In this article we are going to show you different network commands for Windows and Linux, a must for all network administrators.
These network commands can be used separately or they can be combined with software such as Pandora FMS to monitor in real time, or they may even work as part of a long-term strategy.
This, together with the post by network tools, will help you better manage your networks and your time.
- VNStat
- Ping (Unix/Windows)
- Traceroute (Unix/Windows)
- Arp (Unix/Windows)
- Curl and wget (Unix/ Windows)
- Netstat (Unix/Windows)
- Whois (Unix/ Windows)
- SSH (Unix/Linux/Windows)
- TCPDump (Unix/Linux/Windows)
- Ngrep (Unix/Linux/Windows)
- NMAP (Unix/Windows)
- Netcat (Windows/Unix)
- Lsof (Unix/Windows)
- IPtraf (Linux)
VNStat
It is one of the most complete network commands. It works on all Linux and BSD systems, and allows you to monitor network traffic from the console.
- Installation is very simple and quite fast, allowing monitoring all network interfaces.
- With VNStat you may collect all traffic you need from any configured interface.
- One of the big differences between VNStat and other tools, is that VNStat collects kernel data instead of the interface itself, achieving lighter execution for the system.
- It won’t need administrator permissions to be executed.
- It has the ability to store the information collected so it does not get lost, even with system crashes or system reboots.
- It is possible to configure Vnstat to listen to traffic on a daily basis, by billing time, or many more options.
- Its flexibility is outstanding when setting up traffic reading.
- Finally we’d like to highlight that it is possible to configure Vnstat’s output to generate graphs by console and even customize them with colors.
Ping (Unix/Windows)
Ping dates back to the 1970s and is known to be one of the most basic network commands. However, it is not as simple as we may believe and has many more uses than those we already know. It is based on the ICMP protocol and is used to determine:
- Whether there is connectivity between your machine and another machine in the network.
- It is used to measure the “speed” or latency time.
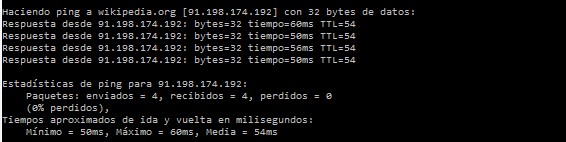
It is a command that exists on all operating systems that support TCP/IP, and it is a basic one that you should know.
Ping stands out for having dozens of parameters and the one that is most useful to us is that one responsible for monitoring “the number of packets to be sent”. There are networks that undo the first packet, so it is essential to send at least three so that you may check that any of them arrived without being discarded. For that you may use the –c parameter.
That same technique can be used to find out the packet loss percentage in your network by sending ten packets and checking whether any of them gets lost. Surely you are surprised by the amount of packets that are often lost. (This tool comes integrated by default in Pandora FMS)
Execution: ping computer name/ip
Traceroute (Unix/Windows)
The main objective of this tool is to find the path a packet travels throughout your network. This network command will allow you to find out where the packet goes through (machines, switches, routers) and check that your network is working properly. If it detects any problems, it will allow you to have a rough idea about where the fault is located.
Pandora FMS uses it in its network mapping tool (Recon Server) and thanks to this, together with other advanced tools, it is possible to “draw” a network hierarchy.
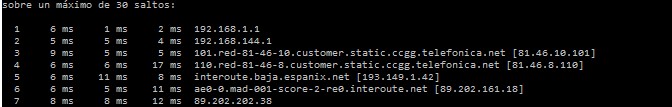
Execution:
traceroute –n (on Unix / Linux)
tracert –d (on Windows)
Arp (Unix/Windows)
This network command is used to modify and see the ARP table, which collects mappings between the IP address and MAC address. It only sees connections in your local area network (LAN) segment, so it could be called “low-level.” However, it is useful to find out which machines have been connected directly with your host or which machines you connected to. It is a diagnostic tool, and sometimes it can be interesting to monitor it by ruling out ARP Poisoning attacks that are one of the most common forms of spoofing attacks on local networks.
With Pandora FMS, a common integration is to verify, on some hosts, that the IP and MAC correspondence is always the same. If it suddenly changes, it is because some network host is impersonating another.
Execution: arp -a
No matter what operating system your machines use, you can monitor them ALL using this:
And using it for free for any number of devices you want to monitor.
Curl and wget (Unix/ Windows)
These are essential commands for making HTTP, HTTPS, or FTP requests to remote servers. They allow you to download files or download entire web pages, even recursively (which allows to make a literal “copy” of a website, including images). They support cookies and allow POST requests to be sent, in addition to being able to “simulate” a user agent, use an HTTP proxy or even a SOCKS4/5 proxy.
One of the most common utilities in integration with Pandora FMS, is to verify the content of a specific WEB page. Since wget/curl allows you to download the full content of a website, it is easy to compare the MD5 of that content with a previously verified value. If it changes, the WEB was in fact altered.
Netstat (Unix/Windows)
Network command that identifies all TCP and UDP connections opened on a machine. In addition to this, it allows you to find out the following information:
- Path charts to learn about your network interfaces and their outputs.
- Ethernet statistics that show the packets sent, those received and possible errors.
- Know the ID of the process being used by the connection.
Netstat is another basic command like Ping that fulfills many elementary functions. Some of the elements that Pandora FMS agents use to obtain system information are traffic statistics, the number of open connections and, most importantly, the number of connections pending closure or in the process of being established. Unusual growth in these metrics can be a serious problem and may be due to a server performance issue or even an external attack.
