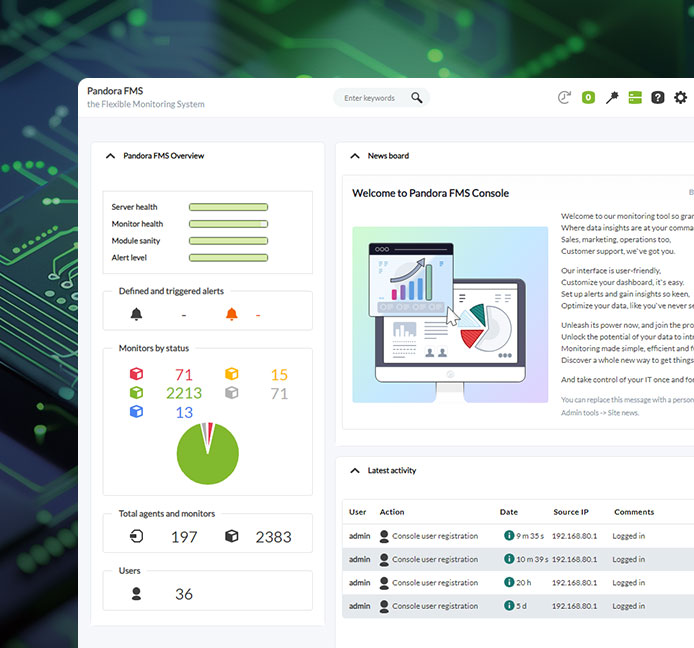
Security monitoring with Pandora FMS
System Security Permanent Monitoring
At Pandora FMS, we understand the importance of ensuring the integrity and security of your systems in an ever-evolving digital world. That is why our platform is designed to give you the tools you need to audit and secure your systems with absolutely no worries.
Security monitoring with Pandora FMS
The importance of maintaining integrity and security
The Pandora FMS platform is designed to provide you with the necessary tools to audit and secure your systems with confidence in a constantly evolving digital world.
Discover all that Pandora FMS can do for you with our complete and functional trial.
Contact our team to request a demo, resolve your doubts or receive a personalized quotation

Pandora FMS 360º Monitoring
Root out all vulnerabilities in your system and protect your infrastructure without fissures.
Hardening Monitoring
We merged CIS recommendations with our monitoring technology to provide you with an integrated securitization audit system that includes more than 1,500 individual checks. Track and evaluate in real time the evolution of your hardening measures in all your environments.
Proactive Alerts
Not only do we help you spot potential security breaches, but we also provide proactive alerts and recommendations to address any issues before they become a real threat.
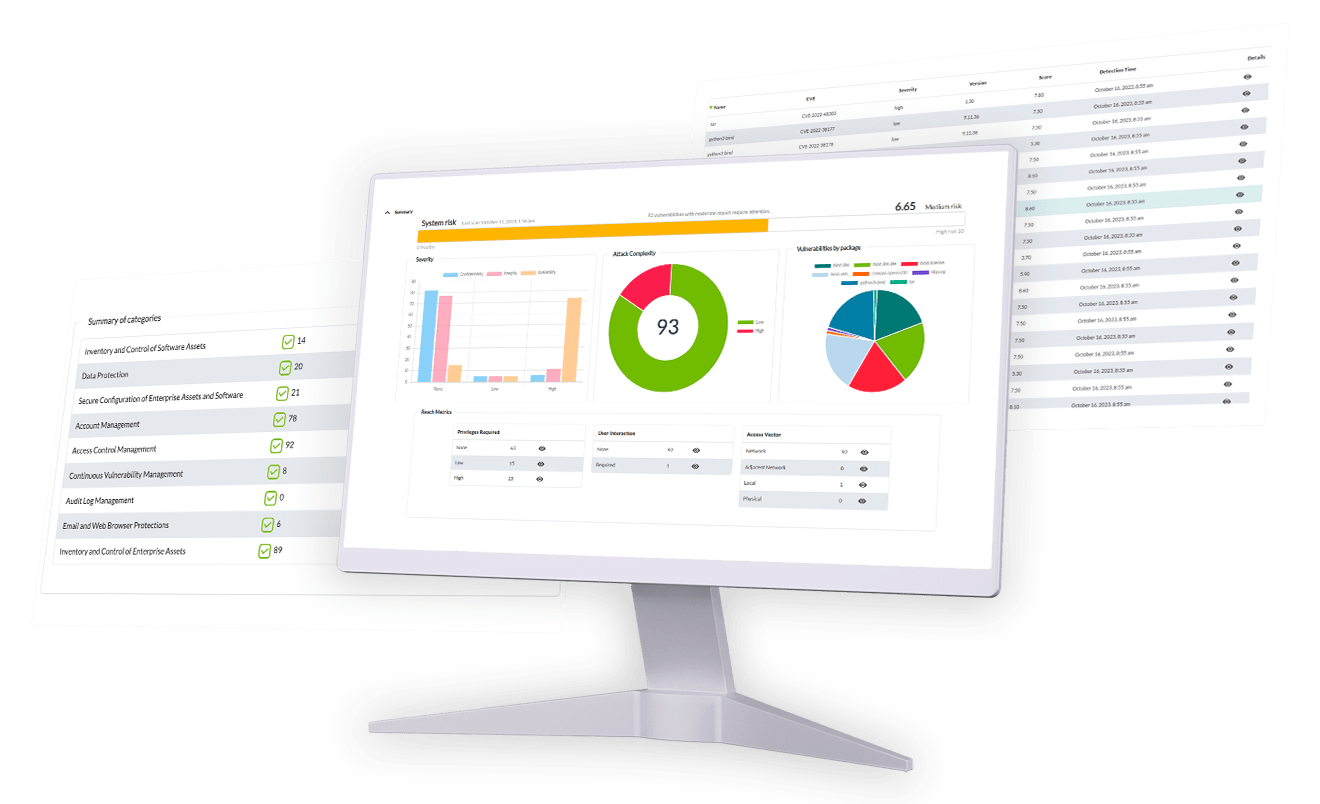
Permanent Vulnerability Monitoring
We integrate the whole vulnerability database from Mitre (CVE) and NIST to perform vulnerable software audits throughout your entire organization on a steady basis. Both agents and the Discovery remote component will be used to point out which systems have software with vulnerabilities.
