Around March we already had a warning in the form of a newsbreak that someone was infecting devices managed with TeamViewer with ransomware. Now June has just started and we get news of another, more disturbing, incident that is also affecting TeamViewer. The TeamViewer team, following the European tradition of denying everything, blames its users justifying themselves by saying that if users use weak passwords, it’s perfectly normal that they get ripped apart by hackers. The worst part about this is that there already too many users on Reddit denying this excuse and that assure they’re using 22 character, single-use passwords, double authentication and yet still have a stranger moving their PC’s mouse right in front of their puzzled faces. We’re here today to detail what’s happening, why, and some safer alternatives to this remote control solution.
What’s going on?
Whether it’s true or not, security-wise the most dangerous thing is to lose confidence in a product. I imagine that if it’s your responsibility to manage various devices remotely with TeamViewer, you expect the software manufacturer for the most expensive remote access product on the market to be just a tad bit more professional. You’ve probably reached the point when you’re thinking “I need a TeamViewer alternative”.
How does modern remote access work?
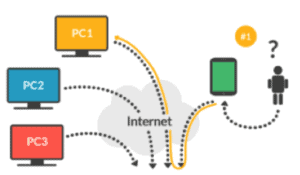
People that don’t know much about this subject can think that it’s useless to pay having Windows remote desktop, VNC on Linux, or the MacOS remote desktop. These systems are ok, but they won’t work if you need to access a customer’s server located in his or her network while you’re on a whole other network, and the way to reach that customer is via internet. You’ll need to be connected through a VPN, create a NAT, or something like that. In any case, it’s a complex process and it’s not always possible. That’s why online centralized systems were created, such as TeamViewer and its many alternatives.
The concept is simple enough: you’d install a small program on the device we need to manage, and this device connects to the internet server. This system acts as a “middleman” between the device we wish to manage and our current location. This way we can manage our devices remotely without the need for these to have incoming internet connections. This model is replicated on all systems that work even remotely similar to TeamViewer.
The issue with the so famous “cloud” is that, in the end, its security is in the hands of those who manage those “middleman” servers, and that the software you install is the front door to the outside. We need to perform an “act of faith” and trust that we’re not getting played. If we don’t want to take this leap of faith for a third party, the only alternative is to trust those third parties and the information that isn’t shared on the cloud: a double factor authentication system and a local password. This way, in the first case it’s Google –for example– who provides authentication, in the second case it’s a password which, in theory, the central server doesn’t know and therefore no one can steal.
TeamViewer is supposed to be using those two security elements. The issue is that hundreds of users are claiming to use these two methods and are still getting their devices broken into.
All of this leads to the supposition that TeamViewer has some way to “skip” the user protection protocols. This is not only something bad, it’s extremely horrible, and at this point you should be looking for alternatives.
Alternatives to Teamviewer
While it’s true that TeamViewer is one of the best remote access software products: it’s comfortable, quick, efficient and has multiplatform support. It’s also the most expensive product. Let’s discuss some similar software to TeamViewer.
GotoMyPC is an excellent alternative, even though it doesn’t have double factor authentication, it’s quite unexpensive: around 130€/year per managed device.
LogmeIn is another classic. For a starting price of 75€/year per device, it has an amazing amount of features, including double factor authentication. Of course, the double factor system is managed by them as well, it’s not Google’s. Sorry guys, but at a security level, I trust Google more.
Ehorus is one of those underground products (right now), yet offers some very interesting features for system administration like a remote shell or an integrated task manager. It includes double factor authentication and they use the one managed by Google. Best of all, as of now it’s free.
Splashtop is also a little known solution, but it’s quite similar to the aforementioned alternatives. The “Anywhere Access” version which allows connections from anywhere via their central servers and costs the small price tag of 17€/year per device, which makes it very appealing. The downside is that they lack double factor authentication yet, but they promise to have it included soon.
Why not have it all?
This is no new idea, as a matter of fact there are already different software solutions on the market that do this, but they’re either good in one thing (i.e. monitoring) or good at another (remote access and control) and they always, always have a SaaS model (which implies cloud computing). We’re referring to the group of applications known as RMM (Remote Monitoring an Management). Tools like LogMeIn Central, LabTech, N-Able, Kaseya, Naverisk or Atera.
These tools, although they have remote access, it’s usually a bit lacking, and a lot of them need to install a small client to be able to remotely access managed devices, apart from the control agent. Their license model is usually very flexible and has low costs -much, much more than TeamViewer- usually rounding out at 25-30€/year per device, although they’re thought out to be used in corporate environments and have a minimum input volume of 5-10 devices.
If it’s already a scary concept to be able to externally access our devices since everything is cloud-based, having monitoring and device management available on the cloud should scare us even more. This way the solution we’ve though out from Pandora FMS is to have a mixed solution, On-Premise for monitoring and SaaS for management. This is why we’ve integrated with eHorus so you can manage your devices from Pandora.
We’ve chosen this integration because eHorus is the only current SaaS provider that has public APIs and that is also free. And, why not mention it, because they’re the only ones who have proven interest in integrating themselves with an Open Source tool, therefore this integration is 100% Open Source and free. From the next release, Pandora FMS 6.0 SP3, you’ll be able to enjoy the integration of eHorus with Pandora FMS to have monitoring and remote device management (on Mac OS, Linux or Windows) all from the same WEB console, Pandora FMS’ console.
Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring. Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.