php IPAM: Check IP addresses and all their changes
Php IPAM , as its compound name indicates , is the use and administration, through PHP, of Internet Protocol Address Management (IPAM) addresses, which makes the software very unique. In this article we will look at how we can use php IPAM as an auxiliary tool, although we will find that it has certain monitoring-based elements, let’s go!
php IPAM and Pandora FMS

In a previous article we explained what an IP calculator is and how it works when implemented in Pandora FMS. The truth is that since May 2014 (and formally released in version 5.1). Pandora FMS includes IPAM as a very useful extension for the management, the discovery, the existing agents associations, the registration of comments in each one of the IP addresses, also being able to establish exceptions from the monitoring point of view. The IP addresses can be detected through ping or through the IP addresses given to us by the agents previously registered: Pandora FMS will do the equivalences and correspondences for us.
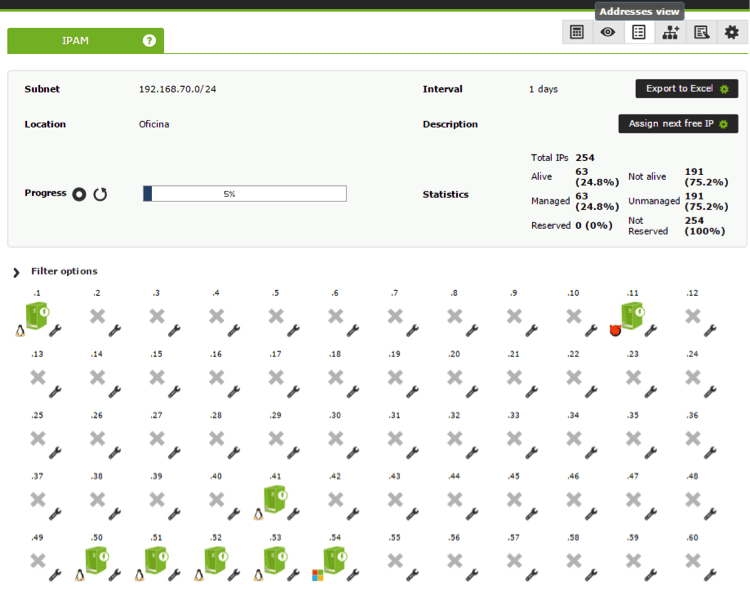
When the detections are controlled by the Pandora FMS agents, it is easy to know their operating systems, which are represented graphically in the IPAM extension. We can set alerts when an IP address changes, we can also see an overview with all the addresses or in a segmented way: the active devices, the managed devices, etc. and their possible combinations.
So, what is the advantage of using php IPAM?
php IPAM
There is a great variety of software available to work with IPAM and in this article we will look at php IPAM software in detail as an auxiliary tool but first we will look at the concepts that involve IP addresses: without this abstract concept the Internet and the monitoring would not exist at all.
Brief history of php IPAM
The first public version was 0.1 and by November 2014 php IPAM released its version 1.1 of Miha Petkovsek’s workmanship, in January 2016 version 1.2 and in July 2017 version 1.3 was released.
It is developed under the free software modality, GNU 3 license since June 2015 when the repositories were moved to GitHub and apparently its funding source is donations of both money and web hosting. In fact, the site is in a special virtual machine, provided by a webhosting company. This free software model has brought together a select community so it is difficult to find information about it.
Today, in almost every business and home, there is a local area network. At the start of the Internet, the IP address system was planned in such a way that it was decided to set aside three types of network for private use on local area networks. These addresses are called private addresses. Each organization can use these private addresses to connect its devices and each device can also have one or more IP addresses. (For example, a laptop can be connected by Ethernet cable, by its integrated “wifi” antenna and also by a “wifi” antenna connected by USB port; generally web servers are redundant and have two Ethernet connections for data traffic and at least one Ethernet connection for monitoring).
