real time). In the 21st century, with hardware developments and the ubiquity of connectivity, we have been increasingly working remotely, which calls for telecommuting open tools. According to surveys and data, roughly 70% of people want to be able to telecommute, but currently only 40% of companies have been able to actually implement it (keep in mind that, due to the nature of each profession, only around 22% of the workforce can work remotely). Before COVID-19 made an appearance, in Europe 15% of workers worked remotely, just once in a while. So we just had an increase of at least 25 points all of a sudden!

Caption: “Brooklyn home office (Wikipedia https://commons.wikimedia.org/wiki/File:Brooklyn_Home_Office,_Minimized,_At_Night.jpg )
It turns out that the modern trend is for you to do the work that many employees used to do before. In my case, in my youth I was trained as a cashier in a bank and now the vast majority of people carry out their own financial operations online (service and tax payments, insurance procedures, stock market operations, etc..). Therefore, there are just a couple of times when we have to actually go to a bank, and this is also happens in different economic areas and even government entities.
Given this situation, it is necessary to know what software we have available and evaluate it in this already changed and irreversible world of ours, without losing sight of our self-sufficiency thanks to the benefits of telecommuting open tools.
Pandora FMS
Obviously, our community version is a telecommuting open tool that will definitely help you supervise and control your computers in the office or workplace to a greater or lesser degree. Alerts will allow you to focus your time mainly on your work. You will only receive them if something that really needs your attention happens, which will ease your mind.
Now, if we really want to access our personal computers located in our office facilities… Can Pandora FMS help us? Yes, indirectly through eHorus, which can be integrated into Pandora FMS. But wait, there’s more…
eHorus for remote control

Caption: «eHorus logo»
eHorus was created years ago as an ideal complement for Pandora FMS. I use it myself with my clients -for free up to ten devices-, not only to be able to connect remotely, but also to perform basic monitoring. It can be used separately from Pandora FMS, since it has its own software agent and is managed online from its website. We can see what services are running, stop them, restart them, manage files and other tasks. The key point is that when installing the agent, we set our own access password, not shared by anyone else, not even by eHorus itself. With this tool and Pandora FMS, it will be as if we were sitting in our usual workplace.
OS: GNU/Linux

Caption: Debian 10 Buster image for wiki
( https://wiki.debian.org/DebianArt/Themes/futurePrototype )
In our homes, we can install GNU/Linux as a second operating system or, even better, keep to that end an old computer from the last five years and install Lubuntu, which takes up less resources than Ubuntu. There are different versions that come directly from the Debian distribution, and even with non-Linux kernels like Hurd or NetBSD. In the case of Pandora FMS, CentOS is recommended. This would be a very stable base to start working from home.

Caption: CentOS logo ( https://commons.wikimedia.org/wiki/File:Centos-logo-light.svg )
Web browser

Caption: About Chromium version 81
You know even more than me about this. However, I have to mention it because it is extremely essential today. Almost all applications and/or hardware already offer some web user interface. Just as I love Debian, I insist on continuing to use Mozilla Firefox, but I recognize that Chromium works much faster, although none of them are efficient in memory consumption. If the name rings a bell, yes, just as Debian is the source of many distributions, Chromium as a project comes from Google Chrome® and shares its rendering engine, called Blink, with other browsers like Microsoft Edge® and Brave®.
LibreOffice

Caption: Discover LibreOffice ( https://es.libreoffice.org/descubre/libreoffice/ )
LibreOffice® (version 6.4.4 and previously called OpenOffice® and StarOffice®) is a complete office suite that comes bundled with most GNU/Linux desktop distributions, and comes with the following applications with very intuitive names:
- Math: To edit mathematical formulas.
- Draw: For basic image editing, organization charts, flow charts, and even 3D objects.
- Impress: For slideshows.
- Calc: A spreadsheet that fully supports Microsoft Excel®.
- Writer: The text editor with which this article was written.

Caption: LibreOffice® Write opening a document stored in Google® Drive through a linked account in Ubuntu®
ownCloud

Caption: OwnCloud logo
Online file hosting services offer today many alternatives, but it is worth highlighting ownCloud and its fork Nextcloud. As its name says, it allows our own online server to share files, control their version and their encryption, control favorites, public calendars, contact management, etc. It uses the new WebDAV protocol to handle these files. This protocol was proposed by Jim Whitehead to the World Wide Web Consortium (W3C) following the vision of Tim-Berners Lee, considered the father of the Internet. You can use MySQL as a data server for that purpose and, if necessary, they offer payment alternatives for storing, if we want to delegate our management work.
There are also plugins that we can install for text and/or video forum chats, but we must evaluate them well since most of them are not official.
Etherpad and Ehtercalc
Both projects, Etherpad and Ethercalc are also telecommuting open tools, since they allow you to keep documents online to edit them in real time with other people. This can be done by any computer at home (or hosted on the Internet or in your company), as long as you install the Node.js environment which runs JavaScript language (on the client side in your web browser it also works with JavaScript). Once that is configured,call the package manager npm with which you will install Ethercalc for the spreadsheets. For Etherpad it is a little different: you also need Node.js but you will be able to clone the repository from GitHub. These are very practical programs, where security and permanence are not covered.
Drawpile whiteboard

Caption: About Drawpile
Do you remember the chalk and the blackboard? Sometimes we need to express our ideas quickly by drawing diagrams or flowcharts by hand. We just clone the project from GitHub and compile it either as a dedicated server and/or as a client as well. If you find it very complicated, you can also install it with the help of Flatpak, a package manager that will do the entire download and configuration process for you.
After installing, run Drawpile and show your ideas (yes, look at the image above, I have no talent for drawing). Choose the option to host a session, either on your local area computer by address (plus some adjustments to the firewall of your computer) or simply use the publishing service on drawpile.net for all your teleworking colleagues.
Mastodon Social

Caption: Join Mastodon
The need for communication in telecommuting is essential. There are tasks that are not urgent or worth starting a video call or email, just a message is enough. Mastodon is quite similar to the social network Twitter, with the difference that we can set up our own servers and join a federation. This is a long-term task, due to the complexity and work involved in managing a social network by ourselves, but if this quarantine becomes longer then…
Now, if you want to try it, find out in which community you feel more comfortable. And remember: if you’re not fond for any community or after joining you don’t like it, build your own instance.
Riot team chat

Caption: Riot im sign up welcome
With Mastodon, we must install the same software on each of our servers and then join the federation (they will generally accept us with no issue). But, what about a communication method involving a protocol (or “language” if you want to see it that way) for a universal federation?
The Matrix protocol (nothing to do with the film) was created for that purpose and it is part of an even larger project called Web Real-Time Communication (WebRTC). Essentially the idea is to be able to share audio and video between pairs without installing anything additional, just your favorite software and that’s where Riot team chat comes into play.
You can download the desktop version for your computer or copy the project from GitHub and unzip and configure the digital certificates to have your own server. Messages are sent and received in JSON format and are thus end-to-end encrypted.
What’s surprising about this protocol is the growing amount of apps and platforms that have joined: for iOS there is Ditto Chat, Nio and Pattle and FluffyChat for Android and iOS. For our computers there is Spectral, Quaternion, nheko Reborn, Mirage, Fractal and Seaglas. Even there are clients for command terminal and Nintendo 3DS (Miitrix)!
Kanboard

Caption: Kanboard
Finally, I present you my favorite telecommuting open tool, to such an extent that I have collaborated in its translation into Spanish: Kanboard. Based on the Kanban method (“fence” in Japanese), it is based on placing cards on it and moving, creating, destroying or reusing these labels to display the steps taken or to be taken. It was developed by the Toyota® automotive company to order and increase its production.
It is also used in software development, but it is used in remote work to set up our own server with MariaDB as a database and centralize our projects and tasks. It has a large number of plugins but it is minimalist and, if you like, even a little spartan.
Maybe when you try it, you will get the impression that it is yet another to-do list program, but don’t be fooled. It has an extension to connect via LDAP, which will allow managing a good number of users. In addition, it has images created for Docker, it allows to keep a chronometer to the tasks that we carry out and also to set tasks and events to warn the members to hurry up or about a deadline. We will be able to respond to events such as finishing a note with the assignment of a new task and/or notification to other users. Also you can set reminders based on time events or add predefined tasks at the beginning of each week, month, etc.
Before finishing this article about telecommuting open tools, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
by Dimas Pardo | Last updated Aug 27, 2021 | Community, Geek culture
Pandora FMS employees choose their favorite video games
A long, long time ago, almost before Pandora FMS green color became part of the rainbow, a revolutionary idea came from the heart of the company: creating an arcade machine, like those of arcades, so that our staff here could play at breaks, like they do at Google offices.
This extraordinary fantasy flowed from the brain of one of our former workers, Miguel de Dios, to whom, although he has the name of a western movie character, we owe everything. He got the supplies and ordered the components from the company. In his free time, also as a hobby, he began to make it.
Once assembled and fully programmed, the light that overflooded our spirits shone and the fun began. Since then, and in the absence of getting a human foosball, it is an essential part of our well-being and fun in the offices.

