Linux vulnerability is measurable through Lynis security
But does this mean that Pandora FMS is also into Lynis security? Well, its specialty is different… but yes, of course, it reaches everything covered by monitoring. In fact, flexibility is inherent to its name: FMS means Flexible Monitoring System and it is a tool with which you can save yourself many headaches, as well as tailor it to your needs!
Plugins in Pandora FMS
For those who do not follow our blog, Pandora FMS offers, broadly speaking, two types of add-ons: server and software agent.
But what does Safety have to do with Lynis and Pandora FMS? Well, you can develop a plugin that runs on the machine that you need to monitor to obtain a score, out of one hundred, which will be obtained by means of Lynis.
You are then faced with security monitoring, based on discrete values related to questions such as: What security level do you have in a server cluster?
With Lynis and Pandora FMS, in this article we do not claim to be the blue team -in the cybersecurity world the red team is the external one, which attacks your systems on purpose-, but we can answer with an exact figure when we can go to safety tests for both teams. For example, let us say Lynis gives an average score of 71 for the entire system: the red team will have to check whether that is true and the blue team will take note of the tips and warnings to improve the security level.
Lynis security: installation
Pandora FMS will allow to configure an overview in your console about the average level obtained, but if you want – or rather you have to – raise that score, you must pay attention to Lynis messages.
To that end, start by installing Lynis. It supports Unix substituting operating systems, such as FreeBSD, Linux, macOS, OpenBSD and Solaris. In fact, it is part of the solid Kali Linux distribution, used by security professionals and hackers. Us, heavy Debians, use a virtual server with Ubuntu 18 that has tasks to perform MySQL database replications.
For this case, Lynis is available in Canonical® repositories, a company that develops Ubuntu; but if your distribution has not included it yet, you can always copy the source code from GitHub.
Legend: «sudo apt install lynis»
In this last case, there is absolutely nothing to compile! Lynis does not need specialized libraries, BASH is enough to use it. However, do not underestimate Lynis, as it complies with the ISO 27001 specifications that normalize information security, as well as other standards such as “Data Security Standard for the Card Payment Industry”, in order to fully comply with the “Vulnerability Management Program” point.
Lynis security: First security report
Similar to how Docker Bench does it, you will obtain a long document where, at the end in the «Hardening index» section (strength index). In the example it gave back a value of 56.
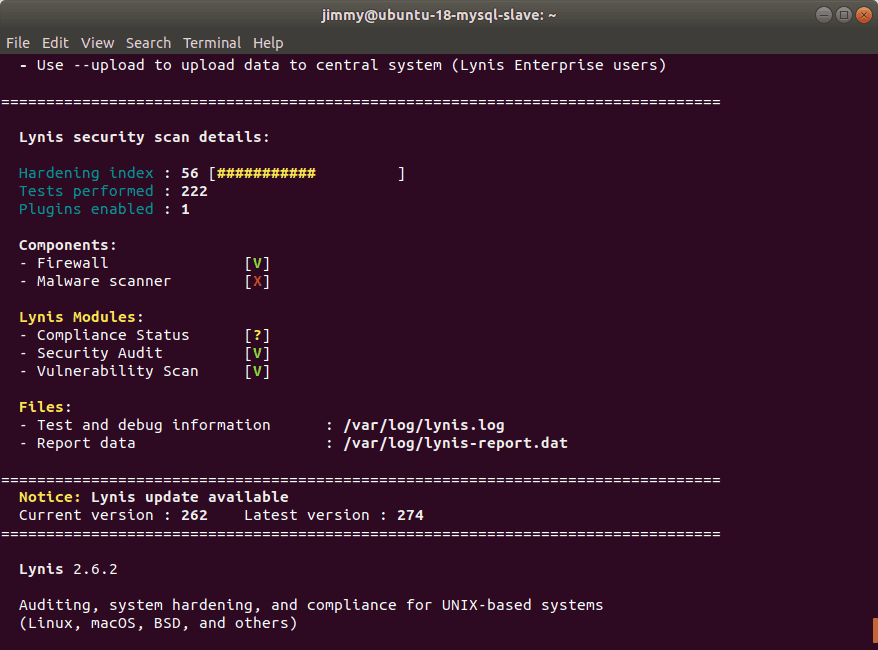
Legend: «sudo lynis audit system»
The Lynis version we tested is for a maximum of 100 devices. The Enterprise Lynis version allows the –upload parameter which sends a copy of the results to the CISOfy software house, company that develops the application.