The addresses are repeated in each organization, but there is no problem because they are not connected to each other and this is where the Internet comes in, the interconnection of private networks through the network address translation (NAT) because on the Internet each public IP address is unique and routers get a public IP address which is “shared” within each organization.
Numerical practice (IP calculators)
How many IP addresses do we need in our organization?
There are three types for private use:
- Class A: 10.0.0.0 a 10.255.255.255 (8 network bits, 24 host bits).
- Class B: 172.16.0.0 a 172.31.255.255 (16 network bits, 16 host bits)
- Class C: 192.168.0.0 a 192.168.255.255 (24 network bits, 8 host bits)
In short, class A allows a single network with millions of IPv4 addresses, class B allows 16 networks, each one with thousands of IP addresses and class C allows hundreds of IPv4 addresses (exactly 253 because 0 and 255 have other uses that we will discuss later on). There are other kinds of networks that are not relevant for this article, such as Class D for multicasting and Class E for research and development.
For our minds, in reality, Class C networks are adapted to our needs at home and in small businesses. Keeping track of one or two dozen devices on the router that shares a public IP address for the entire private network is easy and convenient to use.
But in the other cases, thousands and even millions of IP addresses are a real nightmare, a very time-consuming undertaking. For these cases we have to follow exactly the same steps as the Internet Corporation for Assigned Names and Numbers (ICANN): to assign each of the departments a subnetwork and to delegate the authority to the department heads. But writing down and recording everything easily exceeds the capabilities of a spreadsheet and that’s why the php IPAM software was developed.
Installation of php IPAM
Unlike the historical details, there are many tutorials about php IPAM on the internet, some of them are better than others; we tried it on Ubuntu 16 and then we got the images that you can see. The first thing we did at the end of the installation was to upload our own logo for evaluation purposes and fill in the data that identifies our test server including the sending of email which is very important to receive the alerts, although this is not so common due to the nature of the work.
In short, you need a MySQL database server, an Apache web server, the proper firewall permissions when scanning your network or local area networks… and even the subnetworks, this leads us to the following point.
Subnetworks (or in other words: how php IPAM works)
Some of us do not work with hosting companies or Internet access providers, so the examples discussed here are based on private addresses. We can assure you that everything described here applies to the Internet and there are organizations “that make money” with the help of php IPAM, which in turn donates to the FreeBSD Foundation, so this is an endless cycle.
The tasks of php IPAM are the tracking and storage of information in a MySQL database of:
- Our devices and their IP addresses.
- Our computer cabinets or racks
- Our circuits (with the help of Google Maps APIs)
- It supports LDAP authentication which saves us a lot of work.
- To keep track of virtual private networks.
- The NATs we have created for our computers to connect to the external.
- You can even make notes in a sort of micro Wikipedia! (although we do not recommend it for issue management, perhaps it could be done in chronological order of cause/effect/solution to avoid making the same mistakes twice).
In order to talk about subnetworks, which are a routine and difficult task to synchronize between computers, we first have to explain how they are managed and why they exist. In 1980, the devices that were in charge of connecting to Internet were very basic devices. Thus, the need to create work subnets arose, but the computers did not have the necessary technology. The solution was to create subnet masks as a way for the devices to quickly detect whether the message or datagram received belonged to the subnet they had been assigned to work on.
That is why the mask is used to distinguish the IP address between the part that identifies the network and the part that identifies the device, apart from the fact that it does so with binary numbers. The network masks have the same format as the IPv4 addresses but always with values for each byte always one by one, for example the network mask for a private class A network that we will create in php IPAM would be the following:
11111111.00000000.00000000.00000000
That is, in decimal notation, 255.0.0.0.0 since our private network can contain millions of IPv4 addresses (the multiplication of the last three bytes 255 x 255 x 255 = 16581375 approximately because the zero addresses identify the network and 255 is used for multicasting). Now let’s imagine that it is possible that we have at least one million devices in our organization. How would the devices maintain the transport and shipment of packages or datagrams with such a volume of users?
