WordPress plugin from Pandora FMS: How to expand its functionality
WordPress is present in 27% of all websites and has more than 27 thousand plugins. This Pandora FMS plugin for WordPress is a special one as it is focused on strengthening the security of systems that use this popular free software. Bear in mind that last year, in 2016, the UK Prime Minister resigned following a scandal about the exposure of emails stored on a mail server where a WordPress blog was also running and it had a plugin installed with a security flaw that allowed attackers to access information. WordPress is very secure, but some of its plugins and updates (even the ones from WordPress) can put our data in risky situations (we should all be entitled to some privacy).
What is «Pandora FMS WordPress plugin»?
We already know what it is used for, but now let’s have a look at what the Pandora FMS WordPress plugin actually is. Originally written as free software just over a year ago, it recently changed to “Apache 2.0” license, but in both cases, it guarantees access to the source code, its use and distribution, and even its modification so that you can adapt it to your needs. Therefore, the responsibility for its use rests on our shoulders, since the guarantee offered by «Ártica ST» is limited.
But, don’t panic! This company has a long history in monitoring servers and networks, these are essential tools in security management and this plugin is another great tool for this; Their flagship product «Pandora FMS» is able to monitor our WordPress site so that we can have a great work environment at an enterprise level. In case we have to manage multiple blogs the «Pandora FMS WordPress plugin» offers some monitoring options, although they are not as advanced as the «Pandora FMS» software, they always guarantee our goal of ensuring and protecting our web server that hosts WordPress.
The Pandora FMS WordPress plugin is mainly written in PHP and JavaScript language, in a GitHub repository and it contains a brief description of use, installation and uninstallation. It also offers screenshots from its site in “WordPress.org” (where we can safely download this “Pandora FMS WordPress plugin”) however we will publish here our own enlarged and detailed screenshots for didactic purposes.
Installation of «Pandora FMS WordPress plugin».
In order to use the Pandora FMS WordPress plugin, we must have at least WordPress 4.7 version installed and we must log in to our website with our proper administrator credentials.
Once we have accessed it, in Dashboard, we click on the icon of plugins and we choose “Add new” and we type the keyword “pandora” and we press: “search” so we’ll see something like this:

Here we should check that it has the checkmark: “Compatible with your version of WordPress” and if so, then we proceed to press the “Install now” button.
If you want to install it differently, then you must go to the repository, download and “upload” it by pressing the button “Upload plugin”: this option is intended for environments that have no Internet access (a private local area network, for example). In this case, we are going to do the first one, since we are trying with a production server and it is faster this way: by communicating directly with the WordPress website.
We must be patient when downloading the plugin from the WordPress.org website and once it is finished, the “Activate” button will be displayed. This process will take some time depending on your computer. Then, we will see something similar to this:
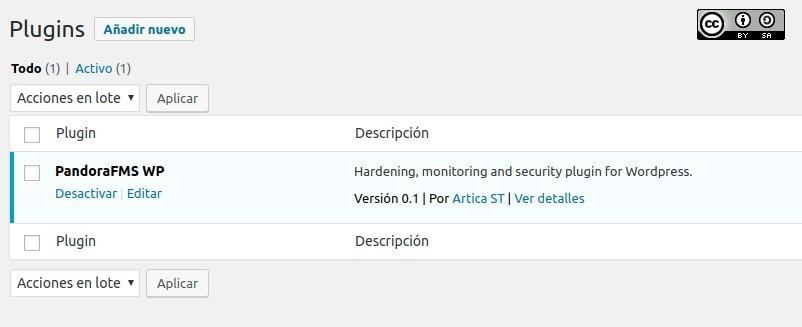
Now we must configure our custom values and needs in the next section.
Configuration of «Pandora FMS WordPress plugin».
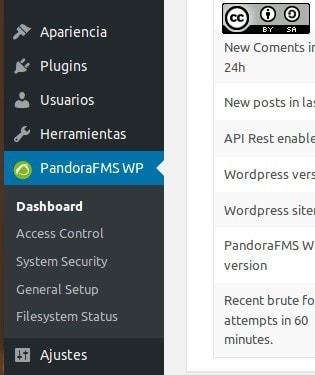
In this picture, we can see that the Pandora FMS WordPress plugin, has its own icon in the side menu of WordPress, and it stands out from the other plugins which makes it easier to administrate, due to these well-structured options:
- “Dashboard”.