This evaluation made with Lynis is the Debian complement with 222 standard tests.
Lynis security: Overview
It is impossible to address all aspects because, as we repeat,you are just monitoring security and in no case are you implementing it. You are just a thermometer that reports a value to your Pandora FMS server. However, we can list the basics:
- Directories and files related to registration and auditing.
- Software packages installed and yet to be installed.
- Configuration files.
- Files that load boot mechanisms.
In points one and two, you have, just to name a few, the verification that you have installed, apt-listchanges or debian-goodies for tracking installed packages, as well as needrestart to obtain the services («daemons») that need to be restarted after some update or fail2ban to control brute force attacks. Lynis also checks that your repository list includes one devoted to security, which is the most important in order to deal against “zero-day attacks“.
In point four, remember to protect Grub2 by password, in order to prevent that, in the event of a person’s physical irruption to your equipment, it is not possible to take advantage of restarting the equipment and executing recovery options, for later opening entrance doors. In the field of partition and disk encryption, it will also present many suggestions, while in the firewall section, it will show a warning of uncreated rules, even if it is working at that moment (that is, it is installed with the default settings).
Where also close attention must be paid -due to the large number of suggestions- is the SSH support section, no wonder since this is vital to manage your equipment remotely. It checks the support for SNMP, LDAP services, if you have PHP installed and some web server (Apache and Nginx by default) and that is it.
Lynis security: Security reinforcement
If you have reached this point, we must confess that the easy part was our constant monitoring task. We have already published how to retrieve the value that interests you: you can configure Pandora FMS if this score falls below a certain value (this can happen when you have not frequently updated the software, or if several security important programs are uninstalled for some reason).
To be able to see the suggestions of the last report, just execute:
sudo cat /var/log/lynis-report.dat | grep suggestion
And then take note of the descriptions and structured codes. In any case, the work is upon your blue team who will be in charge of the whole task of raising that score: with constant practice and determination the time will come when they ask you what else you can do to improve. Faced with such a possible – and rather likely – request and without being security analysts, some of us will indicate the option of the Lynis security development set.
This set of development tools are very clear in GitHub and there they structure its scope in three steps that I consider very logical:
- Contributing to Lynis by sending them your feedback (I call this “retribution”: here it is very important to note that you should always use “Bourne shell” instead of BASH to ensure that what your contribution supports all Unix platforms).
- Make sure that evaluation quality is kept.
- And the most important part: start using custom tests and then evolve to create your own plugins.
Once you reach this last stage, as a monitoring team, review and, if necessary, reconfigure the monitoring tasks. If you are still not sure why monitoring covers so many fields of automated computing, we recommend you to read our article about development, operations and security equipment where any doubt about it will be clarified.
Satisfied with Lynis security but still want to know more about system monitoring? Luckily, you are at the right place to find out more. In this blog, there are dozens of articles that can get you in this exciting world. Here you have a link to our home page.
Or you may also contact Pandora FMS directly if you have more than 100 devices to monitor. Click here.
If you have a small number of machines to monitor, you can download the Pandora FMS OpenSource version here.

Traductora a francés e inglés. Me encantan las lenguas. Amante de la ropa oversize, la tarta de queso y el chocolate caliente en invierno. Me gusta leer, escuchar música, viajar y explorar cosas nuevas. Mi frase más temida por aquellos que me conocen es “he estado pensando…”
Translator into French and English. I love languages. Lover of oversized clothes, cheesecake and hot chocolate in winter. I like reading, listening to music, travelling and exploring new things. My most feared phrase by those who know me is “I’ve been thinking…”


















