Why backup monitoring is fundamental
A backup, for those whose IT knowledge is a little rusty, is a copy of certain files stored in a safe place for reasons of security. This practice usually covers you in case of incidents or problems on your principal network, as the data is generally stored on an unassociated network, or, more usually, completely offline. It should be a regular practice for any systems administrator, as well as complementary backup monitoring. Let’s look at some example situations.
Reason number one: security. With the example of Wannacry still fresh, alarm bells are ringing in every sector’s IT departments, making IT security a trending topic. This is one of the subjects that interests us in the present article, and its relation to backup monitoring. If we can’t avoid these frequent attacks against our infrastructure, at least we can take steps to mitigate the negative effects.
A little more context; what is ransomware? It’s malicious software designed to restrict users’ access to their own files, by blocking the OS, encrypting the data on them, blocking hard drives, and demanding a ransom for their safe return.
There is a multitude of virus of this kind, propagated via trojan horses or computer ‘worms’, that invite the careless user to open an infected file or to click on a doubtful link. Wannacry is the virus on everyone’s minds right now, but this specimen was preceded by others, with names like Reveton, CryptoLocker, CryptoWall, TeslaCrypt, Mamba, TorrentLocker, etc.
Prevention
Fundamental security recommendations are to maintain all your software and systems up to date, use a corporate antivirus, and obviously, not to trust any unsolicited URLs or suspicious emails.
Add to this the use of backups. These should be stored offline, on hard discs out of the reach of infectable hardware, so, in the case of attack, your data can be recovered and your business, organization or infrastructure affected as little as possible.
Despite backups being used ever more frequently, particularly at corporate and business level, it is still complicated to know if your data is being stored correctly, if there is enough space on the drives where the data is saved, if there has been a problem inside the anonymous black box, or if any one of a number of backup fundamentals has been omitted. Hence, backup monitoring.
Backups
Backups are created in diverse ways, depending on various factors; available technology, systems, capacity, requisites, company policy, etc. That’s why, far from being a trivial issue, every back up is a unique case, with its own complexities and inherent problems. Let’s take a look at some sample backup cases plus how to monitor them for maximum guarantees, ensuring that our precious data is available in times of virus crisis.
There are three basic types of backup:
- Complete backup: a complete copy of all your files.
- Differential backup: makes a copy of all new or modified files created since the last complete backup.
- Incremental backup: a copy of all new or modified files created since the last complete or differential backup. The optimal choice in terms of performance and disc space as well as being the most widely used.
Due to the particularities of each generation of backups a generic monitoring system applicable to all cases is currently unavailable. Despite this, Pandora FMS is flexible and customizable and gives you options for covering most cases of backup monitoring, whatever the specifics of your case.
Search patterns in backup monitoring
Whatever kind of backup you use, or the methods of its creation, it will be stored under certain directory patterns and files that can be used as references: name, date, time, version, etc .
This is due to the necessity of quick and intuitive access to backup files, which should be given easily identifiable labels, and which you can take advantage of to create the monitoring you need.
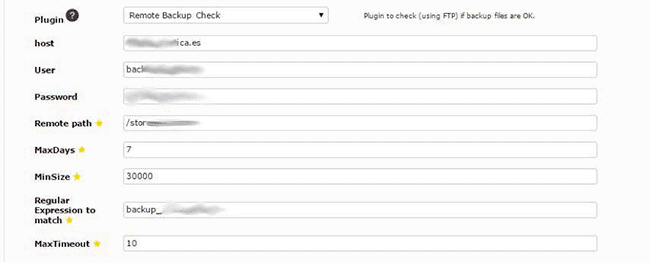
The following is a practical case of monitoring backups that are saved on an FTP server with a system of specific labeling. We’ll use a remote backup monitoring plugin with the following parameters:
- Host of the FTP server.
- User of the FTP server.
- Password of the user.
- Path where the remote FTP files are located.
- Maximum days in regards to the calculations. That is, Pandora FMS will check, within the configured timeframe, that the backups are being stored correctly.
- Minimum size that the backup files should have, keeping in mind the amount of data to be stored on a daily basis.
- Regular expression of the backup search word.
- Timeout cancels the execution in case of uncompleted connection.
In the screenshot below you can see how the parameters are used to perform backup file searches whose names match the regular expressions given on specific systems and paths. It also checks that the file size is correct and that the number of backup files created is also correct.
Taking all these options into account you can set up very reliable backup monitoring thanks to Pandora FMS.
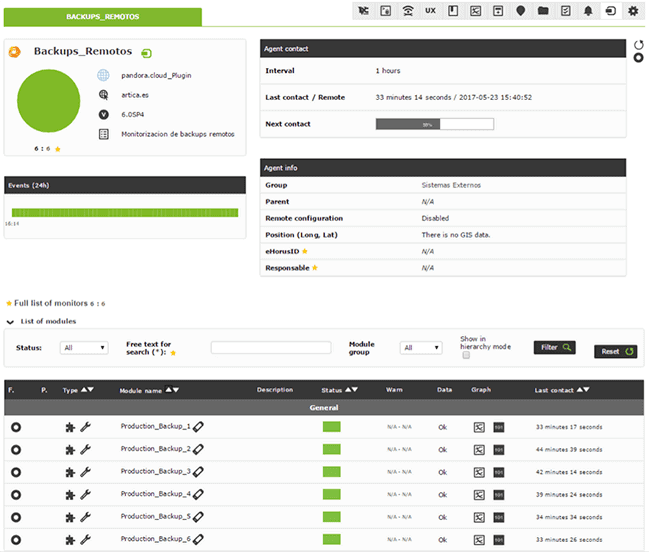
Examples like this show how simple it is to set up backup monitoring with Pandora FMS, employing different systems for collecting information. In this case a remote FTP server connection has been used, although installing a software agent to collect the data locally would be another option to achieve the same result.
Search terms will vary according to the specific case, and in the majority will be based on the patterns mentioned above, using regular expressions and sifting the results.
Apart from monitoring the backups themselves, the hardware on which they are saved can also be monitored to check that everything is fine. Pandora FMS offers plenty of options for this kind of monitoring as well, whether you want to monitor using SNMP, an FTP plugin, or software agents to carry regular out local checks in more detail.
Thanks to Pandora FMS’s flexibility it’s possible to monitor backups in various ways, using different options to maintain control and security on your systems, while maintaining tight security.
Furthermore, in cases of security breaches and compromised systems Pandora FMS’s visual reports can give you essential feedback on where incidents have been produced. The following graph shows where a couple of incidents have occurred with the system of backup generation:
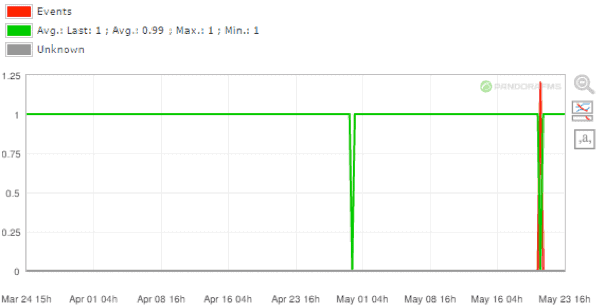
There are many commercially available options for automated file backup. Most of them are powerful and can be complicated tools to use. In coming articles we’ll be looking in detail at how to use Pandora FMS to monitor dedicated backup systems such as Bacula or Veritas Backup Exec.
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
If you have more than 100 devices to monitor, you can contact us through the following form: https://pandorafms.com/en/contact/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!
Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring. Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.





















