SimpleSAML 2 . 0 local
Introduction
Once SAML Single Sign-On is installed following the official documentation, you may use these steps to configure a local authentication.
Important: This local authentication is for testing purposes only, it is never recommended for use in production environments and it is recommended to revert step 1 and step 2 changes before moving on to production.
Step 1: Enabling exampleauth
Open the following configuration file with the text editor of your choosing:
/opt/simplesamlphp/config/config.php
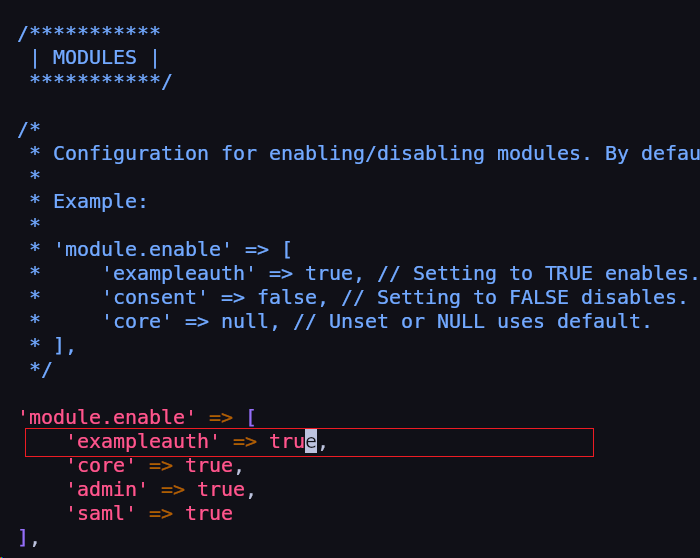
Find the block module.enable, then exampleauth, whose default value is false and change it to true.
Save and exit.
Step 2: Creating a local authentication source
With the text editor of your choosing, open the file:
/opt/simplesamlphp/config/authsources.php
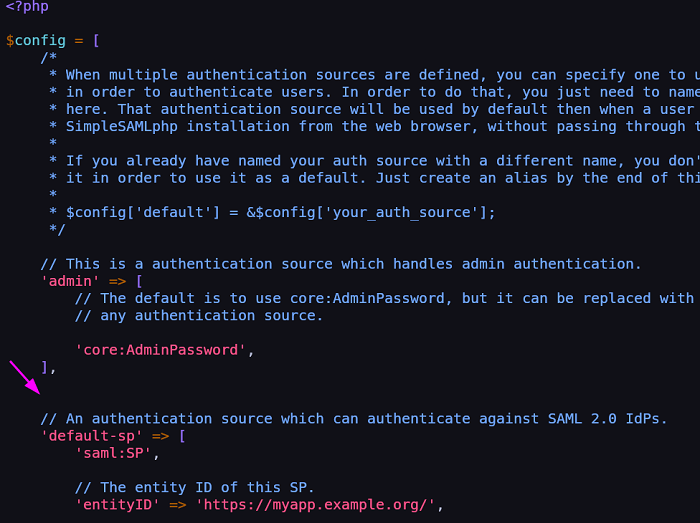
A block must be created for the new authentication source, the easiest way is to create it just before the default-sp:
With a block similar to the following:
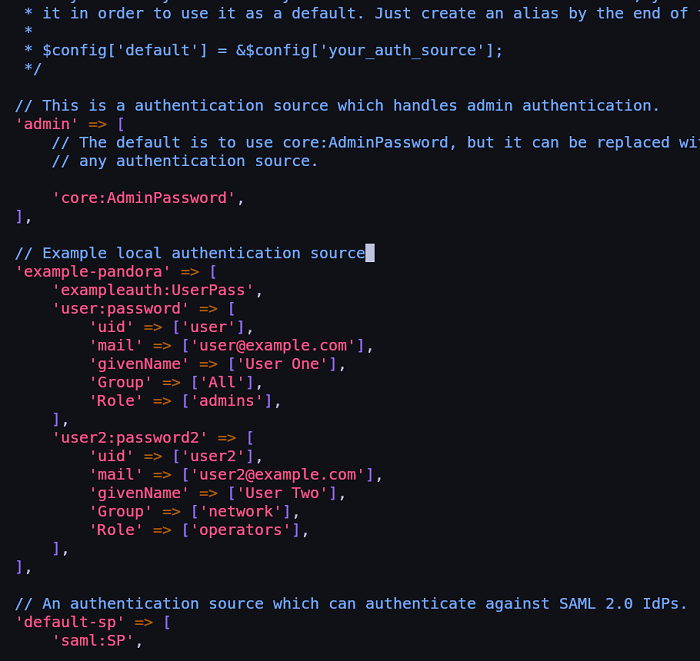
// Example local authentication source
'example-pandora' => [
'exampleauth:UserPass',
'user:password' => [
'uid' => ['user'],
'mail' => ['user@example.com'],
'givenName' => ['User One'],
'Group' => ['All'],
'Role' => ['admins'],
],
'user2:password2' => [
'uid' => ['user2'],
'mail' => ['user2@example.com'],
'givenName' => ['User Two'],
'Group' => ['network'],
'Role' => ['operators'],
],
],
The result should be similar to:
The auth source named example-pandora contains 2 users:
userwith passwordpasswordanduser2with passwordpassword2.- Each user has a number of attributes such as
uid,mail,givenName,GroupandRole. - These attributes are defined in the array so you may change or add more attributes in order to perform further authentication tests.