To show you that you should not take our love for this machine lightly, we are going to ask those who are really into it in our company what their favorite game is, where they played in the golden age of arcade games and what is their personal record in any of them.
–Dimas Pardo López, Communication.
The arcade game that you liked the most?
My top is: 1) Street Fighter II. 2) Tumblepop. 3) Metal Slug.
Where did you play?
La Rosa Arcade. My father sent me to mass and I would spend masses there. I could spend the whole the morning playing with the few coins my grandfather used to give me on Sundays. I loved that place. Then it became the meeting point before going out to party at discos and thousands of motorcycles gathered at the door. Then came the times when everyone had a console at home or preferred internet cafes. They had to close it and now it’s just a bar in my hometown.
Did you seta a record
Honestly, I wasn’t very good in any of the games. I preferred to watch the older ones play. It was exciting. Much more than watching soccer or motorcycle racing on TV. There were real machine heroes. The Lottery man once arrived with quite a bunch of coins. I remember that we were all there supporting him and we celebrated all together when he won.
-Sara Martín, Human resources.
The arcade game that you liked the most?
Ghosts ‘n Goblins.
Where did you play?
At a friend of my mother’s who had four real arcade machines at home and a pool table. I used to spend my childhood evenings with a couple of friends there. Then I discovered Counter-Strike and I started going to the internet cafe in my neighborhood.
Any records?
I think I still have the record for Pang in a Majaelrayo arcade, I should go back to see if it is still around.
-Eduardo Corral, Projects.
The arcade game that you liked the most?
I always loved Golden Ax, although I was very bad at it in general. I also spent quite the time on Metal Slug and Street Fighter II.
Where did you play?
Well, I played in an arcade in Ferrol a long time ago, almost as much as it has been closed.
Did you set a record?
Well, unfortunately no records. Also, it was hard, because it used to be very crowded so there was no time to fully devote yourself to any game. It was tough being a skinny kid in an arcade full of teenagers trying to play tough.
–Manuel Montes, Development.
The arcade game that you liked the most?
One game I fondly remember is Outrun. You drove your convertible, with the sea at the background… it was kind of cool. But the most exciting ones I remember are Street Fighter for the competition between players and Pang for the fights when I played with teammates. They were epic.
Where did you play?
In my time, games were not a game. You see, in arcade games, when I was fifteen, the room was full of hormones. Each game costed an important part of your weekly allowance, but more important than money was social status: if you played a game very well, you were admired by everyone.
Did you set a record?
I played ping pong in the arcade holding the paddle with two hands. If you can consider that some kind of record or virtuosity… there you go!
–Ramón Novoa, AI.
The arcade game that you liked the most?
Street Fighter II, without a doubt!
Where did you play
In summer, my brother and I always saw the arcades when passing by an ice cream parlor, but at the time people did not approve of arcades. So when we managed to save a few coins and sneak out to play a couple games, it was something very special.
Any records?
As I say, arcades were not entirely welcomed. I guess because of ignorance and because they would see it as a waste of time (and money). I speak of my acquaintances, of course. So the record was just that, getting some coins, running away and playing.
–Kevin Rojas, Projects.
The arcade game that you liked the most?
My favorite game is Metal Slug, ALL versions. The time I have spent learning the strategies of my enemies!
Where did you play?
I have played both at arcade places and at home with the magical MAME (multipurpose arcade machine emulator). I have two brothers, and we played all three on the same keyboard… That was worth seeing!
Did you set any record?
I think I set a record in a game I played in an arcade, one of these beat ’em up like Streets of Fury, but in 3D… But one day it disappeared from the arcade I went to. Since I didn’t know the name of the game and I was always player 2 (my brother was older), I called it “the girl’s game”. Years later, I found out that the game was called Die Hard, and it seems to be a game from a Bruce Willis’ movie.
-Sancho Lerena, CEO.
The arcade game that you liked the most?
When I was just a little boy, I was so into arcade games. My favorite one was Double Dragon. When I was just a 10 year-old boy, I could spend about half an hour playing with a single coin. Another one that I really liked was Operation Wolf, where you had to shoot with a machine gun aiming as if it were real, but it was quite a hard one and I always ended up getting killed quickly. Another one that I loved was “Shinobi”, for the martial arts and stuff, but it was also quite difficult.
Where did you play?
At that time, I used to spend the afternoons in town playing in the arcade, but also in the bar where my father used to have coffee. It is funny how the smells and sounds of that time remain attached to memories.
Did you set a record?
The real challenge was to play not so much the ones I liked but the ones that lasted the longest so I could play more with less money.
And that was the list of games our Pandora FMS colleagues loved the most. It does not seem coincidental that the love we have for these recreational adventures matches in time and space with the adorable memories that we keep of playing them. Good old times when a game was a community fight, you against the machine as exciting as it was momentous. Not surprisingly, there were people watching, and your weekly pay was literally at stake.
You can tell us about your favorite arcade games and your adventures playing them in the comments below or on social networks. We will be there to make fun of your low score or to celebrate any Tetris or Super Pang record.


by Laura Cano | Last updated Aug 27, 2021 | Community, Geek culture
Abbreviations, acronyms … What is the programmer slang?
Programmer slang is very particular, but it is by no means the exception and that is why in all specialties they have their own jargon. In this article, we will focus on showing its peculiarities. Let’s go!
SMS, MMS and cell phones
You remember the meaning of the three-letter SMS acronym, don’t you? Pandora FMS is capable of sending you alerts by text message so this term appears both in the technical documentation and in the software itself. Although it has mostly been replaced by Twitter, Telegram, etc., this word is still understood by both users and programmers. If we say RCS, does it ring a bell? Let’s have a look.
Abbreviations can have many meanings but in English, SMS means Short Message Service and MMS means Multimedia Messaging Service.
RCS means Rich Communication Services, which became the successor to MMS. RCS are being promoted by Jibe, a division of the company Google®, so stay tuned for this new development for your mobile phones as Jibe seeks to take advantage of existing hardware, but adding new features. The thing is that programmers must include all these names in the source code and think ahead, both for the developers in charge of maintaining the code (for example, IT patches) and for the end users.
Let’s think selfishly
All programming languages allow you to add comments to point out something important, or for didactic purposes (the creators of the programming language themselves must teach their colleagues and include comments in the examples for language learning). That is why we must seek the best possible way so that our ideas are fully understood, either now or in the future.
But here comes the small detail: this must include ourselves. This means adding an important note to programmer slang: write the comments as if you sent a letter to your future self.
Thinking that way, there is a high probability that your ideas will be well interpreted. But, how should you comment on your source code?
Some languages are advanced and seek to formally integrate these comments to compile them together with the program. We already talked about the Python language and we will use it here as an example. That way, when the source code is converted into machine language – ones and zeros – our comments will remain as a software help for other programmers as well as for users.
It is our duty to note that Python also allows comments only to be read by programmers. However, they also have strict rules to write them (these rules are known as PEP 8 and PEP 257).
Abbreviation considerations
With the example we saw at the beginning, this new RCS feature prevents you from using that abbreviation for any use other than to name this technology. The same happens to the reserved words of each programming language, whether they might be commands or declarations. Example such as exit or int (abbreviation of integer, used to declare a numeric variable without decimals) cannot be used for our purposes of saving in writing -and reading- the source code for us human beings.
Some words are consolidated and even have extremely wide meaning in many countries, they are exclusive to the programming language but human abstractions. A notable example here is the word OK. We won’t get into a debate about what each letter means, but the two of them together and their combinations (“Ok”, “oK”, “ok”) express the same idea: “fine”, “positive” or “correct”.
We can add another group of abbreviations not related to hardware technology but to software. It will even be fully understandable to any user, such as, TCP/, etc.
Acronyms
Even today, a significant part of the population knows the acronym HTML. Well, this language has its own system to deal with them (very clever, by the way). Firstly with acronyms -label not used anymore- and secondly with abbreviations:
The <abbr title=”Organization of the Petroleum Exporting Countries”>OPEC</abbr> was founded in 1960.
As we can see, it is actually an acronym but this particular element
<acronym>… </acronym>
was excluded in the latest HTML 5.0 standard. Let’s see then what the acronyms in the vocabulary of programmers are.
Acronyms come from Latin. Its use became popular during the Roman Empire and then spread to many other languages. It consists of simply taking, as we show, the first letter of each word being mindful of its pronunciation letter by letter. These have undoubtedly become one of the main programmer slang elements. What usually happens is that it is pronounced as a word and in the case of programmers, some even become verbs.
Recursive acronyms deserve a special mention. The most famous is GNU (“GNU is Not Unix”) and, although this term is not used directly in programmer slang, it is used at the beginning of each file that contains a script of this language (“Hypertext Preprocessor”). The most recent recursive acronym is YAML (“YAML Ain’t Markup Language”), but originally meant “Yet Another Markup Language”.
Abbreviations and apocopes
Abbreviations are also part of the programmer slang but, on the other hand, they seek to remove at least three letters to make the effort worthwhile. Do not mistake them with the symbols.
For example, the letter “s” is used to indicate seconds, and “ms” for milliseconds, the unit of time measurement most used in computing. Many times abbreviations and symbols are mixed, as it is the case of «mbps» which means «megabits per second».
But wait, there is even more, be careful: while “Mbps” has the same meaning as “mbps”, it is not the same when we use “MBps”, since this means “Mega Bytes per second”!
We finish the example with one more detail: in real and everyday life “megabits per second” is abbreviated as “Mbit/s”, which is not common to use among programmers because both the “/” and the “\” have special uses in programming languages and operating systems.
As for the apocopes, which consist of deleting part of the end of the words, perhaps the most famous case is “COM” to name “communications”, although it has also been used to represent other concepts (their use in programming languages is almost always a reserved word.)
“Numeronyms”
We finish off this section of programmer slang with numeronyms. No, you will not find its definition in the dictionary because its use is very controversial and they refuse to canonize it. As we know, we can represent our Arabic numbers by means of letters (words), but it just so happens that the opposite is possible here too. I will explain.
Obviously, the messages to the end users of any computing program in the world must be in their own native language. Said branch of study and work is called software “internationalization”, very long to say it every time you have to work in this area. Of course it is long, but, do you know that some companies also used “international-enabling” to refer to the work of programming an application in several languages?
The solution, if we want to call it that way, was to name said job i18n, since between the first and last letters there were eighteen characters. Apparently this began when a system administrator created the username “S12n” for the employee Jan Scherpenhuizen for his email account! As the rest of the employees found the idea funny, programmers took it over, but it wasn’t until the mid-90s that it became popular and widely spread:
· Globalization: g11n.
· Japanization: j10n.
· Localization: l10n.
· Europeanization: e13n.
Before saying goodbye, you know Pandora FMS, right? Just in case: Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.