The practical solution of that time was to apply an AND operation (an AND operation is a simple multiplication) to each packet address and netmask, in order to determine if it was for the network or subnet. Let’s assume that a packet is routed to 10.0.7.23 on our Class A private network
0000000010.000000000000.0000000007.0001010111 <-package addressed to 10.0.7.23
11111111.000000000000.000000000000000000 <- net mask 255.0.0.0.0
00000010.000000000000.0000000000.0000000000 <-oper. AND results in 10.0.0.0.0 (multiplication)
Here is something that is implicit: our network mask, “the one we chose” is implicit because a class A network the first octet identifies the network, that is 8 characters so in a notation called CI DR (which implies the address of our network and the network mask together) is represented by the following simply as follows: 10.0.0.0/8
1. Creating a private subnet
Now imagine that in our private class A network we need a subnet where we will place the machines for our programming tests. For this purpose, 253 IPv4 addresses are more than enough, so by mutual agreement with our computer we are assigned 10.0.0.0.0/24 this means that in the private network class A 10.0.0.0.0 we are assigned a net mask 255.255.255.0 and going back to the last numerical example, but with our net mask:
0000000010.000000000000.00000111.0001010111 <-package addressed to 10.0.7.23
11111111.11111111.11111111.0000000000 <- net mask 255.255.255.255.0
00000010.000000000000.00000111.0000000000 <-oper. AND results in 10.0.7.0
(it is not our network, our network is identified as 10.0.0.0.0)
2. Public subnet
At the end of the last century we realized that IPv4 addresses were running out due to the exponential growth of the Internet, so ICANN realized that many Internet Providers (“Internet Service Providers” or ISP) were assigned very large blocks which caused idle IPv4 addresses. The decision was Solomonic: to allocate using network masks for each provider in order to fit the right size and believe it or not, their computers do these calculations millions of times a day: they compare addresses against network masks to see if they are in their subnet (today, in fact, there are other mechanisms implemented in the now existing modems, routers, hubs and repeaters but the basic concept remains the same). That’s why we said that many organizations benefit from the use of php IPAM to register and plan assigned addresses.
3. Subnets with variable length mask
If you have understood up to this point what we have explained, some academics or professionals could be surprised. We can move on to the concept of variable length network masks: as simple as they are not limited to the values per byte (8, 16 and 24) but to any other value, such as 10.0.0.0.0/28 for our example (we will leave this one for you to practice with your IP calculator).
Creation of users and groups in php IPAM
After this conceptual basis, we recommend to start with the creation of groups and then users when working with php IPAM. Php IPAM includes by default two created groups: administrator group and guest group. This will simply allow us to group our users together when it comes to a search or visualization or to keep in mind some kind of order, i.e. it does not provide any other use of writing or inheritance rights.
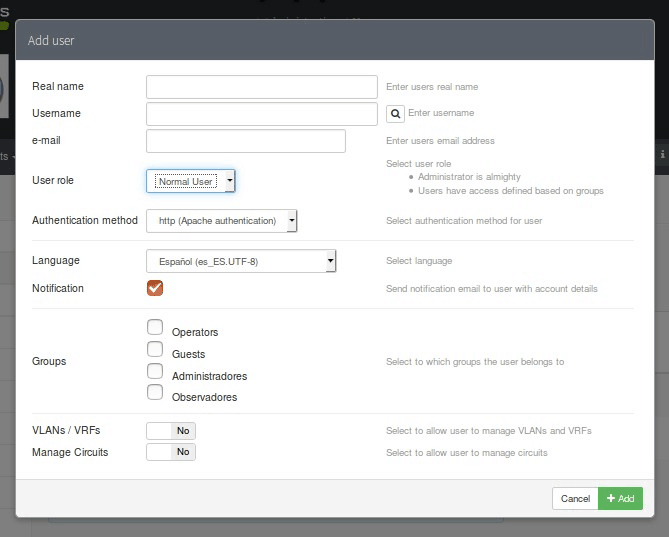
In the user creation part we will have the complete overview: to create a user as a normal user or administrator and at the same time it will show us the groups that we have created ( remember that the description of the group with its user classification is not binding, a group that is described as “Remote Administrators” does not mean that its users have administrator rights). Simplicity is often welcome, by using the two groups that are created we can work unless the organization is extremely large.