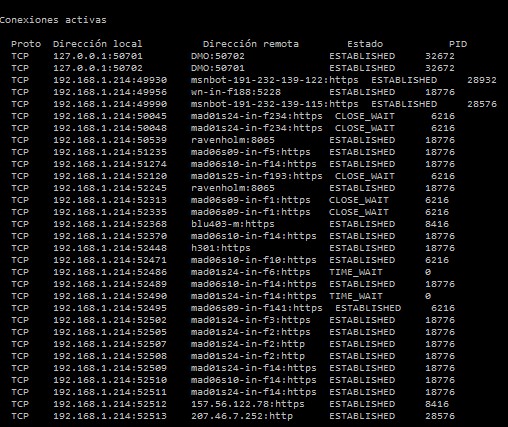
Whois (Unix/ Windows)
This network command is used to query data on domains, such as to find out who owns the domain, when the domain expires, to see configured records, contact details, etc. Its use is highly recommended to contact domain administrators or in case of incidents of mail and web service migrations.
To use ‘whois’ in Windows, it is necessary to download the software from this url:
https://technet.microsoft.com/en-us/sysinternals/whois.aspx
You may also check it out through their website.
SSH (Unix/Linux/Windows)
Command to run terminals on remote machines safely. SSH allows any user to run a console by simply registering and entering their credentials. So you may run the commands you want as if it were local.
More details you need to know about SSH:
- To use SSH on Windows we recommend Putty. You may find it at http://www.putty.org/
- To allow a remote computer to connect to your server through SSH, an SSH server must be installed and configured as FreeSSHd.
- SSH allows, in addition to obtaining an interactive remote shell, to execute remote commands and copy files in both directions.
- It should not be forgotten that SSH is the natural replacement for classic tools such as Telnet or FTP, and that it has become the basic system management tool over the years. It is extremely powerful and despite its complex combinations of symmetric encryption and authentication and verification schemes, it is the target of continuous attacks.
Pandora FMS uses SSH in different ways, and offers the possibility to execute remote commands. For security, we need the user to establish a certificate-based authentication scheme, which allows remote execution connections to be made from a machine without requiring a password. It’s easy, but a little complex to implement. Therefore, in the Enterprise version, our Satellite Server allows you to make multiple remote executions to different hosts easily and in a much more optimized way. This allows you to do hundreds of check-ups per second.
If you want you may have a look at the following video, in which we tell you more about network monitoring in Pandora FMS:
TCPDump (Unix/Linux/Windows)
It is another network-command “basic” tool, which if used correctly becomes a great ally for network administrators, system administrators or programmers.
TCPDump is an advanced command used to inspect the traffic from different machine interfaces in order to obtain the exchanged packets. You may dump the output to a file and then analyze it with other more powerful sniffers and with graphical interfaces such as Wireshark. For Windows, use WinDump.
Ngrep (Unix/Linux/Windows)
- The power of the grep command is taken to the network.
- It is a TCPDump with a real-time text substring filter.
- It has a very powerful regular expression filtering system and is usually used to process files generated by tcpdump, wireshark, etc.
- It is a filter of communication packages on http, SMTP, FTP, DNS and other protocols.
NMAP (Unix/Windows)
NMAP is considered the father of general network scanners. Although today there are more reliable tools for some tasks (eg: Fping), NMAP is still a very versatile tool for scanning networks. It is used to determine which hosts are alive on a network and to perform scans in different ways.
Netcat (Windows/Unix)
NetCat, or NC, is the most versatile network command available and one of the lightest. However, its use requires some imagination. Only if you have dealt with scripting will you understand the subtlety of its name: NetCat. It is a tool designed to be used as the destination of a redirection (a pipe or |). It sends or receives information about a connection. For example, a WEB request to a service would be something as simple as:
echo -e “GET http://pandorafms.com HTTP/1.0\n\n” | nc pandorafms.com 80
Lsof (Unix/Windows)
The ‘lsof‘ command is not only used as a network tool, it also identifies which files have a process open. In UNIX environments, a file can be a network connection, so it is useful to know which ports are open to a specific process in execution, something extremely helpful in some cases.
It can also be used to find out how many files a process has open. It has nothing to do with the network, but I’m sure it can be useful.
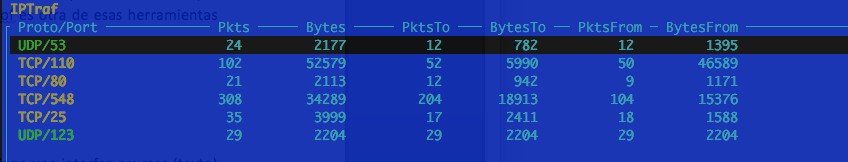
IPtraf (Linux)
Specialized command to get traffic statistics. It has an ncurses (text) interface for real-time analysis of traffic going through an interface. It allows you to work at a low level and see what connection pairs are established on each machine, seeing in detail the traffic per connection pair, all this in real time. Very useful if you detect something unusual on your machine and do not know what traffic is going through it.
We hope you found this network command list interesting. Do you miss any network commands? Please let us know so we can include it in this list.
If you still don’t know Pandora FMS, the IT monitoring software, then what are you waiting for? Visit our website! But if you are already familiar with our tool, you will know that it stands out for its flexibility, so it won’t come as a surprise that it allows you to customize and create monitoring plugins. With the commands that we saw today you may create plugins that will make your work much easier, adapting the tool to your needs. Remember that if you wish, you can access a Pandora FMS Enterprise FREE 30-day DEMO.
Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring. Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.


