by Pandora FMS team | Last updated Aug 27, 2021 | Servers, Tech
Blade and rack servers; advantages and disadvantages
Choosing between blade servers or those intended to go installed in a rack is a small headache that is repeated daily in the complex minds of technicians around the world. What configuration to choose? What can best serve my installation? These are questions that are repeated while they pull out their silvery and silky hairs.
As always, on the Pandora FMS blog we do not have the absolute truth, but we do have the best intentions in order to describe what these two types of servers consist of and some of their advantages and disadvantages, in order to help you make a good decision and untangle your troubled thoughts (or mess them further, which could also be). However, we will do it in a very basic and simple way, so that also all those who do not have great technical skills know what this exciting universe of server disposition is.
Without further ado, let’s get to know what blade and rack servers look like and see some clues to help you decide.
Blade and Rack Servers: What Are They Like?
Rack servers are designed to be installed, as you can guess, inside a rack, specifically in racks intended for this purpose. As you probably already know- and if you don’t know we’ll tell you right now – racks are a type of very specialized cabinets and are designed to house electronic components, and their size is measured in own units called “U”. If you want to know more about what a rack is and some things to keep in mind before choosing one, you can enter this excellent article.
Blade servers, on the other hand, are created to be installed in a chassis in which each of the servers that make up the whole are housed. One difference from the servers located in a rack is that in the arrangement in blade these are installed in “sheets”, perpendicular to the housing and “inserted” in it.
Blade and Rack Servers: How to Choose?
As you might assume, the choice between one type of server or another will depend on your needs.
If you need a significant number of servers, you may have the best option to have them on blade. Blades tend to take up less space and are also often more energy efficient.
If, on the other hand, your needs aren’t as demanding, you might want to have the servers in a rack. Racks are often cheaper than chassis for blade servers, so a blade installation will need multiple servers on its “sheets” to become economically more cost-effective than a rack.
However, also keep in mind that, although the rack is usually cheaper than the blade chassis, when we talk about the servers that make up each of these two provisions the opposite usually happens, and that is that blade servers are usually cheaper than those housed in racks, so the number of servers you need to purchase will also be important when deciding on one or the other option, from the point of view of money. However, as you can imagine, all this also depends on the performance of servers, range and manufacturers.
In addition, there is another solution that will leave both blade and rack manufacturers happy, such as having both types of server and taking advantage of the advantages that both provisions offer. Of course, therefore you will have to spend a certain amount of money. In addition, there are blades that can be installed inside racks, which would allow you to combine in the same space both modalities. However, if you choose this option you will need to confirm the compatibility of both types first.
Finally, one thing to keep in mind is that the regular blade servers can only be installed on chassis of the same brand, so you have to be aware of possible incompatibilities. Also, don’t forget to check the manageability; they usually include management tools.
A little monitoring
So far we’ve come, knowing a little better the differences between blade and rack servers. Do you want to know something else, very related to servers? What about monitoring? And if we talk about monitoring, we’ll have to talk about Pandora FMS.
Servers are, of course, one of the many things Pandora FMS can monitor. If you want to know more you can go here.
In addition, remember that Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!

by Samuel Bocetta | Last updated May 13, 2020 | Network
Why using Remote Checks is vital for any company
One of the biggest impacts of the Covid-19 pandemic has been the number of employees asked or required to work from home.
Whilst the capability to work completely remotely has been available for many years now, some companies have been reticent to take advantage of this due to the managerial and technical difficulties involved in managing remote teams and networks.
In order to effectively manage networks remotely, managers and IT staff need to have in place a remote monitoring software like Pandora FMS. This system allows you monitor different types of networks and avoid the problems caused by a lack of direct access to office machines.
In this article, which builds on our guide on how to work with network scanning, we’ll explain four major issues that can be caused by working remotely, and how remote monitoring software can solve those issues through remote checks.
Mass Connections
A critical security tool for remote workers is a Virtual Private Network (VPN), which protects sensitive data by encrypting it and routing it through a proxy server. Whilst this is necessary to protect your data, it can also cause problems with network load. VPN connections generate more network traffic across office servers, which can cause a VPN to fail.
Pandora FMS allows you to supervise connections from your servers and supervise individual router usage. Because of this, you can prioritize certain highly-sensitive connections and ensure that your VPN does not fail on critical systems.
Data Volume
Most remote working systems make extensive use of cloud storage, and most cloud storage software will automatically create backup files as employees work. This is one of the major advantages of cloud storage, but it can also cause problems for companies. It can quickly lead to both cloud and office-based drives being overwhelmed by huge amounts of data, rendering further work impossible.
Pandora FMS can help teams to avoid becoming overwhelmed by data. It makes use of native-level commands in your OS to directly monitor disk usage, and can alert you when disks are full or are under-performing, thus making remote work significantly easier.
Machine or Service Failures
The two issues above – increases in data volume and disk usage – can ultimately result in remote machines failing, that’s why remote checks are vital. If these machines are running key services, this can cause significant damage to your network, and make it impossible for employees to work remotely.
Of particular concern are two types of machines: those that handle payment and accounting software, and those that run fundamental networking services like Apache. A failure in either type of machine can lead to data loss, missed payments, or a complete inability for employees to access remote files.
Simulating machine failure has, in fact, become an important part of the cybersecurity market, where it is known as “chaos engineering”. Pandora FMS helps to fight against the problems caused by machine or service failures by giving you detailed oversight on the machines connected to your network, and what services they are running.
This network map can be used to generate real-time reports on the status of your network, alerting you to machines switching on and off immediately. You can also use Pandora FMS to monitor the status of critical services running on remote machines, so that you can respond to service failures immediately.
Remote checks and System Heating
For network engineers, one of the largest dangers of switching to remote work is the risk of machines overheating. Increased network traffic and increased disk usage can quickly lead to drives or cores overheating, and with no physical access to machines taking action to prevent this is difficult.
This issue is particularly common if remote teams have been provided with secure, encrypted remote working solutions. The most secure browsers today use complex encryption schemes that keep data safe, but also use relatively large amounts of computing power. The hardware charged with performing encryption algorithms is particularly vulnerable to overheating, and failure caused by this can lead to both data loss and security vulnerabilities.
Pandora FMS provides you with direct defenses against machine overheating. By using Pandora FMS, you can install remote clients on all your network machines that will monitor temperatures, alerting you to the potential risk of overheating. You can then shift network traffic away from vulnerable machines.
Going Further
There are several other issues that can be caused by remote working, though they will not affect all companies. The issues above are compounded by the use of third-party tools and services on your network, for instance, which can be difficult to monitor using standard tools. Pandora FMS provides you with the capability to track network and disk usage generated by these tools, and take action if it threatens to overwhelm your system.
Similarly, many network engineers will prefer to set up automatic responses to the common problems mentioned above. Pandora FMS allows you to configure alert thresholds that will instantly alert you if there are problems on your network, and can be configured to perform actions in line with these alerts.
Remote Monitoring and Remote Working
of the issues in the list above are new; they have been around as long as compute networks have. For some companies, however, the dramatic rise in remote working over the past few months has put their networks under unprecedented strain.
If this applies to you, you need to implement a remote monitoring system as quickly as possible, alongside other systems such as web monitoring tools. Together, these will help to keep your network, your data, and your employees secure.