When creating a user it will show us how our users will authenticate themselves and we will only see two options: by local database and by Apache which is an outdated and file-based method that we do not recommend. Our choice will be LDAP, however, we must first activate the php-ldap library on our Apache server and restart the service. In total there are seven possible forms of authentication:
- Local.
- Apache.
- Active Directory (AD).
- LDAP.
- NetIQ.
- Radius.
- SAMLv2.
IP calculator
Once we have paved the way for work we can create our networks and sub-networks. The easiest way is to go to the integrated IP calculator, enter your assigned CIDR or the one you will create yourself in the case of private networks. php IPAM will calculate and display all values and will offer to create a network with that result and even its subnets.
*Important note: if some subnetworks or phpIPAM subnetworks overlap, this will be indicated in a red letter warning.
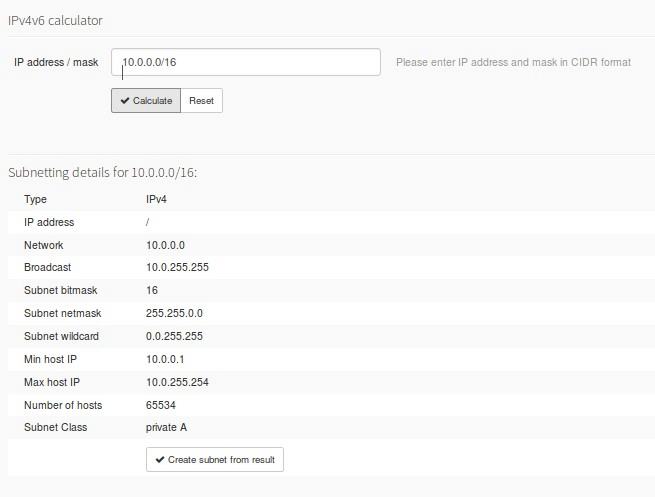
Once the CIDR values have been set correctly, we can assign the user groups the corresponding rights over that network or sub-network (note that the rights are given here as an option). Here we would like to highlight once again the peculiar way of managing read and write rights in php IPAM!
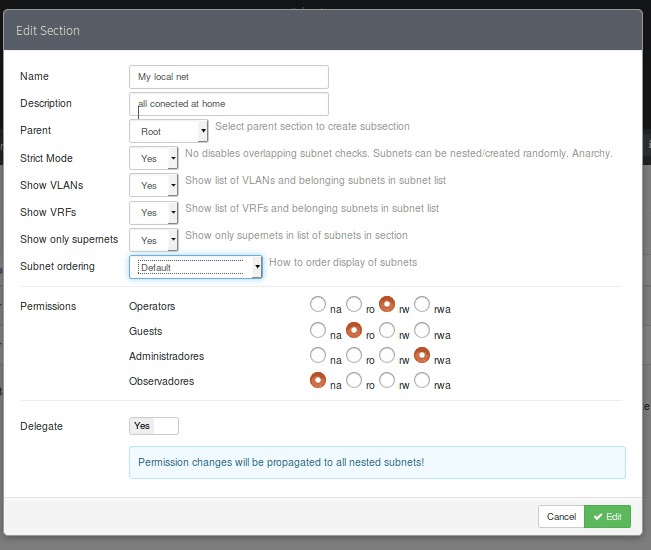
Exploration of devices in php IPAM
To facilitate the tasks of adding php IPAM, it has the utility of using the ping program to contact the devices to our network or subnetwork previously created, but the interesting thing is that there are two more ways, one for the devices that we already have and the other one for the new devices:
- Through agents: this is similar to Pandora FMS, that is, a software installed in each machine and suitable to the current operating system. In Windows environment the Active Directory will allow us to massify this task and in GNU/Linux by SSH and well designed scripts we will be able to manage hundreds or even thousands of machines as desired.
