All Pandora FMS tasks rely –or have to do- with port monitoring.
The ancient Roman Empire used to call what is now the Mediterranean Sea as Mare Nostrum (Nostrum Mare), stating what is now the port city of Barcelona as the entry point to Hispania (today the Iberian Peninsula) from the city of Miseno, located in the south of what is now Italy. For ancient Romans, port monitoring was crucial, and for us now too. “How?” you may wonder. Let’s see!

Roman trireme model
https://commons.wikimedia.org/wiki/File:Trireme_1.jpg
Yes, in real life each seaport is the gateway to most countries in the world, since shipping is dozens of times cheaper than land transport… although much slower than air transport. Romans and now modern states know from thousands of years of experience that port monitoring is of the utmost importance.
In computers there are also physical ports, where you connect each keyboard, monitor, etc. Thus there are countless of them, such as serial ports (9 or 25 pins or connector pins), USB, others for video such as HDMI or the old VGA. In this article we will go a step further: virtual ports, an abstraction (or rather, 65,535 abstractions, that’s the number of ports covered in 16 bits) that operating systems make in the application layer, to deliver to each program its necessary data or information. But that will be later when we return to this point.
So then, in the world of computing, port monitoring is not just any trivial question:
- Companies like @StatusCakeTeam (Twitter) perform more than 380 million website checks daily, of course contacting the respective ports of each protocol (HTTP/HTTPS, TCP, SSH, DNS, SMTP, PING, PUSH).
- In countries like the United Kingdom, Germany and Finland, port exploration is taken very seriously, to the point that there are laws about it. Obviously this does not apply to monitoring, even if it is carried out by third parties that may be hired for this task, since they are consensual tasks.
As security monitoring is among the immediate challenges of Pandora FMS, here is an overview of port monitoring, keeping that in mind.
Devices and port monitoring
Pandora FMS is a software for monitoring computer networks and their infrastructure. You can monitor the performance and health of network computers, virtual infrastructure, operating systems, and different types of security-sensitive systems and applications, such as databases, firewalls, and web servers.
Pandora FMS has a chapter entirely devoted to discovery tasks (Discovery) and includes a network exploration tool called NetScan.
In summary, this offers the option of being able to keep track of an inventory of devices and services offered by each of them (hubs, applications, modem, etc.). There everything is well explained in depth about how network exploration works. However, how can that tool determine which devices are connected or not?
For that we have to review some theory, little, but necessary. We do not intend to outperform a computer science graduate or a qualified academic, we just have to be practical.
In the 70s and 80s criteria were unified for creating the Reference Model for Open Systems Interconnection (OSI Model). It was derived from a model proposed by the International Standards
Organization (ISO, founded in 1946 by more than 70 countries), also called ISO/OSI Model.
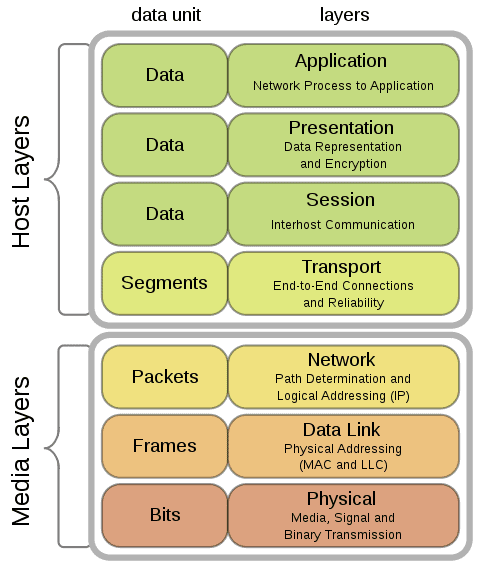
This model describes seven (my favorite number) of the layers that underlie the concepts necessary for an ideal, wide and open network:
- Physical layer.
- Data link layer.
- Network layer.
- Transport layer.
- Session layer.
- Presentation Layer.
- Application layer.
 OSI model
OSI model
https://commons.wikimedia.org/wiki/File:Osi-model-jb.svg
As a programmer I always find myself in the seventh layer and I can easily forget about the lower layers, although due to my large experience in this field this was not always the case. For port monitoring you have to “get down” to layer number 4, the transport layer, where two protocols associated with ports are located. This pair is the Transport Control Protocol (TCP) and the User Datagram Protocol (UDP).
To test connectivity again, go down, this time a single step, to the network layer where the Internet Protocol (IP) and its pair of allies, ICMP and IGMP are. I won’t keep on detailing name by name to not get you bored out of your minds. All of this is called the TCP/IP protocol suite or just TCP/IP.
