Increase team collaboration quality and speed in emergencies with Pandora FMS and ilert’s ChatOps features
Pandora FMS is an excellent monitoring system that helps collect data, detect anomalies, and monitor devices, infrastructures, applications, and business processes. However, more than monitoring alone is needed to manage the entire incident lifecycle. ilert complements Pandora FMS by adding alerting and incident management capabilities. While Pandora FMS detects anomalies, ilert ensures that the right people are notified and can take action quickly. This combination helps reduce the mean time to resolution (MTTR) and minimize the business’s impact.
While Pandora FMS and ilert are reliable and robust foundations for your system’s resilience, the magic of team collaboration and real-people decisions happens in chats. This trio of tools is indispensable in today’s business world. In this article, we will provide practical recommendations on evolving your ChatOps and enhancing the speed and quality of incident response.
What exactly is ChatOps?
ChatOps is a model that connects people, tools, processes, and automation into a transparent workflow. This flow typically centers around chat applications and includes bots, plugins, and other add-ons to automate tasks and display information.
As a model, ChatOps means that all team communication and core actions are taking place right in a chat tool, which eliminates the need to switch between the services and makes it possible to orchestrate the work from one platform. As there is a variety of chat tools on the market, there are, for sure, two of the most commonly used among IT teams. Those are Slack and Microsoft Teams. As for the available data, they have 18 million and 270 million users, respectively, and those numbers are growing consistently for both companies.
As there is a wide variety of implementations of the ChatOps model to everyday work, we will concentrate specifically on how to manage incidents through ChatOps.
ChatOps and Incident Management: What is it all about?
The fusion of monitoring and incident management platforms with ChatOps is a manifestation of modern IT operations aiming to optimize efficiency, speed, and collaboration. By marrying these paradigms, organizations can capitalize on the strengths of the tools, leading to streamlined incident resolution and enhanced operational visibility.
At the core of ChatOps lies real-time collaboration. When an incident arises, time is of the essence. Integrating ChatOps with an incident management platform ensures that all team members—be it developers, support, or management—are immediately aware of the incident. They can then collaboratively diagnose, discuss, and strategize on remediation steps right within the chat environment. This kind of instant cross-team collaboration reduces resolution time, ensuring minimal service disruption.
Here are other advantages that integrated ChatOps provides in times of incident response.
Centralized information flow
ChatOps can funnel alerts, diagnostics, and other relevant data from various sources into a single chat channel. This consolidation prevents context-switching between tools and ensures everyone has access to the same information.
Team awareness
Everyone involved in the incident response has a shared view of the situation. This shared context reduces miscommunication and ensures everyone is aligned on the incident’s status and the response strategy.
Detailed overview
Every action taken, command executed, and message sent in a chat environment is logged and timestamped.
Accountability
With each chat action being attributed to a team member, there’s clear accountability for every decision and command. This is especially valuable in post-incident reviews to understand roles and contributions during the incident.
Automation
Through chat commands, responders can trigger predefined automated workflows. This can range from querying the status of a system to initiating recovery processes, thereby speeding up resolution and reducing manual efforts.
Accessibility
With many ChatOps platforms being available on both desktop and mobile, responders can participate in incident management even when away from their primary workstation, ensuring that expertise is accessible anytime, anywhere.
9 Tips on How to Squeeze Maximum out of ChatOps in Times of Incidents
ChatOps provides a synergistic environment that combines communication, automation, and tool integration, elevating the efficacy and efficiency of incident response. But what exactly do teams need to uncover the full potential of their chats?
We won’t dive deep into instructions on how to connect Pandora FMS with the ilert incident management platform, but you can find related information in Pandora FMS Module Library and a step-by-step guide in ilert documentation. Find below a list of best ChatOps practices for organizing your workflow when an alert is received.
