Is it a virus, a malware? Protect yourself by knowing it even more
What is Ransomware?
The Ransomware virus became a real global problem in 2014. Moreover, since then, it has only become more threatening and harmful. This is a type of malware that enters the victim’s devices intrusively and unstoppably, while blocking access to the data or, alternatively, encrypting it completely. After the attack, the victim must make a ransom payment if they intend to recover access to their own data that has been blocked or encrypted. It is therefore essential to know how to protect ourselves from ransomware.
According to a report presented by IBM, Ransomware’s virus (malware) was responsible for nearly 4,000 attacks per day in 2016, a 400% increase on what happened in 2015. The FBI, in turn, says that victims of the virus paid close to $209 million dollars (a disturbing figure) to recover their data in the first quarter of 2016 alone, which is a far greater figure than the $24 million that was paid in 2015.
As if the data to which we have just referred were not sufficient, the figures have increased even more in 2017, but we will refer to them later on. Computer security authorities and many experts in the field usually recommend that victims not pay ransoms at all (as is the case with all kidnappings), since this motivates cyber-criminals to increase their criminal activities. In addition, there is no guarantee that victims will recover access to their kidnapped or encrypted data after payment is verified to rescue them. Let’s go into detail, then, to see what WannaCry is.
What does WannaCry consist of?
Over the past few years, the world has witnessed an enormous amount of sophisticated malware and also attacks targeting governments in major countries and leading global corporations. To capture much more recent data than those presented in the introduction, let’s say that, in May of this year, the world witnessed “WannaCry” which, it is fair to say, is the largest and most devastating cyber-attack in history. To be more explicit and specific, let’s note that Ransomware was an extremely daring and damaging Ransomware that dramatically affected more than 200,000 organizations from over 150 countries around the world.
WannaCry blocked the data on a huge number of devices and left users in precarious condition, to the point where it left them with only two files: one file containing instructions on what victims should do next and one file containing instructions on how to recover their abducted data. In such circumstances, the victims of the crime had only one option: to pay to recover their data, contrary to the recommendations of the authorities and experts.
What does the U. S. National Security Agency have to do with all this?
It turns out that, being the most sophisticated “viral outbreak” that had ever occurred, it seized and used several cyber-piracy software tools, which were stolen from the NSA (National Security Agency). They were filtered online in April of this year, by a group that calls itself “Shadow Brokers” which is pretty self-explanatory. Despite this devastating scenario, last October, “Bad Rabbit”, the massive new Ransomware that is keeping Europe on edge, made its appearance.
What does Bad Rabbit consist of?
In addition to the malware already mentioned, namely WannaCry, many were the victims of another large-scale attack by Ransomware: ExPetr, also known as “NotPetya” or simply “Petya”. Now, a third attack is taking on a worrying force: “Bad Rabbit”, a new malware that is spreading throughout Europe, with Russia and Ukraine being the most affected nations, although it should be borne in mind that Germany and Turkey have also been “prey” to this new Ransomware modality. Let’s make it clear that the term “Ransom” is very accurate in this case, since our data is being “kidnapped”. Protecting ourselves from ransomware is urgent and imperative.
Let’s look at the targets or victims of Bad Rabbit (or at least those who have reported):
- the Ministry of Infrastructure of Ukraine
- Kiev’s Public Transport System
- Interfax, a Russian news service
- Kaspersky, another Russian media
- Fontanka.ru, a Russian news medium
According to this list and according to the investigators’ criteria, these attacks are apparently directed towards the media, while also having many similarities with the other malware already mentioned, namely NotPetya or Petya. As far as Kaspersky (another victim of the above list) is concerned, this time, let us say that it is an attack that does not use “Exploits” or, in other words, that does not take advantage of operating system failures. Rather, it is an attack known as “Drive-by” which, it is necessary to warn that it requires the actions of the victims, paradoxically.
TechCrunch’s opinion on this global problem affecting governments and organizations
Some of you may be wondering, and rightly so,”why is this company’s opinion important?” and even “what the hell is TechCrunch?”. Well, it turns out that this is a blog which, by 2009, had more than one million subscribers using RSS, while receiving more than 200,000 hits a day at the time. If that was eight years ago, can you imagine how the statistics of this site look like today? In other words, it’s not just a blog. It’s “THE” BLOG. Let’s continue, then, to say that TechCrunch maintains (and we agree) that Bad Rabbit requires the attacked victims to download and run the virus that comes in the form of an Adobe Flash installable file.