- “Access Control”.
- “System Security”.
- “General Setup”.
- “Filesystem status”.
We will see each and every one of these sub-menus, not necessarily in this order; Let’s begin with the Dashboard.
“Dashboard”
We will use this section very often as it shows the general state of the system at a glance:
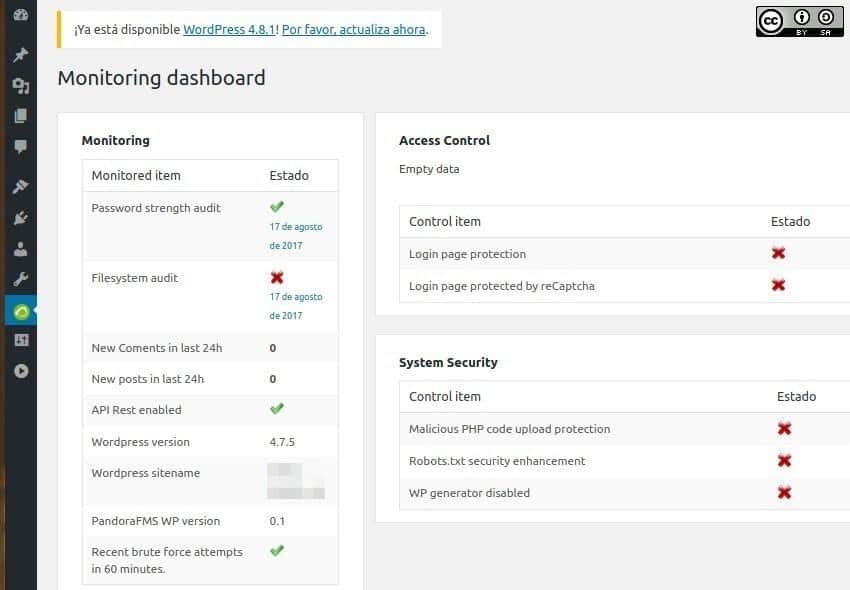
- Monitoring.
- Access Control.
- System Security.
– We will focus on the Monitoring section because the other two sections have their own administration. For now, Access Control and System Security are disabled, however in the Monitoring section, there will be some tasks already enabled and some others disabled.
– Password strength audit is enabled in this picture, which indicates that the password we have chosen is not in the list of the top 100 most common passwords. Make sure to use a strong password, at least 10 characters in uppercase, lowercase, digits, and special characters, to ensure that your password is not included in the giant dictionaries for brute-force attacks. Otherwise, we must change it using the WordPress tool designed for this purpose.
– Filesystem audit is disabled because it is a programmed task that runs every 24 hours and it is active by default, be patient when running it. We will get back into it in another section.
– New comments and/or posts in the last 24 hours; this can be very useful if you are the only person who writes the articles, because if you haven’t written it, then this would mean that our system has been compromised. Remember that WordPress includes an alternative for publications, this is a brand-new mailbox intended for that purpose: everything you send there will be published.
Pandora FMS WordPress plugin does not monitor this, but we will be aware of an unauthorized publication appears. On the other hand, if there are several authors then it might be harder to detect anomalies since other people would be using its site as well.
– API Rest Enabled: Do you know that the Pandora FMS WordPress plugin can extend your automated and centralized monitoring capabilities with the excellent «Pandora FMS» tool? Well if you want to acquire «Pandora FMS» and integrate it here then you will need special libraries to have a data connection. In this example, it is ready and enabled so we don’t have to do anything else.
– WordPress version and WordPress sitename: this is merely informative, here it shows that we have version 4.7.5 installed and it also shows that a new version is an available version 4.8, so we need to update it as soon as possible.
– Recent brute force attempts in 60 minutes is enabled and it means that we are safe at this time.
– PandoraFMS WP version
Pandora FMS WordPress Plugin in other languages.
