Starting monitoring? Remember network scanning goes first!
The work of an admin or network administrator may seem ordinary, that type of work that just follows a guide, but right now, you could not be further from truth. Here I bring you network scanning, a task that could take a lot of your time… or little, if you have Pandora FMS by your side and with the help of one of those free software applications included in GNU / Linux. Let’s take a look!
The range of network devices has changed. Now there is more that desktop computers or servers, like virtual servers, voice over Internet (“VoIP”), hubs and routers with full and embedded operating systems (OS) and not forgetting wireless Access Points for mobile phones, and even wristwatches with their own OS! Yes, the latter is a trend: our beloved local area networks have become a kind of bring-your-own-device thing. Did a salesman come from company X with gigabytes of information? For courtesy and practical reasons, you allow him to connect to the local network of the company. But that doesn’t just happen with visitors. Every employee feels comfortable bringing their own laptop. Of course, as long as the nature of the company’s business allows it, not all of us work on launching rockets to the Moon or developing military defense systems.
Whether you base your favorite computer on GNU / Linux or on Microsoft Windows, we are not talking about creating the common network map with the applications of both environments. We do not document a network map so that it gets “written in stone” later, because, as the network grows, the administrator must keep on auditing to keep up with the new devices and components that each business entity takes in.
What is network scanning?
Network scanning is the process, either manual or automatic, followed to find new devices and their interfaces. Ideally, it should find as much as it can, make a network map and, upon request, generate certain timely reports. Although it is unusual, you may receive alerts (email, text or SMS, Twitter, etc.), which are more than welcomed. In that regard, Pandora FMS stands out for doing its homework very well. We must differentiate it from a network inventory obviously, in this case the second one comes from the first one.
Here I summarize just three functions:
- Network scanning.
- Network map creation.
- Alerts.
I should also mention that it could optionally be of help in cybersecurity. But that depends on the specific requirements of that department, which will have its user group when Pandora FMS is implemented in your network.
To achieve these functions, hereinafter I leave you links so that later you learn more about the features of Pandora FMS or third-party applications. Remember that Pandora FMS is open source and is flexible in terms of using your own solutions or those provided by the community.
Zenmap
First, I will start with an appetizer: Zenmap is a graphical open source interface that uses nmap (open source too, focused on security auditing) for network scanning on any network. It is an excellent example of an application aimed exclusively at network scanning: it has interactive graphics, network scanning profiles (fast, normal or intensive – it has at least 10 pre-configured profiles) and it allows you to create your own custom profiles.You may save or keep a network scanning history to later on compare and see differences (new devices or those that left your network).
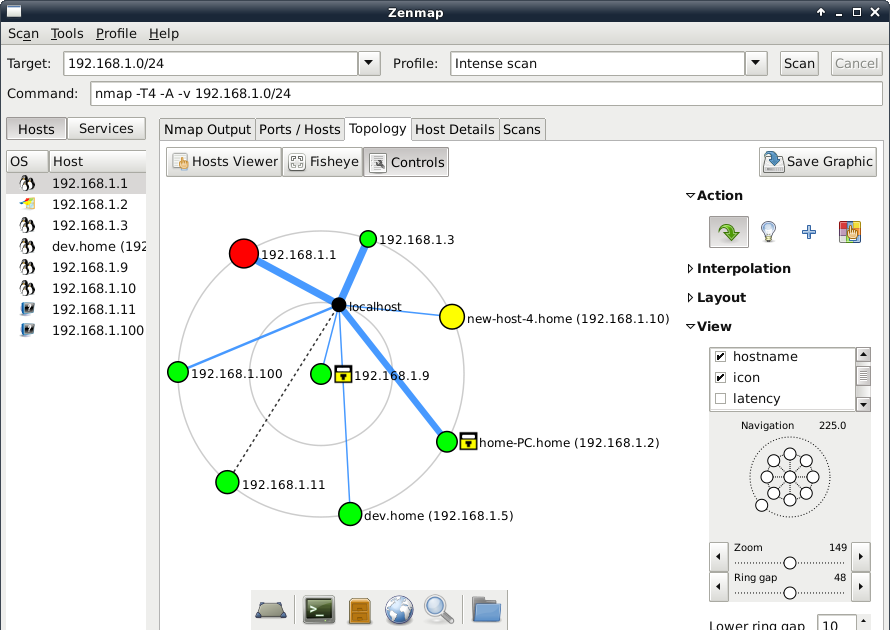
Legend: Network scanning with Zenmap (Linux screenshots at flickr https://www.flickr.com/photos/xmodulo/9477360960 Creative Commons 2.0 license)
Whether for didactic purposes or for your home network, Zenmap presents an excellent opportunity to dive into network scanning concepts. However, to really go big we need to move forward.