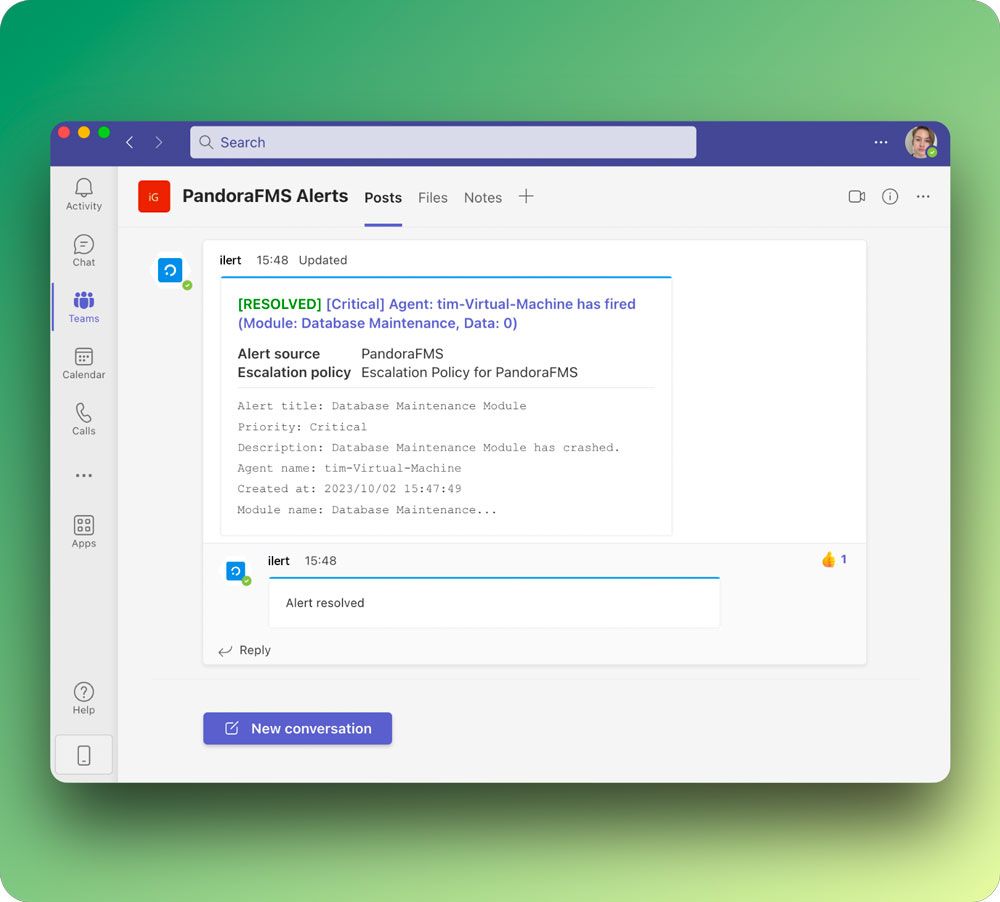
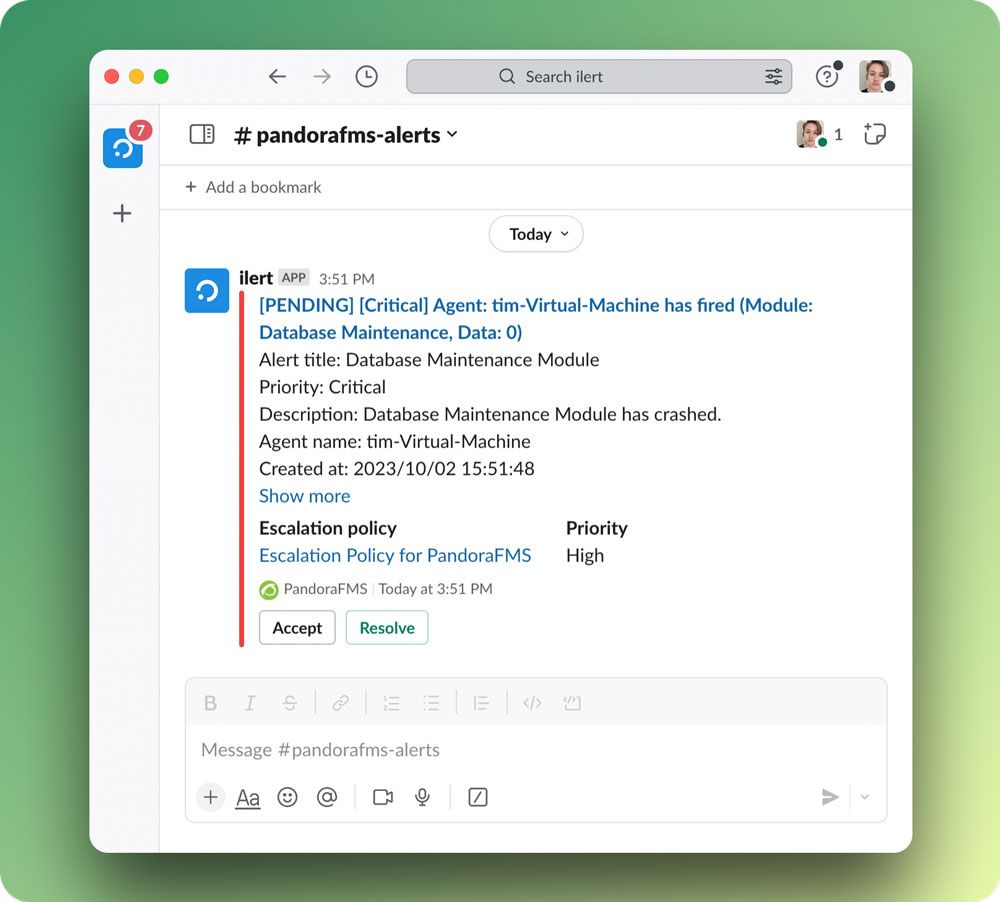
Use dedicated channels
Create dedicated channels for specific incidents or monitoring alerts. This helps to keep the conversation focused and avoids cluttering general channels. And don’t forget to set a clear name for those channels. In ilert, the pre-build title includes the name of the monitoring tool and the automatically generated number of an alert, for example, pandorafms_alert_6182268.
Allow users to report incidents via your chat tool
Enable all users to report incidents through Slack or Microsoft Teams using pre-set alert sources for each channel. This approach empowers teams to have a structured method for reporting concerns related to the services they offer within their dedicated channels.
Decide on what channels should be private
Most chat tools provide functionality to create public channels that are searchable across an organization and can be viewed by all team members, and private where only specific people can be invited. Here are a few reasons why you might want to create a private channel:
- Sensitive data exposure. Such as personal identification information (PII), financial data, or proprietary company information.
- Security breaches. In the event of a cyberattack or security compromise, it’s important to limit knowledge about the incident to a specialized team. This prevents unnecessary panic and ensures that potential adversaries don’t gain insights from public discussions. You can read more on how to prevent data breaches in the article “Cyber Hygiene: Preventing Data Breaches.”
- High-stakes incidents. If the incident has potential grave repercussions for the organization, such as significant financial impact or regulatory implications, it’s beneficial to restrict the discussion to key stakeholders to ensure controlled and effective communication.
