DNS Monitoring: Reasons and elements to be included
When we think of DNS (Domain Name System), there are two thoughts that we all assume to be true and that become natural justifications for the development of a DNS Monitoring scheme:
- If the DNS system we use to navigate fails, our users will not be able to connect to the desired websites.
- If the DNS system that must supply information about our WEB services fails, our clients will not be able to access these services.
Simple and forceful, in fact since the rise of the Internet, DNS systems are a fundamental part of our communications.
Now, in a simplistic way we can say that a DNS system allows this:
- Our end users can connect to any web server by knowing only the name, without having to have the IP address.
- Our customers, located anywhere on the planet, can access our web services without having to have the IP address of our server. They just need the name.
- We can send emails by knowing only the addresses of the type nombre@dominio.ext
For this, the DNS systems start from a database, distributed and hierarchical, which allows this:
- To correlate any domain name (pandorafms.com) with a valid and approved IP address (104.24.102.7).
- To correlate with a given domain name, the IP addresses of the associated mail servers.
A fundamental point in the functioning of the DNS systems is the response time, since it is required that the users can establish their communications in a simple way, and of course fast.
Therefore, DNS systems implement a name resolution scheme that aims to introduce latencies as small as possible, since a failure in the performance of the DNS system will have a direct impact on the browsing performance of users and the performance of applications used by our customers.
Therefore, ensuring optimal performance in the operation of the DNS system is another justification for the development of a DNS Monitoring scheme.
On the other hand, DNS systems play a very important role in terms of security, as their records document all connections made to a particular domain, information that can be used for vulnerability analysis and forensic analysis.
Before continuing you can take a look at this video, in which we explain in a simple way how to check a DNS record in Pandora FMS:
In addition, today we must face the fact that there are many attacks that use the presence of DNS systems to enter organizations, divert traffic and steal information.
So, security is another element that justifies the efforts we can make in DNS monitoring.
Do you want to discover the most flexible monitoring software on the market?
Pandora FMS Enterprise is capable of monitoring devices, servers, applications, services or business processes. What are you waiting for to get to know it better?
Before reviewing what should be covered by a DNS monitoring system, we invite you to review those fundamental concepts that will be relevant at the time of defining such a monitoring system:
DNS Process
We use DNS systems almost transparently; in fact, after the configuration of network addresses that is often supplied by DHCP services, we get our users’ applications, such as Browsers, mail clients, etc., to use DNS services.
However, when one of these applications needs to resolve a domain name, it makes a search request to its operating system. This request is attempted by searching for the correct cache reference.
If the reference is not found, the search request is passed to a DNS server.
At this point, the process will depend on how the network and DNS service are configured; network administrators usually configure their own internal DNS servers, which are intended to resolve the most common search requests.
If the internal DNS servers fail to resolve the requests, they are moved to the external DNS servers. These servers can usually be:
- Free DNS Services
- Services provided by the Internet provider.
- Contracted DNS services that provide greater speed and better levels of security.
Here the search process becomes a recursive process of queries to a group of servers, which depend directly on a hierarchy that governs the creation of domain names.
Let’s review this process from the different types of DNS servers involved.
Types of DNS servers
There are two types of DNS servers:
- Recursive Servers
- Authorized Servers
Recursive Servers
When receiving a search request the first thing a recursive server will do is to validate whether or not it has the requested information in cache. If you don’t have it, it will start a search process that will take you, as we said, through the DNS hierarchy.
The DNS hierarchy refers to the fact that every domain name implies a structure of servers responsible for each part or zone that makes up the name.
The search then involves resolution requests in which the requested information or the address of the next server to be consulted is accepted as a response, until the server with the necessary information arrives.
The following figure shows an example of the hierarchical DNS structure.
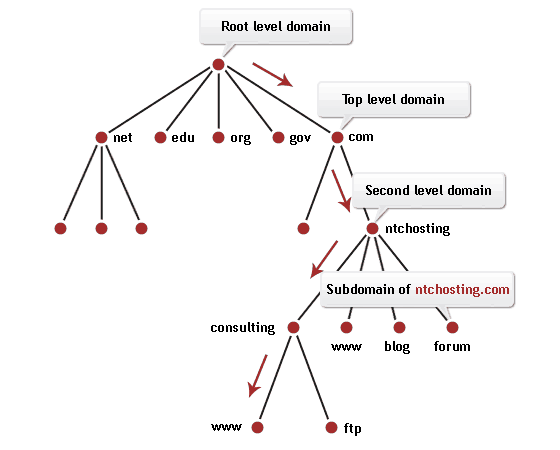
The DNS hierarchy starts from a Root Zone associated with the point with which every domain name ends and which is usually omitted (mydomain.com. ).