Programmers are used to working in English, because of Alan Turing. He is the father of computer science; he is the pioneer of modern computing, so he set the rules for computing, in his mother tongue. But the world is huge, and lots of different languages are spoken, so in each software development project, there is a folder where the translations for each language are housed. This is called “internationalization” which is abbreviated as “i18n“.
Unfortunately, in the repository of “Pandora FMS WordPress plugin”, currently there are no translations but there is a file for this. Would you like to collaborate? In order to do so, create an account on GitHub, perform a fork, make your contribution (translation) and do a “pull request”, if the code is correct and the original authors accept it, which is not compulsory, then we will be able to enjoy this plugin in lots of different languages (at least the instructions and interface).
“Filesystem status”.
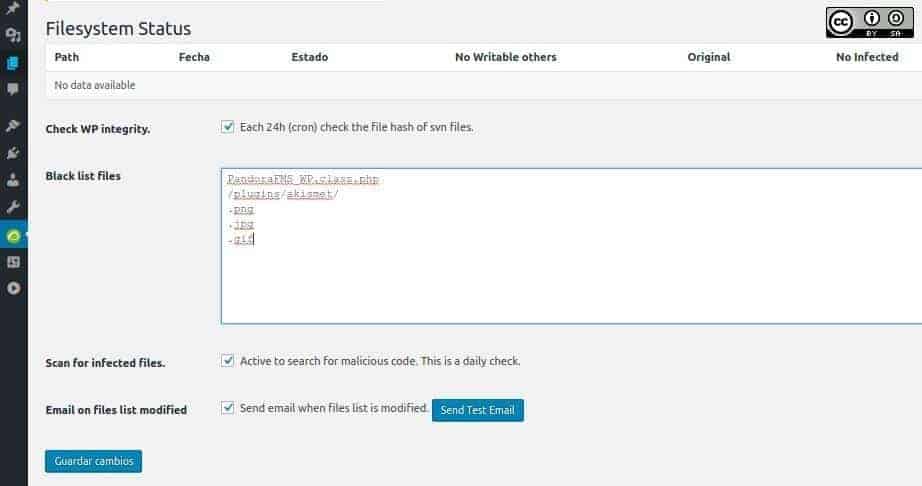
We mentioned earlier that every 24 hours, a verification is performed to verify the integrity of each and every one of the files through the procedure of version and revision control and the one created by the “Apache Software Foundation” is a very popular one. This foundation created the “Apache Subversion”, abbreviated as SVN, which assigns each file a “hash” by a mathematical algorithm and by a simple comparison, we will be able to know if a file has been modified.
This technique is widely used by the so-called: antivirus program, which performs the detection function. The Pandora FMS WordPress plugin also does this; if this event happened, then it would show a figure with a summary. It also shows a window where files are split up by type; in the following figure, we get to see the graphic files (with GIF, JPG and PNG extensions), that will not be monitored, as well as a subdirectory called askimet in the plugins folder. Askimet is a well-known anti-spam plugin.
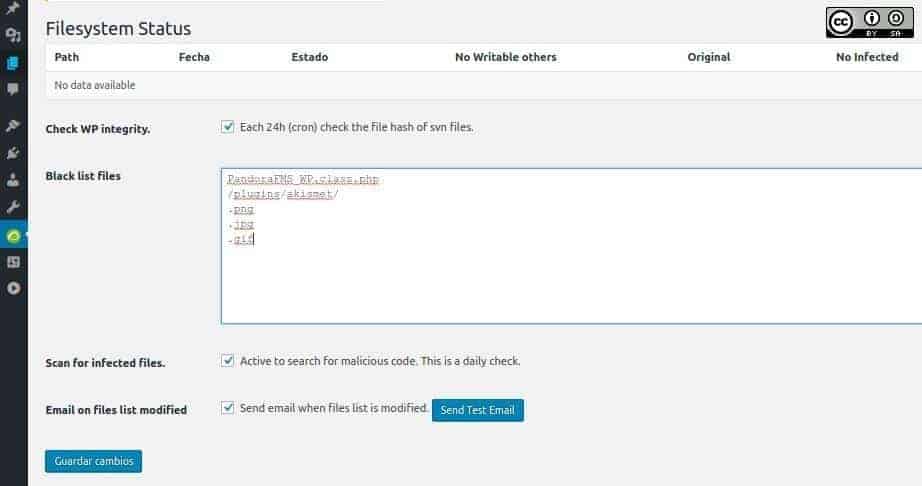
At this point, we might think that this is an installation failure, but we must keep in mind that the larger the number of files that are monitored, the slower your page will run, and we also need to consider if it will be shared by other websites! Each administrator should delete or add – the folders and/or files as well as the plugins that they need.
