Configuration
JOLOKIA INSTALLATION
Download the Jolokia agent from the official website: https://jolokia.org/download.html
Jolokia Agent Securisation (WAR)
You can assign security policies to restrict both access and use of the options available in the Jolokia agent.
These restrictions can be specified in a policy XML file. This file is divided into sections with which you can control various parameters:
IP-based restrictions
General access can be allowed based on the IP address of an HTTP client. This restriction is specified in the<remote> section, it will contain <host> elements. The source can be an IP address, a hostname, or a network in CIDR format.
The following example allows access from localhost and all clients on the network
10.0.0.0/16:
<remote>
<host>localhost</host>
<host>10.0.0.0/16</host>
</remote>Command Restrictions
You can restrict the commands that will be allowed to be executed in a general way, by specifying which commands are allowed. To do this, use the <commands> section by specifying each command with a <command> element.
The following example enables the commands READ, LIST, SEARCH and VERSION . The other commands ( WRITE, EXEC ) would not be available:
<commands>
<command>read</command>
<command>list</command>
<command>version</command>
<command>search</command>
</commands>There are restrictions on mbeans queries and request sources. Full help is available at the following link: https://jolokia.org/reference/html/security.html
https://pandorafms.com/guides/public/link/233#bkmrk-ejemplo-de-pol%C3%ADtica-
Example security policy
This example allows connection from localhost and network 10.0.0.0.0/16. The available commands are also limited to READ,LIST,VERSION and SEARCH.
<?xml version="1.0" encoding="UTF-8"?>
<restrict>
<remote>
<host>127.0.0.1</host>
<host>localhost</host>
<host>10.0.0.0/16</host>
</remote>
<commands>
<command>read</command>
<command>list</command>
<command>version</command>
<command>search</command>
</commands>
<http>
<method>post</method>
</http>
</restrict>Inclusion of a security policy
To repackage a policy in the WAR file of the Jolokia agent, you must follow these steps
following steps:
# Donwload war agent
$ jolokia
Note: You can download it manually from: http://search.maven.org/remotecontent?filepath=org/jolokia/jolokia-war/1.5.0/jolokiawar-1.5.0.war
# Download the sample policy template
# in the local directory as "jolokia-access.xml".
$ jolokia download --policyNote : If you received errors when executing the previous steps, you can download the sample policy from http://www.jolokia.org/templates/jolokia-access.xml.
Edit the policy and place the jolokia-war-VERSION.war file and the jolokia-access.xml file in the same directory.
# Repack the to add the policy file 'jolokia-access.xml' form the cwd
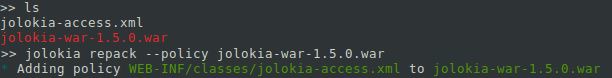
$ jolokia repack --policy jolokia.warYou should receive an output similar to the following:
$ jolokia repack --policy jolokia-war-1.5.0.war
* Adding policy WEB-INF/classes/jolokia-access.xml to
jolokia-war-1.5.0.warYou can perform a verification of the contents of the WAR file with the following command:
# Show current state (policy file include: yes/no)
$ jolokia jolokia.warJolokia on WebSphere
To install the proxy on IBM Websphere. Perform the following steps:
Select from the side menu:
Applications > New Application