Then you have a top-level domain that competes with .com, .org, .es, .edu, etc. From there you have secondary level domains, or subdomain and host levels.
Each of these levels has servers with authority over the level in question; these are called Authorized or Authoritative servers.
Authorized Servers
Authorized servers are responsible for providing answers to recursive servers on search requests and framed at the level or zone in which they are inherent.
The path of the servers responsible for containing the records associated with the domain name is defined with the queries made by the recursive servers and the answers offered by the Authorized servers.
It is in these records where the domain name information is stored.
Types of DNS records
There are several types of records; here is a short list of them:
Host A or AAA records
These records associate a specific IP address with a domain name. There are A records for IPv4 addresses and AAA records for an IPv6 address.
example.com A 192.168.5.25
CNAME Records (Canonical Name)
This type of record is used to assign an alias to a true or canonical domain name.
It is used when we have several services in the same physical server or when we have a web service in a domain that is not our own.
ftp.example.com CNAME example.com
onlinesale.example.com CNAME anothercompany.com/example/sale.cgi
Bear in mind that a CNAME record can only point to an existing A or AAA record. It cannot point to another CNAME record, thus avoiding the possibility of infinite cycles.
If the IP address of a host changes, only the A or AAA record needs to be modified and the CNAME records can remain unchanged.
MX records (Mail Exchange)
This record type specifies how the name associated with an email should be resolved.
Associates the domain name (taken after the @ in the mail address) with one or more mail servers, specifying a priority level for each of them.
example.com MX(10) mail.example.com
About DNS Monitoring
Having reviewed the basic concepts about DNS we can define what a DNS monitoring system could be and what we can expect from it.
Basic check
The basic check may correspond to the verification of connectivity between our network and the configured recursive server (either a public server, or a server contracted to an Internet service provider or specifically DNS services).
In addition to connectivity, we can verify that our domain name is being resolved correctly.
This type of basic check is usually performed using the Network validation tools that our monitoring tool provides.
With this check-up we can get information like:
- The number of times the recursive DNS server is out of service.
- Failures in the resolution of our domain name.
- The response time registered to resolve a domain name.
Checking Outgoing Traffic Volume
We can monitor the volume of outbound traffic (internal users surfing the Internet) based on domain name resolution requests. It would also be interesting to maintain a table with the information about the most requested domains.
The idea can be to establish quotas that reflect the normal levels in the number of connections and schedule the issuance of alerts in the event that any measured volume exceeds the specific quota.
Checking of Records
The next level can be the validation and checking on the records associated with our WEB services. The idea is:
- To monitor changes that may occur in the records associated with our services.
- To keep an updated copy of the records associated with our WEBSITE.
- To generate a history of the changes made.
The main benefit of this type of monitoring is to achieve control over our DNS service and receive an alert when an unwanted change is made and to be able to apply correctives in order to keep our communication channel open and available.
There are many documented cases of DNS impersonation as part of a hacking process that can be resolved more quickly if we have this type of monitoring.
Security check
DNS is not an especially secure protocol, so it is the target of many attacks, in fact the Coleman Parkers DNS 2018 threat report goes so far as to mention that 77% of the universe of companies considered in the study are sensitive to attacks based on the DNS system.
However, the responsibility to prevent these attacks is not exclusive of monitoring tools, there is an important role for elements such as firewalls, intrusion detection systems, etc.
That being said, a monitoring scheme must include among other things:
- It must evaluate the security of domains that are accessed for the first time, considering their reputation and whether the domain is dynamic or not. Many attacks start by creating dynamic domains such as command and control centres, which are usually activated for a short time and then discarded. Techniques have been developed to achieve early detection of Botnets based on DNS traffic monitoring. If the reader is interested in these types of threats, we recommend checking this article in this blog.
- It must detect changes in the configuration of DNS servers in internal stations. Many attacks make changes to this configuration in order to transfer Internet traffic through malicious servers and have the opportunity to steal sensitive information.
As we can see, DNS monitoring efforts can bring interesting benefits. We hope that this first approach will motivate you to investigate your options in this interesting topic.
Of course, Pandora FMS has worked according to DNS monitoring, in fact there is a plugin specially developed for that purpose. You can request information about this facility by filling in this simple form.






