Ways to start network scanning
The first network scanning can be started:
- Either manually, one by one, or perhaps by importing from another program in a standard format.
- By scanning IP addresses, preferably starting with your Gateway and its subnets.
- Through wizards that have predefined patterns for operating systems and / or applications (for example, Office 365, Jira, AWS, Azure, Cisco, VMWare vSphare, Docker, etc..).
Although it escapes common sense, there are usually options to exclude specific IP addresses or certain devices: in the first case you may waste time by polling addresses that you are completely sure they are not used, and in the second case Pandora FMS server will not be included in network scanning, just to name two examples.
Once finished with this task, be very careful when configuring or setting automatic and periodical network scans. It can either be set by time or an alert can also be included when new IP addresses are assigned, for example when using PHPipam.
Network scanning methods
The main tools to use, since there are many more, are listed here from simpler ones to more complex ones. Let’s start with the simplest:
- ping: essential even for non-expert users, in this blog we have published a post about it. It almost works at “machine language level”.
- ICMP (“Internet Control Message Protocol”), which is in fact integrated in Pandora FMS.
- fping: one step beyond ping and my favorite to quickly diagnose who is online.
- traceroute.
- nmap.
- Vnstat.
- Netstat.
- Wake-On-LAN: which allows remote switch-on with a magic package, if they are connected by wired network. Yes, many think this line should not be included, but I consider it must be executed before for devices to be online before collecting network information. Precisely, switching them off or configuring them for saving energy will be discussed at the end of this article.
In the category of more advanced tools for network scanning I think:
- The address resolution protocol (ARP), is often used together with Pandora FMS to scan and monitor hardware addresses with IP addresses.
- Specifically designed for Network scanning is the Link Layer Discovery Protocol (LLDP), in which devices provide us with information about themselves and the network in a standardized way (we will soon see that it works as the basis for another more important protocol).
- Other proprietary source code protocols are NetFlow, Sflow, J-Flow and NetBIOS.
I talk specifically about SNMP (v1, v2 and v3), since it collects information from the LLDP to create the MIB. SNMP (Simple Network Management Protocol) is an application layer protocol that enables the exchange of management information between network devices by “pollings” or “traps”. Essentially, SNMP normalizes communication across the entire peer-to-peer network. Version 3 supports encryption and credential authentication, which takes us to the next level.
Pandora FMS, in its Enterprise version, is specialized in most proprietary OIDs (manufacturers’ MIB library), excellent for large networks that cover a large number of devices.
Custom scripts
To take advantage of SNMP v3 you must have a registry, a credential database to connect. At first glance, it goes against the intent and purpose of Network Scanning (to face the “unknown”), but no network administrator -like programmers- can let the opportunity of reusing information to get work done go to waste.
Thus, these “scripts” or credentials can be included with the following:
- Telnet, which I consider appropriate for email servers.
- WMI, in environments with Microsoft Windows (combine with “Active Directory”).
- SSH, for GNU / Linux environments.
The last one is vital, it allows the use of software agents installed by means of Puppet, Vagrant, etc., and which may receive additional instructions for future network scans. Here we could perfectly use separate scripts that handle electricity savings like “wake-on-lan” devices, just saying. Remember that Pandora FMS uses Software Agents, but also through its different servers it directly monitors:
- First, Pandora FMS Network Server must be enabled, which is available in both the Community and Enterprise versions.
- Recon Server: specially created for discovery monitoring and which can be used in network scanning.
- ICMP Enterprise and SNMP Enterprise servers, with discoveries in addition to the Community version.
- WMI Enterprise server for:
◦ Active Directory®.
◦ BIOS.
◦ System information.
◦ Windows® information.
◦ Printers.
◦ IIS®.
◦ LDAP.
◦ Microsoft Exchange®.