Step 3: Local authentication check
It is accessed through the URL https://pandora.local/simplesamlphp/admin/ (replace pandora.local by the URL of PFMS Web Console).
It must be accessed with HTTPS, as HTTP will fail authentication.
Enter the credentials for the admin user previously configured in SAML.
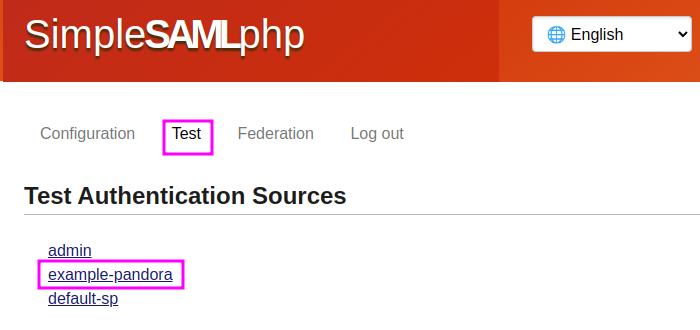
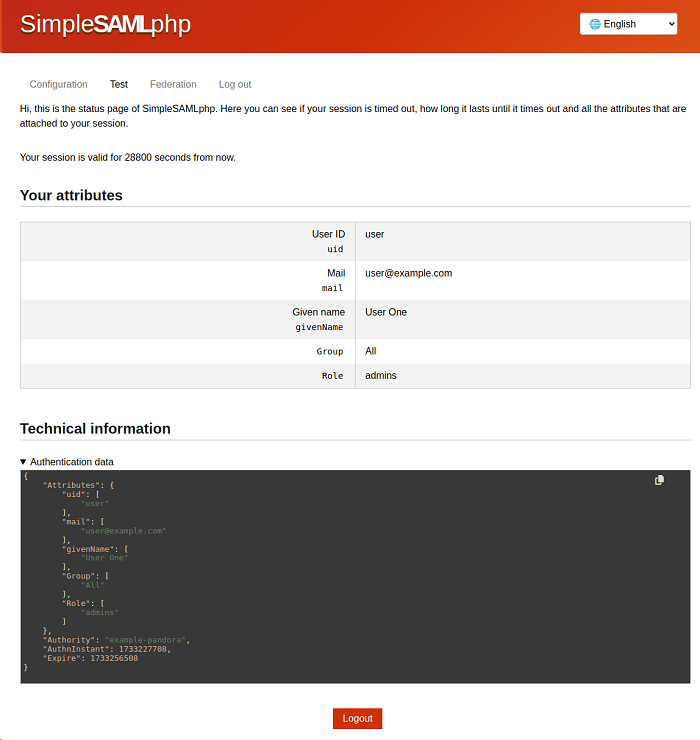
Click on the test tab which will display the new authentication source (example-pandora):
Click on example-pandora and it will ask for username and password, check with one of those defined in step 2 (shown for user):
See in Your attributes and compare with all the defined attributes, with this you may check that authentication using SAML works properly and you may configure in Pandora FMS.


 Home
Home