In addition, according to the opinion of the experts of this prestigious blog, when a computer or other device is victim of Bad Rabbit, two tasks are generated with the names of two dragons from “Game of Thrones” and “Grey Worm”, the commander of Daenerys Targaryen’s army. Now, all this terminology can be unknown and even exotic to many readers. However, you only need to type in on Google or your preferred search engine, TechCrunch + the term you want to know about. We won’t explain it here, as this article would become too long.
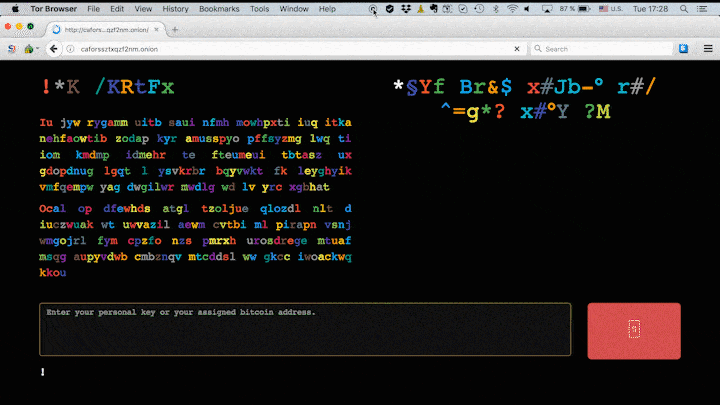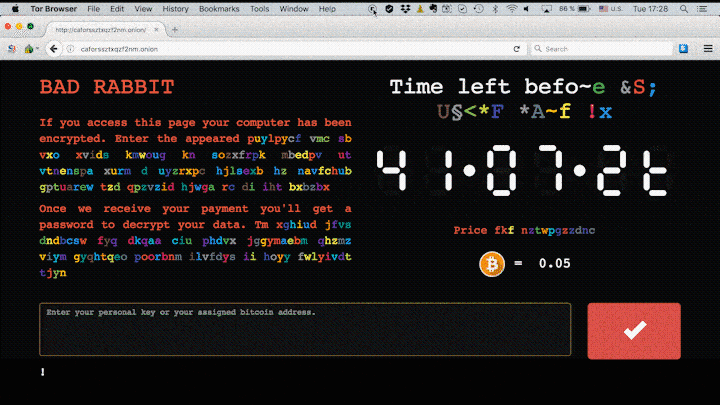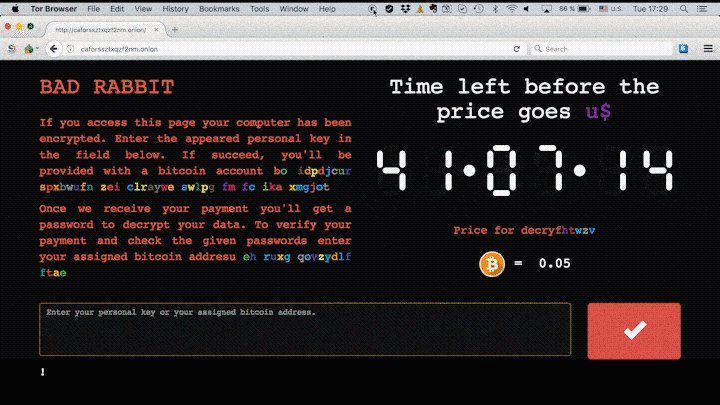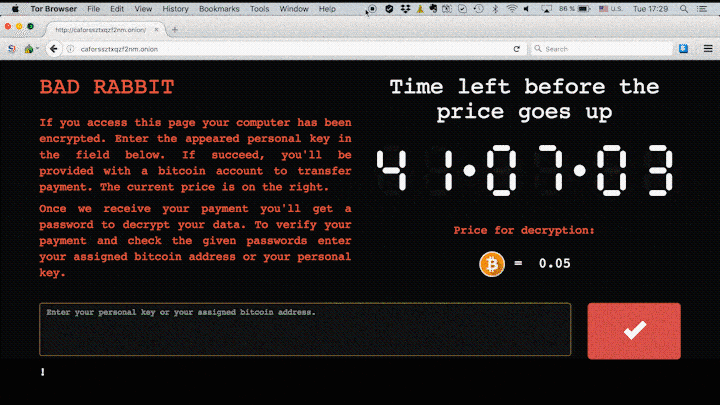
Then, the computers affected by this malware are directed to a domain in which they are asked to pay 0.5 Bitcoins, which is equivalent to about 276 dollars or, in other words, 237 euros, to recover the data. There is a “infamous” countdown at that site, where the victim can see the time unilaterally set by the offenders before the price increases. As is the case with almost all kidnappings, it is not yet known whether cybercriminals who use this malware release the kidnapped data and remove the virus after receiving payment. In the following image we can see the site that shows the mentioned countdown.