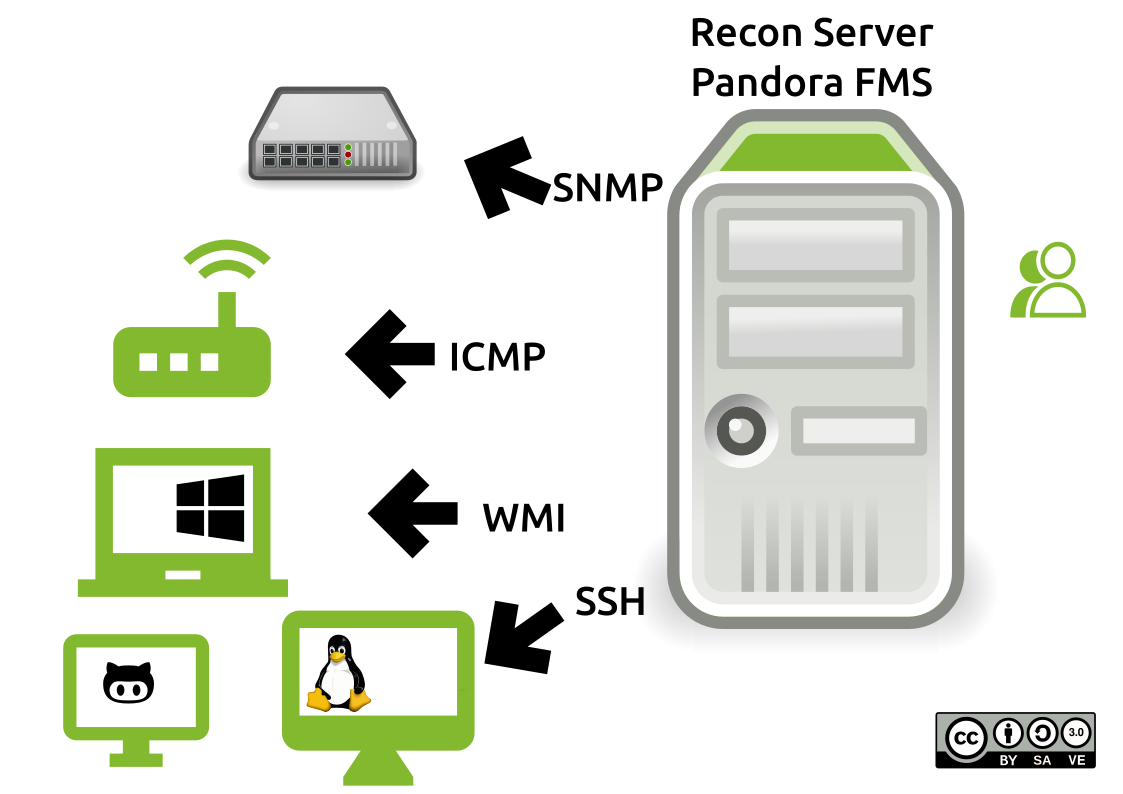
Legend: Network scanning with Pandora FMS Recon Server (Creative Commons 3.0 license)
Information collected
At the end we will have a good stock of elements for network inventory:
- Databases (explored by well-known ports).
- Firewalls.
- Network traffic (values in mbps).
- Outputs to the Internet (ADSL, optical fiber).
- Cisco NetFlow (hardware).
- Physical (hypervisors) and virtual servers.
- “Active Directory”, in the case of using Microsoft Windows®.
- L2 / L3 network infrastructure.
- Route tables.
- Software Defined Networks or SDN.
Before finishing, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Would you like to find out more about what Pandora FMS can offer you? Find out more clicking here.
Or if you have to monitor more than 100 devices you can also enjoy a 30 days FREE DEMO of Pandora FMS Enterprise. here.
Do not hesitate to send us your questions. Pandora FMS team will be happy to assist you!

Traductora a francés e inglés. Me encantan las lenguas. Amante de la ropa oversize, la tarta de queso y el chocolate caliente en invierno. Me gusta leer, escuchar música, viajar y explorar cosas nuevas. Mi frase más temida por aquellos que me conocen es “he estado pensando…”
Translator into French and English. I love languages. Lover of oversized clothes, cheesecake and hot chocolate in winter. I like reading, listening to music, travelling and exploring new things. My most feared phrase by those who know me is “I’ve been thinking…”