Some days ago, a user ask us about the new ShellShock vulnerability (affecting Bash). I give him this answer:
Most interaction with Pandora on the user side is using CONSOLE, this is build on PHP and it uses bash for executing some custom scripts defined by the admin. So if the admin enter a vulnerable script ok, it’s vulnerable, but if you’re admin you don’t need to scalate privileges. Is the same for the agent, based on perl which execute shell commands, admin defines whats there, so if you can alter that, you don’t need a vulnerability to scalate privileges.
Most dangerous vector of attack in pandora could be have a public access console, you shound not have a console on the wild, and NEVER with a public account like “demo” “demo” or left the standard passwords: “admin” “pandora”.
So. It’s vulnerable Pandora FMS to this vulnerability?. No, a user who cannot define custom scripts (means, a user is not root or Administrator) cannot use it to gain root access. Obviously if you’re Root or Admin and put a vulnerable script by your own, the security risk are *YOU* not the Shellshock 🙂
More information about CVE-2014-6271 CVE-2014-7169 (aka. shellshock)
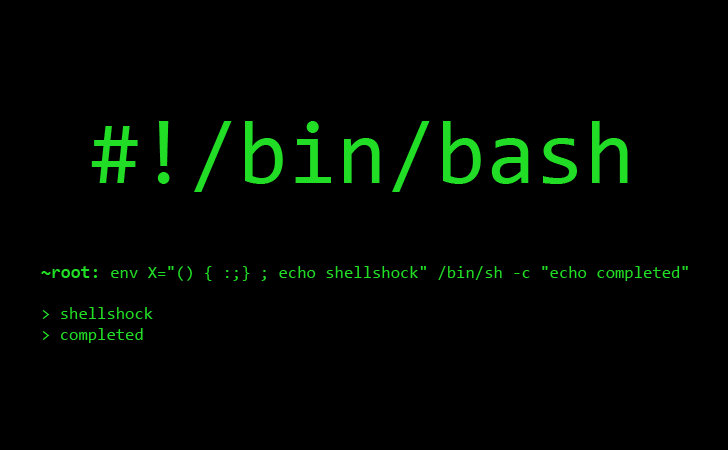
Bash Shellshock
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7169
Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring. Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.
