- Here’s what’s new and very useful:
- When installing new devices we can configure them with the name of the network or sub-network.
- With its respective script it connects to the API of php IPAM.
- Check the last free IP address in that range.
- Self-assigning this value.
- It confirms to php IPAM and is registered in the MySQL database.
- This way php IPAM becomes a kind of DHCP with the difference that it is only used once: when the virtual machine or device is installed (it can also be real, it is the same but it is obvious that a human being is in charge of the process, this would happen when mounting the server farm racks, which in turn contain the virtual machines).
- Currently there are virtual machines that can even be built by our own clients as they wish on our server farms ( each one chooses his or her operating system for the hypervisor we have configured with php IPAM.
- Of course it also includes deletion routines, in case the virtual devices are deleted or the real devices are moved or deactivated.
Auxiliary tool
php IPAM can also register our DNS servers , monitoring idle IP addresses and devices, with a simple ping , fping or pear ping.
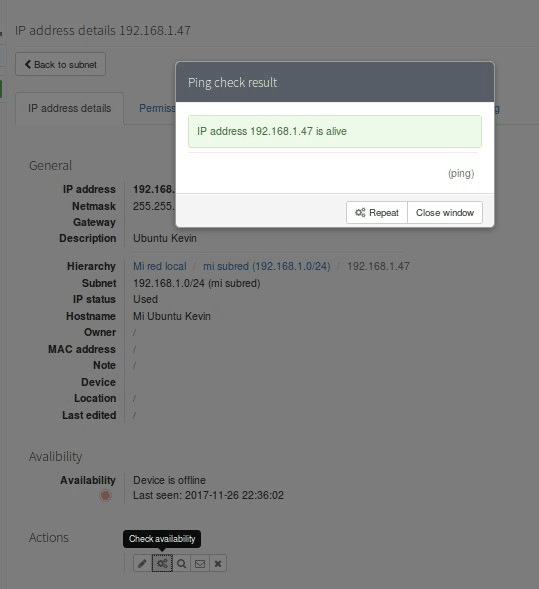
It uses agents, registers and manages NATs as well as basic monitoring with SNMP, but first we must configure our Apache server with the php-snmp module . Then we can configure the devices to monitor . It will even allow us to create SNMP traps , which are useful for the creation of event alerts . For a better compression we have a complete article on the basic aspects to consult through SNMP.
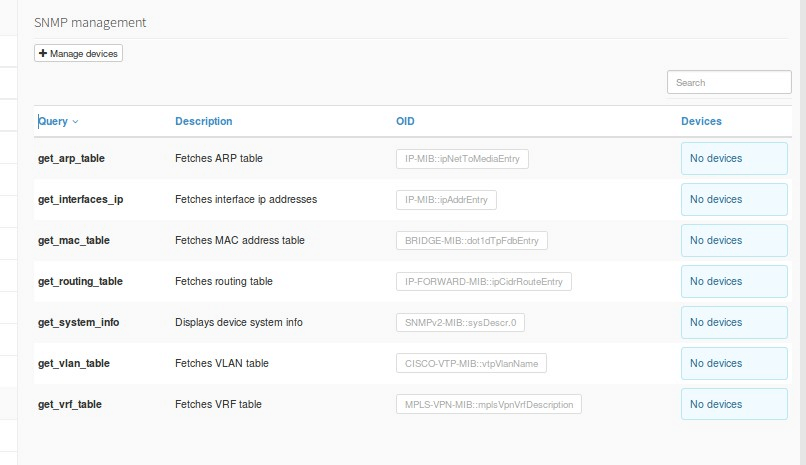
Exporting and importing data
To finish, php IPAM has the option to import or export data in spreadsheet format of the sections we might need or we will be able to export (but not import) the complete database in SQL format or in a large spreadsheet!