We advise you to keep in the list the first special file “PandoraFMS_WP.class.php”, since it is used to install and activate the plugin with these values.
We have to point out that once we have installed and activated this Pandora FMS WordPress plugin, we will never deactivate it or activate it again. The best thing to do is to delete it and install it again. Why? Since we do not monitor this file, which has the activation routine, there’s a chance that an attacker could change the default values thus harming the software, which protects us. These days, anything could happen!
“Scan for infected files” is a daily check-in search of two characters (written in hexadecimal) that are essential when a PHP file is infected, but it will require more complete software to determine the type of infection (but first the malicious code will have to be decoded). This option is enabled by default.
“Email on files list modified” is enabled by default. If an email is not assigned then «Pandora FMS WordPress plugin» will send it to the “admin” email. Why does it need a different email address? Well, for greater protection.
“General Setup” in «Pandora FMS WordPress Plugin».
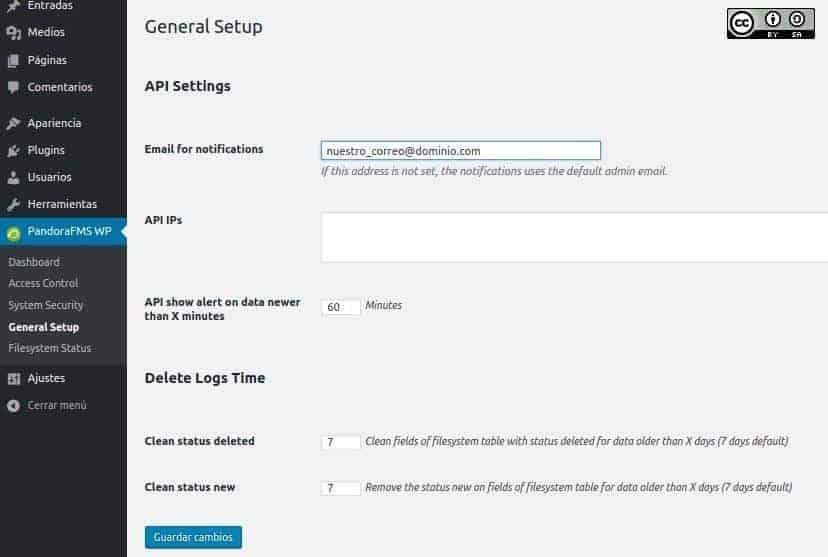
The email address should be introduced here by the person who is going to take care of security. But, It’s better if it’s from a different person instead of the administrator of WordPress.
“Pandora FMS” uses API’s to collect information; we can specify the IP addresses of the servers, which are authorized for that, this refines security by closing the entry gap. Also, by default, those APIs report changes every hour and we have seven days to keep our security records of the “Pandora FMS WordPress plugin”; after this period of time, these records will be erased to save space.
