Security monitoring as prevention and tool in computer security
Security Information Monitoring or Security Event Monitoring is part of Security Information Management. Yes, I acknowledge they are flashy names and that even experts have their differences about concept and scope. Here in Pandora FMS, flexibility is part of our name, so, hereby, I will abbreviate it as Security Monitoring. As you can see, it is short and manageable!
If this is your first time reading Pandora FMS blog, we are glad to inform you that in our programming plan for 2020–2021 we have included security monitoring as another element of our IT supervision software.
In monitoring systems, the use of alerts for when an event takes place, whether authorized or not, is inherent in the network system. Said alerts are easily defined with Pandora FMS to detect changes or behaviors, even suspicious ones, for their collection as data and, after being analyzed, turn them into information.
This set of alerts also includes those that are more used and interesting: free disk space, workload, etc. They are predictable and quantifiable parameters, but how can we apply it to the issue at hand, security? With the help of a very specialized software, such as Lynis, you may also obtain a quantitative analysis, with whose result you can set a security qualitative state in your system.
Metric use
Any system can be degraded if it is not properly improved over time. To know if an improvement has been made, it must be measured, quantified and compared. But in order to measure anything, it must be defined. If defined, it can be measured and monitored. That includes security.
Directly, Pandora FMS intervenes in the following key aspects, to name a few and to precise our work:
- Keeping track of service level agreements (SLA): it is very important to check the expiration date on a regular basis. That way, you ensure you won’t have no support if there is a failure or no access due to a lack of license to any of the business-critical applications.
- Device inventory monitoring.
- Pandora FMS supports third party authentication through LDAP or Active Directory (except for users with admin permissions, who always authenticate locally), so user and password management can be handled massively. You can even monitor a server with the OpenLDAP Plugin.
- Managing any other type of issue, including a security one can be managed through Integria IMS, a Pandora FMS suite software.
- Supporting backup management, even for different applications, to somehow protect from ransomware attacks.
- You may check antivirus programs work through software agents in an automated way, and also interactively through eHorus, another Pandora FMS suite product.
Previously we mentioned Lynis to check for updates and security patches on GNU/Linux systems, but also through Windows Management Instrumentation (WMI)® you will have a clear and exact overview of the coverage status of the possible vulnerabilities in the software installed on Microsoft Windows®.
Let’s say, for example, that you need to monitor backup executions on a weekly basis: it is important to know what success percentage you have. So you choose the metrics on the time dimension against the number of times correctly performed (that is, the pseudocode would be: number of times correctly performed divided into the number of performed backups within a week). An indicator like this gives an exact image value of your security monitoring.
What security monitoring is not
Often a great way to define a concept is by means of its “opposite”. That is why I take this chance to set what an Information Security Management System (ISMS) is. It is an extremely standardized field, whose main rule is ISO/IEC 27001, internationally, and then in each country according to its own laws.
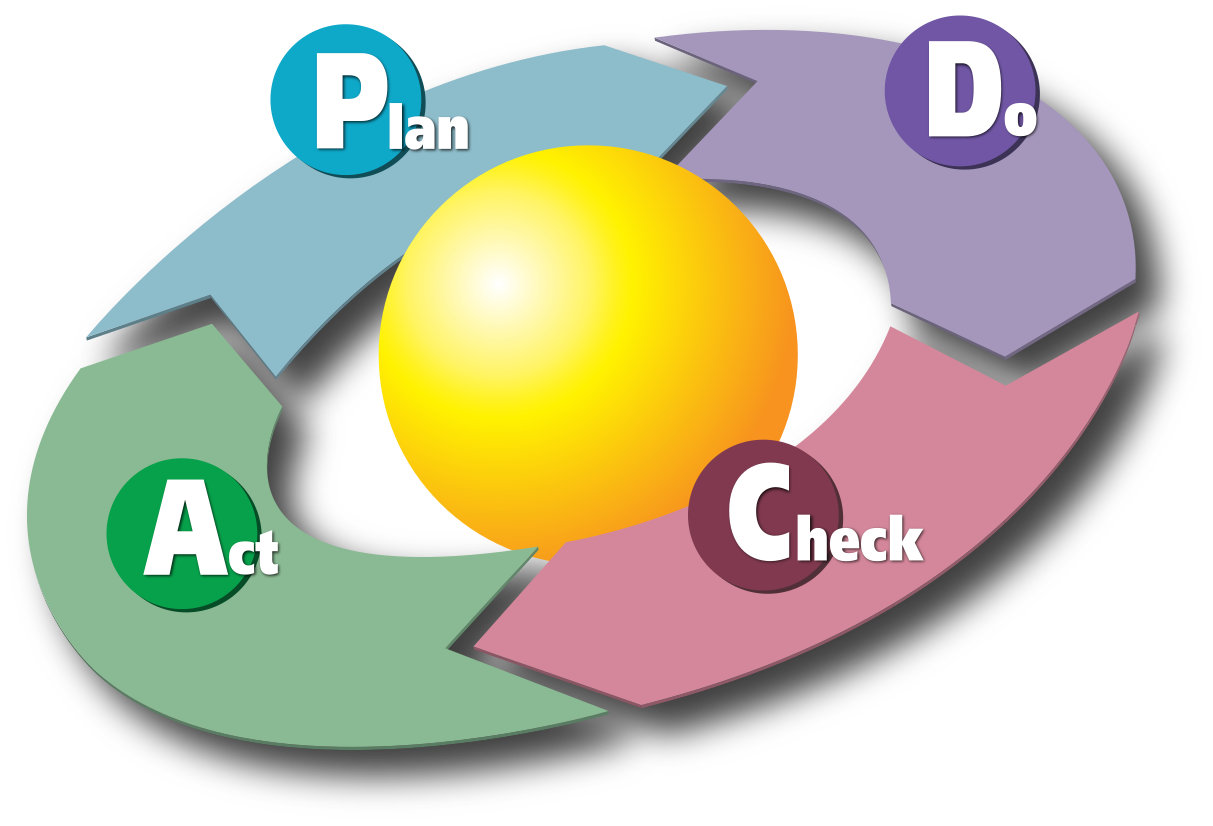
Caption: “Deming Cycle” or PDCA: “Plan-Do-Check-Act” used in ISO/IEC 27001
Image: https://commons.wikimedia.org/wiki/File:PDCA_Cycle.svg