by Pandora FMS team | Last updated Aug 27, 2021 | Tech
Centralize Monitoring: The Importance of the Metaconsole
Gradually, brick by brick, we will get the necessary toolkit to build a company and maintain it. If on previous occasions we have emphasized the importance of monitoring a company’s IT systems, today we will review what it is and what advantages we when we centralize monitoring. The goal is pretty simple: we want to have maximum control over the IT of a company moving unbridled to the summit.
The importance of centralizing monitoring
To be able to talk about the importance of centralizing monitoring, you must first know what monitoring is. Monitoring is “to observe by special devices the course of one or more physiological or other parameters to detect possible anomalies“. In our field, it could be translated to the monitoring of a technological device (computers, servers, cell phones…) to detect anomalies. Monitoring software has many objectives; among others we can find the maximum use of the company’s resources, the prevention of incidents and detection of problems, the notification of possible problems, cost savings, time savings and improving customer satisfaction. Pandora FMS, the monitoring software we’ll talk about, performs its functions mainly in order to be a preventive service.
Once we know what it is to monitor and what it is for, let’s put a monitoring case whose need for centralization is critical. Let’s imagine a company, “Tundra P.F.” , with offices spread over Spain. This well-advised company begins to monitor each of the servers, computers, network devices, etc. of all of their headquarters: Albacete, Palma de Mallorca, Lequeitio… with the same working tool. In total the company has a multitude of monitored devices, divided into different installations of the same tool, where each one has to be configured individually from the headquarters that is monitoring. In the end the company sees the need to hire specific personnel for each of those locations to control the configured monitoring… or not?! Pandora FMS, always with its eagle eye and always being on the breach, noticed this problem and decided to react by creating the Metaconsole!
Metaconsole. What is it, how it is used and what advantages does it have to centralize monitoring?
Metaconsole is nothing more than a Pandora FMS console where you can view, synchronize and manage in a unified way different monitoring systems of Pandora FMS (from now on instances), thus avoiding having to look at all the different systems individually.
It is a complex environment that is intended to operate with all the infrastructure you have, and not at a low level as for one instance.
Once we have installed the Metaconsole on one of our servers, the next step would be to configure the data for all the instances that we want to handle centrally. In order to perform this step, you’ll need to grant permissions to the Metaconsole admin user on the information that you want to handle within each instance. In order to obtain and modify the desired information, each instance will be accessed through the API and by direct access to its database.
It is true that, to this day, the Metaconsole does not have all the functionalities that an instance has, but in the future everything will be achieved and be managed from it. In addition, there are unique functions of the Metaconsole, such as the self-provisioning of agents, with which new agents will be assigned to one of the multiple registered instances in the Metaconsole following specific parameters.
Metaconsole is based on two modes of use: synchronization and propagation. Synchronization is based on passing all the information that has been created in the Metanconsole to the desired instances. This is critical because, for example, a user created in an instance cannot be managed from the Metaconsole, but we will be able to do it if we create the user in the Metaconsole and synchronize it with the instances. Through propagation, the Metaconsole generates information that will be provided to the instances.
Do you still want to delve deeper into this great tool, the Metaconsole in Pandora FMS? In these two links you can see in more detail the functionalities of the Metaconsole and all the services that you’ll be able to do with it:
https://pandorafms.com/docs/index.php?title=Pandora:Metaconsole:Documentation_en:Introduction
https://pandorafms.com/docs/index.php?title=Pandora:Documentation_en
As we have seen, it is totally necessary to centralize monitoring for greater order and control over the parts that make up our company’s IT, and the Metaconsole, tool of the Pandora FMS monitoring software, helps us in this.
Now that you’ve seen in the ins and outs of networks and innovations, would you like to take a walk on this path? Go even further in the world of technology? Would you spend a few minutes to know what it is to monitor computer systems and also why is it very important?
Monitoring systems monitor technology (hardware, networks and communications, operating systems, or applications, for example) to analyze its operation and performance, and to detect and alert about potential errors. And this leads us to Pandora FMS, which is the great tool thanks to which this blog is possible.
Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes. Do you want to know what Pandora FMS can offer you? Find out by going here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!
Discover the great results we got at Hughes using Pandora FMS
by Pandora FMS team | Last updated Aug 27, 2021 | Network, Servers, Tech
Server operating system: a basic and fundamental piece of software
Web server. File server. Email server… In this post we could review most of the servers we use every day; this world is highly interconnected on a global scale. I write these lines from America and whether you are in Europe or anywhere else in the world, you’ll use at least one server to read this and have the basic notions of what a server operating system is, but not without first knowing the background of this specialized software!
Non-dedicated server and dedicated server
Both will need a Server operating system, but we can even use the non-dedicated one ourselves for our daily work and to offer services to our co-workers. For example, if we have a very fast printer and despite laser technology it has a low power consumption, that turns our computer into a print server, with the inherent limitations.
Now, we can place our computer as a dedicated server simply by not logging in to the user and, if possible, uninstalling the graphical user interface. You have guessed well: a dedicated server (or simply server in the rest of this writing) only has the task of serving remote requests, including requests to be managed (software update, etc.) and we do not even need to sit in front of that computer, because it will not even show us graphics on the screen. Other things it probably won’t have, will be optical readers and USB ports; nor will a mouse and keyboard be needed (actually, when multiple servers are together they group them into a single monitor, keyboard and mouse for everyone with a converter or “KVM” device).
What has happened over the decades? Well, the cost of hardware components has fallen in price and they have been incorporating it into motherboards for our benefit as end users. In our local area network we will be able to implement them, if it is with GNU/Linux good, but be careful that the matter has drawbacks!
Computer manufacturers have made sure that we have some very good equipment at our disposal that we can use as servers for a handful of users, but also to save money they have eliminated microprocessors and chips, so that they have derived the work they did towards the operating system… And here we enter into the subject: a server operating system will not do that work, because that would be a waste of resources. What’s more, we won’t even be able to use it, it will maybe recognize the hardware additions, but it’ll need specialized controllers that you have to install separately, and no server operating system can afford to jeopardize its stability with such adaptations and spend memory and use the Central Processing Unit (CPU) for it.

Legend: Wikimedia Foundation Servers
https://commons.wikimedia.org/wiki/File:Wikimedia_Foundation_Servers-8055_35.jpg
Server hardware
An example that illustrates the previous section are network cards. We’re talking about those entries that we put a cable in, which is a little wider than the ones we use on the old office phones (even today we are assigned cubicles or offices with that endowment to communicate with us). A server will have several of them, which can be replaced without shutting down the computer, and in addition the Server Operating System will do absolutely nothing of the work that they are required to do. Encrypt any of the communications? Okay, the CPU can do it too, but such work can – and should – be done on hardware by network cards (this is a simple example to illustrate, it goes didactically).
In Spanish redundancy is disliked and avoided, but for server hardware it is the opposite: It is required! Thus, a server will also have two or more power sources, many hard drives (now of solid state), lots of random access memory (RAM) and multiple CPUs, each with multiple cores… All of this brings us to the concept of a Server operating system.

Legend: «Removable hard drives
Pixabay https://pixabay.com/photos/server-drive-bay-hard-drives-memory-4393370/
Server operating system
There are server manufacturers who assemble the entire equipment, and generally sell them directly online. We will order them by specifying the estimated workload they will have, which will cost us more money the higher the load (more hardware needed). Such producers shall recommend an appropriate and optimized server operating system.
Although we can choose a proprietary Operating System (OS), this will limit our work because we will depend on that company for everything that has to do with software. For that reason, currently a Server OS is synonymous with GNU/Linux: almost one hundred percent of supercomputers run with the penguin logo and the Ñu. The main representatives are:
- Suse Linux Enterprise Server (SLES): Legendary, pioneer since 1992 for businesses; its community version OpenSUSE, both, have extensive experience for your management.
- Gentoo: A minimalistic distribution requires more work by network administrators because they will have to “customize” it (add, install software) according to the needs of each.
- Red Hat Enterprise Linux: Long-term support and hardware-certified software make it a major competitor. Its community version, CentOS, is your favorite home of monitoring software.
- Debian: a champion in distribution and committed to free software, very stable and light. Its descendant, my favorite, is Ubuntu, which has long-term support and is also very dynamic with updates (more security, but could decrease stability). It also has a very popular desktop version; I use both.
As we said, the hardware now has a lot of computing power and prices have even lowered, which favors as business users for our own physical servers, but companies larger than ours can acquire fantastic equipment to give a step further. See.
Server of servers
Yes, I introduce that term to refer to virtual machines, making a difference with what hypervisors are. A hypervisor is another server operating system application, and can contain dozens of virtual servers that are very varied. In this special scenario I locate the monitoring, that we can perform by the way with Pandora FMS or any of the ones that we have analyzed and compared in this blog.
“Reliability, Availability, and Serviceability” (RAS) is a term introduced decades ago by the blue giant, IBM®, for its mainframes and over time for software; in fact, every Server Operating System must meet those premises.
- Reliability: Almost always delivers a satisfactory result, even if it involves closing applications that get out of control and starting them again, or even restarting a server completely (hard reset). Unfortunately, we don’t only evaluate by result and for this Pandora FMS is very capable of alerting us about restarts, failures in the mail service or database, etc; when and for how long, all of this will allow analysis for possible future events.
- Availability: regulated by the famous ‘five nines’ rule, i.e. 99.999% of online time (five minutes offline in a year). Pandora FMS has special tools for this purpose and, if we decide to delegate to a third party the hosting and operation of our servers outside our company, we will confirm whether it complies with the contracted SLA.
- Serviceability: Early fault detection and timely warning to hardware administrators count, and are very important for fault recovery if they occur. At this point, Pandora FMS and any other good monitoring software are called to account, they are special for it. Does a solid-state hard drive support 50,000 writes? How many are left? Is the server temperature right for its components? Does it meet the manufacturer’s criteria? Pandora FMS will be able to answer these and many other questions for our server of servers, but wait, there’s more.
Monitoring as a whole
The above is just an appetizer for Pandora FMS. We will be able to keep an eye on the consumption, speed and congestion of our local network with our server of servers (internal communications) and the firewalls that receive external requests via SNMP to routers and modems. With Software Agents on leased machines in different cities around the world, we will be able to account for our web servers and/or satellite servers passing the encrypted information through the “Tentacle” protocol; By bypassing firewalls (duly authorized) we will be able to centralize and create in our console visual maps of the situation in general.
As this article should end, I invite you to read our weblog publications with many more indications and solutions about device monitoring.
Oh, and before we say goodbye, remember that Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Do you want to know more about what Pandora FMS can offer you? Find out by going here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!

by Pandora FMS team | Last updated Aug 27, 2021 | Servers, Tech
How to choose servers for your company
You’ve been thinking all morning. You keep wondering how to choose servers for your company. All right, think the answer will be almost always: What do you need them for?
And the choice of servers will depend on the functions that they will fulfill, and these are also likely to be related to the size of your company.
In addition, among the wide range of possibilities you can choose from, there will be important factors, such as its price, which will also vary depending on the type of server you need.
In this article we will look at some of the most common server types and match them to the size of the companies that usually use them. Let’s go!
How to choose servers for a company; 4 options to discover
-Cloud computing
Before we go on to learn options for physically acquiring servers, let’s mention a different alternative that companies can choose from instead.
This has to do with the so-called “cloud computing”. Basically, cloud computing solutions for servers consist of contracting the services provided by the server of a provider that will be located on its premises or those of a third party.
This option is usually chosen by small companies, but also by some larger ones. It has advantages such as its price and ease of management, but control over the data and operations performed by the server will be, as you can assume, much less than if you choose to install it under your control on your own premises.
-Tower servers
Do you have a small company? A tower server may be your best option.
Tower servers are small and independent units – similar to the tower of a desktop computer – for companies that do not require very high performance. Cheaper and more basic than other server types, however they are able to deliver very satisfactory performance to small companies. They usually have all the basic elements that a server will need (CPU, motherboard, hard drive, network components, etc.) and, because of its small size and quietness, it will be easier to store them without having large premises. In addition, they will require less maintenance than other server types.
-Rack Servers
They are “classics” in the world of servers. Racks are specialized frames in which multiple servers can be stored and have a structure designed to facilitate their good performance (they usually take factors into account such as cooling, for example).
Rack servers are often used by companies with greater needs than those that opt for tower servers. They are commonly used, for example, in data centers, and they usually have rooms equipped for their use. In addition, its maintenance is more demanding than required for tower servers, which will be another factor to take into account. One of the advantages they have is that their scalability will be greater and easier than for tower units.
-Blade Servers
Blade servers are those that are installed in “sheets” forming a chassis in which all the servers that make up the whole are stored. In addition to the servers, the structure often accommodates other elements, such as cooling units or network components.
Like rack servers, blade servers are often used by companies with demanding requirements. They have some advantages over rack servers, such as taking up less space and being energy efficient, and they also have some disadvantages (they are usually more expensive, although the price inconvenience can even be reversed when a certain number of servers is reached).
Either way, don’t forget to monitor!
The ones we’ve seen are some of the different options you’ll have when choosing servers for your company. As long as you have to choose computer equipment for your company there will be many other factors to take into account, such as its price, reliability or the guarantee offered by the different brands. However, after choosing your servers, do not forget to monitor them.
The monitoring systems are in charge of supervising the systems computer (hardware, networks and communications, operating systems or applications, for example) in order to analyze their operation and their performance, and to detect and alert about possible errors. And this leads us to Pandora FMS, which is the great tool thanks to which this blog is possible.
Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
And of course Pandora FMS is also capable of monitoring servers.
Do you want to know what Pandora FMS can offer you? Find out by going here.
Or if you have to monitor more than 100 devices you can also enjoy a 30 days FREE DEMO of Pandora FMS Enterprise. here.
Do not hesitate to send us your questions. Pandora FMS team will be happy to assist you!

