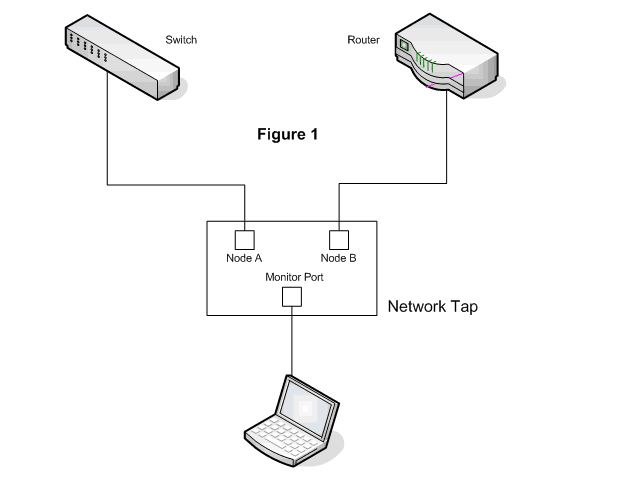
Network TAP (Terminal Access Point or Test Access Point) is the most common hardware device used for network traffic capture purpose.
A Network TAP is basically a hardware designed to access the traffic between two network nodes and mirror it into a monitor port where we can connect a third party Analysis tool to listen.
Network TAP: three situations in which they are necessary
- Any SPAN port depends on processing resources of the switch where it is defined. This fact implies using SPAN ports can affect the throughput of the network or be inefficient for the amount of packets lost.
- Regularly SPAN ports don’t copy to monitor port those packets or frames corrupted in some way, that is to say, errors in level 1 and some in level 2 are removed.
- The efficiency of a SPAN port depends on the relation between the amount of traffic we are capturing and the capacity of the monitoring port we are using.
Network TAPs are intended to be the solution to those problems based on the following characteristics:
- Network TAPs don’t depend on the processing resources of any network node.
- Network TAPs are capable of gathering all data on the link they are connected to, including corrupted packages and frames.
- TAPs do not cause interferences on the traffic they are gathering. Also they allow a continuous flow of data, even in the event of a failure or a cut on its power supply.
Additionally, Network TAPs have other interesting characteristics that can change depending on the manufacturer, if you are interested in a list of different types of TAPs and their features we recommend reading this article.
Now that you know the main advantages of Network TAPs we recommend finding out when you should use this kind of device.
Monitoring a network link with high level of traffic
This is the main situation for considering using a Network TAP as an alternative to an inefficient SPAN port.
Links with high level of traffic are also crucial for businesses, so first of all we have to think how we can interrupt the network’s service in order to install the Network TAP.
Then make sure the TAP you will use is a real Bypass Network TAP or has this feature in order to keep the traffic flowing in case of any failure to prevent a network shutdown.
We recommend checking the volume of traffic offered by the different manufacturers. You can find TAPs with monitor ports from RJ45 of 10/100Mbps and fiber optics ports of 100Gbps.
Different tools requiring network traffic capture
If you have different tools that require network traffic capture (Security Systems, IDS, IPS, monitoring, traffic analysis system, etc.) two or more tools will need access to one specific network link, duplication of traffic, several point of failure, etc., which can cause some problems.
The first step could be to make a review on the tools and consider only those tools we already use or those we need to use in the near future.
Taking into account that every tool is as good as the information it works with, we have to define a strategy to capture, filter and deliver the data.
In order to capture data, we have to identify the places where more than one tool must gather traffic, for example the traffic through the internal port of a central router, which could be a target for a security system, for a monitoring system and for forensics system.
In those network segments we can use a kind of Network TAP called Regeneration or Replication Network TAP, which can create multiple copies from one network segment and send them to different monitoring ports. In figure 2, we have a TAP with a 1:3 ratio.
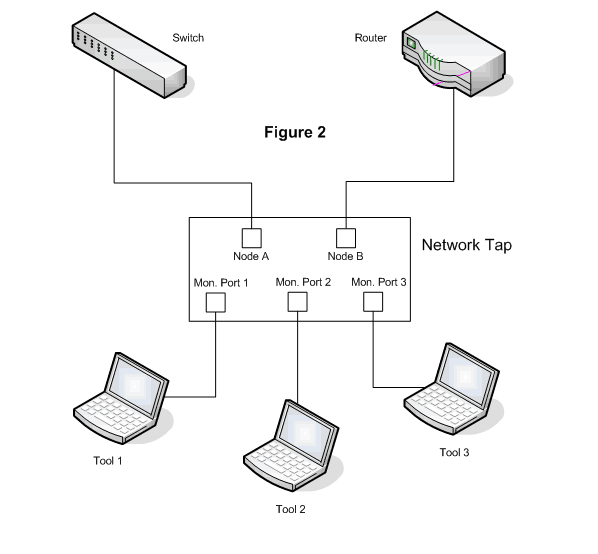
For filtering, we have to know what kind of taps can include features of filtering data on certain rules in order to adequately capture, following the requirements of each tool.
In complex environments with many tools, very specific requirements and many points of gathering (or if you are facing an ambitious project of Total Visibility Architecture) you can consider the possibility of including a Network Packet Broker (NPB)
A NPB is also a hardware that is oriented to concentrate the data gathered by different TAPs and bringing very sophisticated level of filtering and delivering data.
Monitoring traffic between virtual servers
The penetration of server virtualization technologies implies a challenge for monitoring. In high virtualized environments there can be a lot of traffic between virtual servers that never crosses a network physical port, and analyzing this traffic could be a crucial step for Application Performance Monitoring.
Traffic between virtual servers are commonly referred to as east-west traffic in order to establish a difference with the north-south traffic, which is the traffic that flows through networks links, for example the traffic between users and one specific server.

There is a kind of Network Tap to capture east-west traffic that is called Virtual Tap. This software-based version of a Network TAP is configured to capture the intra Virtual Machines traffic and send it to monitoring tools.
When choosing a Virtual TAP, it is very important consider those that are fully compatible with hypervisors (VMware, Hyper-V, KVM, etc.) in our installation.
Another important aspect is the performance of the platform after the installation of a Virtual TAP; consider the consumption of resources (CPU, Memory) of the virtual TAP and the impact of sending gathered data through network.
We recommend Virtual TAPs that can filter data before sending it through the network.
Additionally, the cost is usually a main issue for Network TAPs. However, you can find equipments in a wide range of prices, from a few hundred dollars to thousands of dollars, depending on the specificity of the TAP and its features.
Consider taking time to choose the appropriated TAP and finding the correct balance between your budget and goals in Monitoring and Security.
Don’t forget to share your experience with Network TAPs and ask for a Pandora FMS Network Monitoring trial by filling this simple form.


