In security monitoring, prevention is the biggest advice, by unifying events and collected metrics. For example, to cite a critical and vital case for many companies such as electronic payment: there is the Data Security Standard for the Payment Card Industry (PCI DSS) that sets measures such as sending duly encrypted information on clients, on a mandatory basis, and the use of firewalls to prevent intruders from accessing the data you have stored about your clients. A well implemented Information Security Management System (ISMS) includes security audits, either regularly or unexpectedly (or both even), and must ensure that these two resources (and others, in addition) are working and are being used correctly.
Caption: Common firewall configuration, an important element in Security Monitoring
Image: https://commons.wikimedia.org/wiki/File:Firewall.png
On the other hand, in Security Monitoring you can offer reports about whether the security certificates for information encryption are in force and operational, so that they can be renewed in advance in order to keep communications encrypted at all times. Likewise, you will be able to monitor the company firewalls, where, how and when they are working, and restart them through alerts if necessary. These are just two examples that provide reporting tools on strong bases, but they are not and are do not replace an ISMS!
Thus, at this point, an ISMS covers many aspects and in each of those aspects, security monitoring (
- Patches and updates
and their automated management.
- Antivirus status
, as well as the network status regarding spam filtering.
- Staff training regarding fraud and its prevention ☒.
- Network and computing resource usage
.
- Mobile devices on your network and its security ☒. (Although, at least, you can report connection times, megabytes consumed, etc., the basics).
- Services and their accesses through user permissions
.
- Data leak ☒. Delicate task, mostly based on staff surveillance (although you will be able to monitor the application records in the company and generate reports that look for specific fields and values in them).
- It is important to fully comply with the legislation in each country ☒.
- Depending on the size of the company, evaluating whether it is possible to implement Unified Threat Management, which despite its disadvantage of being a single point of failure is relatively easier to manage and security monitoring can benefit from it
.
ISMS Tools
I do not intend to name them all, and I explain it oriented towards security monitoring:
- Network audit: looking for router models, which ones connect the company or cataloging information. In its analysis, models are correlated against firmware installed versions, exposed ports, etc.
- Perimeter Security: it sets or determines the different layers or steps, from the point of view of outside the company, to “get” to the network audit components.
- Penetration test: the so-called red team, personnel totally foreign to the company and coordinated to attack and try to enter without knowing the previous audit information.
- Web audit: both internal to the web server within the company, and its encrypted synchronization to the web server hosted by third parties on the Internet. It also includes legal aspects.
- Forensic Audit: to perform an exhaustive analysis of post-mortem incidents. In case evidence is needed, part of them can be provided by Security Monitoring.
Before finishing this article about security monitoring, remember Pandora FMS is a flexible monitoring software, capable of monitoring devices, infrastructures, applications, services and business processes.
Want to know more about what Pandora FMS has to offer you? Find out by entering here.
Or if you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Get it here.
And remember that if you have a small number of devices to monitor you can use the OpenSource version of Pandora FMS. Find out more here.
Don’t hesitate to submit your inquiries. The Pandora FMS team will be happy to serve you!
Read our related success story and see the results we’ve got

Traductora a francés e inglés. Me encantan las lenguas. Amante de la ropa oversize, la tarta de queso y el chocolate caliente en invierno. Me gusta leer, escuchar música, viajar y explorar cosas nuevas. Mi frase más temida por aquellos que me conocen es “he estado pensando…”
Translator into French and English. I love languages. Lover of oversized clothes, cheesecake and hot chocolate in winter. I like reading, listening to music, travelling and exploring new things. My most feared phrase by those who know me is “I’ve been thinking…”



