by Pandora FMS team | Last updated Aug 11, 2023 | Community, Features, Tech
Solarwinds alternative
Solarwinds alternative
In the present article, we want to introduce Pandora FMS as a Solarwinds alternative. We’re going to put two of the fullest-featured and highly regarded monitoring products on the market, Pandora FMS and SolarWinds, through their paces, and seeing how they shape up mano a mano. We’ll begin with a general overview of the two tools before looking in more detail at:
- General technical capabilities
- User-friendliness
- Costs and licensing
Both solutions are designed with medium-to-large business IT infrastructures in mind, and are focused on monitoring those systems to ensure detection and anticipation of problems proactively and immediately. Both platforms are also visually oriented, presenting information in the form of graphs, charts and dashboards.
Requisites
Let’s begin by looking at what’s needed, in terms of number of machines, to start using these solutions. Here is where we find our first difference: Pandora FMS is a more compact solution, requiring fewer machines for its installation. Pandora FMS consolidates almost all its functions in a single product, which, in the Enterprise version, includes all the components necessary to monitor networks, hardware, websites, and to produce reports and network maps, enable dashboard functionality, and so on. Moreover, the Enterprise version of Pandora FMS includes extra features, which, while being integrated in the console interface, have to be installed separately, for example remote control or dedicated mainframe monitoring and dedicated SAP monitoring. On the contrary, SolarWinds is made up of a series of products which can be integrated, covering all the bases by use of a modular system, but which requires more machines for its installation.

We’re going to look in detail at the components and requirements for each product, as well as carrying out a price comparison, based on the starting price points quoted by each supplier on their website:
Pandora FMS Products
With the Enterprise version Pandora FMS provides the same network oversight as the Solarwinds products listed below.
The LITE version of Pandora FMS, oriented to SME and small organizations, includes the same functions and features as the Enterprise version with the exception of WUX and Satellite server. eHorus allows remote control and Shell remotes, as well as file transfer, and is totally integrated within Pandora FMS. The prices in the Enterprise licence are for a total of 100 devices and a period of one year, including official support and access to enterprise plugin library.
SolarWinds Products
Each of these components have their own hardware requirements; some of them belong to the Orion suite of products, some of them can be integrated to create a central monitoring server modularly, others function independently. The hardware requirements of almost any of these products surpass those of Pandora FMS. Orion suite products can be installed independently or on the same machine, but will always require an additional physical server for the installation of an SQL database. As for the rest of the products, the manufacturer does not specify if they can cohabit the same machine, or whether it’s recommendable that they be installed separately. However, given their elevated hardware requirements, a setup with a minimum of three machines would probably give the best results; Orion suite, SQL database and Log & Event Manager; the other products listed above have more limited requirements and can be installed on one of the previously mentioned machines, although the manufacturer recommends those machines be used exclusively to host monitoring applications.
To put it basically: just one Pandora FMS license gives you the same monitoring coverage as the following Solarwinds products:
| Pandora FMS Enterprise |
Network Performance Monitor
Server and Application Monitor
Web Performance Monitor
Netflow Traffic analyzer
IP Address Management
Virtualization Manager
Log & Event Manager
Network Topology Mapper |
The cost of the base license includes a minimum of 100 elements to monitor, plus a year’s official support, except in the case of remote control software DameWare, whose licenses are for number of users, not the amount of hardware to manage, with a starting price of €299. In the case of Pandora FMS, the remote control cost is based on the number of devices, independently of the number of users or active sessions there are.
Requirements Comparison
After analyzing both possibilities, and the different concepts they represent, some differences are particularly noticeable:
- Pandora FMS offers 90% of its features within a single tool. Solarwinds is totally modular.
- Pandora FMS’s hardware requirements are minimal, whereas Solarwinds requires various powerful machines and additional software licences for Microsoft (Windows and SQL Server).
- To get the same functionality from Solarwinds as you can from Pandora FMS you’d be obliged to invest much more of your business’s money. In both cases the price corresponds to 100 elements and a year’s official support.
Installation
Pandora FMS comes with all the necessary components out-of-the-box to launch integrated monitoring. Some of these components come deactivated by default for performance motives, but are easily activated.

On the other hand, SolarWinds is made up of various products that must be separately installed. We’ve tried a few of them ourselves: Network Performance Monitor, Server and Application Monitor, Web performance monitor, Virtualization manager, etc. Each of these products has its own hardware requirements and its own installer, but it’s possible to install many of them on the same machine (Orion) and their integration is totally automatic, with a single point of access to the information (web console), although some will also function independently from the monitoring web console. However, to achieve the same functionalities as offered by Pandora FMS you’d have to install all the distinct Solarwinds products mentioned above.

The second difference is in the area of compatibility: Pandora FMS is officially supported on Linux systems while SolarWinds is supported on Windows. The second important difference resides in its database; Pandora FMS uses MySQL/Percona while SolarWinds uses Microsoft SQL Server.

Installing either solution is simple. The Pandora FMS team provides an appliance in the form of an ISO image with which to install the recommended OS (CentOS), along with the application and all its dependencies. In just a few minutes the software is ready to go. On the part of Solarwinds, .exe installers are supplied for each of its applications, which, via a simple wizard, quickly carry out the installation.


How user-friendly are they?
Once you log on to either one of the systems you have total access to the tools. Apart from the design component, you can see clearly the basic differences. The Pandora FMS interface is cleaner and more intuitive, featuring dynamic menus sorted into convenient subsections. It also tells you where you are in the dashboard at all times, via a green check mark in the corresponding menu. Solarwinds, for its part, presents an interface with a large amount of default information.
In terms of navigation, Pandora FMS’s clean layout makes it easy to explore, with its clearly differentiated sections, large and intuitive buttons, and little in the way of clues about what’s inside, making it obligatory to start from zero and explore for ourselves the possibilities contained in this “Pandora’s box”. Solarwinds, for its part, displays a lot more information right from the first screen, with a default appearance loaded with dashboards, graphs, charts and information-bearing elements, giving a good account of its power to present data. Furthermore, practically all tasks and configurations are executable through detailed wizards.

The final choice will depend on your own preferences: the lightness and clarity of Pandora FMS, easy to assimilate but featuring less initial information; or SolarWind’s info-bombardment, which needs time for the user to get to grips with, but which demonstrates from the get-go much of its capabilities. In the case of Pandora FMS, supplementing the lack of default visual elements is easy enough, by creating agents, dashboards and custom screens, thanks to the clarity of its interface and its “one tab” navigation system. Solarwinds’s wizards perform the same function, guiding the user through screen creation and custom options.

One useful detail of the Pandora FMS dashboard is the ease of orientation within the different menus: you always have a visual reference letting you know just where you are at any time, facilitating the learning process, something lacking in the Solarwinds GUI.

Technologies
Both tools support remote monitoring as well as agent-based monitoring on Windows and Linux. Both technologies are also similar, using principally ICMP, SNMP and WMI for remote checking, as well as port and web transaction checks. As far as agent-based monitoring goes, Solarwinds has an advantage: automatic deployment of agent software on the machines where you want them, directly from the server. You’ll need the corresponding credentials, but it makes the initial deployment go much more smoothly.
On Windows systems it’s important to keep in mind that possible problems and incompatibilities can arise (ongoing conflicting installations, pending reboots, system requirements (.NET framework version)), and so on, making a troubleshooting manual all but mandatory. Once the agents are installed, both solutions centralize management via their respective web consoles.
Solarwinds’s agents work based on a series of default plugins, installed in function of the system where they are to operate and these plugins obtain the relevant information from that system, making working with agents very easy as they run a large number of default checks. The drawback is the extra drain on the system’s memory such a loaded agent implies.
Pandora FMS comes with a powerful software agent, whose function is based not only on plugins but also on individual checks, as well as permitting the deployment of software thanks to its archive collection, proactive execution of scripts and self-healing commands. Apart from being lighter, the biggest advantage of Pandora FMS agents is their flexibility, which allows an administrator to individually carry out any kind of check in the form of a command or a script, as well as to add new community plugins (developed in any language) in order to perform more complex checks and extend the capacities of the tool still more.
Despite the ease of installing Solarwinds’s agent software and the access it affords to abundant visual information, its lack of flexibility and reliance on the included plugins can be limiting. In this category it’s not unfair to say that Pandora FMS’s powerful agent software has the lead over Solarwinds.
Furthermore, Pandora FMS incorporates dedicated Mainframe monitoring as one of its very few additional modules, and it’s 100% integrated in the Pandora FMS console, a feature that Solarwinds doesn’t include.
Adaptability in different environments
Both tools can adapt to distributed and complex environments, adopting different options to do so, for example, monitoring via NAT, monitoring DMZ networks, cloud monitoring, behind firewalls, and so on. Although they are labeled differently, the options are quite similar on both Solarwinds and Pandora FMS. Both offer distinct monitoring engines which act as proxies, redirecting the information before finally consulting a single database. In this respect both solutions have done their homework, being highly adaptable, and able to operate in diverse technological environments.

data storage/maintenance
Since we’re dealing with products whose value resides in the information they collect, the database is a critical component, impacting on the performance of the tool and its usefulness. Each solution has its own way of managing the data history of the monitored systems in order to optimize performance and maintain the data in the best way possible.
Solarwinds maintains its database through periodic purges of older data. The default values permit the storage of detailed data for a seven-day period, hourly data for a 30-day period, and daily data for 365 days.