It is in this third layer where you can make use of the popular ping, in my opinion the cornerstone of monitoring. There is no port there and it is excellent to determine if a device is connected to a network. On very rare occasions network administrators disable it or simply suppress it from responding to any request, so I take it for granted and ubiquitous.
Nmap
Nmap (I guess it is short for Network Mapperor Network Mapper) was created and published by Gordon Lyon in 1997. It was soon modified, ported and improved, reaching our days as a champion program, not only to solve “problems” such as the deactivation of the ping that I mentioned, but also to explore complete networks in port ranges, showing all the TCP/IP option specifications.
For example, Pandora FMS uses Nmap to check the communication and services by command line in the Console Configuration. Nmap also has a graphical interface called nmapfe. There are a number of programs that also use Nmap.
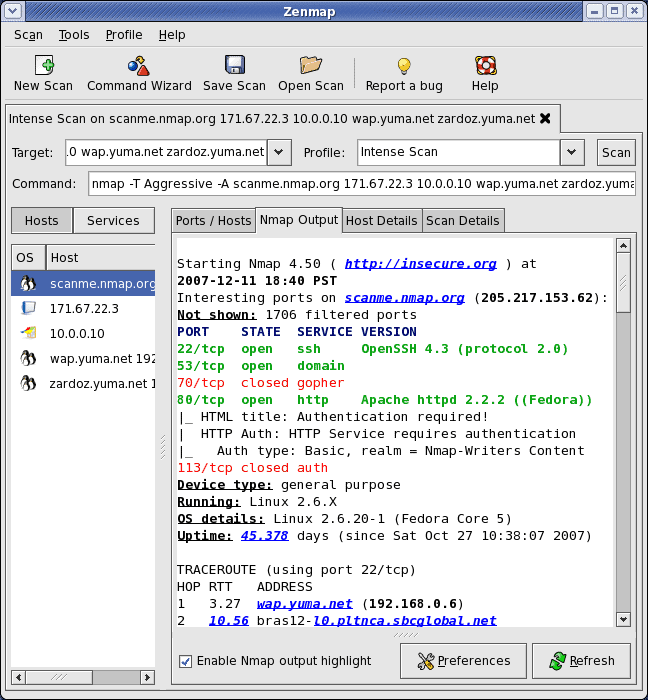
“Zenmap utilizando Nmap 4.5
https://commons.wikimedia.org/wiki/File:Zenmap_2.png
Ping, Nmap, Curl and many other network tools were confirmed by Pandora FMS team as essential. In this article, we offer a brief summary of each of them, if you want to explore a little more – in a technical way – port monitoring.
Remote Monitoring
As its name says, we will carry out checks externally with a Pandora FMS component called Network Server. Although it has been entrusted with many jobs and tasks, port monitoring is within TCP Monitoring, one of its three basic task blocks.
If you want to see how to create a TCP module in Pandora FMS you can take a look at this video:
The first task is to determine whether a port on a remote host is open, and based on that issue orders and/or alerts. Remember that I told you about ping, and for that there is ICMP Monitoring (although it is not relevant, I will give you a teaser: the third block is what includes SNMP Monitoring in Pandora FMS Network Server).
And as they say in advertisements “wait, there’s more!”: to make totally sure whether the port is open or not, Pandora FMS also allows receiving a specific response through the requested port («OK», «200» or some other standard response of some common application). It can even send something several times and receive several responses until you can find the condition or status that you want to monitor.
Always remember security: due to the nature of these protocols, these communications are not encrypted.
Enterprise version: “Satellite Server”
Pandora FMS Enterprise version is used by many industry leaders. For example the Municipal Transport Company of Madrid (EMT), the Ministry of Telecommunications and the Information Society of the Republic of Ecuador and the Governo Povo do Acre, state of Brazil with 22 towns and 700 thousand inhabitants.
As I already told you, remote monitoring is executed by Pandora FMS Network Server, which has specific features. TheSatellite Server, in turn, makes use of Perl language and needs (in addition to fping and Nmap, installed separately) a wmic and braa (included when downloading the binary file) to be able to match Pandora FMS Network Server features.
Bearing all this in mind, and without delving too much, you will be able to monitor ports in networks that, for security reasons and/or technological divides, you cannot directly access through your Pandora FMS Server (the devices you will perform port monitoring on).