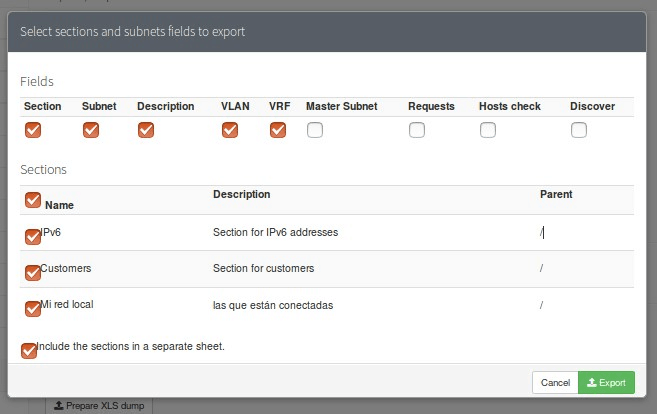
In the case of importing data we must follow a detailed protocol, in order to have an exact compatibility of the data:
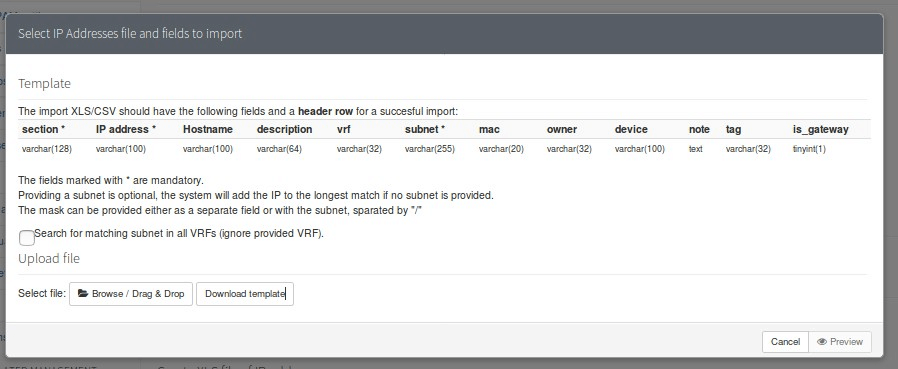
Automation in data export
Although the option spreadsheet is available, We suggest to develop through the API few scripts that allow extracting updated data and whether there have been changes in the network and what those changes are, if we have added or removed devices, ourselves or our clients to whom we have delegated the creation of virtual machines and thus we will be able to monitor with Pandora FMS the complete infrastructure.
If we want to go one step further, we could also create a plugin for Pandora FMS that consults directly in the database looking for changes but it is an advanced topic, it would not be a normal plugin (obviously with read-only rights, always from php IPAM to Pandora FMS).
Conclusion
We predict a great future if with php IPAM, which is created in free software and to which we have access to its source code, we can obtain data on what devices we should monitor in an almost completely automated way, keeping the infrastructure planning and development computers completely isolated from the monitoring and maintenance ones. We see then, an excellent symbiotic relationship between both software products!
Please leave us your comments or opinions and we will be happy to answer all of them.

Programmer since 1993 at KS7000.net.ve (since 2014 free software solutions for commercial pharmacies in Venezuela). He writes regularly for Pandora FMS and offers advice on the forum . He is also an enthusiastic contributor to Wikipedia and Wikidata. He crushes iron in gyms and when he can, he also exercises cycling. Science fiction fan. Programmer since 1993 in KS7000.net.ve (since 2014 free software solutions for commercial pharmacies in Venezuela). He writes regularly for Pandora FMS and offers advice in the forum. Also an enthusiastic contributor to Wikipedia and Wikidata. He crusher of irons in gyms and when he can he exercises in cycling as well. Science fiction fan.