According to these (configurable) default values, you can access reports with complete data for a week, or reports with hourly data for three weeks, and daily data reports for a period of up to the previous 11 months (the 12th month corresponds to the present and will contain more detail). This data is stored for each individual check carried out by the tool, and maintenance is automatic, and on a regular basis.
Pandora FMS is different in this feature, as it stores all data for a period of up to a year, thanks to a double database system: one in real time, and the other historic. The real-time database stores all information for 45 days by default and afterward transfers it to the historical database, where it is stored at the same level of detail. This is done by compressing the numerical data, thereby getting the most out of the storage system without suffering any negative consequences, in terms of degradation, or affecting the database’s performance.
Pandora FMS enables you to get detailed reports, and for longer, without affecting performance. Maintenance, as with Solarwinds, is performed automatically and on a regular basis.
Dashboard and custom screens
Solarwinds enables us to view large amounts of information due to its automatically generated dashboards, viewable upon installation of the applications, and completion of the wizards.


Pandora FMS ‘s requirements are considerably less demanding, but a more ample deployment is necessary at the beginning in terms of manually constructing the dashboards. Plus, Pandora FMS runs fewer default checks than Solarwinds. However, its potential is immeasurable, and thanks to its flexibility, allows the user to achieve similar, or even superior, results when compared to Solarwinds.


Both tools feature mapping utilities allowing the user to create custom maps, which can be used in dashboards to present information quickly and intuitively on a large monitor or screen, either for a team of operators or an operations manager in order to, for example, see the result of nightly backups or regional sales.
Given that Solarwind’s agents are oriented exclusively toward collecting IT data (networks, servers, applications) it’s complicated to make control panels which also include complex business metrics, such as calculations derived from a database, real-time calculations, etc. Using Pandora FMS it is possible to display this kind of real-time information, giving the edge in terms of flexibility.
Pandora FMS:


Solarwinds:


Alerts system
Both solutions also come with their own alerts systems that enable configurable automated actions to occur, such as email delivery or the execution of personal scripts. Both alerts systems feature advanced configuration options, affording them both a high degree of flexibility. The alerts are generally based on the state of modules, which are defined by thresholds.
In this sense, Solarwinds does go the extra yard, featuring an intelligent learning system that automatically modifies thresholds, basing the modifications on recent data (from the previous few days). However, this feature is also integrated in the Pandora FMS roadmap for its next major release at the beginning of this year, 2017.
events console
Both Solarwinds and Pandora FMS feature detailed events consoles that supply useful information about the platform immediately, using “activity register” mode. This permits the execution of filters and searches to locate problems or changes, extremely practical when it comes to precisely identifying the problem.
However, Pandora FMS includes an advanced feature that enables event-based alerts, allowing the user to configure automated responses to specific situations, such as updates, the introduction of new agents, received SNMP traps, and so on, adding yet another layer of flexibility to your tool.
Pandora FMS:


Network maps and topology detection
Pandora FMS and Solarwinds both automatically generate their own network maps, based on self-discovery and manually created group distributions. The design of both is similar, although Solarwinds has an especially useful characteristic: exporting maps to Microsoft Visio. It needs the Network Topology Mapper product in order to use this function, whereas Pandora FMS comes with full maps in its Enterprise version.
Both products are capable of detecting network topologies via the switches’ SNMP and map the interfaces of each device, allowing manual editing of the maps generated.
Pandora FMS:

Solarwinds:

Managing large environments
One of Pandora FMS’s most notable characteristics (much missed in Solarwinds) is large-scale management of the monitoring environment. Threshold editing, deployment of new checks, creation of new checks and new alerts, plugin execution, and so on, all performed on hundreds, or even thousands, of devices simultaneously and from a centralized point, Pandora FMS’s policies consist of complete monitoring screens that include all these elements and can be deployed on as many devices as you want, centralizing the deployment and allowing custom monitoring and the ability to change any element simply by editing the policy, whose changes are inherited immediately by all the devices included in that policy.
The most pertinent feature to note is Pandora FMS’s capacity to perform the above either via agents or remote checks, enabling total control over the monitored park.

Furthermore, among Pandora FMS’s numerous features, a software deployment system can be found, the archive collection, which allows any kind of file to be transferred from the tool to the agents, facilitating the deployment of plugins or additional personal scripts. The archive collection can be found integrated with the policies, meaning it can be massively managed. Solarwinds has a separately available product dedicated to software deployment, Secure Managed File Transfer Server.
Solarwinds does not have a solution targeted specifically at massively managing a monitored environment, making it difficult to maintain the tool, or to include new elements within our monitored area. Although Solarwinds can achieve this by means of groups, Pandora FMS has the lead in this area.
Scalability and large environments
Both Solarwinds and Pandora FMS are upward scalable to accommodate large or distributed environments. Basing their scalability on adding extra process servers, both manufacturers claim to be able to manage thousands of devices with no degradation of the service.
Solarwinds allows the addition of as many polling engines as necessary, which contact the main server, and this in turn contacts the relevant database. In the case of Pandora FMS, there are various options, from adding servers that redirect the data to the principal server, or installing processing servers (in the latter case the servers require an individual connection to the database). It’s also possible to install Pandora FMS on parallel servers and allow an external load balancer to handle the load distribution. As you can see, both Solarwinds and Pandora FMS feature diverse high availability and failover options, and not either one of them seems to have found its limit in terms of the number of devices that can be managed.
Both alternatives come with a high-level management dashboard for just those cases in which an architecture is geographically distributed, or distributed among different clients. These consoles allow the user to access all the information from different instances, with their respective databases, and provide quick access to the status of a high number of machines. Pandora FMS’s Metaconsole is free for environments of over 2000 devices; Solarwinds’s Enterprise Operations Console comes at an extra charge.
Pandora FMS:

Solarwinds:

Web reports and SLA
Again, both tools include a reports section integrated in the web console. They work in similar ways, allowing the user to choose among a series of items and default reports, showing the results in HTML in the browser itself or in PDF. Solarwinds’s variety of prefabricated reports gives it an advantage in this area, but Pandora FMS can create reports based on custom SQL queries.
Solarwinds also comes with a free product dedicated specifically to creating SLA IP reports. However, on-demand SLA reports must be created manually via SQL queries.
The following example shows an SLA report on work hours:

In terms of SLA reports, Pandora FMS has the edge over Solarwinds, whether it’s in the case of predefined monthly reports or custom reports for measuring SLA for any element, which can also be displayed as graphs or charts and extra information relevant to the specific SLA, and all via a complete wizard which allows you to modify any parameters still farther. Furthermore, thanks to Pandora FMS’s data storage model, which stores detailed data for long periods, it’s possible to get SLA reports (or any others) long after the data was collected.
The next example shows an SLA report including maintenance periods:

Inventory
Pandora FMS y Solarwinds both have an integrated inventory management system which allows you to see what hardware and software you have installed, and which can generate reports, alert on any changes in the infrastructure and perform searches to achieve real time control over your IT assets such as, for example, finding out which of your machines have an anti-virus installed. This characteristic is especially useful, facilitating enormously the work of system administrators, liberating them from the tedious task of updating spreadsheets.
Service monitoring
Is your online store working correctly? Is there any problem with deliveries? Can users access my web support? All these questions have their answers in technical components: servers, databases, and so on.
In order to cover these requirements at the highest level Pandora FMS counts on a series of features known collectively as service monitoring, through which it’s possible to define a series of critical elements, forming a tree graph like the one below, displaying the critical points of a company and where it’s possible to see how technical issues can impact on the business itself. The graph also includes the SLA status of any critical service.

In the above screenshot, the graph displays just how a failed component is affecting an intermediate service (a monitoring satellite), and producing a dip in service quality for the end-user or client.
In the following screenshot, the effect of a failed component on a larger network can be seen. You can see how the software allows a user to know whether the problem is critical, or represents a drop in service, and exactly where the problem is occurring within the infrastructure.

Solarwinds does not have a product or application that meets this demand, giving Pandora FMS another significant advantage.
Final conclusions
After an in-depth analysis of these two monitoring products it’s time to go over one more time the key points of each tool, and their respective pros and cons. Both solutions feature characteristics aimed at Enterprise environments, and supply solutions that any medium to large company needs to have covered.

Pandora FMS
PROS
- Compatibility
- Price
- Requirements
- Flexibility: the possibility to incorporate any plugin to the tool, along with the possibility to customize both the monitoring and the control panels
- Software agents
- Business-side monitoring/services monitoring
- SLA reports
- Managing huge environments: policies
CONTRAS
- Limited default content
- More extensive initial deployment
- Steep learning curve, due to its power
Solarwinds
PROS
- Easy to install
- Large number of default control panels
- Large number of plugins and default information
- Gentler learning curve: use of wizards
CONTRAS
- Price
- Requirements
- Difficult to maintain: many products and machines
- Not much flexibility to change default content
- Compatibility: only with Windows
Pandora FMS focuses its efforts on being a technically powerful product that also enables customization and flexibility, being a light piece of software that doesn’t require a large team of admins to use or maintain it. It offers a suite of tools that make managing your network simpler, and almost all its functions are incorporated in the one product.
Solarwinds offers a lot of information, control panels and content quickly and easily right from the get-go, and to a high quality. Due to its range of separately licensed products Solarwinds can achieve better results in some specific monitoring tasks such as log analysis and correlation, or exporting Microsoft Visio to its network maps.
Update. 18th December 2020
Due to the shocking news of the serious vulnerability of Solarwinds that has been reported by the United States government, we have written a more up-to-date article about Solarwinds and the importance of security in computer systems.
Do you want to know more about Pandora FMS?

by Rafael Ameijeiras | Last updated Mar 12, 2024 | Geek culture, Tech
Let’s delve into the confrontation between Docker vs Podman.
Is actually Podman the successor of the renowned Docker? Or is it just a wannabe?
What is Podman?
Podman is a container engine developed by RedHat, and yes, if you thought about Docker when reading container engine, you are on the right track.
Podman wants to be the alternative to the well-known container Docker engine, but you may wonder:
What does RedHat offer through Podman?
Why should I switch to Podman?
Is Podman the replacement for Docker or just another competitor?
it is still early to answer all these questions, but in this article you will discover what Podman’s wildcards against Docker are.

