Do you already know what a web firewall is? Let us tell you about it.
There’s something that humans and machines have in common, and no, it’s not the disappointment suffered by the final season of Game of Thrones, or, well, at least not only that. What we have in common is that we need protection. You know, animals need it too, and plants, but if you’ve gotten this far, it seems that you’re interested in computers, networks and all these pretty modern “geek” things, so today we’ll talk about that kind of protection.
Just as you would protect your dog, your ficus or yourself, you have to protect your computer. The world is a place full of dangers and risks and the Internet is not far behind. It’s like in Crystal Jungle, only instead of people carrying guns around, we’ll find hunched over users willing to collect information from your computer, networks, and troll you in any possible way.
Remember: “The night is dark and harbors errors”. And horrors too.
The Internet also hosts them, so to protect our beloved computer, we must make use of a “Web Firewall”. What is this “Web Firewall”?
A “Web Firewall” is a system that is intended to protect our private network and block unauthorized access or attacks from other networks. In turn, it allows incoming and outgoing traffic between computers on the same network. That is, it is like the door of your house, or, worth the analogy, a half-open blind that only lets in a specific amount of breeze according to your personal comfort.
But not only that, it can be our beloved ally, protector of what we love the most, since through configurations you may limit, encrypt or decrypt this traffic. Here’s another lucid analogy: Maybe, in your day to day, you have to go to a clandestine meeting whose members no one should know. It is similar with your computer, you may encrypt your traffic so that you cannot access the most relevant data.
The web firewall, capable of such feats, can be implemented in hardware or software. If it’s well configured, it will be an advantage when it comes to protecting your networks, so it’s vitally important to understand how it works and how you may get the most out of it.
How does a web firewall work?
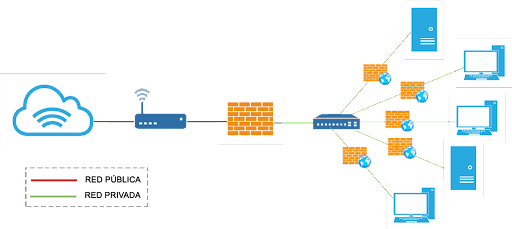
Outline of a firewall on a computer network
It is usually located at the junction point between two networks. Each network or computer can have its own firewall. This can limit the consequences of an attack, as you can prevent damage from spreading from one network to another. The sooner the spread of evil is tackled, the better.
The essential thing that you must know for the operation of the web firewall is that the totality of information and traffic that goes through our router and that is transmitted between networks is analyzed by it. If the traffic complies with the rules you have configured for it, it can enter or leave your network. If the traffic does not meet those certain rules, then it will be blocked from reaching its destination.
There are several methods by which you may filter the traffic of the firewall, for example, configuring it as you please. Remember that a good firewall configuration is paramount. If the lock on your front door was badly designed and anyone could open it, bad people could get in and steal, this is the same thing.
Let’s take a look at some of the filtering methods we’ve been provided by our dear friend, the Web Firewall.
Traffic filtering methods
- Firewall policies: They allow you to block certain types of network traffic.
- Anti-spam firewall: It protects against spam, phishing, etc.
- Antivirus firewall: It protects the internal network against attacks that come from the Internet or wan.
- Content filtering: It allows you to block some types of web content.
- WAP Managed Service: It allows you to control wap devices.
- DPI services: It allows you to control specific applications.
There are a few types of firewalls to highlight, these can be software or hardware, and, if we investigate a little more, we will find others that are somewhat more defined.
Types of web firewall
- Gateway application level: It applies security mechanisms for specific applications.
- Gateway level circuit: It applies security mechanisms when a tcp or udp connection is established.
- Packet filtering: At network level as an IP packet filter.
- Personal: It is installed as software on your computer.
Using a firewall has lots of advantages. We already discussed some, with lots of examples and tremendous analogies, even so, we are going to list the most obvious ones:
Advantages of using a firewall
- It blocks access to computers and/or applications to our networks.
- It allows you to control and restrict communications between the parties under your settings.
- It optimizes communication between internal network elements, helping to reconfigure security settings.
- It establishes reliable perimeters.