“Access Control” in Pandora FMS WordPress plugin
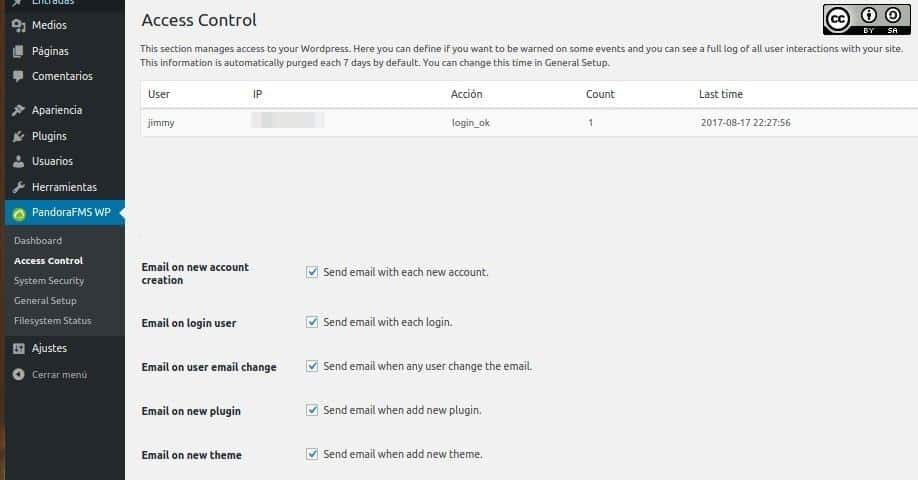
This picture displays the data of connected users and the time and date and IP address of if. This plugin records the successful or unsuccessful attempts of registered users, but if someone tries to log in with any other username, we will not be able to see it here, however, we will go through another method in order to combat these attempts. We will also see that these IP addresses can be added to “Blacklist IPs”.
The Pandora FMS WordPress plugin will notify us of the following aspects, which are activated by default in the installation:
- “Email on login user”.
- “Email on new account creation”.
- “Email on user email change”.
- “Email on new plugin”.
- “Email on new theme”.
We are able to monitor all these events apart from the first one. We didn’t check if this Pandora FMS WordPress plugin notices when adding a user through MySQL directly, as shown in this tutorial, we leave this task for you fellow readers to practice your skills.
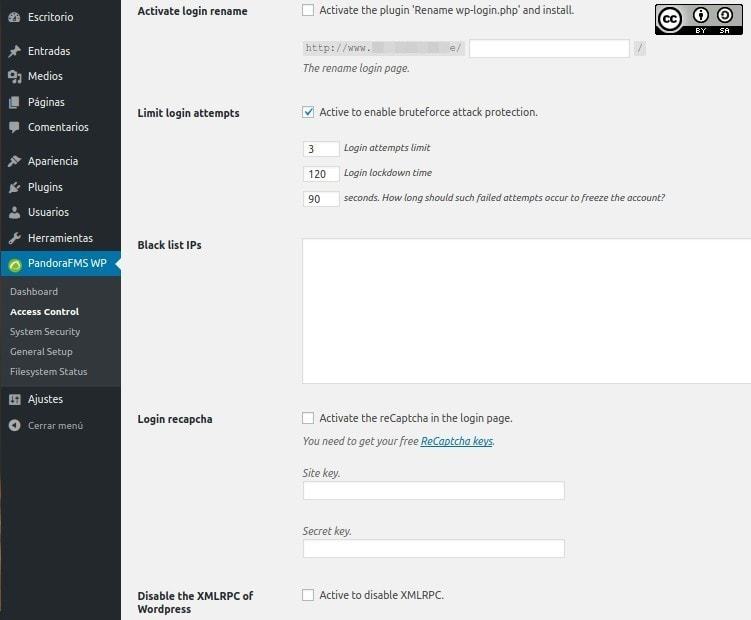
“Activate login rename”. It means that the file “wp-login.php” is renamed but this change is not as simple as that: You have to change the references of that file. For example, we did a test by renaming the file that allows us to enter our user credentials; we named it jimmy and saved the preference. Next, we added a user named lucy, and we received the following message by mail which let us know about the new user but also, the new user received a message too with the link of the renamed file (which invited us to change the password) here’s the screenshot of the message:
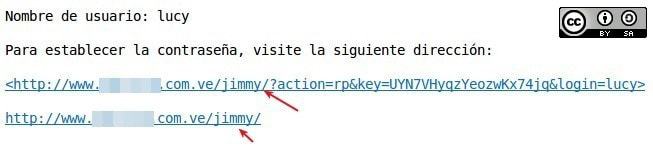
The idea is to “hide” the file from the public view, thus cutting off any unauthorized access attempts. We can even change it periodically to further mislead the unwanted. There are different plugins that are dedicated exclusively to this purpose.