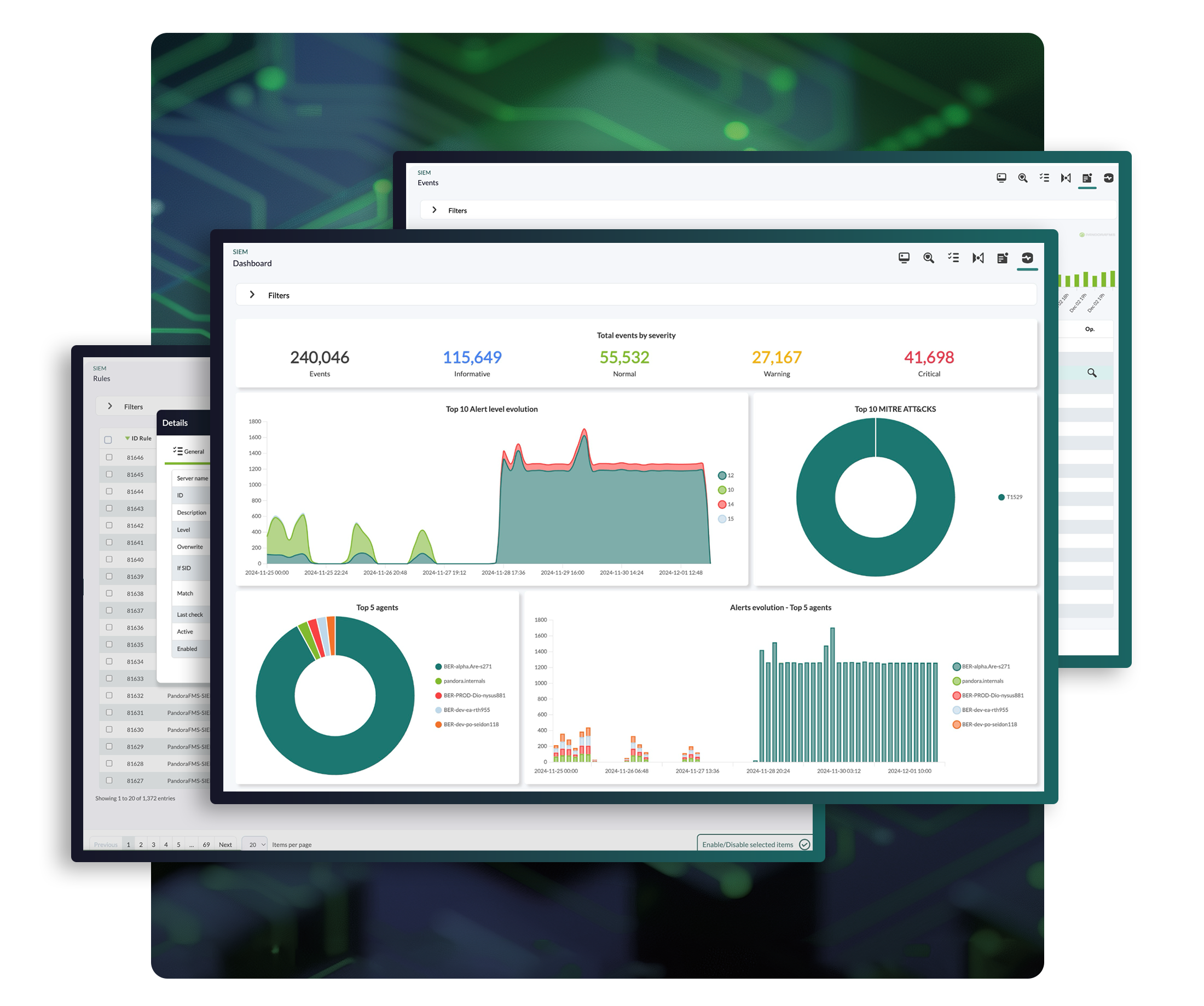
Security Infrastructure Monitoring
Monitor the status of security infrastructures: Backups, antivirus, VPN, firewalls, IDS/IPS, SIEM, honeypots, authentications systems, storage systems, log collecting, etc.
Server Security Monitoring
We check in real time the security of remote access, passwords, open ports and system key file changes. If there is any news, you will be warned virtually in real time.
Inventory Flexibility
Whether you use Linux systems from multiple distributions or any Windows version, we adapt to all of it. Regardless of the complexity of your infrastructure, thanks to Pandora FMS you may inventory in detail all kinds of systems and customize it to your liking.
CIS Categories Audited by Pandora FMS
We’ve taken the CIS recommendations a step further by implementing more than 1,500 individual checks in a variety of safety-critical categories.
Hardware and Software Asset Inventory and Control
Monitor and manage all your network software and devices. Keep an updated inventory of your IT assets and use authentication to block unauthorized actions. Furthermore, supervise and manage your network software, allow authorized actions and block non-desired ones. Your security requires so.
Device Inventory and Control
At Pandora FMS, we take care of the security of your systems from the ground up, this means identifying and managing your hardware devices so that only authorized ones have access, blocking unwanted ones. Maintaining proper inventory minimizes internal risks, organizes your environment, and brings clarity to your network.
Vulnerability Management
Analyze your assets on a regular basis to detect possible vulnerabilities and solve them before they become a bigger problem. Reinforce your network’s security by making sure that the software and operating systems in your organization stay updated with the latest safety measures.
Admin Privilege Controlled Use
Closely supervise access and user behavior through accounts with the right permissions to avoid any unauthorized access to critical systems. Make sure only authorized users have higher permissions to avoid admin rights misuse.
Safe Hardware and Software Configuration
Set and keep security measures based on the standards your organization approves. Create a strict configuration management system that detects and alerts on any incorrect configuration and establishes a change tracking process to prevent attackers from taking advantage of vulnerable services and configurations.
Audit Log Maintenance, Supervision and Analysis
Compile, manage and analyze event audit logs to identify possible anomalies. Keep detailed logs to deeply understand attacks and be able to face security breaches efficiently.

Malware Defenses
Supervise and control malicious code installation and execution at different points on your company to prevent attacks. Configure and use antimalware software and take advantage of automation to guarantee defense quick updates and agile corrective actions in the face of any attacks.
Email and Web Browser Protections
Protect and manage your web browsers and email systems against online threats to reduce the chances of an attack. Disable browsers and unauthorized email plugins and ensure users only access trustworthy websites through URL filters based on the network.
Data Recovery
Set up procedures and tools to make sure the key information of your organization is correctly backed up. Make sure you have a strong data recovery system to restore information should any attack compromise critical data.