Yes, you may be wondering how the Satellite Server is able to save the collected metrics in the database: said server must have access to the Internet and from there to Pandora FMS Server through its own protocol called Tentacle.
Port number 41121 is used for this purpose (officially assigned by IANA) and this is the only port number that, in my opinion, is not worth monitoring: you will find out very quickly through Pandora FMS Console if you have stopped receiving connections from your Satellite Servers.
What motivates the devices to be monitored to be “isolated” or not within reach of Pandora FMS Network Server? Let’s take a look.
Firewalls and intrusion detectors
Firewall, network of networks (Seth Kenlon, CC BY-SA 4.0)
Finally I slightly mention the much dreaded topic of firewalls. Just as they protect us, they also make life miserable when properly configured. What do I mean?
A firewall (based on software or hardware) can have infinite configurations, but the model I like the most is the one that blocks everything that comes in from the Internet except for what is expressly allowed. And that is where our great work begins, adding what we need such as the famous ports 80 and 443 for web traffic, the most common for web servers (but you always have to take into account the different types of servers there are).
But it goes further, the firewall must also make sure that the incoming packets correspond to an output from our local network. Basically what we requested (remember Pandora FMS Satellite Server?). What a job!
Seen that way, the firewall tasks are demanding and because of that artifacts have been designed and created specifically for that. They are hardware-based and Pandora FMS has several plugins to monitor them, generally by SNMP.
I also add that a firewall must have a list of allowed IP addresses to be redirected to specific servers, as it is our case if we do port monitoring (from outside the company). If the request is received from any other IP address to a port outside the allowed list, we will send it to our “honey pot” server, suitable technology in the case of unknown and unwanted visitors. To keep the list of allowed IP addresses updated you must have a third Internet server that proves your identity to the firewall.
Now, the latter is focused on TCP requests, which are connection oriented (we go back to theory) but UDP requests don’t work that way. This is where you may find forged IP addresses that make you become victim of another web server apart from yours. Fortunately, the Linux kernel delays those queries on purpose to a limit of one thousand per second, so attacking more than 60,000 ports is going to take them some time. That leads us to the next point: intrusion detectors.
Although this technology has been around for a long time, I haven’t seen many use it. It isn’t like you can’t integrate it into your honey pots, but I would recommend for them to work separately; if it’s a hardware-based solution, all the better. The point here is to keep track of the packets that go around the local area network: there Pandora FMS can passively perform port monitoring.
- You may also use the technique of maritime vessels: watertight compartments (but don’t fully trust it, remember what happened to Titanic, it never reached New York, despite having this new technology at the time). That is, after the main firewall, create isolated subnets with additional firewalls, repeating the previous recommendations.
- Each work server to be monitored must also have its local firewall, run by the operating system (and at the risk of being annoying “repeating the previous recommendations”). What does this have to do with port monitoring? If you already have a machine in inventory that has a MySQL database (usually port 3306) and you check it is open and operational, you additionally check that there is no other port open. Such are the monitoring tasks, extremely redundant. These local firewalls have an additional feature: allowing only specific programs to open and use their ports by default (see also log monitoring to be aware of the changes).
- Some network administrators use obfuscation techniques, such as changing the predefined ports (I have seen web servers using port 28081 in pop-up windows, which although at this date is not assigned to anyone by IANA, they should use ports above 49152, custom dynamic ports). This only reinforces my claim: monitoring is a science… and an art.
- In the case of virtual machine orchestrators (Docker with Kubernetes is the most popular) virtual monitoring will be in charge of port monitoring, since it will be more effective to use the API instructions, this without prejudice to everything explained!
Before finishing, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Would you like to find out more about what Pandora FMS can offer you? Find out clicking here.
If you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL . Get it here .
Last but not least, remember that if you have a reduced number of devices to monitor, you can use the Pandora FMS OpenSource version. Learn more here here .

Programmer since 1993 at KS7000.net.ve (since 2014 free software solutions for commercial pharmacies in Venezuela). He writes regularly for Pandora FMS and offers advice on the forum . He is also an enthusiastic contributor to Wikipedia and Wikidata. He crushes iron in gyms and when he can, he also exercises cycling. Science fiction fan. Programmer since 1993 in KS7000.net.ve (since 2014 free software solutions for commercial pharmacies in Venezuela). He writes regularly for Pandora FMS and offers advice in the forum. Also an enthusiastic contributor to Wikipedia and Wikidata. He crusher of irons in gyms and when he can he exercises in cycling as well. Science fiction fan.


