Do not be afraid to click on the link with which we give the respective credit to the image, (it is not the domain to which we referred) located in a website that refers to this serious problem that is affecting Europe. However, when clicking on it, we will be able to appreciate the mentioned countdown, only with informative intention. Let’s see, now, how to protect ourselves from ransomware and, more specifically, from the Bad Rabbit variant.
How to protect against Bad Rabbit malware?
According to the experts who have advised Kaspersky that, let us remember, it is one of the Russian news media that have been victims of Bad Rabbit, even if we have some means of protection or, antivirus software, as could be the case of Avast or Avira, it is necessary to make sure that we take any of this measures:
- Kaspersky Security Network activated
- System Watcher activated
- block file execution by means of some “vaccines”
- Create files called c:\windows\infpub.dat and c:\Windows\cscc.dat
- after creating this files, block all run permissions
- have a backup of all our data
The best tools for protecting yourself from ransomware and how to remove it if it is already installed
Having the Ransomware virus on our computer is a real emergency, which requires drastic decision making. For this purpose, we will mention some of the best tools that can be very useful to us. If we are Internet users in the home environment or, well, if we are the owners and/or webmasters of a small, medium or large company, it is possible that we find a dialog box that tells us that the files of our computer with the Windows operating system are encrypted and, worse still, that we have 48 or 72 hours to pay 300-350 euros (in Bitcoins, of course) and recover those files. We will also be told that if we do not meet the deadline imposed by criminals, the price will increase.
In this case, it is already too late to do anything, because the only option will be to pay, unless we intend to allow ourselves to pay, without the assurance that the data will be released. Now, if we had the precaution of transporting backups before, everything could be relatively well. In other words, to be clearer and more explicit, let’s say that the best defense against the Ransomware virus is to make and transport backups. Now, antivirus software is better adapted to counter this infamous threat. Some experts even say that these programs have the capacity to “clean up the mess” after it has been unleashed. However, the “mutation capacity” (so to speak) of these viruses means that we must be one step ahead of antivirus programs to protect ourselves from ransomware.
These rescue malwares almost always use unbreakable public key encryption to block files. However, the number of variants is relatively small at any given time, while security software may be tunable to detect the most active Ransomware type, observing the known behavior, such as interaction with the file system. In such a state, it is best to make use of the list of tools that we will now refer to. These are tools with which we can manage to clean up the disaster, while at the same time we can carry out detection and even decryption. Let’s see them, then:
- Trend Micro Lockdown Screen Ransomware Tool.
- AVG Ransomware decryption tools from AVG
- BitDefense anti-ransomware
- Avast, anti-ransomware tool
- Kaspersky, anti-ransomware tool
Now, to be really honest, none of the above-mentioned IT products offers the possibility of 100% Ransomware removal and in some cases, it is not possible to remove even a fraction of it, so people and organizations need to operate with the greatest of care when they are online. It is advisable to prepare and transport the backups mentioned above. However, not the whole picture is bleak because these (listed) programs help us to protect the system and also to recover (if the virus has already entered) as quickly as possible, with minimal damage to the systems themselves and the networks. However, just removing the infection is only one way to recover the system, but not the data that was in it. We therefore reiterate, once again, that the best defense is backups.
Other interesting options for protecting ourselves from ransomware include anti-ransomware Malwarebytes (formerly CryptoMonitor), Rakhni Decryptor, Rannoh Decryptor, the CionVault Decoder, Webroot SecureAnywhere Antivirus, and the important and prominent McAfee Ransomware Interceptor. We can also find more information in other Pandora FMS blog articles about other defense alternatives against this harmful and devastating Ransomware virus.
About Pandora FMS
Pandora FMS is a flexible monitoring system, capable of monitoring devices, infrastructures, applications, services and business processes.
Of course, one of the things that Pandora FMS can control is the hard disks of your computers.
Would you like to know more about what Pandora FMS can offer you? Discover it by entering here: https://pandorafms.com
If you have more than 100 devices to monitor, you can contact us through the following form: https://pandorafms.com/en/contact/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org
Do not hesitate to send us your queries. The Pandora FMS team will be happy to assist you!
Rodrigo Giraldo, freelance technical writer. Lawyer and astrobiology student, he is passionate about computers, reading and scientific research.