- Avoiding speculations. Public channels can sometimes lead to uncontrolled speculations or rumors. It’s best to keep discussions private for serious incidents until the facts are clear and an official narrative is decided upon.
Keep all communication in one place
Ensure that all decisions made during the incident are documented in the chat. This assists in post-incident reviews.
Pin important messages
Use pinning features to highlight essential updates, decisions, statuses, or resources so they’re easy for anyone to find.
Keep stakeholders informed
Ensure you keep your team in the loop and update all incident communication, including public and private status pages, in time.
Use chats in post-mortem creation
The real-time chat logs in ChatOps capture a chronological record of events, discussions, decisions, and actions. During a post-mortem creation, teams can review this combined dataset to construct a comprehensive incident timeline. Such a detailed account aids in pinpointing root causes, identifying process bottlenecks, and highlighting effective and ineffective response strategies.
Regularly clean up and archive
To maintain organization and reduce clutter, regularly archive old channels or conversations that are no longer relevant. Avoiding numerous channels in your list will also speed you up when the next incident occurs.
Provide regular training for all team members
The more familiar your team is with tools, alert structure, chat options, and features, the quicker you will be when the time comes. Trigger test alerts and conduct incident learning sessions so that everyone involved knows their role in the incident response cycle.
Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring. Pandora FMS’s editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.


