Podman’s user-friendliness
While researching for this article, I stumbled upon a presentation by RedHat engineer Dan Walsh, which started by saying how to replace Docker by Podman and outlined how to perform this migration through some steps.
The first is to run:
dnf install -y podman
Then execute:
alias docker=podman
And he ended his presentation by saying: “Any questions?”
Obviously it was a joke, but the idea was to show that switching to Podman is very simple, since RedHat engineers have paid special attention to using the same nomenclature when executing Podman commands.
So if you are a Docker user, you already know most of the commands in Podman.
So indeed it is as simple as, instead of running docker run, running podman run, and the result will be exactly the same.
Dan also refers to a Twitter thread to represent how easy the process is, where another RedHat engineer used his “migration method” using the two commands described above and, after a couple of months, had completely forgotten about it, since he continued using the same commands that had been using in Docker for years.

#nobigfatdaemons
It is a reference to the Docker service (daemon).
As you may know, Docker is a wonderful tool, with endless advantages and options.
It is capable of handling everything related to your containers: network, storage, execution, motorization, etc., and all this is managed by the same Docker service, which can bring some disadvantages, since the more containers you use, the bigger and more complex the docker service becomes.

This is why RedHat has decided to develop its tool without relying on a service, and this is the main difference between Docker and Podman.
Podman does not need a great service (daemon) to work.
They have decentralized all the components necessary for container management and have individualized them into smaller components that will be used only when necessary. This decentralization offers a large number of advantages that we will see later.
You know what else is easy and free?
Controlling your very own systems without the need for expensive software full of patches to work is at your disposal:
Podman: Pods or Containers?
Podman has a very descriptive name, and yes, when we talk about Pods we are referring to those same units that we use when dealing with Kubernetes.
Podman is capable of running containers in exactly the same way Docker does, but it is also capable of running Pods.
For those who are not familiar with Kubernetes, we will soon release an article talking about it in more depth, but for now let’s just make clear that a Pod is the minimum measurement unit in Kubernetes. The main difference is that a Pod may contain more than one container. It specially uses a main container together with one or more “sidecar containers” running in the same Pod as the main container, to “help” with the main task it was designed for.
If it sounds like black magic, for now keep in mind that a Pod is a unit where there may be one or more containers. We will delve into these concepts.
Imagine that each of the seals in the Podman logo is a container, so what you have is a pod.

Image management with Podman
Podman uses a tool based on scopio for OCI-type image inspection and management.
With Podman, you can scan OCI images without downloading them, and even better,you can take elements from one repository and move it to another directly without this image going through your device, since you won’t have to download the image in order to see or use its components.
Although Podman is able to build images very similarly to Docker with the Podman build command, the Redhat team also offers us another tool called buildah.

Buildah is an image management tool that is closely tied to the use of Podman. Among its features, it allows us to manipulate an image or a running container to create new images, build the root directory of a container for its handling or create new images in traditional or OCI format. If you want to know a little more about Buildah, here you have the link to its official repository.
Podman is rootless (Podman security)
Thanks to Podman’s modular architecture, it is not necessary to run containers as root. This is a great advantage, since you can run your containers with different users who have different privileges and without the risk of someone having access to the container service and running containers as root user, and wreaking havoc on your servers.
What Podman does when running as a non-root user is creating a directory in the user’s home directory and storing there all the information for the images and containers this user has. So, for example, if you do a podman image with your non-root user, it will show only the images that this user has created or downloaded.
Another advantage of Podman is that it is capable of using UID separation using namespaces, which provides an extra isolation layer when running your containers.
In terms of security, Docker service leaking is even more dangerous than obtaining root (sudo) privileges.
When you get admin permissions (sudo) and do something on the system, it is always registered in the system audit log, there is always a trace to follow. But if you access the Docker service and do it from a container with privileges and get rid of this container, it is virtually impossible to know what you have done. It is not saved in any log nor is there any record of your actions. Which presents Podman as a safer tool.
Integration with Systemd
Podman allows us to run containers that have Systemd enabled by default, without any modification.
It supports socket activation, so we can use systemd to configure a socket and have access to a remote API through which to communicate with Podman. A series of Python libraries have been developed in order to implement integrations and communicate with the Podman remote API.
In fact, there is already an application called Pypodman developed in Python, which is capable of running everything Podman runs locally, but remotely, communicating with the remote API, which opens up a world of possibilities.
Conclusions
Docker has advantages against Podman: firstly, the distribution and widespread acceptance it has, or tools such as Docker swarm, docker-compose, etc. Right now, if you want to orchestrate containers in Podman, your alternative is to use Kubernetes or, the one I prefer: RedHat, to use Openshift using cri-or, which is the runtime that Podman uses.
There is no clear conclusion on whether Podman is a replacement for Docker or whether it will succeed in dethroning the container king.
What we do know is that RedHat is taking their chances on the world of containers, from the acquisition of CoreOS for its use on the Openshift platform, to the development of Podman, which is currently the default container engine in RedHat 8 and CentOS 8.
Now, what do you think? Is Podman Docker’s replacement? Are the advantages it offers us enough? Do you think it will be able to take its throne?
If you are interested in the world of containers or technology overall, you will be surely interested in what we have in store just for you:
by Pandora FMS team | Last updated Aug 27, 2021 | Tech
Network Types: Are you sure you know them all, every single one?
If you thought the fishmonger’s hair net was the only kind of net you’re wrong. From Pandora FMS we will show you some more, so that you do not get lost without them.
The term “network” is used in computing to name a set of computers connected to each other in such a way that they can share resources, services, and information. There are several ways to classify these networks, based on their scope, relationship, or connection method. Let’s take a look here at some network types.
Network Types: LAN
A local area network (LAN) is a network that interconnects computers within a limited area. There we can put any residence, a school, a laboratory, the college campus or a building full of offices.
Both computers and other mobile devices use a local area network connection to share resources. We can think about interconnecting from our device with a printer or network storage, for example.
Ethernet and Wi-Fi are the two most common technologies in use for local area networks. Other LAN technologies include Token Ring, Fiber Distributed Data Interface, and ARCNET, but those have been losing users as Ethernet and Wi-Fi speeds have increased.
Types of networks: MAN
A metropolitan area network (MAN) is a computer network that interconnects, over a high-speed connection, users with computing resources from a geographic area or region larger than that covered by a local area network (LAN), but less than that covered by an extended area network (WAN), which we’ll see later.
Such networks can be public or private. They are developed with two unidirectional buses; they act independently from each other when transferring data. In equal sizes, fiber optics will give less error rate when transmitting information than if copper cable is used. Both options, however, are safe. They do not give rise to the alteration of their signal, unless the link is physically interrupted.
Network Types: WAN
A wide area network (WAN) is any telecommunications network or computing network that extends over a large distance or geographic location. Such networks are often established with leased telecommunications circuits. Large companies or institutional entities use WAN to transmit data to their staff, their customers, their suppliers, or their users, even though they are in different locations around the world. As you can imagine, this mode of telecommunication allows a company to carry out its daily function effectively, regardless of its location. Yes, and the Internet, the Internet itself, can be considered a WAN.
Network Types: WLAN
A wireless LAN is a wireless computing network that connects two or more devices via wireless communication to form a local area network (LAN) within a limited area. (Let’s remember what we talk about when we talk about a “limited area”: any residence, a school, a laboratory, the college campus or a building full of offices…)
This new option gives users the ability to move within the area while being connected to the network. WLAN can also provide a wider connection through a gateway.
WLAN has become quite popular, especially in private homes, due to the ease with which it is installed and its use. It is also the most popular in those businesses where they offer wireless access to their employees, their customers, and to those who stop by for a while.
Network Types: VLAN
VLAN (Virtual LAN) gives us the opportunity to create networks that are logically independent, even if they are covered by the same physical network.
Thus, any user can have multiple VLANs within the same router or switch. Each of these networks brings together the computers of a specific network segment. These created partitions are a manifest advantage when we want to manage a network.
Currently VLANs are configured through software and bring us many benefits in terms of security and effective computer management. You should think that devices related to one VLAN do not have access to those in others and the same thing in the opposite way. It’s quite useful if you think about segmenting your computers and limiting access between them for security reasons.
Its management is simpler, for the simple reason that we will have the devices divided by “groups“, even belonging to the same network.
Here’s an example of its benefits in your household. With the VLAN, at home, you can separate devices that do access the Internet from those that do not. This can prevent any intruder from reaching them over the Internet and infecting them with some malware.
Now that you’ve seen in the ins and outs of networks and innovations, would you like to take a walk on this path? Go even further in the world of technology? Would you spend a few minutes to know what it is to monitor computer systems and also why is it very important?
Monitoring systems monitor technology (hardware, networks and communications, operating systems, or applications, for example) to analyze its operation and performance, and to detect and alert about potential errors. And this leads us to Pandora FMS, which is the great tool thanks to which this blog is possible.
Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes. Do you want to know what Pandora FMS can offer you? Find out by going here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!
by Laura Cano | Last updated Aug 27, 2021 | Community, Network, Tech
Starting monitoring? Remember network scanning goes first!
The work of an admin or network administrator may seem ordinary, that type of work that just follows a guide, but right now, you could not be further from truth. Here I bring you network scanning, a task that could take a lot of your time… or little, if you have Pandora FMS by your side and with the help of one of those free software applications included in GNU / Linux. Let’s take a look!
The range of network devices has changed. Now there is more that desktop computers or servers, like virtual servers, voice over Internet (“VoIP”), hubs and routers with full and embedded operating systems (OS) and not forgetting wireless Access Points for mobile phones, and even wristwatches with their own OS! Yes, the latter is a trend: our beloved local area networks have become a kind of bring-your-own-device thing. Did a salesman come from company X with gigabytes of information? For courtesy and practical reasons, you allow him to connect to the local network of the company. But that doesn’t just happen with visitors. Every employee feels comfortable bringing their own laptop. Of course, as long as the nature of the company’s business allows it, not all of us work on launching rockets to the Moon or developing military defense systems.
Whether you base your favorite computer on GNU / Linux or on Microsoft Windows, we are not talking about creating the common network map with the applications of both environments. We do not document a network map so that it gets “written in stone” later, because, as the network grows, the administrator must keep on auditing to keep up with the new devices and components that each business entity takes in.
What is network scanning?
Network scanning is the process, either manual or automatic, followed to find new devices and their interfaces. Ideally, it should find as much as it can, make a network map and, upon request, generate certain timely reports. Although it is unusual, you may receive alerts (email, text or SMS, Twitter, etc.), which are more than welcomed. In that regard, Pandora FMS stands out for doing its homework very well. We must differentiate it from a network inventory obviously, in this case the second one comes from the first one.
Here I summarize just three functions:
- Network scanning.
- Network map creation.
- Alerts.
I should also mention that it could optionally be of help in cybersecurity. But that depends on the specific requirements of that department, which will have its user group when Pandora FMS is implemented in your network.
To achieve these functions, hereinafter I leave you links so that later you learn more about the features of Pandora FMS or third-party applications. Remember that Pandora FMS is open source and is flexible in terms of using your own solutions or those provided by the community.
Zenmap
First, I will start with an appetizer: Zenmap is a graphical open source interface that uses nmap (open source too, focused on security auditing) for network scanning on any network. It is an excellent example of an application aimed exclusively at network scanning: it has interactive graphics, network scanning profiles (fast, normal or intensive – it has at least 10 pre-configured profiles) and it allows you to create your own custom profiles.You may save or keep a network scanning history to later on compare and see differences (new devices or those that left your network).