Boundary Defense and Data Protection
Identify and isolate sensitive data and set up a series of processes that include coding, protection plans against data leaks and data loss prevention techniques.
Account Control and Supervision
Closely supervise the whole lifecycle of their systems and application accounts, from its creation to its deletion, including its use and inactivity. This active management prevents attackers from taking advantage of the accounts of legitimate but inactive users for malicious purposes.

The Most Comprehensive
Vulnerability Database
Set up alerts, create dashboards and technical reports to filter by machine groups, types of attack, intrusion vector, privilege use and many other fields.

Our security ROADMAP
We are building a tool to control everything.
Pandora FMS is the base to monitor, audit, obtain logs, generate alerts, manage configurations (NCM), execute tasks in a distributed way (RMM) and much more.
With security monitoring, hardening analysis and vulnerability detection we have taken the first step but our roadmap is much more ambitious.
With this, and other system functionalities, we will complete a circle that we started in 2005.

Security that you can See and Verify
We are committed to show transparency at all times. Our platform allows you to easily check the implementation of every single control and perform an ongoing follow-up of your security state. Not all categories can be applied to all systems, however we have developed controls that will help you determine whether they are relevant for your environment.
Trust Pandora FMS for System Security
When you choose Pandora FMS, you choose a comprehensive solution that seamlessly combines monitoring and security. Our collaboration with CIS ensures that you are aligned with international best practices. From vulnerability protection to attack prevention, Pandora FMS supports you every step of the way.

Need help? get started with our resources and tips
Installation guide and first steps
Startup official guide: all the way from the installation and report generation, to day to day management.
Read the guides →
Pandora FMS on YouTube
Visit our official channel for in-depth guides, tutorials, interviews and important features.
Visit the channel →
Feature map
All features present in Pandora FMS in detailed explanation.
Read more about it →
Changelog
Summary list with all the changes and fixes made to Pandora FMS.
See changelog →
Documentation
User manuals, administration and development documents of Pandora FMS.
See documentation →
FAQ
All common questions about Pandora FMS are answered here.
View FAQs →
Security Architecture
We describe the security elements of each Pandora FMS component.
Visit the entry →
Version comparative
Compare what features are present in which versions of Pandora FMS.
Compare versions →
Quick guides
Discover all the How-to or specific tutorials for any specific task.
Go to guides →
Professional support
Invest in peace of mind with our premium support packages.
Get support →
Pandora FMS Discord
Get in touch with our awesome community and solve any problem asap.
Join the discord →
Related solutions
The most complete monitoring solution for total observability
User experience
User experience
Check that your application is working as expected. Detect failure before your customers do.
Virtual Supervision
Virtual Supervision
Optimize your infrastructure, whether for hybrid, virtual or cloud deployments.
Remote control
Remote control
All your devices controlled by a single tool accessible via a simple web browser.
Incident management
Incident management
Integrate your infrastructure's ticketing system into Pandora FMS with Pandora ITSM.
Application monitoring (APM)
Application monitoring (APM)
Monitor your enterprise applications at every level and get the APM data you need.
Mainframe supervision
Mainframe supervision
A single platform for collecting and displaying information, wherever it comes from.
Log collection
Log collection
Collect, visualize and centralize all your logs in a single location.
Service and support management
Service and support management
Measure and monitor your IT stack to detect and solve problems in your IT infrastructure.
Inventory
Inventory
Collect and monitor the status of all your IT infrastructure data in a single tool.
Network monitoring
Network monitoring
View all your information together, even if you have thousands of devices to monitor.
Inventory
Collect and monitor the status of all your IT infrastructure data in a single tool.
Incident management
Integrate your infrastructure's ticketing system into Pandora FMS with Pandora ITSM.
Network monitoring
View all your information together, even if you have thousands of devices to monitor.
Virtual Supervision
Optimize your infrastructure, whether for hybrid, virtual or cloud deployments.
Remote control
All your devices controlled by a single tool accessible via a simple web browser.
Application monitoring (APM)
Monitor your enterprise applications at every level and get the APM data you need.
User experience
Check that your application is working as expected. Detect failure before your customers do.
Log collection
Collect, visualize and centralize all your recordings in a single location.
Service and support management
Measure and monitor your IT stack to detect and solve problems in your IT infrastructure.
Mainframe supervision
A single platform for collecting and displaying information, wherever it comes from.