Although this measure might be clever, it can also be dangerous to the point that if something were to go wrong, the only solution would be to re-upload the WordPress system files via SFTP in order to gain access again.
By default, this is activated: “limit login attemps” which means limiting the number of attempts incorrectly to a maximum of three, blocking access for 120 seconds including correct and valid users.
As we mentioned earlier, there is a text box where we will write the IP addresses which we will deny access to. The other option would be to place a CAPTCHA and then you name it as ReCaptcha because we must request the corresponding keys to completely prevent automated attacks, this is actually part the technology from Google. This feature is disabled by default.
Finally, the “Disable the XMLRPC of WordPress” section is not activated, although it is very useful in order to communicate and exchange information between different platforms and our site is also used to attack our system, especially “pingbacks” and “trackbacks”.
“System Security”.
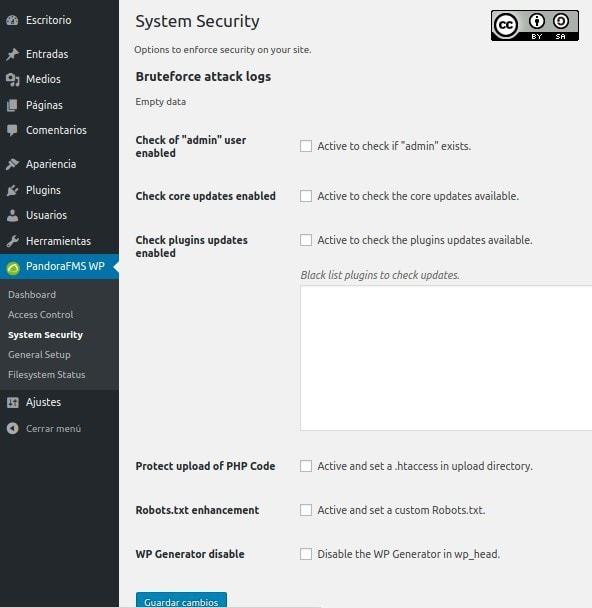
Finally, we have the option to strengthen the security of “WebLog“, the first thing to inform is the registry of brute force attacks, which is empty now, as we have just installed it.
When installing WordPress, a default user named “admin” is created so, first of all, we must create an Administrator account for ourselves and then delete that preconfigured account. The Pandora FMS WordPress plugin is responsible for verifying that this account does not exist since it would be very easy to exploit.
Although usually WordPress is configured as “automatically search for updates”, (including plugins) so if the “Pandora FMS WordPress plugin” is disabled, then it will let us know about it. It also allows us not to update certain plugins: by adding them to the list so they become “frozen in time”, and then it will not warn us about new available versions of these plugins.
We can prevent files with the extension “.php” which can be executed with some malicious code through these special configuration file called “.htaccess” for the “Apache Web Server” . We need to tick this option for this.
(We can also delegate the responsibility of configuring the special file for web browsers, which is called “robots.txt”.)
Finally, another way to avoid hackers and crackers is to inhibit the display of the version of our blog. Although we can do it ourselves, we need to make our lives easier from time to time. This reasoning for protection is described below, and it is logical: imagine that for a specific version a security bug that allows expressing data in an illegal way is discovered, what would cybercriminals do? They would search those portals that still use that same version which could be very easy to do it if we display it constantly in each entry or section. If Google or Wayback Machine has a “screenshot” of the site (data cache) of our version, where they have recorded that version used by us, then we will have it patched by the time attackers arrive.
Conclusions
You need to bear in mind that cybercriminals can be really clever, and they can use you as a slave agent to attack other websites or to distribute spam, so be careful, this Pandora FMS WordPress Plugin will always be there and will help you 24 hours a day, 52 weeks a year.
All images used here were captured and modified under our authorship and are licensed under Creative Commons Attribution-Share Alike 4.0 International
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services, and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
If you have more than 100 devices to monitor, you can contact us through the following form: https://pandorafms.com/en/contact/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring. Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.




