Legend: Network scanning with Zenmap (Linux screenshots at flickr https://www.flickr.com/photos/xmodulo/9477360960 Creative Commons 2.0 license)
Whether for didactic purposes or for your home network, Zenmap presents an excellent opportunity to dive into network scanning concepts. However, to really go big we need to move forward.
Ways to start network scanning
The first network scanning can be started:
- Either manually, one by one, or perhaps by importing from another program in a standard format.
- By scanning IP addresses, preferably starting with your Gateway and its subnets.
- Through wizards that have predefined patterns for operating systems and / or applications (for example, Office 365, Jira, AWS, Azure, Cisco, VMWare vSphare, Docker, etc..).
Although it escapes common sense, there are usually options to exclude specific IP addresses or certain devices: in the first case you may waste time by polling addresses that you are completely sure they are not used, and in the second case Pandora FMS server will not be included in network scanning, just to name two examples.
Once finished with this task, be very careful when configuring or setting automatic and periodical network scans. It can either be set by time or an alert can also be included when new IP addresses are assigned, for example when using PHPipam.
Network scanning methods
The main tools to use, since there are many more, are listed here from simpler ones to more complex ones. Let’s start with the simplest:
- ping: essential even for non-expert users, in this blog we have published a post about it. It almost works at “machine language level”.
- ICMP (“Internet Control Message Protocol”), which is in fact integrated in Pandora FMS.
- fping: one step beyond ping and my favorite to quickly diagnose who is online.
- traceroute.
- nmap.
- Vnstat.
- Netstat.
- Wake-On-LAN: which allows remote switch-on with a magic package, if they are connected by wired network. Yes, many think this line should not be included, but I consider it must be executed before for devices to be online before collecting network information. Precisely, switching them off or configuring them for saving energy will be discussed at the end of this article.
In the category of more advanced tools for network scanning I think:
- The address resolution protocol (ARP), is often used together with Pandora FMS to scan and monitor hardware addresses with IP addresses.
- Specifically designed for Network scanning is the Link Layer Discovery Protocol (LLDP), in which devices provide us with information about themselves and the network in a standardized way (we will soon see that it works as the basis for another more important protocol).
- Other proprietary source code protocols are NetFlow, Sflow, J-Flow and NetBIOS.
I talk specifically about SNMP (v1, v2 and v3), since it collects information from the LLDP to create the MIB. SNMP (Simple Network Management Protocol) is an application layer protocol that enables the exchange of management information between network devices by “pollings” or “traps”. Essentially, SNMP normalizes communication across the entire peer-to-peer network. Version 3 supports encryption and credential authentication, which takes us to the next level.
Pandora FMS, in its Enterprise version, is specialized in most proprietary OIDs (manufacturers’ MIB library), excellent for large networks that cover a large number of devices.
Custom scripts
To take advantage of SNMP v3 you must have a registry, a credential database to connect. At first glance, it goes against the intent and purpose of Network Scanning (to face the “unknown”), but no network administrator -like programmers- can let the opportunity of reusing information to get work done go to waste.
Thus, these “scripts” or credentials can be included with the following:
- Telnet, which I consider appropriate for email servers.
- WMI, in environments with Microsoft Windows (combine with “Active Directory”).
- SSH, for GNU / Linux environments.
The last one is vital, it allows the use of software agents installed by means of Puppet, Vagrant, etc., and which may receive additional instructions for future network scans. Here we could perfectly use separate scripts that handle electricity savings like “wake-on-lan” devices, just saying. Remember that Pandora FMS uses Software Agents, but also through its different servers it directly monitors:

Legend: Network scanning with Pandora FMS Recon Server (Creative Commons 3.0 license)
Information collected
At the end we will have a good stock of elements for network inventory:
- Databases (explored by well-known ports).
- Firewalls.
- Network traffic (values in mbps).
- Outputs to the Internet (ADSL, optical fiber).
- Cisco NetFlow (hardware).
- Physical (hypervisors) and virtual servers.
- “Active Directory”, in the case of using Microsoft Windows®.
- L2 / L3 network infrastructure.
- Route tables.
- Software Defined Networks or SDN.
Before finishing, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Would you like to find out more about what Pandora FMS can offer you? Find out more clicking here.
Or if you have to monitor more than 100 devices you can also enjoy a 30 days FREE DEMO of Pandora FMS Enterprise. here.
Do not hesitate to send us your questions. Pandora FMS team will be happy to assist you!














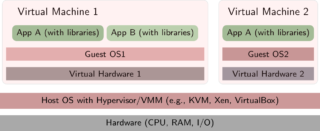
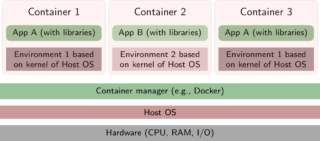







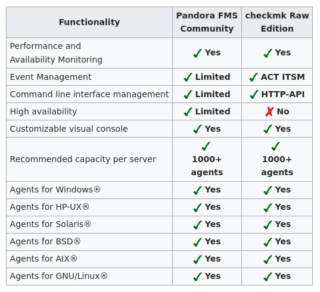

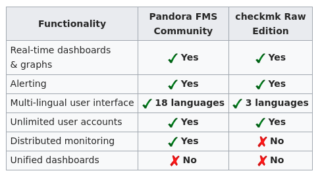







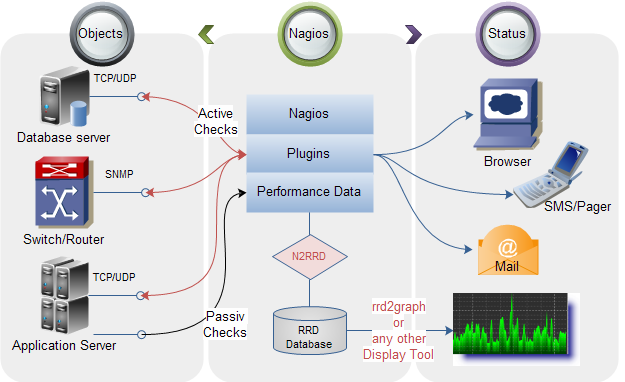
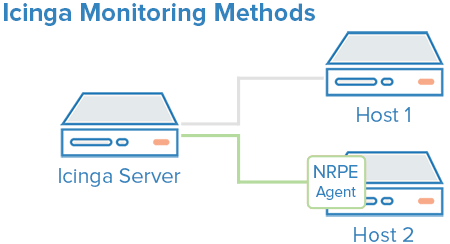





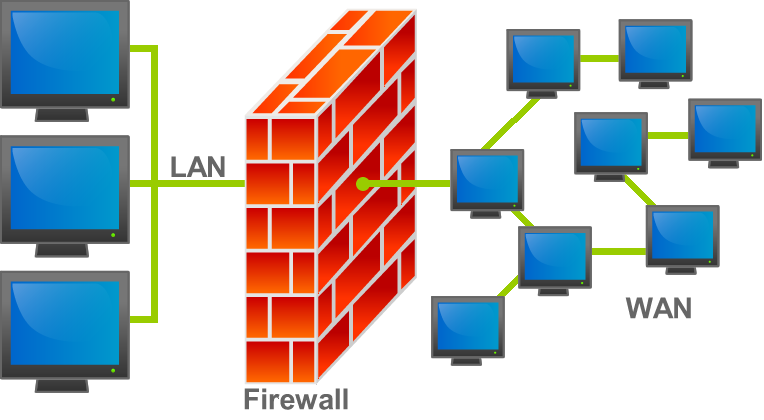
 ) may or may not be present:
) may or may not be present: