I have been a regular user of Pandora FMS for years and the best I can say about them is that they always have something new to add to my learning. Today, for example, I rediscovered the Two-Factor authentication in Pandora FMS!
*And I did it, in part, through this article already published on their blog
Although I devote myself to programming (and it is what I like to do the most), I am more of a Web 2.0 person than a Web 3.0 person because I consider that the latter has been abused too much.
In 2.0, communication is bidirectional and at the same level, while in 3.0, when one inquires something they answer:
“And who’s asking?”
Having already taken advantage, of course, of unnoticeably checking our geolocation by means of your IP address.
No contentos con eso, en fin, nos pegan unNot happy with that, anyway, they stick a label on us as if we were digital livestock…
*And no, I’m not paranoid, several countries globally are amending their national privacy laws! (That’s why I mainly use the DuckDuckGo search engine).
But I wouldn’t ever go back to stay on the Web 1.0; at that time, the 1970s and 1980s (my youth), we were too innocent.
*For example, for many years the password to launch American mass destruction weapons was simply zero repeated eight times…
Obviously we need more robust authentication systems. And one of them came, not from a programmer but from a far-sighted entrepreneur, Kenneth P. Weiss.
Their input was essential to the world and to the issue we are discussing here today.
Since talking about encryption and security gives us enough material to write a whole book, let’s dive into it then!
Get to know the Two-Factor authentication in Pandora FMS
It is important to distinguish what is a Two-Factor authentication and two-step authentication.
Many banks force us to add several security questions that they use after entering our password. They randomly choose one or more of them and we must respond. The point is that they’re always things we know.
A second authentication factor is more about “what you have’‘.
There’s Mr. Weiss’s genius. How to authenticate that “something we have”?
Well, to put it simply: by means of public keys and private keys. Just like we have been doing on our computer for years.
However, Two-Factor authentication technology has evolved and now it also includes, quite frequently, biometric identifications. That’s basically, “what you are”.
My mobile phone, for example, includes fingerprint reading. But it would also be worth an infrared-based facial identification to detect by heat the veins and arteries of our face.
*Not even identical twins in the same egg have equal blood distribution.
More recently, another category has been added: what you do.
The way you sing or make a gesture. Even the speed of your typing, pauses included, and much more.
En todos eIn all these cases it is an additional security layer. To be considered as a Two-Factor authentication, at least two of them must be used.
The acronym MFA is used when three or four of the aforementioned methods are used.
Finally, it is important to point out the case of hardware devices as a second authentication factor: YubiKeyor the trendy Trusted Platform Module version 2.0 (TPM 2.0).
Operating mechanism
Like I said, it’s all about the private and public key pair.
In short, a private key is generated, which is shared with us users and when the time comes to use it, the date and time are taken and a public key is calculated.
That key is only valid for a period of time, say a minute, and it will be the one we give to identify ourselves.
In the site where we are going to enter, where said private key was generated, the same is done, the public key is calculated also for that period of time and is compared with the one that was delivered to the user at that moment.
Of course, this is much more complex than what I am describing, but as Leonardo da Vinci rightly said: “Simplicity is the ultimate sophistication.”
Pandora FMS and Google Authenticator
At Pandora FMS, Google Authenticator has been chosen, which is not surprising, because this company Alphabet Inc. has been in our lives for more than twenty years already and has become “the elephant in the room”.
Of course, there are also many others like LastPass Authenticator or Microsoft Authenticator.
The official Pandora FMS documentation explains very well how to configure the second authentication factor, however, I have something to add.

Two-Factor authentication is not a strong password backup itself. We must use strong passwords so that we have a time period of at least one month (and we should change them monthly).
*If there is a leak of the hash of our password, as it is robust, the thieves will take more than a month to decipher it and before that happens we will have already changed it ourselves.
• Both authenticators I tried can work offline without any problem because they depend on the time and date as I explained.
*However, if any unlikely problem occurs with the time and date on our mobile, Google Authenticator has the option to synchronize online without affecting the time and date of the device at all.
• But not everything was going to be good news: I also print backup codes that I store in a safe place for gmail emails.
*To download Google Authenticator, they will ask to implement the second authentication factor for mail.
Once you wish to log in to a new device, you may use the “Try other methods” option and enter one of the 8-digit backup codes. Remember to cross this code out of the list because they can only be used once.
• From your user profile in Pandora FMS, right next to the button to deactivate the second authentication factor, there is the “Show information” button, which will allow you to show the private code again to add it to an additional backup device.
*Let’s say that the battery of your main mobile has been completely discharged: you save time to enter Pandora FMS with the backup device.
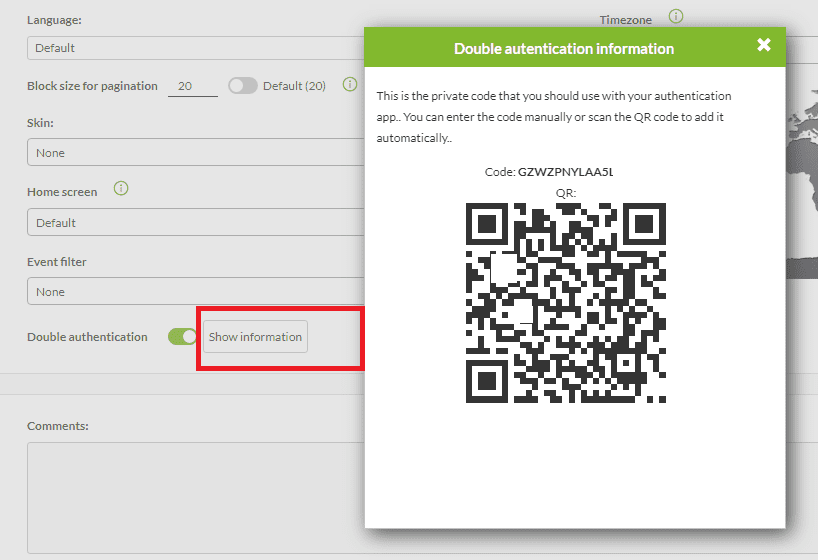
• Time is precisely one of the most frequent complaints in the use of the second authentication factor, since it takes longer to enter.
*But, calm down, I’ll say goodbye with the comforting fact you expected:
80% of attempts to force our accounts can be avoided with the use of a second authentication factor!
Resources

Programmer since 1993 at KS7000.net.ve (since 2014 free software solutions for commercial pharmacies in Venezuela). He writes regularly for Pandora FMS and offers advice on the forum . He is also an enthusiastic contributor to Wikipedia and Wikidata. He crushes iron in gyms and when he can, he also exercises cycling. Science fiction fan. Programmer since 1993 in KS7000.net.ve (since 2014 free software solutions for commercial pharmacies in Venezuela). He writes regularly for Pandora FMS and offers advice in the forum. Also an enthusiastic contributor to Wikipedia and Wikidata. He crusher of irons in gyms and when he can he exercises in cycling as well. Science fiction fan.

