- Protection of intrusions and private information.
Nothing is perfect, and web firewalls, despite their fiery name, well, they aren’t either. These also have some notable limitations:
Limitations of a web firewall
- It cannot protect itself from attacks whose traffic does not go through it.
- It cannot protect threats made by insider attacks or negligent users.
- It does not protect against service security flaws and protocols whose traffic is allowed.
- It cannot protect against attacks on the internal network through files or software.
There are many firewall systems, if we use Linux, the one commonly used is Iptables. Yes, it sounds weird, we don’t like weird sounding things and since we don’t like weird things we use the firewall… Hmm… before entering a self-destructive paradox, we will try to understand what this“Iptables” is through a simple explanation.
What is Iptables?
Linux has a firewall system included in its kernel called Iptables, although its configuration can be a bit complex. Its default configuration is to allow everything to enter and exit.
With a suitable Iptables configuration you will be able to filter which packages, data or information you want to enter and which ones you do not. Just like the previous example about the inputs.
To work with Iptables you need administrative permissions so you will have to use sudo. You will have to choose wisely what you let in and what not, and, for this, an adequate knowledge of the commands that you can use in this system is necessary. The following examples are only intended to teach a basic configuration to understand the logic of the web firewall, but for a more correct and complex configuration, I recommend adding information by searching the Internet, specialized books or colleagues in the world.
Some commands to understand Iptables
sudo iptables -P INPUT DROP
-P = Anyone who wants to access the computer
INPUT = We ignore it
DROP = We ignore it
With this command nobody will be able to enter your computer, in fact you neither… so it is not the most appropriate one.
sudo iptables -A INPUT -i lo -j ACCEPT
sudo iptables -A INPUT -m state –state ESTABLISHED,RELATED -j ACCEPT
The first line tells us that our own computer (lo = localhost) can do whatever it wants.
Before, we said that this was like a house, if we have siblings, parents or children and they leave, we want them to be able to get in again, right? Well that’s what we do with the second line, all the connections that come out of our computer will be allowed by Iptables.
sudo iptables -A INPUT -p tcp –dport 80 -j ACCEPT
With this command, anyone can see the websites that our computer has.
-j ACCEPT = Accept or allow
-dport 80 = Traffic to port 80
-p tcp = make it tcp
-A INPUT = that is incoming
These would be some basic examples of how Iptables works. That is, just to understand the basics of its operation. Like I said, I recommend digging deeper and diving into more information to make an acceptable setup.
And just like Game of Thrones ended, this article also does it, although much better (what a crappy last season), so I only have to say goodbye and wish you to have a good day. AH! And to recommend you to use Pandora FMS, which despite not being a web firewall, is a tool that will also help you protect yourself by collecting information.
Would you like to find out more about what Pandora FMS can offer you? Find out clicking here . If you have to monitor more than 100 devices, you can also enjoy a FREE 30-day Pandora FMS Enterprise TRIAL. Installation in Cloud or On-Premise, you choose !! Get it here .
Last but not least, remember that if you have a reduced number of devices to monitor, you can use the Pandora FMS OpenSource version. Find more information here .
Do not hesitate to send your inquiries. The great team behind Pandora FMS will be happy to assist you! And if you want to keep up with all our news and you like IT, release and, of course, monitoring, we are waiting for you in this our blog and in our different social networks, from Linkedin to Twitter through the unforgettable Facebook . We even have a YouTube channel , and with the best storytellers. Ah well, we also have a new Instagram channel ! Follow our account, we still have a long way to go to match that of Billie Eilish.

Alejandro Sánchez Carrión, desarrollador junior, aficionado a la historia, los videojuegos y los comics, también gran aficionado al fútbol y al Real Madrid. De Alcalá de Henares, como el Quijote. Me encargo de desarrollar, modificar y documentar plugins en el departamento de proyectos.
Alejandro Sánchez Carrión is a junior developer, a fan of history, videogames and comics, and also a big fan of football and Real Madrid. From Alcalá de Henares, like Quixote. I’m in charge of developing, modifying and documenting plugins in the projects department.
















